Subnet / VLAN Design
-
Hey guys, wondering if you can help with my Subnets/VLAN design for my pfSense based network I'm planning. I studied Network Computing at Uni but haven't had much to do with technology for 14 years so I'm using this as a learning project as well as improving my network. Some of the following info is probably not needed but I don't want to leave out anything relevant
Hardware I currently have:
Old PC that Ive installed an Intel quad NIC
Open reach modem
Unifi AC Pro
TP Link powerline adapters
A couple cheap 8 port TP Link switchesI'm planning on 3 VLANs: one for my devices, server etc; one for guests including my work issued devices and one for my security system & IOT devices. I also plan to use pfBlocker but haven't learned enough about this to know what my DNS address will be etc.
The router will be placed where my phone line enters the building. For best speeds I'll be situating my Unraid server, my TV/Firestick and a powerline adapter. There will be another powerline adapter upstairs plugged into a switch which will give me desktop, projects and a future printer a wired connection. All 3 VLANS must be available with separate SSIDs over the WiFi and all 3 must be connectable over the wired network. I'm Assuming that Ill need a VLAN suitable switch to connect to the pfSense box rather than using the available ports on the quad NIC and that I'll also need one upstairs.
This is the IP scheme Ive come up with. Ive tried to account for all my current devices and allow for some future expansion on each VLAN.
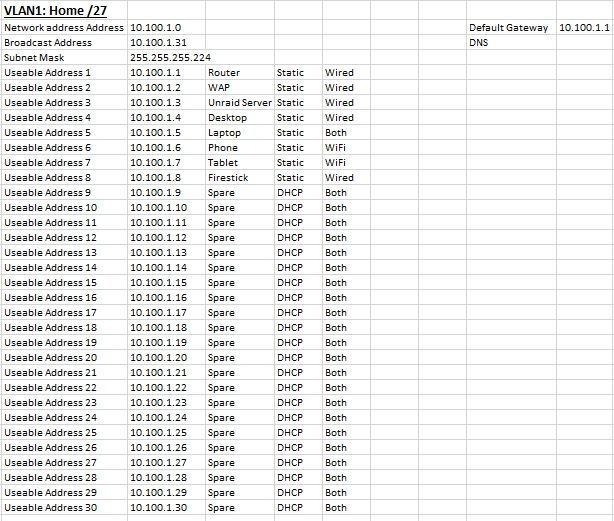
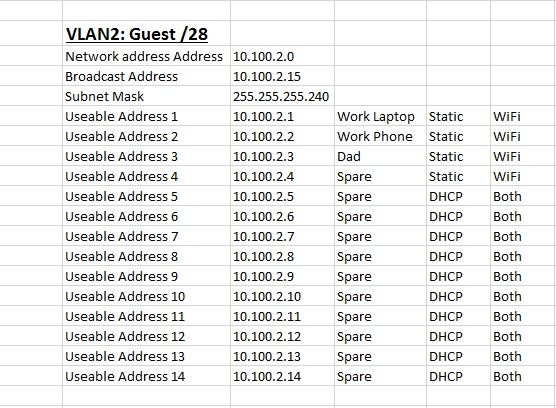
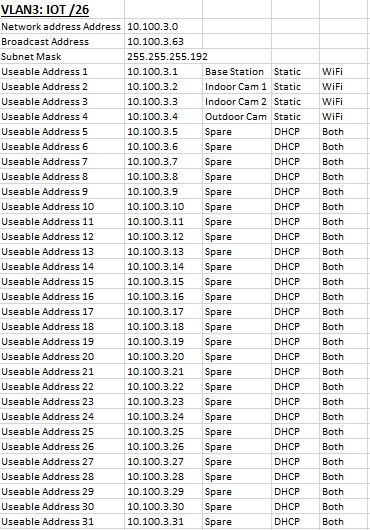
-
@polar_bear88 and what is the question? Dumb switches are not going to be very helpful doing vlans.. Unless your going to create physically isolated networks only.
Your AP can do vlans - you should get switch(es) that can do vlans as well..
-
@johnpoz Sorry, caught enter before Id finished my very long post.
-
@polar_bear88 what is the point of the non /24 masks? I get it if you have only say a /24 to work with... But you have all of rfc1918 to work with. And your already changing the 3rd octet in your different vlans. So why not just use a /24
not sure what the point of using a /27 is?
Still not sure what your question(s) are?
-
The point of using the non /24 was to make them an appropriate size based on the number of devices that I estimate will connect to each of the VLANs.
Main question would be am I right with the design of those IP addresses. Secondary question would be can the devices which are close to the router plug in directly or will I need a VLAN suitable switch as I suspect I will.
If anything seems glaringly wrong with anything else though, please do point it out. I want this all to look correct before I start setting it up so that when something goes wrong (which it inevitably will), i know its because Ive selected a wrong setting or firewall rule etc rather than because Ive used the wrong IP address / subnet.
-
@polar_bear88 said in Subnet / VLAN Design:
them an appropriate size based on the number of devices that I estimate will connect to each of the VLANs.
Why? You have all of 10.x.x.x space to work with... I could see not using a /16, but there is little reason to hinder your own use - /24 in rfc1918 space has almost become standard like /64 in ipv6 space... Unless you have need of larger, there is little reason to use smaller.. Just saying.. It does make it easier to read..
As to right in the design? From what point of view.. I gave you my point of view on the masks your using.
How are they going to connect direct into the router? Does the router have a switch... You said you had only 4 ports - you don't plan on bridging interfaces and try and mimic being a switch? That would be a bad idea.
I brought up first thing - you are more than likely going to want vlan capable switches..
-
@polar_bear88
hey there,
sharing @johnpoz's opinion regarding your subnet masks.
I use /24 for about every subnet. I do not need that many IPs, still...at first I even chose a mask that gave IPs for just as many clients as in use. But then...especially with VLANs, you move devices around after a while, because your first idea did not prove ready for your needs and BAM, you need to change network size again. So now I settled with good old /24, have enough room and pfsense gives IPs to those known clients I use (others will not get IPs).Considering hardware: buy a manged switch with enough ports for your needs, even divide it into two switches if you do not like the huge 48 Port machines. But make sure, it is manged (via web gui for instance) and that your switch knows 802.1 Q...done. :)
-
Thank you both.
Going with the /26, /27 and /28 was just something Id been taught at Uni but Im happy to bow down to those with more real world experience. Ill use a /24 for each of my 3 VLANs.
Next step is to start researching which CISCO switches have POE, VLAN capable and are managed so I can look for them cheap secondhand. Cisco was what I was taught on, I want to try and get my CCNA and in the downstairs location I'm trying to standardise on rack-mountable where possible. For the upstairs location where a smaller form factor is required, I believe a Unifi switch will do. As far as I'm aware, powerline adapters shouldn't affect the VLAN tags?
-
@polar_bear88 said in Subnet / VLAN Design: As far as I'm aware, powerline adapters shouldn't affect the VLAN tags?
Yup correct, power line adaptors won't strip off the tags, I have 3 at home carrying multiple vlans.
-
@polar_bear88 said in Subnet / VLAN Design:
Id been taught at Uni but Im happy to bow down to those with more real world experience.

You have read my signature? Just stumbeling along reading this asking that...thanks to this forum and its users some stuff gets inside my head, no IT pro and no real world experience on my side, just "managing" my homenet...
;) -
@polar_bear88 said in Subnet / VLAN Design:
Going with the /26, /27 and /28 was just something Id been taught at Uni
Not like this wrong.. If you were limited to say a /24 or /23 or something that your company gave you for your location/building etc..
But you have all of rfc1918 space to work with.. You don't have such constraints, so for example I wouldn't suggest you use 10/8 for one vlan and 172.16/12 for another etc.... But in a home setup there is little reason to limit yourself to a /28 hehehe..
With the IPs you showed, I can tell you people would assume /24s on those, since you changed the 3 octet even though your not using a /24 mask..
I agree with your appropriate size for sure - but unless you have constraints on your subnet you have to stay with, realistically /24 has become the really the standard size, even if you only have a handful of devices that will be on that network.. It just that the 3rd octet makes for a really easy to see change when the subnet is different, etc.
As to what switch - I personally would stay away from 2nd hand enterprise gear, unless its for a lab that will only be on part of the time.. They tend to be noisy and power hungry. But if your going to use this as lab and want to practice for your ccna then ok enterprise cisco it is.. But if your just looking to be able to do vlans, you can for sure get a cheaper vlan capable switch..
Why do you think you need poe? Do you plan on adding more poe devices in the future? Your 1 AP is little reason to get a poe switch, just use injector for its power needs..
-
The POE was to save needing to use the POE injector for now and partially wishful thinking. In the future I would love to do some home improvements which include a Node 0, multiple Ethernet ports in each room and multiple wired security cameras so it was to be ready for that. If I'm being honest with myself though by the time I can afford to do that, I can afford to buy a POE switch at the time.
It is a learning experience for me, however its also going to be in use in my sitting room right next to my sofa so noise is an issue. Guess I should be looking at a non enterprise gigabit switch then. I can always get some cheap enterprise stuff purely for a lab at a later date.
-
@polar_bear88 I have some small business cisco sg300s that are fanless etc. and use little power, a 28 and 10 port.. Pretty freaking close to cisco ios, but some differences..
But they are soon eol, and do have my eye on newer stuff - just wish multigig with vlan support wasn't so freaking expensive currently..
Save yourself some noise and power and money and just get something that more suites your current needs and budget.. You can find say 8 port get vlan gig switch for like $40.. Keep in mind your dumb switches can be leveraged off your vlan capable switch when you have devices you all want on the same vlan, etc.