CVE-2023-0056 & CVE-2023-25725 (critical) - haproxy upgrade to 2.2.29 ?
-
Answering to myself :
The workaround can be put in the "Advanced Pass Thru" field of the Frontends definitions. (repeat for all frontends)
http-request deny if { fc_http_major 1 } !{ req.body_size 0 } !{ req.hdr(content-length) -m found } !{ req.hdr(transfer-encoding) -m found } !{ method CONNECT }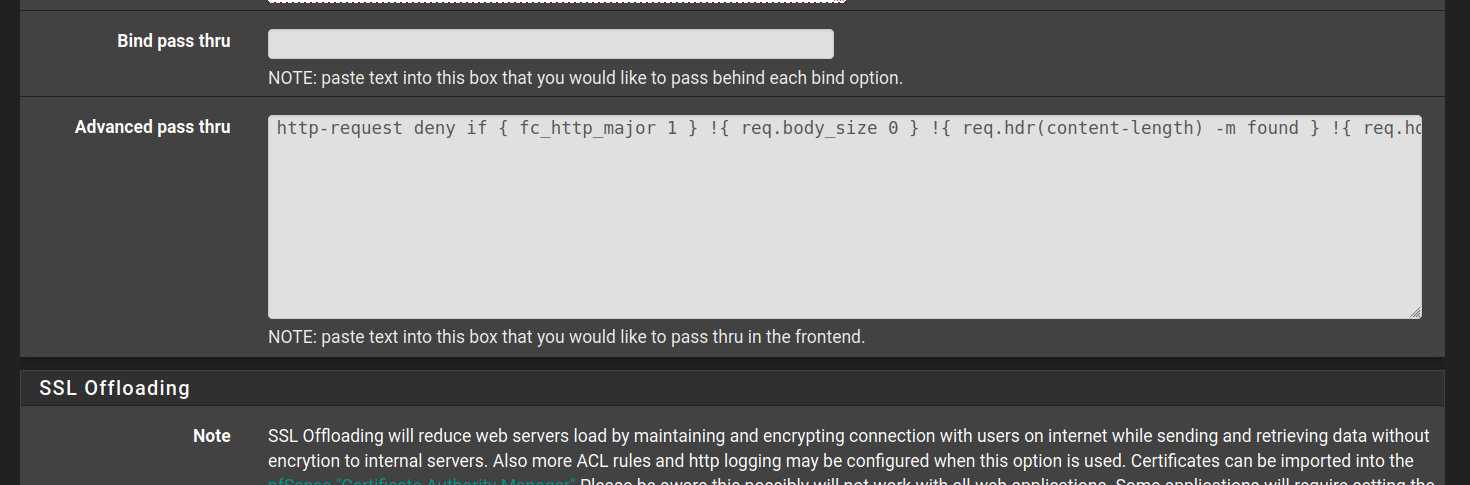
-
@myster_fr said in CVE-2023-0056 & CVE-2023-25725 (critical) - haproxy upgrade to 2.2.29 ?:
http-request deny if { fc_http_major 1 } !{ req.body_size 0 } !{ req.hdr(content-length) -m found } !{ req.hdr(transfer-encoding) -m found } !{ method CONNECT }
thans for posting this.
-
Thank you for the workaround!
It would still be nice to know from Netgate if and when they're going to update the HAproxy package -
We're working on pulling in the patched version of haproxy, it should be available soon.
The workaround should be OK for now.
There is a more detailed list of affected versions in the announcement on the haproxy mailing list:
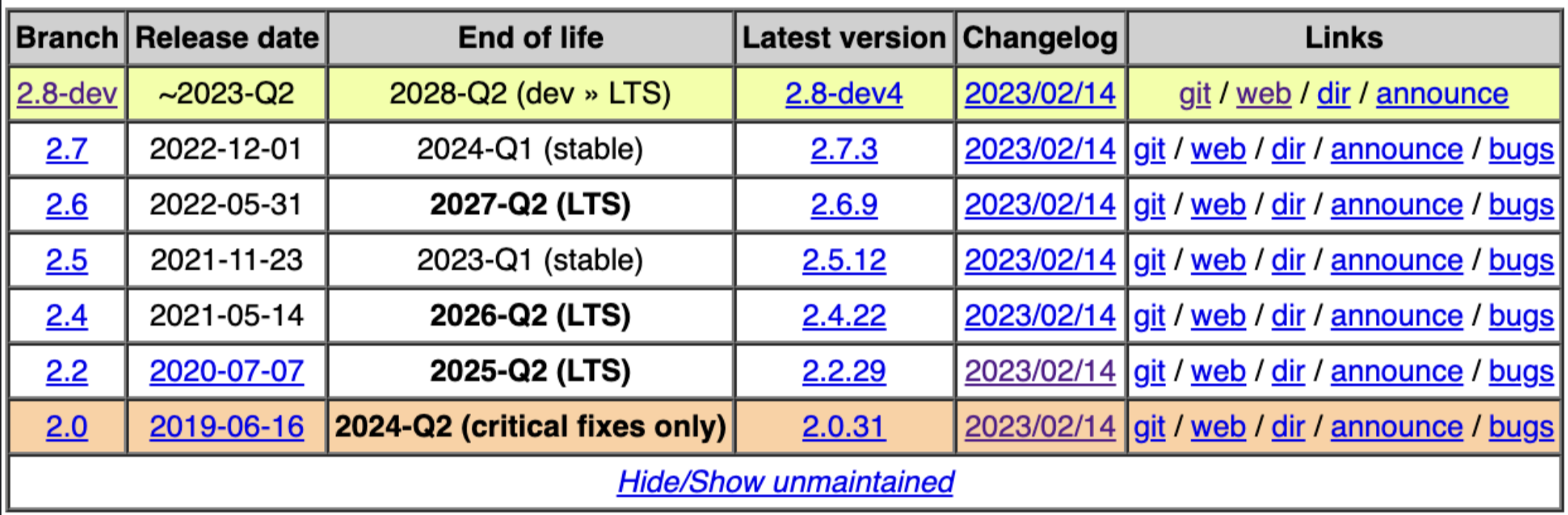
Branch Vulnerable Fixed Maintained until ---------+------------------------+----------+----------------- 2.8-dev 2.8-dev0 .. 2.8-dev3 2.8-dev4 2028-Q4 (LTS) 2.7 2.7.0 .. 2.7.2 2.7.3 2024-Q1 2.6 2.6.0 .. 2.6.8 2.6.9 2027-Q2 (LTS) 2.5 2.5.0 .. 2.5.11 2.5.12 2023-Q1 2.4 2.4.0 .. 2.4.21 2.4.12 2026-Q2 (LTS) 2.2 2.2.0 .. 2.2.28 2.2.29 2025-Q2 (LTS) 2.0 2.0.0 .. 2.0.30 2.0.31 2024-Q2 (LTS) -
This post is deleted! -
@jimp I`m bumping this thread up...
-
@jimp
Hi.
It has been 3 weeks, can you please add updated version?
Thanks! -
@jimp Can we somehow do it manually?
-
No, it has to be done in the package builders or it will more likely than not end up breaking something. We've had some more high priority issues that needed taking care of, so it's still pending.
-
@jimp Is this issue resolved?
-
does anyone know when the patched haproxy version will be available in pfsense?
-
@jsiegfried To be fair to the netgate team, there is a workaround for this as stated on the HA blog.
https://www.haproxy.com/blog/february-2023-header-parser-fixed/
The fix is very straight forward and easy to apply.
So yes an upgrade is nice, but the workaround is literally a copy and paste in your front end configuration.
-
@michmoor
Thank you very much for your reply.
I have already set the workaround in my shared-frontends.
But if I read it correctly, this is only the workaround for CVE-2023-25725.What about a patch or workaround for CVE-2023-0056?
-
@jsiegfried I don’t see any notification from HA Proxy about that CVE. They haven’t addressed it or spoken about it at least on their blog.
The CVE score is pretty low compared to the other one tho.https://www.cvedetails.com/cve/CVE-2023-0056/