Whack-a-mole with DigitalOcean "ET COMPROMISED Known Compromised or Hostile Host Traffic group"
-
@drewsaur said in Whack-a-mole with DigitalOcean "ET COMPROMISED Known Compromised or Hostile Host Traffic group":
I'm still unsure what happened that prompted those IP addresses to re-appear in the Block tab with no new activity?
If it shows up on the BLOCKS tab, then it is resident in the snort2c table and is being blocked. However, it is possible for the
alerts.logfile for the interface to get rotated if it grows beyond the size limit set in LOGS MGMT. Depending on the timing of the rotation, the last alert for that IP might have been "lost" with the rotation as the PHP code only looks in the active log file for that matching alert data. It will not open up and search through any rotated logs. -
@bmeeks I neglected to add that I downloaded the complete set of gzipped logs and did not find the IP address in any of the log files... EDIT-for recent dates.
-
@drewsaur said in Whack-a-mole with DigitalOcean "ET COMPROMISED Known Compromised or Hostile Host Traffic group":
@bmeeks I neglected to add that I downloaded the complete set of gzipped logs and did not find the IP address in any of the log files.
Well, you have a genuine mystery there
 . The BLOCKS tab is populated by dumping the content of the snort2c table using a call to the
. The BLOCKS tab is populated by dumping the content of the snort2c table using a call to the pfctlutility. Did you check the logs for BOTH the WAN and LAN interfaces? They will be located in different subdirectories under/var/log/suricata/-- or alternately, select the other interface for viewing on the ALERTS tab. -
@bmeeks I was imprecise/incorrect/wrong. I am sorry. But I am still confused. Please take a look at the screenshot for this recent entry, and there is no entry in there for any point in time after I cleared the BLOCK.
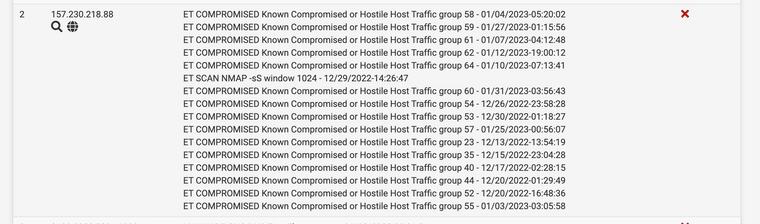
...but there is indeed one entry for 2/1 in the downloaded alert logs (the 5th line) - so my broader question is, why won't that show up in blocks, since it is in the recent alerts for Suricata?
~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log:7855: 01/30/2023-10:15:34.559449 [wDrop] [**] [1:2500118:6422] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:40111 -> 172.XXX.YYY.ZZZ:16643 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log:17292: 01/31/2023-03:56:43.082414 [wDrop] [**] [1:2500118:6422] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:54140 -> 172.XXX.YYY.ZZZ:17444 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log:20447: 01/31/2023-10:06:27.265881 [wDrop] [**] [1:2009582:3] ET SCAN NMAP -sS window 1024 [**] [Classification: Attempted Information Leak] [Priority: 2] {TCP} 157.230.218.88:48112 -> 172.XXX.YYY.ZZZ:17952 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log:20448: 01/31/2023-10:06:27.265881 [wDrop] [**] [1:2500110:6425] ET COMPROMISED Known Compromised or Hostile Host Traffic group 56 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:48112 -> 172.XXX.YYY.ZZZ:17952 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log:37733: 02/01/2023-14:07:01.426232 [wDrop] [**] [1:2500104:6426] ET COMPROMISED Known Compromised or Hostile Host Traffic group 53 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:42058 -> 172.XXX.YYY.ZZZ:6864 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0102_1850:7911: 12/31/2022-08:49:47.522758 [wDrop] [**] [1:2500108:6394] ET COMPROMISED Known Compromised or Hostile Host Traffic group 55 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:51772 -> 172.XXX.YYY.ZZZ:2291 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0102_1850:21882: 01/01/2023-07:44:33.927280 [wDrop] [**] [1:2500108:6395] ET COMPROMISED Known Compromised or Hostile Host Traffic group 55 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:45695 -> 172.XXX.YYY.ZZZ:18900 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0102_1850:31528: 01/02/2023-00:42:59.349828 [wDrop] [**] [1:2500108:6395] ET COMPROMISED Known Compromised or Hostile Host Traffic group 55 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:59630 -> 172.XXX.YYY.ZZZ:1198 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0102_1850:34807: 01/02/2023-06:51:22.749561 [wDrop] [**] [1:2500108:6395] ET COMPROMISED Known Compromised or Hostile Host Traffic group 55 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:53557 -> 172.XXX.YYY.ZZZ:27507 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0105_1840:6404: 01/03/2023-03:05:58.258363 [wDrop] [**] [1:2500108:6395] ET COMPROMISED Known Compromised or Hostile Host Traffic group 55 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:47474 -> 172.XXX.YYY.ZZZ:26050 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0105_1840:20983: 01/04/2023-05:20:02.234341 [wDrop] [**] [1:2500114:6398] ET COMPROMISED Known Compromised or Hostile Host Traffic group 58 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:41377 -> 172.XXX.YYY.ZZZ:17470 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0105_1840:39248: 01/05/2023-13:54:11.503500 [wDrop] [**] [1:2500116:6399] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:55242 -> 172.XXX.YYY.ZZZ:30893 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0108_1900:4959: 01/06/2023-04:02:51.876168 [wDrop] [**] [1:2500116:6399] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:49114 -> 172.XXX.YYY.ZZZ:23342 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0108_1900:19583: 01/07/2023-04:12:48.257136 [wDrop] [**] [1:2500120:6400] ET COMPROMISED Known Compromised or Hostile Host Traffic group 61 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:42988 -> 172.XXX.YYY.ZZZ:20070 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0108_1900:23257: 01/07/2023-11:13:27.541541 [wDrop] [**] [1:2500122:6401] ET COMPROMISED Known Compromised or Hostile Host Traffic group 62 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:56871 -> 172.XXX.YYY.ZZZ:12818 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0108_1900:34288: 01/08/2023-06:04:25.770401 [wDrop] [**] [1:2500122:6401] ET COMPROMISED Known Compromised or Hostile Host Traffic group 62 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:50776 -> 172.XXX.YYY.ZZZ:21399 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0111_1520:6895: 01/09/2023-07:56:21.322000 [wDrop] [**] [1:2500122:6401] ET COMPROMISED Known Compromised or Hostile Host Traffic group 62 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:44664 -> 172.XXX.YYY.ZZZ:4337 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0111_1520:22798: 01/10/2023-07:13:41.997930 [wDrop] [**] [1:2500126:6404] ET COMPROMISED Known Compromised or Hostile Host Traffic group 64 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:58572 -> 172.XXX.YYY.ZZZ:26850 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0111_1520:32792: 01/10/2023-22:32:31.896060 [wDrop] [**] [1:2009582:3] ET SCAN NMAP -sS window 1024 [**] [Classification: Attempted Information Leak] [Priority: 2] {TCP} 157.230.218.88:52466 -> 172.XXX.YYY.ZZZ:27478 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0111_1520:32793: 01/10/2023-22:32:31.896060 [wDrop] [**] [1:2500126:6404] ET COMPROMISED Known Compromised or Hostile Host Traffic group 64 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:52466 -> 172.XXX.YYY.ZZZ:27478 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0114_1905:7969: 01/12/2023-05:06:58.982523 [wDrop] [**] [1:2500122:6406] ET COMPROMISED Known Compromised or Hostile Host Traffic group 62 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:46355 -> 172.XXX.YYY.ZZZ:30075 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0114_1905:16062: 01/12/2023-19:00:12.154489 [wDrop] [**] [1:2500122:6406] ET COMPROMISED Known Compromised or Hostile Host Traffic group 62 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:40263 -> 172.XXX.YYY.ZZZ:31361 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0114_1905:31490: 01/13/2023-23:31:10.836267 [wDrop] [**] [1:2500118:6407] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:54151 -> 172.XXX.YYY.ZZZ:17007 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0118_0100:2791: 01/14/2023-22:55:36.274855 [wDrop] [**] [1:2500116:6408] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:48187 -> 172.XXX.YYY.ZZZ:9851 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0118_0100:9077: 01/15/2023-11:10:53.995156 [wDrop] [**] [1:2500116:6408] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:42213 -> 172.XXX.YYY.ZZZ:25316 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0118_0100:16059: 01/16/2023-01:00:12.017811 [wDrop] [**] [1:2500116:6408] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:56160 -> 172.XXX.YYY.ZZZ:7111 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0118_0100:29776: 01/17/2023-06:07:38.327039 [wDrop] [**] [1:2500106:6411] ET COMPROMISED Known Compromised or Hostile Host Traffic group 54 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:50114 -> 172.XXX.YYY.ZZZ:13139 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0121_0335:2994: 01/18/2023-07:17:44.033972 [wDrop] [**] [1:2009582:3] ET SCAN NMAP -sS window 1024 [**] [Classification: Attempted Information Leak] [Priority: 2] {TCP} 157.230.218.88:44065 -> 172.XXX.YYY.ZZZ:5094 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0121_0335:2995: 01/18/2023-07:17:44.033972 [wDrop] [**] [1:2500104:6412] ET COMPROMISED Known Compromised or Hostile Host Traffic group 53 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:44065 -> 172.XXX.YYY.ZZZ:5094 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0121_0335:7930: 01/18/2023-18:17:42.120452 [wDrop] [**] [1:2500104:6412] ET COMPROMISED Known Compromised or Hostile Host Traffic group 53 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:58016 -> 172.XXX.YYY.ZZZ:7984 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0121_0335:20546: 01/19/2023-14:12:07.668423 [wDrop] [**] [1:2500104:6413] ET COMPROMISED Known Compromised or Hostile Host Traffic group 53 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:51990 -> 172.XXX.YYY.ZZZ:10112 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0121_0335:35681: 01/20/2023-15:44:40.846356 [wDrop] [**] [1:2500104:6414] ET COMPROMISED Known Compromised or Hostile Host Traffic group 53 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:45956 -> 172.XXX.YYY.ZZZ:21896 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0124_0730:7307: 01/21/2023-16:52:07.747769 [wDrop] [**] [1:2500106:6415] ET COMPROMISED Known Compromised or Hostile Host Traffic group 54 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:59892 -> 172.XXX.YYY.ZZZ:26776 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0124_0730:20267: 01/22/2023-15:15:55.623257 [wDrop] [**] [1:2500106:6415] ET COMPROMISED Known Compromised or Hostile Host Traffic group 54 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:53830 -> 172.XXX.YYY.ZZZ:32758 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0124_0730:22579: 01/22/2023-19:23:22.259195 [wDrop] [**] [1:2500106:6415] ET COMPROMISED Known Compromised or Hostile Host Traffic group 54 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:47781 -> 172.XXX.YYY.ZZZ:2359 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0127_0145:120: 01/24/2023-07:39:51.995682 [wDrop] [**] [1:2500112:6418] ET COMPROMISED Known Compromised or Hostile Host Traffic group 57 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:41844 -> 172.XXX.YYY.ZZZ:12784 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0127_0145:12155: 01/25/2023-00:56:07.901411 [wDrop] [**] [1:2500112:6418] ET COMPROMISED Known Compromised or Hostile Host Traffic group 57 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:55867 -> 172.XXX.YYY.ZZZ:17380 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0127_0145:19197: 01/25/2023-12:22:18.497529 [wDrop] [**] [1:2500116:6419] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:49890 -> 172.XXX.YYY.ZZZ:17148 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0127_0145:37592: 01/26/2023-16:46:07.541188 [wDrop] [**] [1:2500116:6420] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:43919 -> 172.XXX.YYY.ZZZ:21306 ~/Downloads/suricata_logs_2023-02-01-15-11-53_igb0/alerts.log.2023_0127_0145:42721: 01/27/2023-01:15:56.706231 [wDrop] [**] [1:2500116:6420] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [**] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:57891 -> 172.XXX.YYY.ZZZ:9270 -
@drewsaur said in Whack-a-mole with DigitalOcean "ET COMPROMISED Known Compromised or Hostile Host Traffic group":
...but there is indeed one entry for 2/1 in the downloaded alert logs (the 5th line) - so my broader question is, why won't that show up in blocks, since it is in the recent alerts for Suricata?
First, just because an IP address is listed in the alert log does not automatically mean it must have been blocked. What IP is blocked in a conversation between two hosts is governed by two settings. First, there is the Pass List logic. If the IP address is part of a Pass List, it will not be blocked but will generate an alert. The second setting that determines whether or not an IP is blocked is the setting on the INTERFACE SETTINGS tab for which IP in a conversation to block. That parameter can be set to SRC (source), DST (destination), or BOTH (both source and destination IP will be blocked). But the Pass List logic still is primary, so if the IP is on a Pass List it will never be blocked no matter what the setting on the INTERFACE SETTINGS tab is configured for.
In your case I don't expect that IP was part of a Pass List, so that logic would not matter here.
When did you clear the blocks using the GUI button on the BLOCKS tab? Was it today, or on some earlier day? If today, what specific time? That matters because of the setting discussed below.
Do you have the "Remove Blocked Hosts" cron task enabled on the GLOBAL SETTINGS tab? If so, what interval is selected there? That task, when executed, automatically removes blocked hosts from the snort2c table if the host has not been seen as either the source or destination of new traffic since the last time the cron task executed. So for example, if the task is set to run every hour, it will clear all IPs from the table that have not seen additional traffic over the last hour. But that will not remove them from the alerts log. Once there, they stay in there.
-
@bmeeks said in Whack-a-mole with DigitalOcean "ET COMPROMISED Known Compromised or Hostile Host Traffic group":
@drewsaur said in Whack-a-mole with DigitalOcean "ET COMPROMISED Known Compromised or Hostile Host Traffic group":
...but there is indeed one entry for 2/1 in the downloaded alert logs (the 5th line) - so my broader question is, why won't that show up in blocks, since it is in the recent alerts for Suricata?
First, just because an IP address is listed in the alert log does not automatically mean it must have been blocked. What IP is blocked in a conversation between two hosts is governed by two settings. First, there is the Pass List logic. If the IP address is part of a Pass List, it will not be blocked but will generate an alert. The second setting that determines whether or not an IP is blocked is the setting on the INTERFACE SETTINGS tab for which IP in a conversation to block. That parameter can be set to SRC (source), DST (destination), or BOTH (both source and destination IP will be blocked). But the Pass List logic still is primary, so if the IP is on a Pass List it will never be blocked no matter what the setting on the INTERFACE SETTINGS tab is configured for.
In your case I don't expect that IP was part of a Pass List, so that logic would not matter here.
Correct.
When did you clear the blocks using the GUI button on the BLOCKS tab? Was it today, or on some earlier day? If today, what specific time? That matters because of the setting discussed below.
Yesterday morning (1/31).
Do you have the "Remove Blocked Hosts" cron task enabled on the GLOBAL SETTINGS tab? If so, what interval is selected there? That task, when executed, automatically removes blocked hosts from the snort2c table if the host has not been seen as either the source or destination of new traffic since the last time the cron task executed. So for example, if the task is set to run every hour, it will clear all IPs from the table that have not seen additional traffic over the last hour. But that will not remove them from the alerts log. Once there, they stay in there.
I have that set to 3 hours. But...why do the older listings still show up in blocks, but not my brand new one(s)?
-
Scratch part of what I said earlier about correlating
alerts.logwith the contents of snort2c. For Suricata, it actually uses theblocks.logfile instead of thealerts.log. I was thinking of how Snort works instead of Suricata. The custom binary plugin used in Suricata works slightly differently and writes ablocks.logfile for each interface.So go look at the contents of that file instead of
alerts.log. The same rules about log rotation will apply.Sorry about that. I confused Snort with Suricata.
-
@bmeeks said in Whack-a-mole with DigitalOcean "ET COMPROMISED Known Compromised or Hostile Host Traffic group":
Scratch part of what I said earlier about correlating
alerts.logwith the contents of snort2c. For Suricata, it actually uses theblocks.logfile instead of thealerts.log. I was thinking of how Snort works instead of Suricata. The custom binary plugin used in Suricata works slightly differently and writes ablocks.logfile for each interface.So go look at the contents of that file instead of
alerts.log. The same rules about log rotation will apply.Sorry about that. I confused Snort with Suricata.
The logs I have been looking at are the ones that I get from pressing the "Download" button on the alerts tab. Are those the wrong ones? (EDIT: I see, they are indeed the "wrong" ones. Please hold.)
-
@bmeeks That too, shows an attack on 2/1, as well as the 1/31 attack that is displayed in my screen shot:
01/31/2023-03:56:43.082414 [Block Src] [] [1:2500118:6422] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:54140
01/31/2023-03:56:43.082414 [Block Src] [] [1:2500118:6422] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:54140
02/01/2023-14:07:01.426232 [Block Src] [] [1:2500104:6426] ET COMPROMISED Known Compromised or Hostile Host Traffic group 53 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:42058
Here are all the attacks from that IP address listed in the block file:
8:32: 01/04/2023-05:20:02.234341 [Block Src] [] [1:2500114:6398] ET COMPROMISED Known Compromised or Hostile Host Traffic group 58 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:41377
8:1225: 01/05/2023-13:54:11.503500 [Block Src] [] [1:2500116:6399] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:55242
8:1717: 01/06/2023-04:02:51.876168 [Block Src] [] [1:2500116:6399] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:49114
8:2582: 01/07/2023-04:12:48.257136 [Block Src] [] [1:2500120:6400] ET COMPROMISED Known Compromised or Hostile Host Traffic group 61 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:42988
8:2824: 01/07/2023-11:13:27.541541 [Block Src] [] [1:2500122:6401] ET COMPROMISED Known Compromised or Hostile Host Traffic group 62 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:56871
8:3505: 01/08/2023-06:04:25.770401 [Block Src] [] [1:2500122:6401] ET COMPROMISED Known Compromised or Hostile Host Traffic group 62 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:50776
8:4315: 01/09/2023-07:56:21.322000 [Block Src] [] [1:2500122:6401] ET COMPROMISED Known Compromised or Hostile Host Traffic group 62 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:44664
8:5170: 01/10/2023-07:13:41.997930 [Block Src] [] [1:2500126:6404] ET COMPROMISED Known Compromised or Hostile Host Traffic group 64 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:58572
8:5706: 01/10/2023-22:32:31.896060 [Block Src] [] [1:2009582:3] ET SCAN NMAP -sS window 1024 [] [Classification: Attempted Information Leak] [Priority: 2] {TCP} 157.230.218.88:52466
8:6709: 01/12/2023-05:06:58.982523 [Block Src] [] [1:2500122:6406] ET COMPROMISED Known Compromised or Hostile Host Traffic group 62 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:46355
8:7125: 01/12/2023-19:00:12.154489 [Block Src] [] [1:2500122:6406] ET COMPROMISED Known Compromised or Hostile Host Traffic group 62 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:40263
8:8110: 01/13/2023-23:31:10.836267 [Block Src] [] [1:2500118:6407] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:54151
8:8925: 01/14/2023-22:55:36.274855 [Block Src] [] [1:2500116:6408] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:48187
8:9320: 01/15/2023-11:10:53.995156 [Block Src] [] [1:2500116:6408] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:42213
8:9815: 01/16/2023-01:00:12.017811 [Block Src] [] [1:2500116:6408] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:56160
8:10775: 01/17/2023-06:07:38.327039 [Block Src] [] [1:2500106:6411] ET COMPROMISED Known Compromised or Hostile Host Traffic group 54 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:50114
8:11657: 01/18/2023-07:17:44.033972 [Block Src] [] [1:2009582:3] ET SCAN NMAP -sS window 1024 [] [Classification: Attempted Information Leak] [Priority: 2] {TCP} 157.230.218.88:44065
8:11989: 01/18/2023-18:17:42.120452 [Block Src] [] [1:2500104:6412] ET COMPROMISED Known Compromised or Hostile Host Traffic group 53 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:58016
8:12605: 01/19/2023-14:12:07.668423 [Block Src] [] [1:2500104:6413] ET COMPROMISED Known Compromised or Hostile Host Traffic group 53 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:51990
8:13433: 01/20/2023-15:44:40.846356 [Block Src] [] [1:2500104:6414] ET COMPROMISED Known Compromised or Hostile Host Traffic group 53 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:45956
8:14221: 01/21/2023-16:52:07.747769 [Block Src] [] [1:2500106:6415] ET COMPROMISED Known Compromised or Hostile Host Traffic group 54 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:59892
8:14934: 01/22/2023-15:15:55.623257 [Block Src] [] [1:2500106:6415] ET COMPROMISED Known Compromised or Hostile Host Traffic group 54 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:53830
8:15087: 01/22/2023-19:23:22.259195 [Block Src] [] [1:2500106:6415] ET COMPROMISED Known Compromised or Hostile Host Traffic group 54 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:47781
8:16291: 01/24/2023-07:39:51.995682 [Block Src] [] [1:2500112:6418] ET COMPROMISED Known Compromised or Hostile Host Traffic group 57 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:41844
8:16809: 01/25/2023-00:56:07.901411 [Block Src] [] [1:2500112:6418] ET COMPROMISED Known Compromised or Hostile Host Traffic group 57 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:55867
8:17153: 01/25/2023-12:22:18.497529 [Block Src] [] [1:2500116:6419] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:49890
8:17966: 01/26/2023-16:46:07.541188 [Block Src] [] [1:2500116:6420] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:43919
8:18250: 01/27/2023-01:15:56.706231 [Block Src] [] [1:2500116:6420] ET COMPROMISED Known Compromised or Hostile Host Traffic group 59 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:57891
8:19419: 01/28/2023-17:01:25.391222 [Block Src] [] [1:2500118:6422] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:51903
8:19708: 01/29/2023-02:23:54.703570 [Block Src] [] [1:2500118:6422] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:46046
8:20737: 01/30/2023-10:15:34.559449 [Block Src] [] [1:2500118:6422] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:40111
8:21306: 01/31/2023-03:56:43.082414 [Block Src] [] [1:2500118:6422] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:54140
8:21520: 01/31/2023-03:56:43.082414 [Block Src] [] [1:2500118:6422] ET COMPROMISED Known Compromised or Hostile Host Traffic group 60 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:54140
8:22365: 02/01/2023-14:07:01.426232 [Block Src] [] [1:2500104:6426] ET COMPROMISED Known Compromised or Hostile Host Traffic group 53 [] [Classification: Misc Attack] [Priority: 2] {TCP} 157.230.218.88:42058 -
@bmeeks Also, here is the latest state of that entry in the Blocks GUI - still no entry for 2/1:
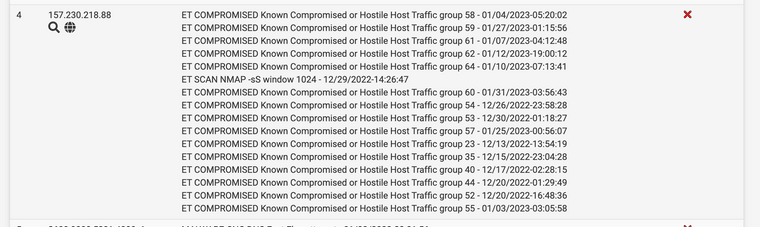
-
Sorry for the delayed reply. Had to step away for a few hours for another commitment.
If I understand your question, you see the 157.230.218.88 IP address as being blocked since it is listed in the BLOCKS tab list. But you are wondering why there is no separate entry under that list of associated rule alerts on the BLOCKS tab for a triggered alert on 02/01/2023.
I don't have an exact answer for that because I don't have your log files to examine, but one possibility is that particular line could contain an error such that the PHP code that parses it with a regex into discrete fields is not coming up with the required number of unique fields for that line. If that condition is hit, the code throws away the offending line. You can examine the PHP code in the file
/usr/local/www/suricata/suricata_blocked.phpbeginning around line 298 to see how that process works.The listing under each blocked IP is just a convenience display. An entry missing there is not critically important. If the IP is in the BLOCKS tab list, it is currently being blocked. The block is what matters. If you truly need to know which rule caused it, look on the ALERTS tab. If you want to disable the rule or suppress future alerts, you must do that on the ALERTS tab anyway.
-
@bmeeks Thank you so much. I did send you the full log separately. Please let me know if I can get you anything else. And you needn’t do any more. I’m more than happy with what I’ve learned. Cheers!
-
@bmeeks Just in case anyone following this cares :), I am now only running port scan rules on my WAN interface, and leaving everything else in my LAN interface.
This was easy to do because I run everything from SID files, so I just downloaded my custom Enable and Disable files, copied them as "EnableWAN" and "DisableWAN," whittled down the contents from each that pertained to "emerging-scan"...configured them in the List Assignments area, clicked the Rebuild boxes, hit Save, and I was off to the races.
Only extra thing I had to do was in the "WAN Categories" tab - I had to hit "Unselect All" and "Save" to disable the (now-manually-checked remnant) rulesets that had been previously enabled by the old SID files. The one category in my "EnableWAN" file stayed enabled with the special little "A" icon.
Everything really is much more "sane" now - I am getting the port scanning protection I want on the WAN; I have more sane "Blocks"; and I have better Alert information logs for the LAN.
All that, and using much less RAM (usually was running at 31-35%; now at 21-22%)
Thanks again!
-
S SteveITS referenced this topic on