WAN Modem and VLAN Firewall Rules
-
@4rr3n Devices on LAN would normally be able to access the ISP router/modem so yes you’ll need block rules. Just allow your PC if you want to connect.
The pfSense WAN has a hidden default block rule (well all do but LAN adds a default allow all rule).
-
@steveits The problem with the Modem I struggle is this, the presented video doesn't assing a local IP address, therefore I struggle in making a firewall rule to block VLANs from accessing its Web GUI.
The modem doesn't have any IP except its own when you for example connect a direct RJ45 cable to access its web interface via a laptop. Except this, I'm not sure how I can access its web interface in pfSense per what I wrote above about the local IP Address.
I think I have read something about that, I think it's called WAN Mirroring or WAN Reflection or something like that. I tried to find the link but can't find it.
Since WAN has default block rules and its own firewall settings, wouldn't be easier to just add a rule to it that says this VLAN and that VLAN can't access its Web GUI ? It also sounds easier than adding the block rules on each VLAN interface.
From my understanding is this, I just need to add a block firewall rule on the VLANs to block them from accessing the Modem's Web GUI but can't really do that since it doesn't have local IP assigned by pfSense.
I'm a bit confused here and would need a bit of guidiance on how I can progress with this as I have been stuck on it for a long time.
Big Edit:
Is this solution to my problem ?
How to access your modem webpage on pfSense.From the 3minute video above, I have gathered that you assign local IP Address to your Modem then do NAT translation rule between your Modem's IP and pfSense instance. Then I can use that local IP in VLAN rules to block the Web GUI ?
My only two questions remains here are:
- Which NAT Mode do I select: Hybrid or Manual ?
- Since it's a NAT translation, does that pose or expose anything externally on the WAN side ? I don't want to expose any part of my network on the WAN side.
Any help is appreciated.
Thanks -
@4rr3n I can only speak for what I've seen...Comcast business routers in bridge mode, or the third party modem I have at home, do have a private IP address. If I try to connect to the modem's IP address, it just works. So to block connecting from a VLAN to that IP I would use a rule to reject from the VLAN network to the modem IP, port 80 and/or 443.
NAT forwarding is used for inbound connections, from the Internet to a private IP address on an internal network that is behind NAT. NAT reflection is used if a device on the internal network needs to make a connection using pfSense's WAN IP. If you set up a NAT port forward you can limit the source of the rule to not allow the entire Internet to connect in to your PC.
However your modem would be in front of your pfSense so NAT would not apply here.
Hybrid/manual refers to outbound NAT which is used to connect out using a non-standard setting for instance a second public IP address or to not use source port randomization.
-
@4rr3n said in WAN Modem and VLAN Firewall Rules:
lock firewall rule on the VLANs to block them from accessing the Modem's Web GUI but can't really do that since it doesn't have local IP assigned by pfSense.
huh? A typical "modems" ip you can use to access its gui is 192.168.100.1, you could for sure block said access with a simple firewall rule on any of your local pfsense interfaces.
What is the IP your using to access this gui?
Lets say its 192.168.100.1
This sort of simple rule would prevent that.
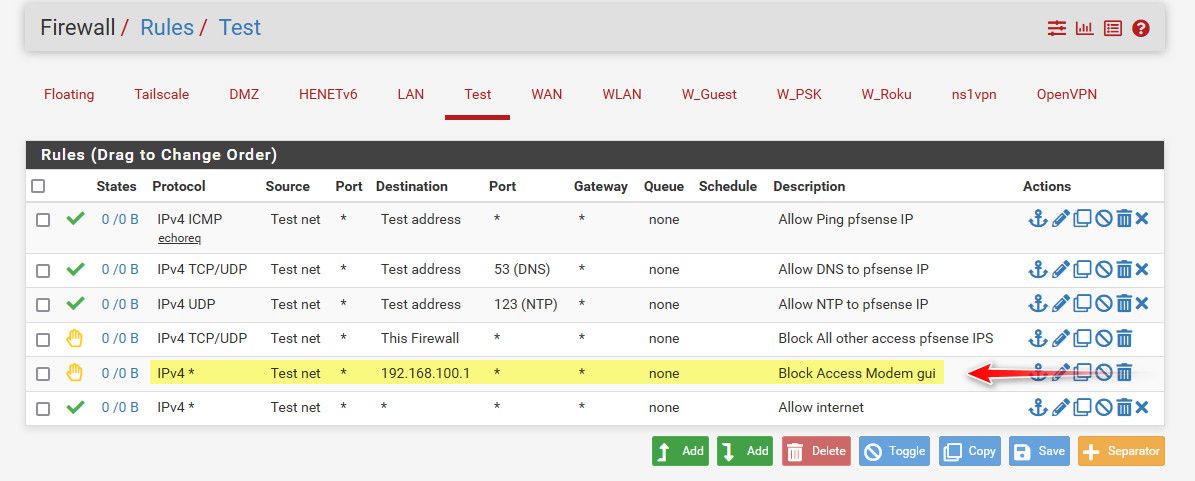
If your having issues with access the gui from anything on your network, then yeah a vip on whatever IP your modem is using on your wan, and then a simple outbound nat via hybrid
Like so
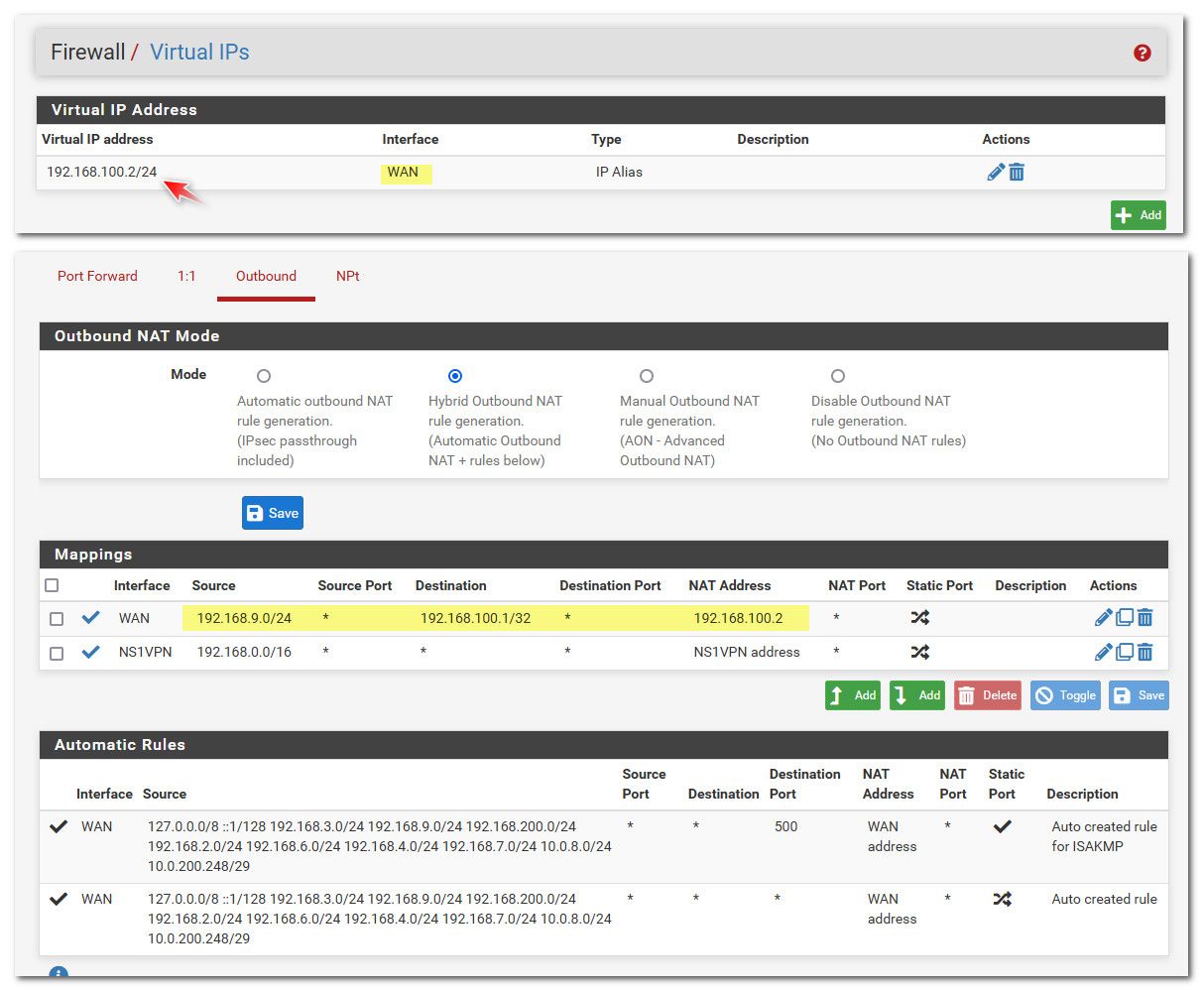
This would nat any IP on my 192.168.9/24 lan network trying to go to the 192.168.100.1 address to my vip 192.168.100.2 address.
-
@SteveITS Thanks for the explanation, it makes things way easier to understand now.
@johnpoz Interesting to see a different ways of doing the same thing in pfSense. Thanks for providing instructions\screenshots as it helps out a lot.
Out of curiosity, I also found this link in the official pfSense documentation, is this the same thing you did above with the NAT but doing it in a different way instead ?
Thanks
-
@4rr3n that is exactly what I did, but instead of using the net, I used the specific address with the /32 mask.
-
I have tried to make the Web GUI of the modem work via pfSense but I have been struggling with it for the past 4/5 hours. I don't know if I do something wrong or what but it just doesn't seem to work. I can't load the Web GUI via pfSense but when I connect directly to the modem via RJ45 cable, it just works.
I followed @johnpoz instructions\screenshots and no go.
I followed this instructions with no success.
I also followed this video as I have exactly the same Modem setup and still no go.I have also tried doing the reboot of the pfSense, make sure that the IP of the firewall and modem are different and still nothing.
Yes, I made sure my modem is in bridged mode. Also, does anyone know if the IP range of the firewall and modem needs to be kind of similar like:
Firewall: 10.X.6.X
Modem: 10.X.8.Xor can you mix it like:
Firewall: 10.X.X.X
Modem: 192.168.X.XI think I'm at my wits end with this as no matter what I do, it just doesn't work.
Any suggestions please ?
-
@4rr3n The subnet used by different routers needs to be:
- different, if they are different networks
- the same if they are the same network (e.g. the ISP router is your WAN gateway)
Whether they are "similar" is irrelevant. Do note your LAN subnet needs to be different than the ISP router private IP, since the same subnet can't exist on both sides of a router...or the packet will not get sent to/through the router.
Your original question was how to block connections to the ISP modem. Are you now trying to access it and can't? Can you post your LAN firewall rules?
With the two ISPs we use most often, Comcast/Xfinity and AT&T, I can just browse to the ISP router private IP from LAN.
-
@4rr3n what modem do you have exactly?
-
Not sure if this applies in this case...
I had a backup WAN with 4G LTE modem in a bridge mode in its own interface (WAN_LTE) on pfSense.
The 4G modem management ip was 192.168.8.1Sorry about the code snippets here, had to dig an old config file...
Static route for the modem ip
<staticroutes> <route> <network>192.168.8.1/32</network> <gateway>WAN_LTE</gateway> <descr><![CDATA[4G LTE Modem]]></descr> </route> </staticroutes>Rule in the LAN interface to allow/policy route to modem management ip
<rule> <type>pass</type> <interface>lan</interface> <ipprotocol>inet</ipprotocol> <protocol>tcp</protocol> <source> <network>lan</network> </source> <destination> <address>192.168.8.1</address> </destination> <descr><![CDATA[Allow access to 4G LTE bridge management]]></descr> <gateway>WAN_LTE</gateway> </rule>Also not sure if this was the correct way to do it, probably a quick&dirty way, but it worked...

-
@4rr3n said in WAN Modem and VLAN Firewall Rules:
I have tried to make the Web GUI of the modem work via pfSense but I have been struggling with it for the past 4/5 hours. I don't know if I do something wrong or what but it just doesn't seem to work. I can't load the Web GUI via pfSense but when I connect directly to the modem via RJ45 cable, it just works.
I followed @johnpoz instructions\screenshots and no go.
I followed this instructions with no success.
I also followed this video as I have exactly the same Modem setup and still no go.I have also tried doing the reboot of the pfSense, make sure that the IP of the firewall and modem are different and still nothing.
Yes, I made sure my modem is in bridged mode. Also, does anyone know if the IP range of the firewall and modem needs to be kind of similar like:
Firewall: 10.X.6.X
Modem: 10.X.8.Xor can you mix it like:
Firewall: 10.X.X.X
Modem: 192.168.X.XI think I'm at my wits end with this as no matter what I do, it just doesn't work.
Any suggestions please ?
On many modems/routers, when in "real" bridge mode, you will not be able to access it's management UI on the bridged port. As an example, the router that my parents have, can be set up in bridge mode but only for port #4. Anything connected to that port will get the Public IP directly from the ISP. Basically full pass thru from WAN to port 4 on the router, and no visibility towards LAN or management UI. Only ports #1-3 can be used to access the management UI...
This is typically the best way to set things up, as you don't have to worry about double NAT and any possible problems that could come out of that. Also, no one can access the management UI of the modem unless physically connecting to one of the other ports on the modem. So if this is the case, you just set pfsense to DHCP (or whatever setting your ISP instructs you to), and you are good to go. No worries about VLAN's being able to access the modem.
Other modems may call it "bridge mode" but in reality it's a DMZ (all ports open) setup but still double NAT.
If that is the case you need to:- Make sure you have different LAN IP range on modem and pfsense. For example 192.168.1.0/24 on pfsense, and 192.168.10.0/24 on modem.
- In the management UI, give pfsense a static IP (MAC based), which then will be the IP that is put in "bridge mode" or DMZ.
- In pfsense you set WAN port to DHCP and it will get the static IP from the modem.
For starters, this would allow you to access the management UI on 192.168.10.1 from inside pfsense.
Step two is to add rules to all VLAN's to block access to 192.168.10.0/24. Similar to @johnpoz suggestion above, although I'd do a full block of the entire range for simplicity. -
@gblenn @johnpoz @SteveITS @mvikman Thanks for helping me out with this one, your knowledge and provided information helped a ton. This whole setup was a nightmare to configure. After taking a short break, I started over and finally managed to set it up. However, I still have two remaining questions.
From my testing, it looks like the virtual interface that is used for PPPoE to pass over the traffic from VDSL line also have access to the Web GUI of the modem that is accessed via its own physical LAN interface. I was able to confirm this by pinging LAN interface of the Modem from the WAN interface in pfSense.
Is this normal behaviour for this type of setup or should I worry as things are not correctly configured ? On the surface, now everything works how I want it to but not sure about this one as I don't want to expose anything on the WAN side.
The last question I have is, my modem provides ports to use like SSH, I tried to find more information about this but was unable to find anything online. The Modem settings only give me ability to allow or deny access to the said port on the LAN side but not WAN, does anyone know if Modems by default expose any such ports on the WAN side when used in bridged mode ?
I appreciate all the help I'm getting here, I know it's a lot of questions I'm asking but I'm new to pfSense and haven't dealt with such a setup before.
-
@4rr3n said in WAN Modem and VLAN Firewall Rules:
@gblenn @johnpoz @SteveITS @mvikman Thanks for helping me out with this one, your knowledge and provided information helped a ton. This whole setup was a nightmare to configure. After taking a short break, I started over and finally managed to set it up. However, I still have two remaining questions.
From my testing, it looks like the virtual interface that is used for PPPoE to pass over the traffic from VDSL line also have access to the Web GUI of the modem that is accessed via its own physical LAN interface. I was able to confirm this by pinging LAN interface of the Modem from the WAN interface in pfSense.
Is this normal behaviour for this type of setup or should I worry as things are not correctly configured ? On the surface, now everything works how I want it to but not sure about this one as I don't want to expose anything on the WAN side.
The last question I have is, my modem provides ports to use like SSH, I tried to find more information about this but was unable to find anything online. The Modem settings only give me ability to allow or deny access to the said port on the LAN side but not WAN, does anyone know if Modems by default expose any such ports on the WAN side when used in bridged mode ?
I appreciate all the help I'm getting here, I know it's a lot of questions I'm asking but I'm new to pfSense and haven't dealt with such a setup before.
Not entirely sure what you mean "virtual interface has access to web GUI"? The LAN side of the modem is protected and separated from it's WAN side by the firewall built into the modem/router. The fact that you can ping, and access it, from pfsense is like I wrote above. You should in fact be able to ping the LAN side of the modem from any device behind pfsense, unless you explicitly block that.
If you try to ping from the WAN side (your actual public IP) your modem will probably not even reply. SSH is a safeguard to be able to access the modem in case the GUI isn't working, or for more advanced control of the device. You can safely turn that off!
And IF for some reason it is available on the WAN side, you should absolutely turn it off...Bridged mode (or DMZ) means that all ports are "passed on" to pfsense, and it's pfsense responsibility to be the firewall, which it does in an excellent way of course. But there is no simple means of accessing ports on the modem, "reaching in from the outside and somehow in between" the modem and pfsense...
The only reason I can think of a modem exposing a port would be if the ISP has it set up for remote support. But I doubt they would use a known port like SSH... Probably some random port very high up then...