Network Segmentation for Beginners?
-
In pursuit of security I'm beginning to segment my network to put "things" outside of my core network. I started with one VOIP phone and one security camera:
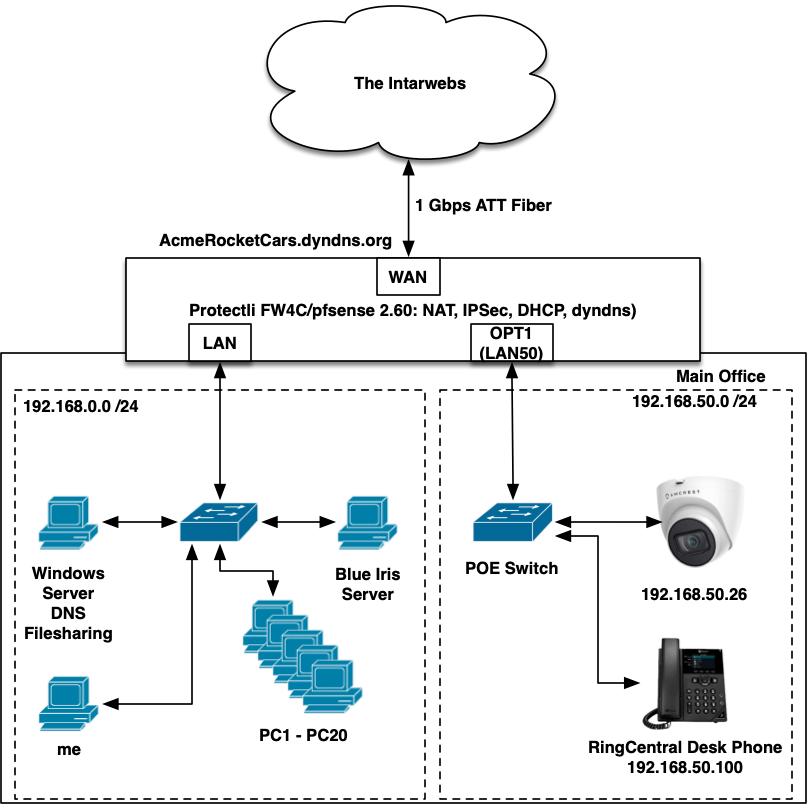
For today (and for learning) I need the Blue Iris NVR computer to be able to speak ONVIF to the camera, and for the camera to be able to send RTSP back to it.
Once I move all the cameras into the .50 network I will also move the Blue Iris box over there, and then everyone will view it from the WAN address and a port-forward.
I also want to be able to speak HTTP/HTTPS to the camera from inside the .0.0 network (e.g. the "Me" computer) to configure it directly.
Did I do this correctly? I can access the camera directly, and its feed shows up on my Blue Iris, but did I do "most restrictive, least permissive" correctly?
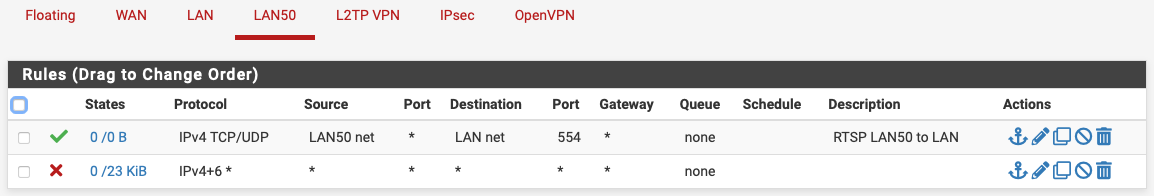
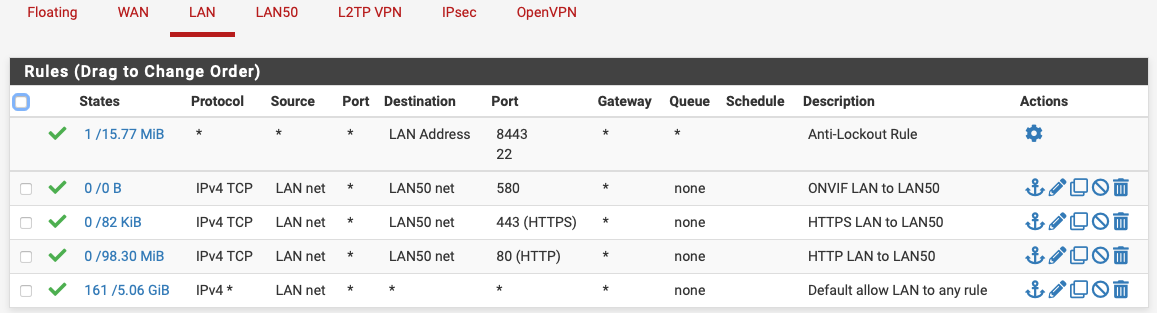
-
@thewaterbug re LAN50…that rule allows any device in LAN 50 to connect to any and all devices on LAN that are listening on port 554, is that really what you want?
-
My next step is to get the hosted VOIP (RingCentral) phone working without some sort of any/any rule.
RingCentral's documentation has this list of supernets (Section 2):
66.81.240.0/20 80.81.128.0/20 103.44.68.0/22 104.245.56.0/21 185.23.248.0/22 192.209.24.0/21 199.68.212.0/22 199.255.120.0/22 208.87.40.0/22I created an Alias, RingCentral_Supernets with these networks, and added this rule:
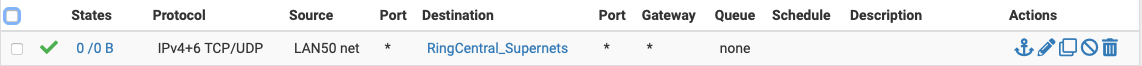
but that's not enough. The phone doesn't work.
Then there is this list of Domain name/IP addresses and Destination ports for desk phones (Section 3.2.6 from the above link):
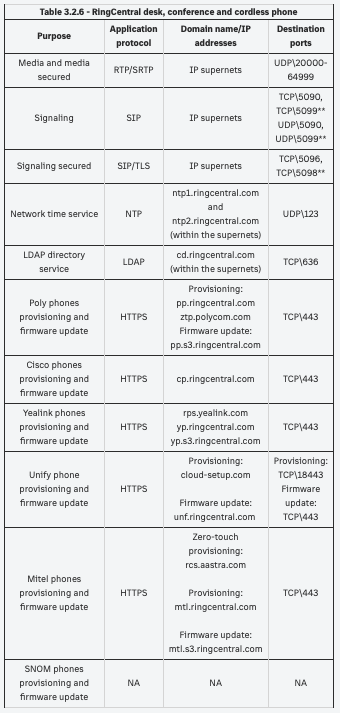
but I'm unsure of how to efficiently allow access to this set of destinations. Help!
-
@thewaterbug said in Network Segmentation for Beginners?:
In pursuit of security I'm beginning to segment my network to put "things" outside of my core network. I started with one VOIP phone and one security camera:

For today (and for learning) I need the Blue Iris NVR computer to be able to speak ONVIF to the camera, and for the camera to be able to send RTSP back to it.
Once I move all the cameras into the .50 network I will also move the Blue Iris box over there, and then everyone will view it from the WAN address and a port-forward.
I also want to be able to speak HTTP/HTTPS to the camera from inside the .0.0 network (e.g. the "Me" computer) to configure it directly.
Did I do this correctly? I can access the camera directly, and its feed shows up on my Blue Iris, but did I do "most restrictive, least permissive" correctly?


2 Things that stick out to me, the block rule on lan50, uneeded. It's already there even though you can't see it. With no rules everything is blocked, so adding another block rule is redundant.
Then, the LAN rules, you can delete all 3 of them since you have the default ANY rule still in place. It literally means ANY. So all 3 rules are incorporated in that one rule.1 bit of advice, use the packet scanner on lan50 to see what traffic is being generated and it'll tell you what ports you need.
-
Ah, good catch. I really only want RTSP to go to either the BI server or to my own PC. I just fixed that with an alias with the IPs of a few permitted machines. Thanks!
-
@jarhead said in Network Segmentation for Beginners?:
Then, the LAN rules, you can delete all 3 of them since you have the default ANY rule still in place. It literally means ANY. So all 3 rules are incorporated in that one rule.
Ok, I think I'm understanding things a bit better now.
But when I watched my first training on CMMC, they did tell me that one thing auditors will look for is a Deny Any/Any at the end of any rules list. And I think they will want me to (eventually) delete the ANY rule at the end, so that I permit only the traffic that has been identified as necessary for the operation of devices in each particular zone.
I'm not entirely sure how that will work for the PCs that run typically desktop applications, but I think I will need to move them out into an intermediate zone that's away from the Windows Server and other critical infrastructure, so that core network will not have an ANY rule once I get to that point.
-
@jarhead said in Network Segmentation for Beginners?:
1 bit of advice, use the packet scanner on lan50 to see what traffic is being generated and it'll tell you what ports you need.
That did it! I forgot to enable DNS for LAN50, but I just did that, and now my phone works.
-
@thewaterbug said in Network Segmentation for Beginners?:
Ah, good catch. I really only want RTSP to go to either the BI server or to my own PC. I just fixed that with an alias with the IPs of a few permitted machines. Thanks!
I think you'll find you don't need RTSP going to BI and definitely not to your pc.
The cameras will use http for viewing. -
Here's a typical camera setup within BI:
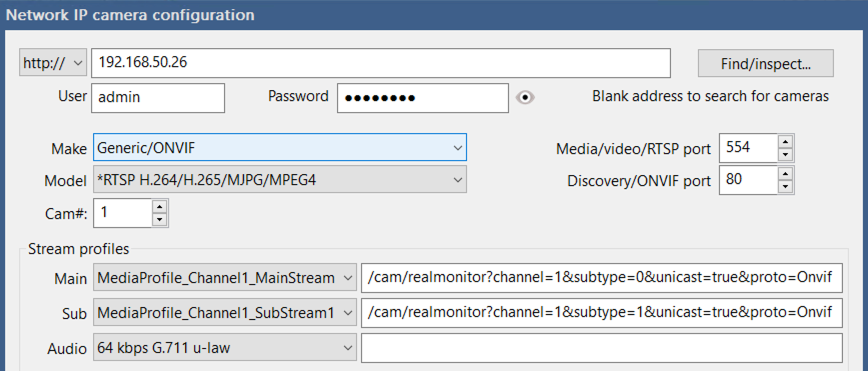
And then when I'm troubleshooting a camera setup from my PC I'll open the RTSP feed from within VLC to make sure I haven't screwed up the URI.
Yes, when viewing the camera through its internal web server I believe it uses HTTP for video.
-
@thewaterbug said in Network Segmentation for Beginners?:
That did it! I forgot to enable DNS for LAN50, but I just did that, and now my phone works.
And NTP. So now my phone has the correct time.
At least I know the firewall works!

-
More progress on this. I moved the Blue Iris (NVR) server to the .50 network:
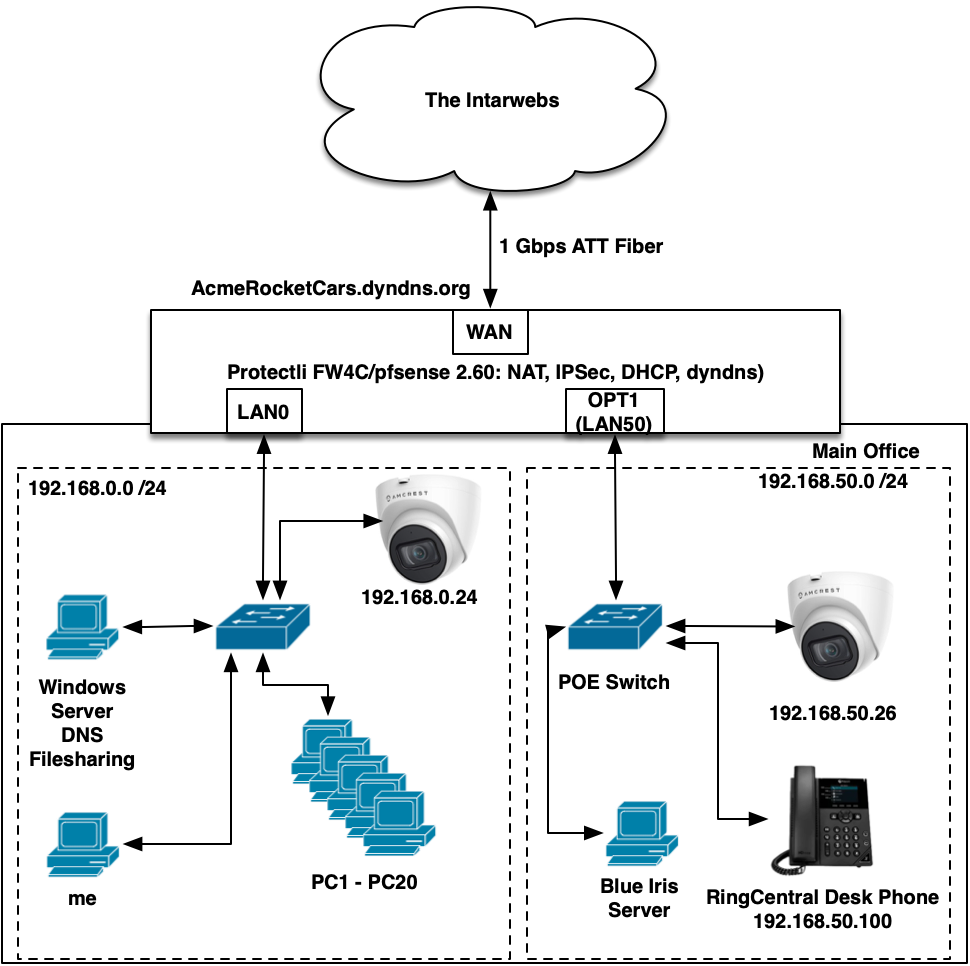
and experimented with the fw rules to figure out how to allow access to the cameras that are still inside .0, and eventually learned I had RTSP "backwards" because it's pulled from the camera and not pushed by the camera. And then I learned about ports aliases and condensed it all, thus:
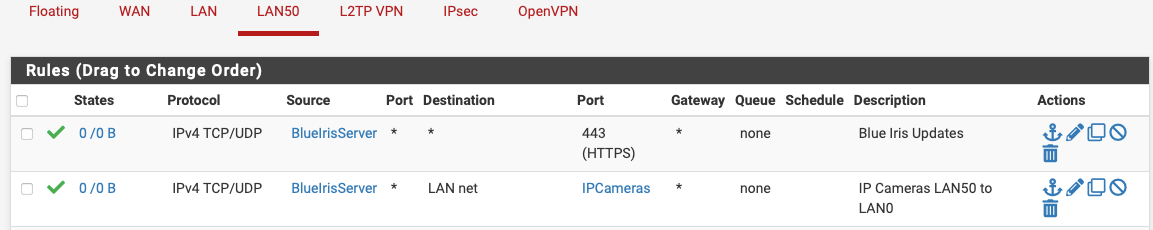
A bunch of this will be moot once I migrate all the cameras to LAN50, but it was a good exercise figuring out how to grant access without the default LAN any rule on the LAN50 side.
-
T TheWaterbug referenced this topic on
-
D Deadringers referenced this topic on