Got T-Mobile 5G Home Internet
-
So, yesterday I got T-Mobile's 5G Home Internet but have not connected it yet as I am unsure about the co-NAT situation having a VOIP FreePBX server in a DMZ. I have been cooking up an elaborate scheme where I have a VPN tunnel site to site with a private cloud at home with a Dell Precision 3630MT I recently bought on eBay without memory or hard drive and is waiting for the memory 64GB and 250GB M2.nvme to arrive next week in the middle of Mardi Gras.
However, I wanted to know how others deal with the co-NAT...I know I'll turn off private address RF1819, but what to do with NAT. My setup is already double natted as I have a Mikrotik RB450x4 behind pfSense controlling LAN; so, I shall disable it.
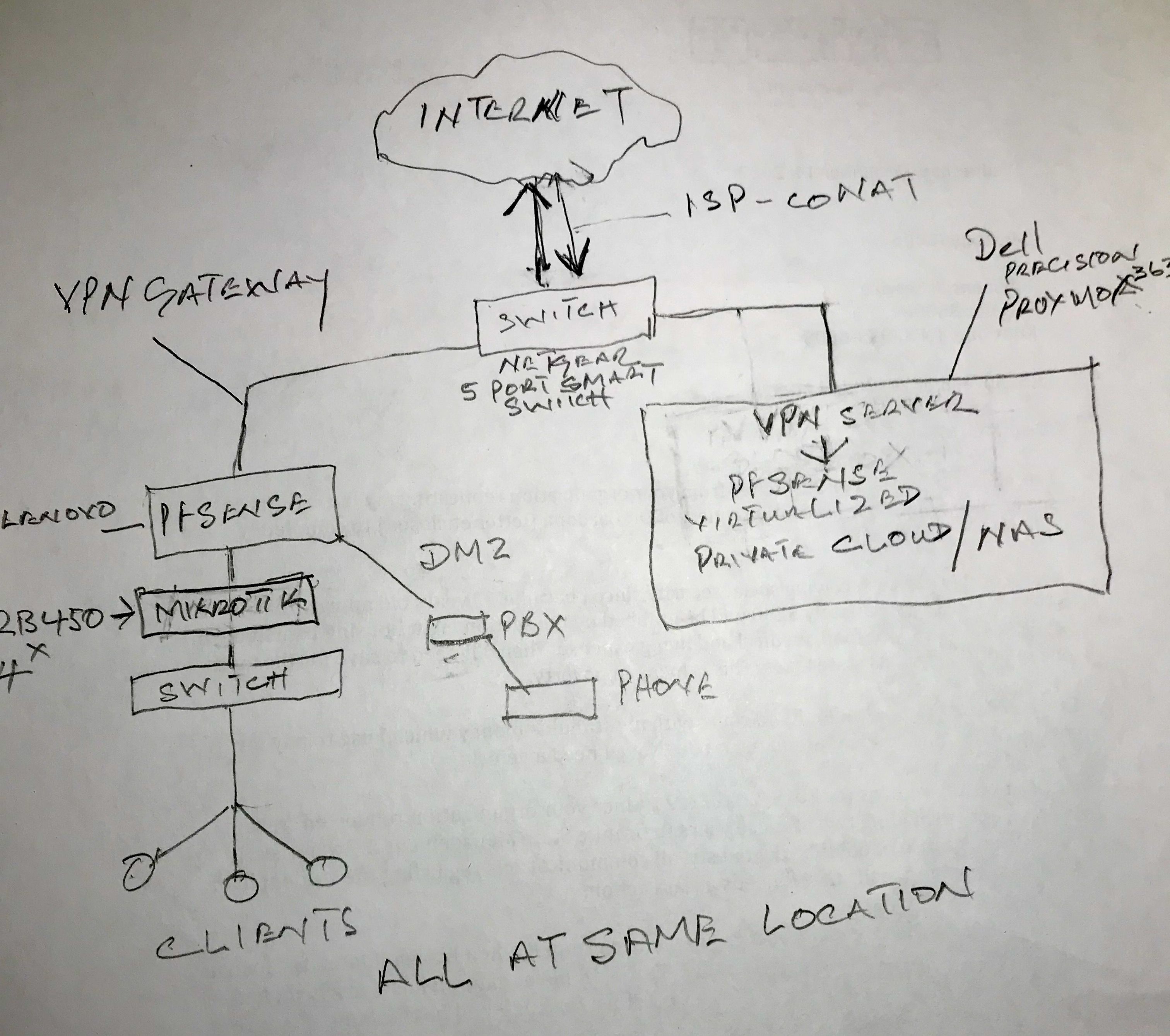
Here's a primitive drawing of what I planned:
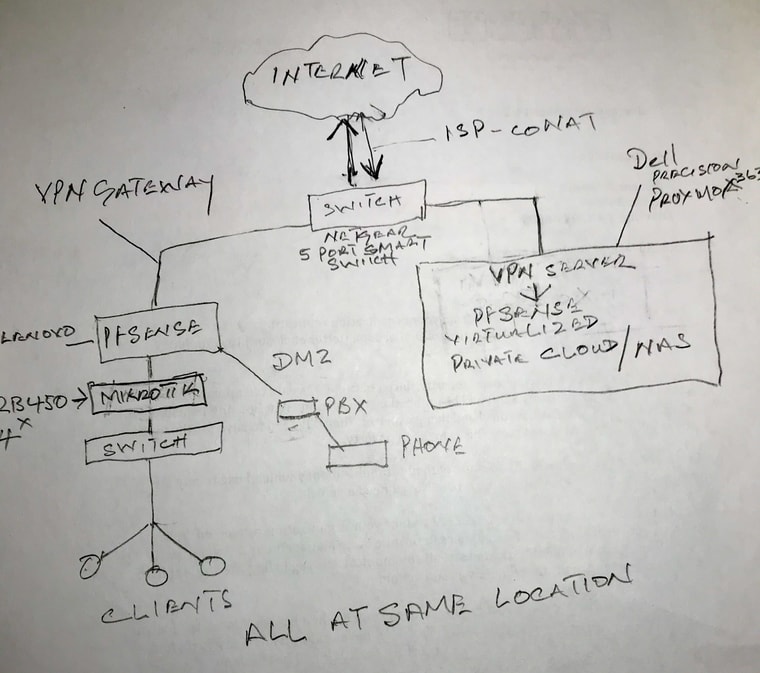
-
I assume you mean CG-NAT here? What problem are you anticipating here? Incoming VoIP issues? That could certainly be a problem.
Will this be your only WAN?Steve
-
@stephenw10 Yes and yes, only WAN...the 5G modem is still in the box and I am wondering whether to just wait for all the hardware to arrive before I attempt connection. I could not find anyone who used the 5G with VOIP to determine any anticipated problem but conversations with ChatGPT as well as you suggested the VPN solution.
-
I final got rid of 5G home Internet. I was unable to get the VPN working on this device.
-
@joenavy Sadly, it sounds as if you gave up too easily...I have no choice, need make it work somehow!
-
@nollipfsense said in Got T-Mobile 5G Home Internet:
have no choice, need make it work somehow!
If you have CGNAT, you'll never get a VPN to work, at least not for incoming connections.
-
Yup it can only ever establish outbound.
In addition one of our guys on staff was unable to use a CG-NAT link when we found that they were NATing to a pool of IPs with no 'sticky connections'. This means that if the remote side is filtering by dyn-dns address, as we do, it doesn't match and drops the connection.
Steve
-
@JoeNavy @JKnott @stephenw10
Maybe I rush to judgement...sorry @JoeNavy
Here are conversations with ChatGPT results:
A VPN tunnel through a carrier-grade NAT (cg-NAT) to a private cloud at the same location should work, as long as the NAT device allows incoming VPN traffic and the necessary ports are properly forwarded.
However, if the carrier is using dynamic DNS upstream, it could potentially cause issues with the VPN tunnel, as the dynamic IP address assigned to the NAT device could change periodically. This could cause the VPN connection to fail if the address changes while the connection is active.
To mitigate this issue, the private cloud could use a dynamic DNS service to keep track of the changing IP address of the NAT device and update the VPN configuration accordingly. Alternatively, the carrier may offer a static IP address option, which would eliminate the issue altogether.
sorry if my previous response was not clear. Let me try to clarify.
A VPN tunnel can be used to create a secure connection between a device and a private cloud server located at the same location, even if both are behind a carrier-grade NAT (cg-NAT).
However, if the private cloud server has a dynamic IP address that changes frequently, it may be difficult to connect to it reliably using a static IP address. In such cases, one solution is to use a dynamic DNS service that maps a domain name to the server's current IP address.
The VPN tunnel itself should not be affected by the use of dynamic DNS or the presence of a cg-NAT, as long as the necessary ports are open and properly forwarded.
I apologize for the confusion in my previous response. If your ISP is using CG-NAT, then it is not possible to create a VPN tunnel directly to your private cloud at the same location, as the CG-NAT router is likely configured to block incoming connections.
However, you may be able to work around this limitation by using a VPN service that supports NAT traversal techniques like UDP hole punching or STUN. These techniques can help establish a VPN tunnel between two devices that are both behind NAT routers.
Another option would be to use a third-party VPN service that allows you to create a VPN connection to a server outside of your network, and then route your traffic through that server to reach your private cloud. This method can be less efficient and may introduce additional latency, but it can still be a viable solution in some scenarios.
In either case, it is important to test your configuration thoroughly and ensure that it is secure and reliable before relying on it for production use.So, after that conversation, I saw this guy's video about using a VPS at a separate location with a reverse proxy at one's private cloud...https://www.youtube.com/watch?v=9tDeh9mutmI
I'll try spinning my wheels to see if I move an inch...it's difficult for me to give up...the cheapest option while the most expensive option is to move to a location with fiber Internet which is my ultimate goal but the pandemic threw a monkey wrench in that plan and slowed me down.
I also looked at this: https://docs.netgate.com/pfsense/en/latest/recipes/ipv6-tunnel-broker.html -
You will not be able to connect inbound through CG-NAT. Just no way.
You can only connect outbound So if you are trying to access resources that are behind pfSense and that is using a CG-NAT WAN you will have to use some external static server that both pfSense and external client connect to.
-
@stephenw10 said in Got T-Mobile 5G Home Internet:
to use some external static server that both pfSense and external client connect to.
This is what I am realizing...one thing I noticed checking the supposed T-Mobile gateway out is that I am given both IPv6 and IPv4 address...what a great way to brush away my IPv6 mental resistance despite my stomach protesting dual stack...
-
Ha. Well if they give you a public IPv6 that solves the problem. Mostly at least.
Of course it won't work if you're trying to connect from somewhere that doesn't have IPv6....
-
IPv6 is where the world is moving to, so you might as well get used to it. I've had it for almost 13 years.
I don't know what T-Mobile hands out, but I get 2^72 addresses from my ISP. This seems to be fairly typical.
-
Back when I used a tunnel to get IPv6, I set up my notebook to get a single address, as well as the /56 on my home network. I wonder if he.net offers something similar, so that you can access IPv6 over IPv4.
-
Yup, you could probably do that if you had to. I can pretty much guaranty that if you're using remote access OpenVPN then at some point you're going to end up trying to connect back from somewhere that's IPv4 only.
-
It all depends also where are you living!
In Germany you could get a Fritz!Box LTE router that is
able to use with T-mobile, they have a choice (service)
that is called My!Fritz so you may able to connect to
the inside of your network with VPN then.The second chance is you get a small business contract
from them (T-Mobile) with an static public IP address
and all is fine for you and the vpn.The third way may be more independent from all others but you must set up a so called "jump host" elsewhere in the internet and over that host you "vpn" home.
-
Here is an interesting statement from my SIP service provider, Voip.ms: "The SIP request would come from a public IP address and port assigned to your modem from the ISP side. There's no issue when using cg-NAT with our service as most of our residential internet users are behind a cg-NAT."
Are they blowing smoke up my rare end?
-
@nollipfsense Connections out to a service don't matter. Connections in to you do matter. So it depends on what connects to whom. We're a 3CX partner and the connection is made from 3CX out to the SIP provider.
*rear ;)
-
Mmm, if you have external VoIP phones connecting to your PBX behind the CG-NAT that's going to fail.
-
@steveits said in Got T-Mobile 5G Home Internet:
@nollipfsense Connections out to a service don't matter. Connections in to you do matter. So it depends on what connects to whom. We're a 3CX partner and the connection is made from 3CX out to the SIP provider.
*rear ;)
If you are using a PBX appliance it would be perhaps good
to place them in a DMZ. Or plain a switch where the phones
will be connected. Will this solve the problem? -
@stephenw10 Yes but phones connecting out to "the cloud" would succeed. Looks like VoIP.ms has both services.