Routing OpenVPN to LAN
-
@irondog
Change the wifi router to be an access point only.
If it doesn't have an AP mode, just turn off the dhcp server, set the IP to an unused IP on the pfSense LAN, and plug it into one of the switchports (might be labeled LAN) instead of the internet port (might be labeled WAN). <- This is all done on the wifi router. -
@jarhead said in Routing OpenVPN to LAN:
@irondog
Change the wifi router to be an access point only.
If it doesn't have an AP mode, just turn off the dhcp server, set the IP to an unused IP on the pfSense LAN, and plug it into one of the switchports (might be labeled LAN) instead of the internet port (might be labeled WAN). <- This is all done on the wifi router.Will this compromise the security and the firewall of the pfSense? I decided to install the pfSense to protect my devices and the NAS behind it and I do not want to compromise it. Thanks for the reply!
-
@irondog As I said in my last line, you aren't doing anything in pfSense.
If you have no reason to have a second subnet in your house, there's no need for a second router.
Keep in mind, "inside" the wifi router is a router ( WAN port and LAN port), a firewall (LAN port of switch connects to the exterior port), a switch (Interior port of firewall connects to it) and an AP which is plugged into the switch with any spare ports exposed to you. You only need to use the AP. So not using the WAN removes the router and firewall. -
@jarhead said in Routing OpenVPN to LAN:
@irondog As I said in my last line, you aren't doing anything in pfSense.
If you have no reason to have a second subnet in your house, there's no need for a second router.
Keep in mind, "inside" the wifi router is a router ( WAN port and LAN port), a firewall (LAN port of switch connects to the exterior port), a switch (Interior port of firewall connects to it) and an AP which is plugged into the switch with any spare ports exposed to you. You only need to use the AP. So not using the WAN removes the router and firewall.is there any difference if I connect the wifi router in AP mode directly to the ISP modem rather than the pfSense appliance in terms of security? in other words, is the way you connect the hardware influences the security of the network as I might be inclined to think? my feeling is that the double NAT is more secure than this new setup, but I do not have enough knowledge to confirm it or not. That's why I was thinking a routing of the OpenVPN clients was my first choice....
-
@irondog pfSense is your first, and best, line of defence, and anything connected outside of it (directly to the modem) is unprotected and completely on it's own.
You can think of your wifi-router as having two sides, when operating as a router... The WAN port represents the outside, and the LAN side is made up of wired (only 4) AND wireless connections (many), all of them connected through the internal switch.
Between WAN and LAN is the routers' built in firewall, which was being used when you used it as a router. This was also the problem in your initial setup since the switch side (LAN) needs to use different IP's than the WAN side.
When you turn it into an AP, you stop using the WAN port and the firewall completely and you turn it into a switch instead (with wireless capabilities). However, it is still quite smart so you need to turn off some of that, like DHCP. Otherwise it will create conflicts with pfsense. You also need to give it a new IP address to access it's UI, and it has to be in the same IP range as your pfsense.
-
@jarhead said in Routing OpenVPN to LAN:
@irondog
Change the wifi router to be an access point only.
If it doesn't have an AP mode, just turn off the dhcp server, set the IP to an unused IP on the pfSense LAN, and plug it into one of the switchports (might be labeled LAN) instead of the internet port (might be labeled WAN). <- This is all done on the wifi router.Hi, I have tried to do as suggested (wifi router has been moved to AP mode, connected pfSense and wifi router with a LAN port instead of WAN) however this was not successfull, the wifi router didn't get any access to the internet from the pfSense resulting in a useless system. I had to restore everything. I suspect there is some sort of DHCP conflict.
As of now, the ISP router has its own DHCP activated, pfSsense also (I suppose), what is the right configuration to make it functioning? thanks! -
@irondog Ok, as I read it you have pfsense set up pretty much default in this regard, which means DHCP is active.
-
Connected to your pfsense, log in and go to Services > DHCP Server and look for the item called Range.
Check that it reads something like 192.168.1.100 and 192.168.1.199
This means that you can use anything outside of that range for any devices that you want to have a Static IP (like your wifirouter). -
Now connect to and log in to your wifirouter (what model is it btw?), and find the basic Network settings where you see the IP address you used in the web browser to log in.
2.1 First, check again to make sure the DHCP Server is turned off. It should be greyed out or empty. If not turn it off...
2.2. Now change the IP address of the router to 192.168.1.10 or something where the last number is unique and not 1 since that is owned by pfsense now. Click save and the router will likely reboot automatically. -
Make sure the LAN cable goes from pfsense LAN > wifi router LAN (not WAN). And connect your PC to any of the other LAN ports on the wifi router. To simplify things, you could place a switch in between so you don't have to move cables around. Connect pfsense LAN > switch and then connect both your PC and wifi router (LAN port) to that switch.
-
You should now be able to log in to pfsense using 192.168.1.1 AND to your wifi router on 192.168.1.10.
-
-
@irondog said in Routing OpenVPN to LAN:
@jarhead said in Routing OpenVPN to LAN:
@irondog
Change the wifi router to be an access point only.
If it doesn't have an AP mode, just turn off the dhcp server, set the IP to an unused IP on the pfSense LAN, and plug it into one of the switchports (might be labeled LAN) instead of the internet port (might be labeled WAN). <- This is all done on the wifi router.Hi, I have tried to do as suggested (wifi router has been moved to AP mode, connected pfSense and wifi router with a LAN port instead of WAN) however this was not successfull, the wifi router didn't get any access to the internet from the pfSense resulting in a useless system. I had to restore everything. I suspect there is some sort of DHCP conflict.
As of now, the ISP router has its own DHCP activated, pfSsense also (I suppose), what is the right configuration to make it functioning? thanks!So you are back on the setup of your initial port, I assume.
To make things easy, simply add a static route to pfSense for the network behind the wifi router.
Go to System > Routing > Gateways and add a new gateway. Select LAN interface, state a name of your choice and enter the wifi routers WAN IP. Save it.
Go to the Static Routes tab, add a new one. At network enter 192.168.0.0/24 (wifi subnet) and select the gateway you have added in the step above, state a description and save it.
Your wifi devices should be reachable from the VPN then (from the point of pfSense).But consider that you may have to allow the access also on the wifi router (other than in AP mode) and that the devices may block access from outside. So you will habe to allow the access on the wifi devices as well or configure masquerading on the wifi router.
-
@viragomann said in Routing OpenVPN to LAN:
So you are back on the setup of your initial port, I assume.
To make things easy, simply add a static route to pfSense for the network behind the wifi router.
Go to System > Routing > Gateways and add a new gateway. Select LAN interface, state a name of your choice and enter the wifi routers WAN IP. Save it.
Go to the Static Routes tab, add a new one. At network enter 192.168.0.0/24 (wifi subnet) and select the gateway you have added in the step above, state a description and save it.
Your wifi devices should be reachable from the VPN then (from the point of pfSense).But consider that you may have to allow the access also on the wifi router (other than in AP mode) and that the devices may block access from outside. So you will habe to allow the access on the wifi devices as well or configure masquerading on the wifi router.
I don't think that is the issue. The first post clearly indicates that the VPN tunnel works as expected, since the 192.168.1.0/24 network (pfsense) is available. The issue is that the wifi-router was connected (as a router) via it's WAN port, to that same network. There is no way to get through that way.
So the suggestion is to make the wifi-router into a simple AP, only using it's switching and wifi capabilities. -
@gblenn
No, in his first post, which I referred to, he mentioned, the wifi is connected to pfSense LAN.Anyway, also if the wifi was connected to WAN it would be possible. Same way, but masquerading on pfSense would be necessary.
But yeah, I agree that setting the wifi into AP mode is best practice to achieve what he intend, but sadly he has obviously trouble setting that up properly.
-
@gblenn said in Routing OpenVPN to LAN:
So the suggestion is to make the wifi-router into a simple AP, only using it's switching and wifi capabilities.
as he described in his 1st post
A wifi router is connected to the pfSense LAN itnerface to which all the home devices are connected in.
the suggestion ist TRUE turn that "wifi router" into an dumb access point served by everything on the IP side needed by pfS (DNS / Gateway / NTP / IP /) and let everything else handle pfS for the clients (dhcp / DNS )
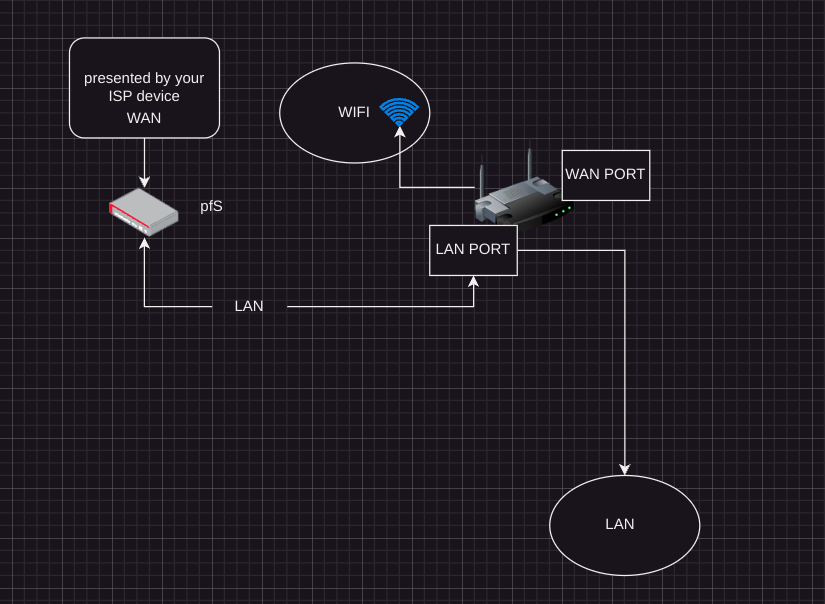
-
@viragomann said in Routing OpenVPN to LAN:
@gblenn
No, in his first post, which I referred to, he mentioned, the wifi is connected to pfSense LAN.Anyway, also if the wifi was connected to WAN it would be possible. Same way, but masquerading on pfSense would be necessary.
But yeah, I agree that setting the wifi into AP mode is best practice to achieve what he intend, but sadly he has obviously trouble setting that up properly.
Precisely, the wifi-router is and should be connected to pfsense LAN. I suppose the whole idea with pfsense here, was to take that step up in the world, away from a simple wifi-router...
BUT the cable shouldn't go to the wifi-routers WAN port, it should go into the LAN port. Just that DHCP needs to be disabled on the wifi-router and the LAN IP needs to be changed on it as well.
-
yep should do the trick ...
set wifi thing (tha router) to dhcp and disable router function)
turn dhcp on pfS on
cable from lan pfS to lan wifi thing (if there is no LAN port use WAN but disable router function first) -
@gblenn said in Routing OpenVPN to LAN:
@irondog Ok, as I read it you have pfsense set up pretty much default in this regard, which means DHCP is active.
-
Connected to your pfsense, log in and go to Services > DHCP Server and look for the item called Range.
Check that it reads something like 192.168.1.100 and 192.168.1.199
This means that you can use anything outside of that range for any devices that you want to have a Static IP (like your wifirouter). -
Now connect to and log in to your wifirouter (what model is it btw?), and find the basic Network settings where you see the IP address you used in the web browser to log in.
2.1 First, check again to make sure the DHCP Server is turned off. It should be greyed out or empty. If not turn it off...
2.2. Now change the IP address of the router to 192.168.1.10 or something where the last number is unique and not 1 since that is owned by pfsense now. Click save and the router will likely reboot automatically. -
Make sure the LAN cable goes from pfsense LAN > wifi router LAN (not WAN). And connect your PC to any of the other LAN ports on the wifi router. To simplify things, you could place a switch in between so you don't have to move cables around. Connect pfsense LAN > switch and then connect both your PC and wifi router (LAN port) to that switch.
-
You should now be able to log in to pfsense using 192.168.1.1 AND to your wifi router on 192.168.1.10.
Thanks I will try this evening. What about the ISP modem router? it also has DHCP.... wifi router is the TP LINK AX50. Thanks again!
-
-
ISP Modem delivers dhcp to your pfS wan interface
Do not use the same ip Adress range on your Lan pfS interface
Worst case you got 2x NAT for starters but everything will work out of the box
-
@irondog If the ISP modem has the ability to do "bridging" then I suggest you set it up like that. This means that it will simply pass thru the WAN to one (probably specific) LAN port. Check the manual for that, but that would be your best option.
Alternatively, as @noplan said, set a different IP (192.168.10.1) on it, so that the WAN on pfsense is different. The next thing could be to make sure pfsense is getting a Static IP (also set in the ISP device). Finally, find a setting under NAT, Security or Firewall which is called DMZ and set the IP to point at pfsense. This will open up the ISP router so it interferes as little as possible.
-
@irondog said in Routing OpenVPN to LAN:
wifi router is the TP LINK AX50. Thanks again!
First, to disable the DHCP server go to Advanced > Network > DHCP and uncheck the box
Second, to change the IP on the LAN side, go to Advanced > Network > LAN
Type in the IP as in my instructions and click Save. That should do it... -
@gblenn thanks will try during the weekend and let you know!
-
Dear all, tried this weekend and everything is working perfectly!
Only one thing was not working correctly was the pfSense WAN IPv4 configuration type that for some reason was set to none (I had no internet from the wifi router LAN) but figured out by myself how to fix putting DHCP.
Thanks everyone for the the help, very much appreciated! -
cool !