Update from 22.05 to 23.01 one bricked another with errors.
-
@itngo Since you mention “passive” is the 7100 in HA? There is this about auto crossover not working:
https://redmine.pfsense.org/issues/13993 -
That would not prevent it coming back up after the upgrade though. It would prevent config sync functioning if they're connected directly and the link is not a cross-over cable.
Steve
-
@stephenw10 said in Update from 22.05 to 23.01 one bricked another with errors.:
That would not prevent it coming back up after the upgrade though. It would prevent config sync functioning if they're connected directly and the link is not a cross-over cable.
Yeah, sorry, I answered too quickly...unrelated to the above but if OP is driving on site, might want to bring a crossover cable.
-
@stephenw10 said in Update from 22.05 to 23.01 one bricked another with errors.:
netstat -i
More or less....
Name Mtu Network Address Ipkts Ierrs Idrop Opkts Oerrs Coll ix0 1500 <Link#1> 3c:ec:ef:3d:45:86 51 0 0 68 0 0 ix0 - fe80::%ix0/64 fe80::3eec:efff:f 0 - - 2 - - ix0 - 10.255.102.0/ 10.255.102.200 48 - - 59 - - ix1 1500 <Link#2> 3c:ec:ef:3d:45:87 2550884280 13506 0 2336847 0 0 ix1 - fe80::%ix1/64 fe80::3eec:efff:f 0 - - 1 - - ix1 - 185.250.90.0/ 185.250.90.251 612424 - - 990 - - ix1 - 185.250.88.25 185.250.88.252 1351705 - - 0 - - ix1 - 185.250.91.25 185.250.91.252 655286 - - 0 - - ix1 - 185.250.90.0/ 185.250.90.253 0 - - 0 - - ix1 - 185.250.89.0/ 185.250.89.253 0 - - 0 - - ix1 - 185.250.91.0/ 185.250.91.253 0 - - 0 - - ix1 - 185.250.88.0/ 185.250.88.253 0 - - 0 - - ix1 - 185.250.89.25 185.250.89.252 170184 - - 0 - - ixl0 1500 <Link#3> 00:e0:ed:88:5e:c6 54902978 99 4294822888 281475420885107 0 0 ixl0 - fe80::%ixl0/6 fe80::2e0:edff:fe 0 - - 1 - - ixl0 - 185.54.108.0/ RZB-BGP01 4603809 - - 7156544 - - ixl1 1500 <Link#4> 00:e0:ed:88:5e:c7 92188931 0 4294822671 281474980273727 0 0 ixl1 - fe80::%ixl1/6 fe80::2e0:edff:fe 0 - - 1 - - igb0* 1500 <Link#5> ac:1f:6b:fe:93:92 0 0 0 0 0 0 igb1* 1500 <Link#6> ac:1f:6b:fe:93:93 0 0 0 0 0 0 lo0 16384 <Link#7> lo0 0 0 0 0 0 0 lo0 - localhost localhost 0 - - 0 - - lo0 - fe80::%lo0/64 fe80::1%lo0 0 - - 0 - - lo0 - your-net localhost 0 - - 0 - - enc0* 1536 <Link#8> enc0 0 0 0 0 0 0 pfsync0 1500 <Link#9> pfsync0 0 0 0 18 0 0 pflog0* 33152 <Link#10> pflog0 0 0 0 0 0 0 ixl1.44 1500 <Link#11> 00:e0:ed:88:5e:c7 3157148 0 0 3349773 5 0 ixl1.44 - fe80::%ixl1.4 fe80::2e0:edff:fe 0 - - 1 - - ixl1.44 - 10.255.144.0/ 10.255.144.253 3141508 - - 3304409 - - -
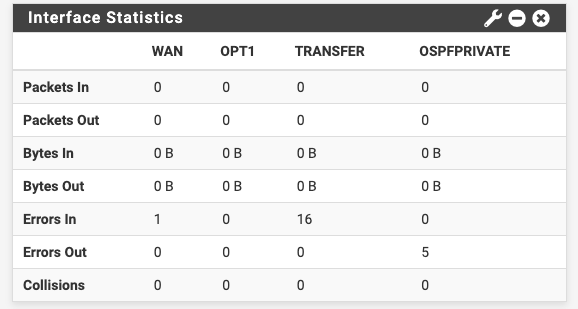
There's a lot more traffic shown there. Is the Interface Stats widget also showing that now?
-
@stephenw10
No, at least still nothing after 6 days runtime.

-
Hmm, what about in Status > Interfaces?
-
@stephenw10
Also empty...
-
About the 7100u.
I am onsite and have USB-Console Connection. The system is looks OK from console with 23.01 but there is no Network-Access overall. A ping from console brings just "Network is down". -
No default route perhaps?
Go to System > Routing > Gateways and make sure the main WAN gateway is set as default.
Possibly this issue: https://redmine.pfsense.org/issues/14057
Steve
-
@stephenw10
Unable, as we can not access the WebGUI. Even a Ping form same Subnet is not possible.... -
Hmm, OK that's a lower level issue then.
Is DHCP working?
Is the firewall pulling an upstream WAN IP?
When you tried to ping from the console and it failed what were you trying to ping? Is it unable to ping out on any interface?
Steve
-
@stephenw10
Thank for reply,It can not even Ping its Master pfsense which is still on 22.05.
So no Ping on LAN, WAN or opt-interfaces.
All static IPs.. -
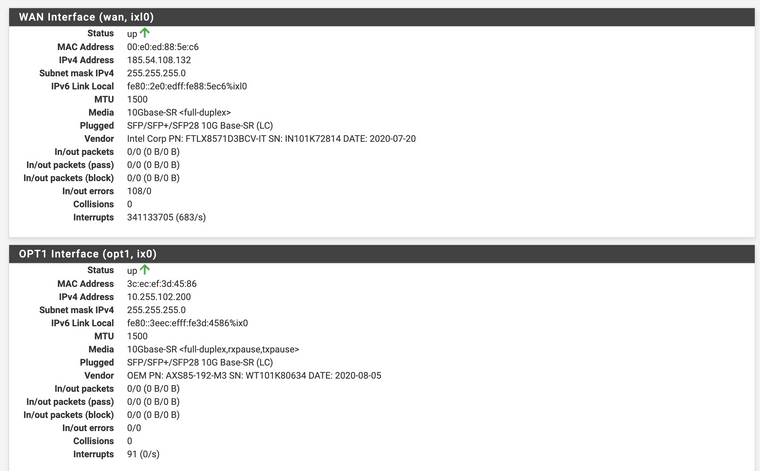
Hmm, are the interfaces linked? NIC link LEDs lit?
Doesifconfig -vashow them as UP with the correct link type?
etherswitchcfgmight be useful there too if you're using the switches interfaces. -
@stephenw10 said in Update from 22.05 to 23.01 one bricked another with errors.:
etherswitchcfg
Yes, ports are active, LEDs are worling and ifconfig -va as also etherswitchfg confirms connections.
-
Hmm, you can't even ping to or from the other node over the sync connection? Is that directly between them?
Can we see the actual error output it shows?
Steve
-
Direct Connection via 10GBe for Internal and HP Switch for other lines.... Node 1 is exactly connected the same way and still works normally....
[23.01-RELEASE][root@pfSense2.jgs.local]/root:
Message from syslogd@pfSense1 at Mar 13 18:33:29 ...
php-fpm[92160]: /firewall_rules.php: Successful login for user 'admin' from: xx (Local Database)
ping 192.168.168.1
PING 192.168.168.1 (192.168.168.1): 56 data bytes
^C
--- 192.168.168.1 ping statistics ---
3 packets transmitted, 0 packets received, 100.0% packet loss
[23.01-RELEASE][root@pfSense2.jgs.local]/root: ping 192.168.168.2
PING 192.168.168.2 (192.168.168.2): 56 data bytes
64 bytes from 192.168.168.2: icmp_seq=0 ttl=64 time=0.173 ms
64 bytes from 192.168.168.2: icmp_seq=1 ttl=64 time=0.082 ms
64 bytes from 192.168.168.2: icmp_seq=2 ttl=64 time=0.069 ms
^C
--- 192.168.168.2 ping statistics ---
3 packets transmitted, 3 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 0.069/0.108/0.173/0.046 ms
[23.01-RELEASE][root@pfSense2.jgs.local]/root: ping 192.168.168.1
PING 192.168.168.1 (192.168.168.1): 56 data bytes
^C
--- 192.168.168.1 ping statistics ---
5 packets transmitted, 0 packets received, 100.0% packet loss
[23.01-RELEASE][root@pfSense2.jgs.local]/root: ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8): 56 data bytes
^C
--- 8.8.8.8 ping statistics ---
8 packets transmitted, 0 packets received, 100.0% packet loss -
Ok, so it can ping itself. The network stack is up at least.
Make sure routes exist:
netstat -rnYou're using only the 10G SFP ports, ix0 and ix1?
Do you see all the expected interfaces present in ifconfig?
-
@stephenw10
Yes all interfaces are present and routes are in place.
[23.01-RELEASE][root@pfSense2.jgs.local]/root: netstat -rn
Routing tablesInternet:
Destination Gateway Flags Netif Expire
default 82.198.xxx.xxx UGS lagg0.40
10.10.10.1 link#15 UH lo0
10.42.1.0/24 link#21 U lagg0.40
10.42.1.2 link#21 UHS lo0
10.42.10.0/24 10.42.1.240 UGS lagg0.40
10.42.11.0/24 10.42.1.240 UGS lagg0.40
10.42.12.0/24 10.42.1.240 UGS lagg0.40
10.42.13.0/24 10.42.1.240 UGS lagg0.40
10.42.14.0/24 10.42.1.240 UGS lagg0.40
10.42.16.0/24 10.42.1.240 UGS lagg0.40
10.42.96.0/24 link#23 U lagg0.96
10.42.96.2 link#23 UHS lo0
10.255.42.0/24 10.42.1.3 UGS lagg0.40
10.255.42.1 link#21 UHS lagg0.40
10.255.192.0/24 10.42.1.3 UGS lagg0.40
82.198.xxx.168/29 link#20 U lagg0.40
82.198.xxx.172 link#20 UHS lo0
127.0.0.1 link#15 UH lo0
192.168.168.0/24 link#1 U ix0
192.168.168.2 link#1 UHS lo0
192.168.178.0/24 link#24 U lagg0.40
192.168.178.3 link#24 UHS lo0Internet6:
Destination Gateway Flags Netif Expire
::1 link#15 UHS lo0
fe80::%ix0/64 link#1 U ix0
fe80::208:a2ff:fe10:d096%ix0 link#1 UHS lo0
fe80::%lo0/64 link#15 U lo0
fe80::1%lo0 link#15 UHS lo0
fe80::%lagg0/64 link#19 U lagg0
fe80::208:a2ff:fe10:d098%lagg0 link#19 UHS lo0
fe80::%lagg0.4090/64 link#20 U lagg0.40
fe80::208:a2ff:fe10:d098%lagg0.4090 link#20 UHS lo0
fe80::%lagg0.4091/64 link#21 U lagg0.40
fe80::208:a2ff:fe10:d098%lagg0.4091 link#21 UHS lo0
fe80::%lagg0.7/64 link#22 U lagg0.7
fe80::208:a2ff:fe10:d098%lagg0.7 link#22 UHS lo0
fe80::%lagg0.96/64 link#23 U lagg0.96
fe80::208:a2ff:fe10:d098%lagg0.96 link#23 UHS lo0
fe80::%lagg0.4092/64 link#24 U lagg0.40
fe80::208:a2ff:fe10:d098%lagg0.4092 link#24 UHS lo0 -
Ok so it looks like you're using ix0 directly and everything else is via VLANs on lagg0. Can I assume lagg0 is still the internal connection to the switch, ix2 and ix3?
As a test try disabling pf:
pfctl -dIf the ruleset is not loading fully it might be blocking outbound traffic.
Usepfctl -eto re-enable it.Steve