DNS & NTP best practice (vlans & IoT)
-
@furom huh - why would I ever use my ISP dns? The only scenario were those would be used is by pfsense itself, a client behind would never asks them anything.
Even if you let your dhcp from your isp hand you dns, the only device that would ever use those is pfsense if unbound failed, it could resort to using those to check for say updates to pfsense.
Only if you setup forwarding in unbound would unbound ever use say your isp dns to forward too if they are in your general pfsense settings. But this is not the default.. Default is unbound resolves. Would never talk to your isp dns, unless it was authoritative for some domain..
edit: another thing these dot and doh providers don't tell you.. Until esni, or the new name ech is standard across the board.. Your isp still knows where you going. For one they going to know the IP your going to unless you use a vpn.. They also going to know the domain your going to, because with IP along - that could be almost anything because hosted of some huge CDN, etc.
But the sni, the fqdn your trying to go to is going to be in the clear, that they can see with the start of the https/tls connection.. So while they might not know your going to www.domain.com/something - they can easy still tell your going to www.domain.com, and they would of never known the /something anyway even if you were sending them your dns directly..
So what exactly is sending encrypted dns to some dot/doh server hiding from your isp exactly? While they might not get it served up on silver platter with you sending it to their dns - they for sure can see the fqdn your going to if they so desire..
esni (encrypted server name indication) is dead, long live ech (encrypted client hello).. But to be honest that is years out from becoming an actual viable thing. Because the server owners have to allow for it, set it up to be able for clients to use it, etc..
-
@johnpoz Ok, now I lost myself in this I think, sorry... So I could do without these?
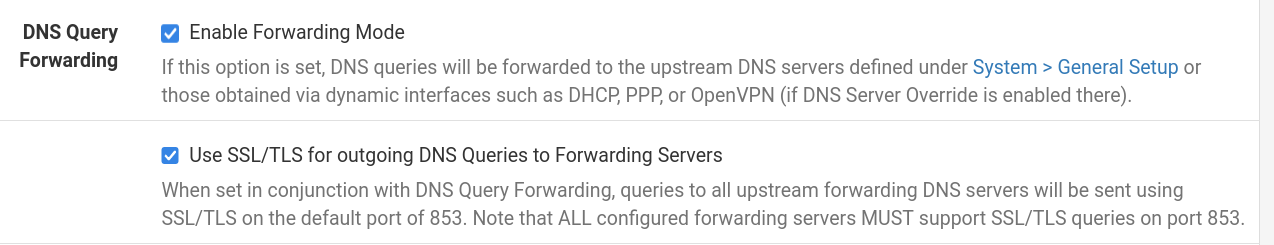
which then wouldn't use these?

If not really needed, why here?
-
@furom do with out what.. You do not need to set that up, your free to do so if you want.. But your just sending all your dns to them on a silver platter.. What do you get in return? Maybe some malware/bad site filtering? You sure are not really hiding anything from your isp, etc.
The only reason to set that up - is you want to, for whatever reasons you might have for doing it. But out of the box pfsense/unbound is a resolver.. It has no need for any sort of dns setup or forwarding too, etc.
-
@johnpoz said in DNS & NTP best practice (vlans & IoT):
Maybe some malware/bad site filtering? You sure are not really hiding anything from your isp, etc.
True, the malware filters are nice, but guess pfBlocker can take on some of that. I don't try to hide anything, just merely keeping data somewhat private when possible
So another woe then... The list of resolver names I now have under
Status / DNS Resolver, I take it that is local to Ubound running on my pfSense and what my queries has asked for, right? But is the resolving between Ubound/pfSense and the root DNS's protected somehow or can it be? -
@furom said in DNS & NTP best practice (vlans & IoT):
But is the resolving between Ubound/pfSense and the root DNS's protected somehow or can it be?
Protected from who, from what? You mean can it be via an encrypted tunnel.. No
If you want to hide that from your isp, then route your dns queries through a vpn.. But no there is no method to talk to the roots or the gtlds via dot or doh, nor would you be able to talk to the authoritative ns for some domain via dot or doh either.
Now by default when you resolve you would be using dnssec, so the info you get from roots would be validated that its correct with that. But that only goes as far as the dnssec has been setup for the tld, the specific domain. Most of the tlds have been setup for dnssec - but pretty sure there are still some that have not setup dnssec..
And the use of dnssec for specific domains is way lower than it should be, so yeah there are many a domain that do not do dnssec, and then their are something that just F it up anyway trying to use it ;)
-
@johnpoz said in DNS & NTP best practice (vlans & IoT):
And the use of dnssec for specific domains is way lower than it should be, so yeah there are many a domain that do not do dnssec, and then their are something that just F it up anyway trying to use it ;)
Ok. Well, yeah. Things move slowly sometimes. Just look at the IPv6 "rollout". It was said IPv4 addresses were almost depleted, yet we still use them in what I believe most places still. I haven't felt the need really to switch to IPv6, and suppose it won't happen until there is a must or real benefit from doing that.
I would have liked it better if there were a tunnel to the root DNS's though, but well, can't have it all... lol -
@furom said in DNS & NTP best practice (vlans & IoT):
I haven't felt the need really to switch to IPv6, and suppose it won't happen until there is a must or real benefit from doing that.
I am with you.. I see it as the future sure - but I don't believe it is on the curve to adoption that they thought it would be. I have yet to find a resource - not one that would require me to have IPv6..
I have zero use for it myself, and it is pretty much off.. My current isp doesn't even provide it native hehe.. and have not even seen any mention of it even being on their radar.. I have used a tunnel from HE for years and years for my access to Ipv6, but its only for learning and playing.. I do not use it on any of my devices in any sort of production.. I turn it on a device when I want to play/test something. I use to provide my ntp server to the pool over both ipv4 and ipv6, but have turned that off.. It was more of learning curve thing anyway.. I have no real desire to provide services to the public internet ;)
Part of the problem to be honest, is the adoption of IPv6 for stuff like phones that require a vast amount of IPs to use - how many billions of phones are on the planet.. My phone does not get an IPv4 address, it gets IPv6 only for cell data - when it wants to go to an IPv4 address the cell providers network handles that connection via their 464xlat setup..
So them moving away from IPv4 freed up a bunch of IPs to use for other stuff. There is pretty active market in selling your IPv4 space to those that need it.. And you can make some good money, I was directly involved in the sale of some of the /16 in my old company.. They really have actual need of small fraction of that space, were not using most of it. To be honest if they would be doing what arin suggests they would of returned most of that space to arin years and years ago. It was quite lucrative deal.. I got screwed out of my bonus that I should of gotten for coming up with it.. Suppose to get like 10% when you came up with any sort of out of the box thing that made the company money.. Should of gotten like 50k in that deal, they threw me a bone of 5k.. Bastards! ;)
There is just the cost for companies moving to it as well - at least internally.. And what driving force do they have - the migration sure isn't going to save them money, not even in the long run.. They have plenty of rfc1918 space to use on the company internal network.. They will not run out of that ever.. So where is the advantage of them moving to ipv6.. Sure you can play nice and throw up some public IPv6 access to your public facing servers.. That is pretty simple and easy to do, and really easy to get a /32 from Arin for your own IPv6 space.. Was involved in that whole process - has the company really done anything with it - no they have used some of it in a future project that not sure will ever go anywhere.. So some infrastructure is using IPv6 on the public internet - but there is no driving force for its use elsewhere in the company or other projects..
My new company, on the fortune 100 list, it is not a tiny network that is for sure.. While I am new and sure do not have a handle on everything going on in the company - Can tell you from study of all the network diagrams and info. IPv6 is no where that I see... And even the public site for website has no AAAA.. I might have to ask around if any IPv6 work planned anytime in the near future..
I more than for sure will retire before any real traction with IPv6 in the corporate landscape to be honest - I got 10 years.. So we will see I guess.. But if I could place a bet, I would and a very large sum that not much happens with it.. I use to see new customer networks all the time old company was a MSP.. Never once did get a customer that had used any IPv6 in their networks, nor any customers that had any real plans or drive to do so..
-
@johnpoz Oh well, as for coming up with cost savings, heck, even tech that introduced possibilities not there before - and not getting even the credit for it - been there done that, it sucks.
I also doubt I'll ever come to use IPv6 in any commercial way, and though it seems rather straightforward, it is many new things to remember and cope with. Maybe something for a really boring rainy summer, who knows... lol
I think you hit the nail there - cost of implementing. Why fix something that isn't broken? It's always hard to motivate. What I think of for myself is perhaps along the lines of future-proofing, preparing just enough to not having to do a complete overhaul if the rainy day comes... :)
-
@furom said in DNS & NTP best practice (vlans & IoT):
and though it seems rather straightforward
There is way more too it than just a longer address ;)
-
@johnpoz said in DNS & NTP best practice (vlans & IoT):
There is way more too it than just a longer address ;)
Yes, I'm aware of that, but not necessarily hard - pending on scope, just a different way of thinking (trying to stay positive about it)