Problems configuring OpenVPN on pFsense 23.01
-
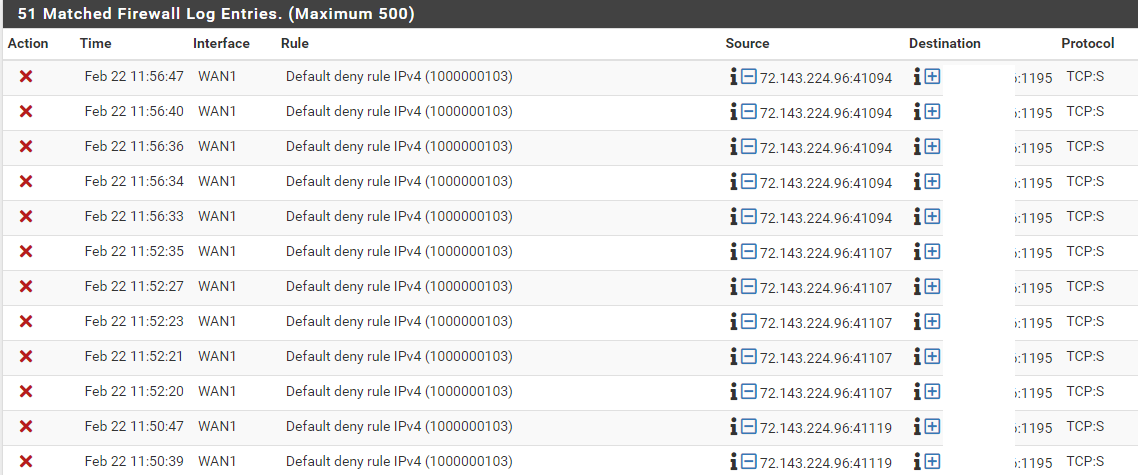
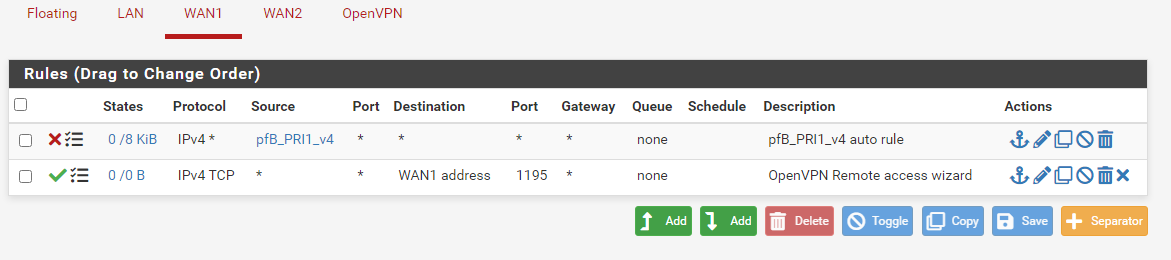
I was able to have this rule working by changing the destination from "WAN1 address" to "single host or alias" and then adding the public IP address of my WAN1 interface. My problem is that that interface is DHCP. I need to use the WAN1 address solution. I did also try WAN1 net and it also did not work.
My question is, is this a bug on the new 23.01 pfsense? Should it be reported? Any ideas or suggestions?
Thanks
-
Hi @johnpoz
According to your last post in weird error with NAT/firewall:
I believe there was a thread around here where someone was having that sort of issue, and they had renamed the interfaces in the xml or something and it was causing all aliases to fail, like the lan net, the firewall, etc. if I recall correctly.
Do you know how to fix that? I did play with the XML file! So, this can be my problem. And yes, the traffic is arriving! And, in my case, if I change from the alias, WAN address to the public IP, it works like a charm. Not to mention that I already capture a lot of traffic and it is always coming to the firewall and not being identified...
So, you idea that it may be related to XML sounds just what my problem is.
-
@fbrunken well what you could do is look in your full rule list..
pfctl -sr
if I then filter that for my wan interface igb1, I can find lots of rules were the wan address is expanded to actual IP
pass in log quick on igb1 reply-to (igb1 209.snipped) inet proto udp from <pfB_AllowPfb_v4> to 209.snipped port = openvpn keep state label "USER_RULE: UDP openvpn" label "id:1513069465" ridentifier 1513069465So for example here is my rule that allow openvpn traffic in to my "wan address" and it has my wan IP and my wan net in the reply-to.. Maybe you have an issue with the reply-to when you have multi-wan?
Does in your rules it show you the correct IP for your wan1 address
edit: let me see if I can dig up that other thread..
-
Here is that thread about the aliases not working
https://forum.netgate.com/topic/173608/pfsense-not-propagating-system-aliases-lanx-net-lanx-address
-
@johnpoz Many thanks for your help
I just had the following result for pfctl -sr
If I do it using "WAN address", I get nothing. If I force the IP address, the rule shows up. So, yes, I believe I am getting closer to the problem/solution.
See here: (the xxs are for my public IP and gateway)
pass in log quick on igc1 reply-to (igc1 xx.xx.x.x) inet proto tcp from any to xx.xx.x.xxx port = rsf-1 flags S/SA keep state label "USER_RULE: OpenVPN Remote access wizard" label "id:1677092037" ridentifier 1677092037Like the guy from the other post, I am also not ready to start the entire installation from scratch again but... I will have to leave soon and will investigating this further when I come back. If there is any other documentation that you recommend, let me know.
Many thanks again for your help
-
@johnpoz I hope you don't mind me bothering you with this one more time.
What would be the best way to configure my pfsense new? Using Diagnostics/Factory Defaults and factory reset or just really start with a new boot USB and start from scratch?
Thanks once again for all your help.
-
@fbrunken Not what your asking - do you want to go completely clean?
What I have done in the past when I wanted a clean start - is just clean install and setup my rules by hand... Not like I have 100s of them or anything, and only a handful of interfaces and vlans.
I just too some screenshots of my interface rules - so I would have something to go by etc..
-
@johnpoz Also, just for personal learning for the future, couldn't one download the config from a netgate backup first? Or would that be highly likely to reintroduce the problem ?
-
@nightlyshark you could leverage ACB sure to get a backup of your device. While automated backups in the cloud are a good fail safe thing to do.
But if I was in the process of doing an upgrade, I would take a specific local backup of the config as step 1 in the process. Only takes a few seconds to do that - and now you know for sure where your backup is, and that it is current.
But if the goal is something is wrong with the setup, and the config might be corrupted or have some bad info in it causing problems. The setup clean might be better option. Or loading of specific details from the backup vs a full load of everything.
For example the enterprise whenever you are going to do really any sort of change on a piece of equipment, pretty much always step one is take a backup. You don't just rely on the automated backup solution to have your backup for you.
-
Dear @johnpoz,
many thanks again for your patience and support. I went for a clean install and configuration of my pfsense and the problem is solved.
Thanks again and have a great rest of the day.