IPSec DNAT not working
-
We had a prior setup on an NSX edge for a customer where they would attempt to RDP to an IP address which was listed on the remote IPsec site. It would then DNAT on RDP to an IP address on an isolated interface (isolated network is NOT on the IPsec)
This previously was setup to DNAT on 'any' interface. However it doesn't appear PFsense offer an 'any' on DNAT rules.
Wondering how we can re-create the same NAT rule but having no luck so far...
-
@matt_sharpe
Not clear, what you want to achieve here.
Maybe you can provide a drawing, which shows details, from where you want to access which device. -
@viragomann so if we imagine a simple 2 site connection via an IPsec VPN.
Site 1 = 172.16.100.0/24
Site 2 = 172.16.200.0/24Site 2 has an isolated network which we want to be able to provide RDP access to. However, we don't want this on IPsec VPN, so we're aiming to create a NAT rule which NATs an IP address on the 172.16.200.0/24 which directs to the isolated network.
The connection should look like this:
172.16.100.1 > IPsec tunnel > 172.16.200.253 (NATs to) 172.16.210.253
We achieved this on another firewall using a DNAT on 'any' interface' However no luck on PFsense as of yet.
-
@matt_sharpe said in IPSec DNAT not working:
However, we don't want this on IPsec VPN
NAT has to happen in IPSec. There is no way around.
172.16.100.1 > IPsec tunnel > 172.16.200.253 (NATs to) 172.16.210.253
You can do this in the IPSec phase 2, however:
At site 2 add an additional p 2, at
local network select Address and enter 172.16.210.253
NAT/BINAT translation select Address and enter 172.16.200.253
Remote Network select Network and enter 172.16.100.0/24 -
@viragomann Done this in our lab but no luck (generic FW rules allowing all traffic)
I assume no P2 tweaks needed on Site 1 for this....
-
@matt_sharpe Got it working, needed the Phase 1 setting "Split Connections" and an IPsec tunnel restart. Thanks @viragomann !
-
@matt_sharpe
If it's a pfSense it should work with that so far.But since both phase to have the same local network, you probably have to move the BINAT p2 to the top.
-
@viragomann This resolution does work. However the P2 tunnel (only created on the target site) is disconnecting after short periods. Even with a keep alive enabled and an IP to ping...
-
@viragomann This has cropped up once again. The customer has since changed the P1 tunnel to a routed VTI type and rather than having several Phase 2 tunnels. They now have a single P2 with a broader subnet to capture all remote networks.
When we now try and create/connect the IPv4 Phase tunnel for the RDP to isolated network, it kills the other tunnel completely. Would this be expected due to the P1 type?
-
M Matt_Sharpe referenced this topic on
-
@viragomann this is being picked back up and I'm at a loss at present. When we try and create a P2 tunnel for the NAT, it just takes the other P2 offline.
Is there any other way of accomplishing this NAT when coming across an IPsec tunnel? A form of double NAT etc?
I've tried adding a VIP/IP Alias for the address they're trying to hit across the tunnel, which should then NAT to the Isolated IP.
I've created a Hybrid outbound NAT so it knows how to communicate across interfaces, nothing working.
-
@Matt_Sharpe
It's not clear to me, what you actually have. Did you mix VTI and policy-based (BINAT) tunnels?Post both tunnel settings and the IPSec log.
-
@viragomann So the current working configuration (without the NAT requirements) is a single VTI tunnel with manual static routes configured.
I tried adding the second P2 tunnel for the RDP NAT as you previously suggested, but the other tunnel was then impacted.
This was a few hours ago, do you want the log for when the other P2 tunnel is created?
-
@Matt_Sharpe
As far as I know, you cannot mix routed and policy-based IPSec.However, this should not be necessary. NAT should be possible on the VTI interface directly.
You have to assign an interface to the VTI tunnel first, if you didn't this already.
Than you can assign a virtual IP of type IP alias to it and NAT it to whatever you want. -
@viragomann So I already have an interface assigned for the IPSEC tunnel. Named 'IPSEC'.
I am however unable to assign an IP address to this interface manually:
"This interface type does not support manual address configuration on this page"
It seems to pull the IP address from the Gateways list but it's set as 'Dynamic'.
If I try and add an IP Alias to the IPSEC interface we get:
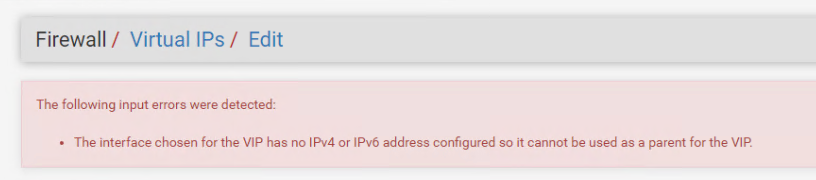
-
@Matt_Sharpe
So I assume, this is not the VTI interface.
Go to interface > assignments. Can you see the IPSec there? -
@viragomann Yes, I see the VTI in the list (customer information excluded of course)
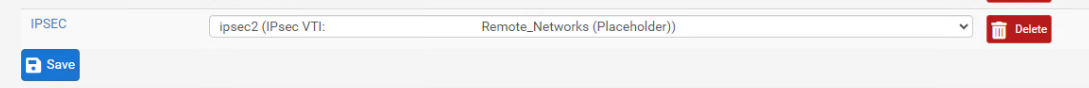
-
@Matt_Sharpe
OK, the virtual IP should not really be needed. You can apply NAT rules also without it.
You have to switch the IPsec Filter Mode in the IPsec Advanced Settings to "Filter IPsec VTI and Transport on assigned interfaces, block all tunnel mode traffic".
However, this only works, if all your IPSec tunnels are VTI! If this is not given you cannot use it. -
@viragomann Unfortunately, we have 2 tunnels, the other one into Azure is a tunnel-based IPsec.
Do we have any other options ?
-
@Matt_Sharpe
This is the only way to get traditional NAT rules working on IPSec.The only other option is routed IPSec with BINAT. But I don't know if this works simultaneously with a VTI tunnel. I assume, it should.
Maybe the setting and the log can shed some light. -
@viragomann I added the second Phase 2 IPsec (tunnel mode). Here are the IPsec logs shortly after enabling the tunnel. I've changed IP addresses for security.
PART 1
Last 500 IPsec Log Entries. (Maximum 500)
Jan 16 14:40:07 charon 75651 06[CFG] vici client 1276 disconnected
Jan 16 14:40:07 charon 75651 12[CFG] updated vici connection: con2
Jan 16 14:40:07 charon 75651 12[CFG] id = CUSTOMER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] class = pre-shared key
Jan 16 14:40:07 charon 75651 12[CFG] remote:
Jan 16 14:40:07 charon 75651 12[CFG] id = PROVIDER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] class = pre-shared key
Jan 16 14:40:07 charon 75651 12[CFG] local:
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 2880
Jan 16 14:40:07 charon 75651 12[CFG] over_time = 2880
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 25920
Jan 16 14:40:07 charon 75651 12[CFG] reauth_time = 0
Jan 16 14:40:07 charon 75651 12[CFG] keyingtries = 1
Jan 16 14:40:07 charon 75651 12[CFG] unique = UNIQUE_REPLACE
Jan 16 14:40:07 charon 75651 12[CFG] childless = 0
Jan 16 14:40:07 charon 75651 12[CFG] fragmentation = 2
Jan 16 14:40:07 charon 75651 12[CFG] dpd_timeout = 0
Jan 16 14:40:07 charon 75651 12[CFG] dpd_delay = 30
Jan 16 14:40:07 charon 75651 12[CFG] encap = 0
Jan 16 14:40:07 charon 75651 12[CFG] dscp = 0x00
Jan 16 14:40:07 charon 75651 12[CFG] aggressive = 0
Jan 16 14:40:07 charon 75651 12[CFG] mobike = 0
Jan 16 14:40:07 charon 75651 12[CFG] ppk_required = 0
Jan 16 14:40:07 charon 75651 12[CFG] ppk_id = (null)
Jan 16 14:40:07 charon 75651 12[CFG] send_cert = CERT_SEND_IF_ASKED
Jan 16 14:40:07 charon 75651 12[CFG] send_certreq = 1
Jan 16 14:40:07 charon 75651 12[CFG] remote_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] local_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] remote_addrs = CUSTOMER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] local_addrs = PROVIDER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] version = 2
Jan 16 14:40:07 charon 75651 12[CFG] copy_dscp = out
Jan 16 14:40:07 charon 75651 12[CFG] copy_ecn = 1
Jan 16 14:40:07 charon 75651 12[CFG] copy_df = 1
Jan 16 14:40:07 charon 75651 12[CFG] sha256_96 = 0
Jan 16 14:40:07 charon 75651 12[CFG] hw_offload = no
Jan 16 14:40:07 charon 75651 12[CFG] remote_ts = CUSTOMER_LAN_RANGE|/0 0.0.0.0/0|/0 ::/0|/0
Jan 16 14:40:07 charon 75651 12[CFG] local_ts = SITE2_LAN_IP/32|SITE2_ISOLATED_LAN_IP/32 0.0.0.0/0|/0 ::/0|/0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
Jan 16 14:40:07 charon 75651 12[CFG] inactivity = 0
Jan 16 14:40:07 charon 75651 12[CFG] label_mode = system
Jan 16 14:40:07 charon 75651 12[CFG] label = (null)
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in_sa = 0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] interface = (null)
Jan 16 14:40:07 charon 75651 12[CFG] priority = 0
Jan 16 14:40:07 charon 75651 12[CFG] tfc = 0
Jan 16 14:40:07 charon 75651 12[CFG] reqid = 5003
Jan 16 14:40:07 charon 75651 12[CFG] close_action = none
Jan 16 14:40:07 charon 75651 12[CFG] start_action = start
Jan 16 14:40:07 charon 75651 12[CFG] dpd_action = start
Jan 16 14:40:07 charon 75651 12[CFG] policies_fwd_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] policies = 1
Jan 16 14:40:07 charon 75651 12[CFG] mode = TUNNEL
Jan 16 14:40:07 charon 75651 12[CFG] ipcomp = 0
Jan 16 14:40:07 charon 75651 12[CFG] hostaccess = 0
Jan 16 14:40:07 charon 75651 12[CFG] updown = (null)
Jan 16 14:40:07 charon 75651 12[CFG] rand_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 360
Jan 16 14:40:07 charon 75651 12[CFG] life_time = 3600
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 3240
Jan 16 14:40:07 charon 75651 12[CFG] child con2_3:
Jan 16 14:40:07 charon 75651 12[CFG] copy_dscp = out
Jan 16 14:40:07 charon 75651 12[CFG] copy_ecn = 1
Jan 16 14:40:07 charon 75651 12[CFG] copy_df = 1
Jan 16 14:40:07 charon 75651 12[CFG] sha256_96 = 0
Jan 16 14:40:07 charon 75651 12[CFG] hw_offload = no
Jan 16 14:40:07 charon 75651 12[CFG] remote_ts = VTI_CUSTOMER_IP/32|/0 0.0.0.0/0|/0 ::/0|/0
Jan 16 14:40:07 charon 75651 12[CFG] local_ts = VTI_SITE2_IP/32|/0 0.0.0.0/0|/0 ::/0|/0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = ESP:AES_CBC_256/HMAC_SHA2_256_128/MODP_2048/NO_EXT_SEQ
Jan 16 14:40:07 charon 75651 12[CFG] inactivity = 0
Jan 16 14:40:07 charon 75651 12[CFG] label_mode = system
Jan 16 14:40:07 charon 75651 12[CFG] label = (null)
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in_sa = 0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] interface = (null)
Jan 16 14:40:07 charon 75651 12[CFG] priority = 0
Jan 16 14:40:07 charon 75651 12[CFG] tfc = 0
Jan 16 14:40:07 charon 75651 12[CFG] reqid = 5002
Jan 16 14:40:07 charon 75651 12[CFG] close_action = none
Jan 16 14:40:07 charon 75651 12[CFG] start_action = start
Jan 16 14:40:07 charon 75651 12[CFG] dpd_action = start
Jan 16 14:40:07 charon 75651 12[CFG] policies_fwd_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] policies = 0
Jan 16 14:40:07 charon 75651 12[CFG] mode = TUNNEL
Jan 16 14:40:07 charon 75651 12[CFG] ipcomp = 0
Jan 16 14:40:07 charon 75651 12[CFG] hostaccess = 0
Jan 16 14:40:07 charon 75651 12[CFG] updown = (null)
Jan 16 14:40:07 charon 75651 12[CFG] rand_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 360
Jan 16 14:40:07 charon 75651 12[CFG] life_time = 3600
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 3240
Jan 16 14:40:07 charon 75651 12[CFG] child con2_2:
Jan 16 14:40:07 charon 75651 12[CFG] conn con2:
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: load-conn
Jan 16 14:40:07 charon 75651 12[CFG] updated vici connection: con1
Jan 16 14:40:07 charon 75651 12[CFG] id = AZURE_IP
Jan 16 14:40:07 charon 75651 12[CFG] class = pre-shared key
Jan 16 14:40:07 charon 75651 12[CFG] remote:
Jan 16 14:40:07 charon 75651 12[CFG] id = PROVIDER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] class = pre-shared key
Jan 16 14:40:07 charon 75651 12[CFG] local:
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 2880
Jan 16 14:40:07 charon 75651 12[CFG] over_time = 2880
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 0
Jan 16 14:40:07 charon 75651 12[CFG] reauth_time = 25920
Jan 16 14:40:07 charon 75651 12[CFG] keyingtries = 1
Jan 16 14:40:07 charon 75651 12[CFG] unique = UNIQUE_REPLACE
Jan 16 14:40:07 charon 75651 12[CFG] childless = 0
Jan 16 14:40:07 charon 75651 12[CFG] fragmentation = 2
Jan 16 14:40:07 charon 75651 12[CFG] dpd_timeout = 60
Jan 16 14:40:07 charon 75651 12[CFG] dpd_delay = 10
Jan 16 14:40:07 charon 75651 12[CFG] encap = 0
Jan 16 14:40:07 charon 75651 12[CFG] dscp = 0x00
Jan 16 14:40:07 charon 75651 12[CFG] aggressive = 0
Jan 16 14:40:07 charon 75651 12[CFG] mobike = 0
Jan 16 14:40:07 charon 75651 12[CFG] ppk_required = 0
Jan 16 14:40:07 charon 75651 12[CFG] ppk_id = (null)
Jan 16 14:40:07 charon 75651 12[CFG] send_cert = CERT_SEND_IF_ASKED
Jan 16 14:40:07 charon 75651 12[CFG] send_certreq = 1
Jan 16 14:40:07 charon 75651 12[CFG] remote_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] local_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] remote_addrs = AZURE_IP
Jan 16 14:40:07 charon 75651 12[CFG] local_addrs = PROVIDER_WAN_IP
Jan 16 14:40:07 charon 75651 12[CFG] version = 1
Jan 16 14:40:07 charon 75651 12[CFG] copy_dscp = out
Jan 16 14:40:07 charon 75651 12[CFG] copy_ecn = 1
Jan 16 14:40:07 charon 75651 12[CFG] copy_df = 1
Jan 16 14:40:07 charon 75651 12[CFG] sha256_96 = 0
Jan 16 14:40:07 charon 75651 12[CFG] hw_offload = no
Jan 16 14:40:07 charon 75651 12[CFG] remote_ts = AZURE_LAN|/0
Jan 16 14:40:07 charon 75651 12[CFG] local_ts = SITE2_LAN|/0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_GCM_12_256/NO_EXT_SEQ, ESP:AES_GCM_8_256/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_12_128/NO_EXT_SEQ, ESP:AES_GCM_8_128/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_192/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_128/HMAC_SHA2_256_128/NO_EXT_SEQ
Jan 16 14:40:07 charon 75651 12[CFG] inactivity = 0
Jan 16 14:40:07 charon 75651 12[CFG] label_mode = system
Jan 16 14:40:07 charon 75651 12[CFG] label = (null)
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in_sa = 0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] interface = (null)
Jan 16 14:40:07 charon 75651 12[CFG] priority = 0
Jan 16 14:40:07 charon 75651 12[CFG] tfc = 0
Jan 16 14:40:07 charon 75651 12[CFG] reqid = 0
Jan 16 14:40:07 charon 75651 12[CFG] close_action = none
Jan 16 14:40:07 charon 75651 12[CFG] start_action = trap
Jan 16 14:40:07 charon 75651 12[CFG] dpd_action = trap
Jan 16 14:40:07 charon 75651 12[CFG] policies_fwd_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] policies = 1
Jan 16 14:40:07 charon 75651 12[CFG] mode = TUNNEL
Jan 16 14:40:07 charon 75651 12[CFG] ipcomp = 0
Jan 16 14:40:07 charon 75651 12[CFG] hostaccess = 0
Jan 16 14:40:07 charon 75651 12[CFG] updown = (null)
Jan 16 14:40:07 charon 75651 12[CFG] rand_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_packets = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] life_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rekey_bytes = 0
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 360
Jan 16 14:40:07 charon 75651 12[CFG] life_time = 3600
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 3240
Jan 16 14:40:07 charon 75651 12[CFG] child con1_1:
Jan 16 14:40:07 charon 75651 12[CFG] conn con1:
Jan 16 14:40:07 charon 75651 12[CFG] vici client 1276 requests: load-conn
Jan 16 14:40:07 charon 75651 12[CFG] updated vici connection: bypass
Jan 16 14:40:07 charon 75651 12[CFG] remote:
Jan 16 14:40:07 charon 75651 12[CFG] local:
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/AES_CTR_128/AES_CTR_192/AES_CTR_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/CAMELLIA_CTR_128/CAMELLIA_CTR_192/CAMELLIA_CTR_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_CCM_16_128/AES_CCM_16_192/AES_CCM_16_256/CHACHA20_POLY1305/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/AES_CCM_12_128/AES_CCM_12_192/AES_CCM_12_256/AES_CCM_8_128/AES_CCM_8_192/AES_CCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/CURVE_448/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
Jan 16 14:40:07 charon 75651 12[CFG] rand_time = 1440
Jan 16 14:40:07 charon 75651 12[CFG] over_time = 1440
Jan 16 14:40:07 charon 75651 12[CFG] rekey_time = 14400
Jan 16 14:40:07 charon 75651 12[CFG] reauth_time = 0
Jan 16 14:40:07 charon 75651 12[CFG] keyingtries = 1
Jan 16 14:40:07 charon 75651 12[CFG] unique = UNIQUE_NO
Jan 16 14:40:07 charon 75651 12[CFG] childless = 0
Jan 16 14:40:07 charon 75651 12[CFG] fragmentation = 2
Jan 16 14:40:07 charon 75651 12[CFG] dpd_timeout = 0
Jan 16 14:40:07 charon 75651 12[CFG] dpd_delay = 0
Jan 16 14:40:07 charon 75651 12[CFG] encap = 0
Jan 16 14:40:07 charon 75651 12[CFG] dscp = 0x00
Jan 16 14:40:07 charon 75651 12[CFG] aggressive = 0
Jan 16 14:40:07 charon 75651 12[CFG] mobike = 1
Jan 16 14:40:07 charon 75651 12[CFG] ppk_required = 0
Jan 16 14:40:07 charon 75651 12[CFG] ppk_id = (null)
Jan 16 14:40:07 charon 75651 12[CFG] send_cert = CERT_SEND_IF_ASKED
Jan 16 14:40:07 charon 75651 12[CFG] send_certreq = 1
Jan 16 14:40:07 charon 75651 12[CFG] remote_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] local_port = 500
Jan 16 14:40:07 charon 75651 12[CFG] remote_addrs = 127.0.0.1
Jan 16 14:40:07 charon 75651 12[CFG] local_addrs = %any
Jan 16 14:40:07 charon 75651 12[CFG] version = 0
Jan 16 14:40:07 charon 75651 12[CFG] copy_dscp = out
Jan 16 14:40:07 charon 75651 12[CFG] copy_ecn = 1
Jan 16 14:40:07 charon 75651 12[CFG] copy_df = 1
Jan 16 14:40:07 charon 75651 12[CFG] sha256_96 = 0
Jan 16 14:40:07 charon 75651 12[CFG] hw_offload = no
Jan 16 14:40:07 charon 75651 12[CFG] remote_ts = SITE2_LAN|/0
Jan 16 14:40:07 charon 75651 12[CFG] local_ts = SITE2_LAN|/0
Jan 16 14:40:07 charon 75651 12[CFG] proposals = ESP:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_CBC_128/AES_CBC_192/AES_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/NO_EXT_SEQ
Jan 16 14:40:07 charon 75651 12[CFG] inactivity = 0
Jan 16 14:40:07 charon 75651 12[CFG] label_mode = system
Jan 16 14:40:07 charon 75651 12[CFG] label = (null)
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] set_mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_out = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in_sa = 0
Jan 16 14:40:07 charon 75651 12[CFG] mark_in = 0/0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_out = 0
Jan 16 14:40:07 charon 75651 12[CFG] if_id_in = 0
Jan 16 14:40:07 charon 75651 12[CFG] interface = (null)
Jan 16 14:40:07 charon 75651 12[CFG] priority = 0
Jan 16 14:40:07 charon 75651 12[CFG] tfc = 0
Jan 16 14:40:07 charon 75651 12[CFG] reqid = 0
Jan 16 14:40:07 charon 75651 12[CFG] close_action = none
Jan 16 14:40:07 charon 75651 12[CFG] start_action = trap
Jan 16 14:40:07 charon 75651 12[CFG] dpd_action = none
Jan 16 14:40:07 charon 75651 12[CFG] policies_fwd_out = 0