Pia Lan issues
-
I have managed to get PIA working across two different vlans/interfaces and its providing me with a different external Ip. I've set up the nat rules and the firewall rules ect but I have a problem in that I can no longer access stuff on the lan when the Pia server is enabled. What would likely be causing this ? The virtual Ip address of the pia server is 10.17.112.*** and when I do a trace route in cmd trying to ping an internal ip its first hop is 10.17.12.1. is it trying to route my request externally ? as soon as I turn off the pia server I can then ping everything on my network. I don't work in networking or IT so any help would be much appreciated.
I've attached some more information about my set up. Many thanks Mike
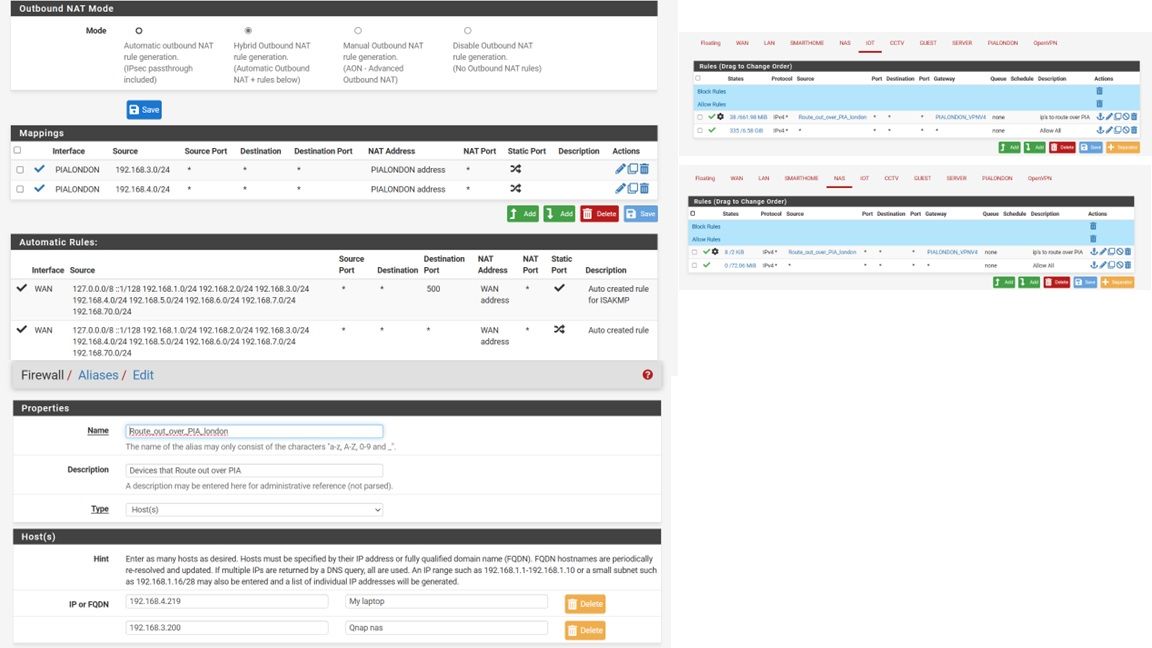
-
@mike123-0
Your firewall policy routing rules forces all traffic the the OpenVPN server.The rules are probed from top to bottom. If one matches to the incoming traffic it is applied and further rules are ignored. So your policy routing rule matches to any traffic from all IPs includes in the source alias, so the traffic is routed to the PIA.
You have to care that the policy route is not applied to internal destinations.Best way to solve this:
Assuming you're using only private network ranges in your LAN, create an alias, call it RFC1918 and add all RFC1918 networks to it.
Then set this alias as destination with "invert match" checked in the policy routing rule.
So this rule is then only applied for destinations outside of the private network ranges. -
Thanks for the quick reply viragomann, I'm very new to networking so please forgive me if this is a stupid question but why would it apply the rule to everything on that vlan when I've chosen it to match the alias that only has a couple of ips on it ?
-
@mike123-0
That's not a stupid question at all. No, this shouldn't be the case, of course.
The rule should be applied to the certain IPs in the source alias.But maybe the server pushes the default route to you. That is the default behavior of PIA.
If you want to set the routes for the VPN yourself, go into the server settings and check "don't pull routes" to avoid this. -
@mike123-0 You also have to define a destination. You need an inverted RFC1918-alias as destination in those rules.
-
I've changed my setting as you've advised and its now working correctly, can you please just look over my attachments and see if I have done it correctly .
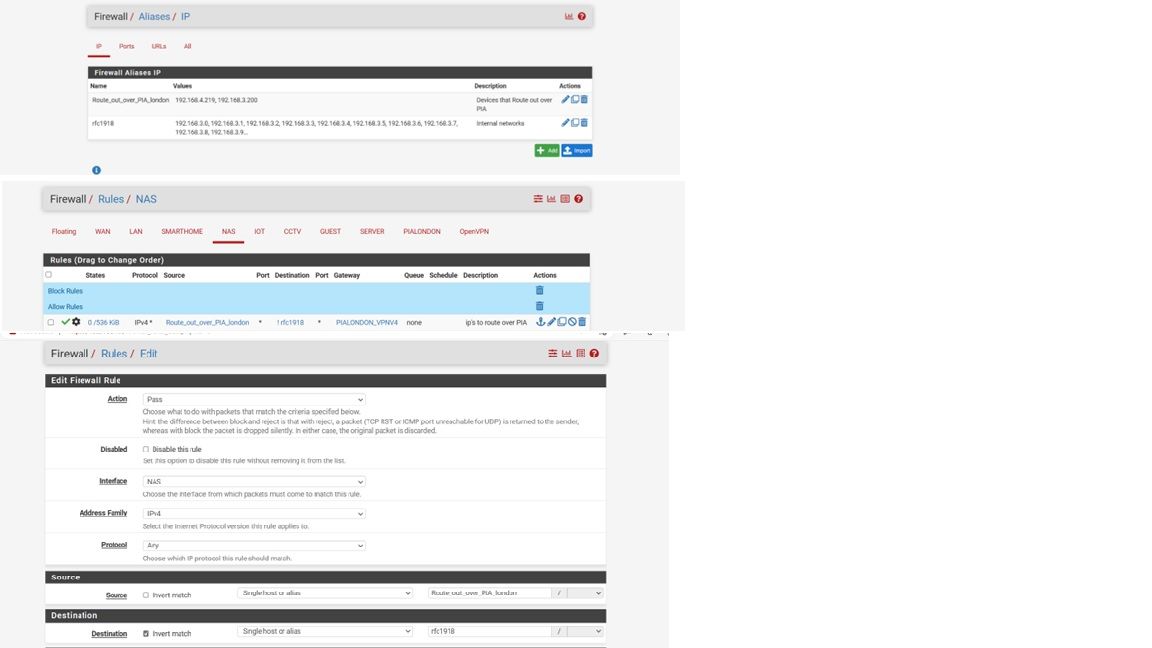
Many thanks
Mike -
@mike123-0
Why did you add all these networks to the RFC1918 alias.
Simply add the three overall blocks to it as shown on https://en.wikipedia.org/wiki/Private_network:
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16With these the alias covers the whole private network ranges. So if you add a local network segment in the far future, you don't need to care about this alias and your settings will be still save.
Apart from this, your rule seems to be correct.
-
@viragomann I've just tried doing this and it wont let me as the maximum amount of ips you can have in an aliases is 5000, is the only way to do it to create multiple aliases for the internal network ?
-
@mike123-0
No, select alias type "Network(s)" and add the three network ranges below.
So each of it is just one entry in the state table. -
@viragomann Thanks so much for your help, I've just done this and its now all working as it should.