DNS - higi.com - Attacks on my DNS Server with random IP Addresses
-
Hello.
A week into using PFSense and I installed ntopng.
While in [Flows], I noticed many entries hitting my DNS Server from supposedly a domain named higi.com. It does not use the same IP address, so chances are, this is a spam bot implanted on victim computers.
Here is a screenshot of the attacks.
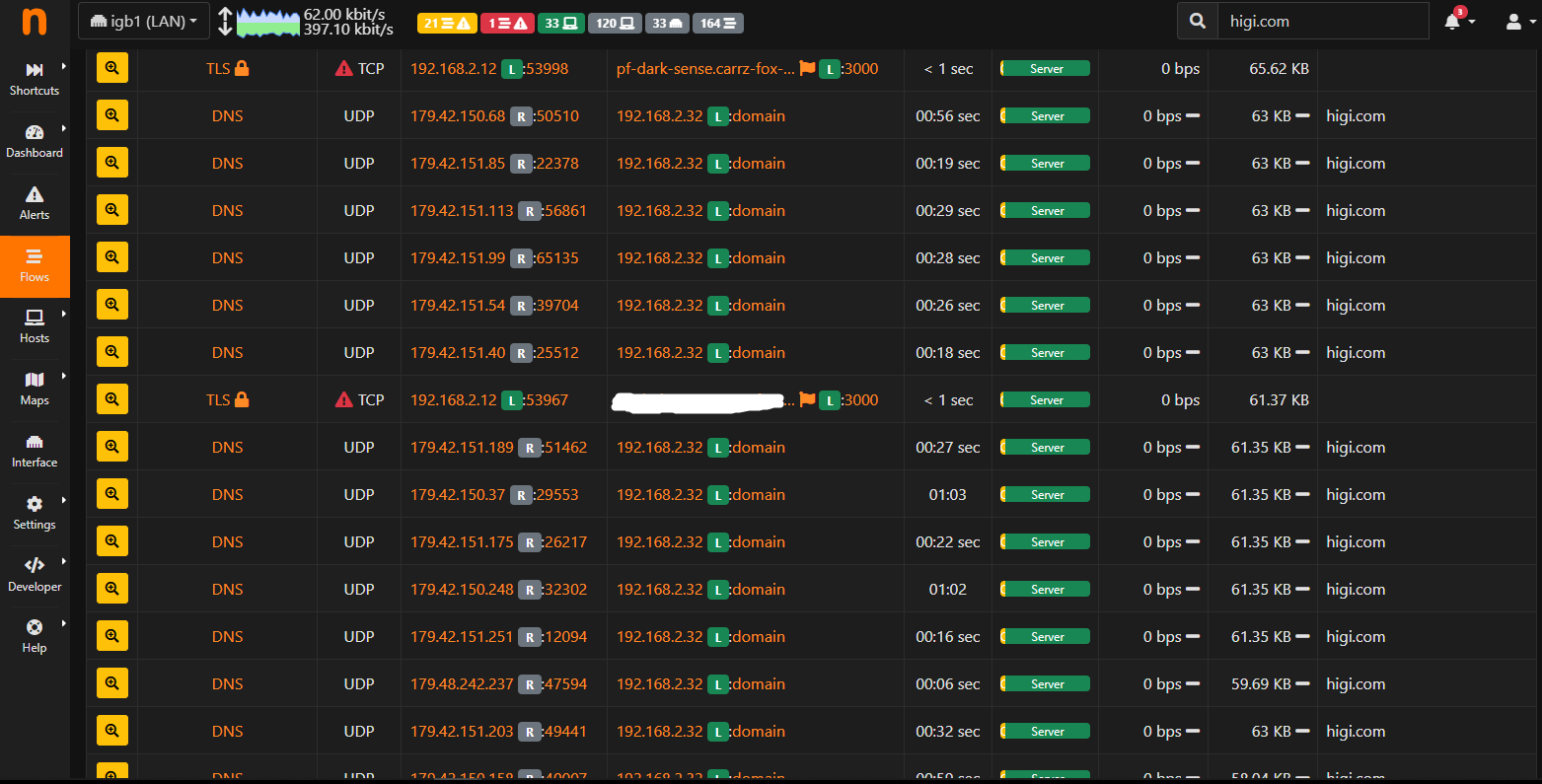
I've never noticed these types of attacks before, but then again, I was not running a system like PFSense where I could easily monitor it.
So, the question is.
How to stop this?
Most will say to block traffic on my DNS Server, but I cannot. I am running a web service, so the DNS has to be live in order for the sites to be available, so blocking the ports is not an option.Thank all.
Wayne -
@carrzkiss said in DNS - higi.com - Attacks on my DNS Server with random IP Addresses:
Most will say to block traffic on my DNS Server, but I cannot. I am running a web service, so the DNS has to be live in order for the sites to be available, so blocking the ports is not an option.
The issue was solved some decades ago ^^
That is, if your DNS is running on world's most know 'Internet OS' : Debian and friends, FreeBSD etc.
Microsoft : can't tell ...I protect my web mail and DNS servers with a tool that follows the log files of these apps.Assoon As this tool detects that an IP is 'spamming' it will block that IPv4 or IPv6 for a while.
The log parsing is done by classic regex filters.
The tool is called fail2ban.My pfSense is a @work and @home. My eb mail DNS etc are hosted on dedicated servers, out there in the wild.
edit : here it is At any giving time, some 10k IP's are blacklisted. The quantity is a bit fluctuating.
-
@carrzkiss Dude while ok if you want to run your authoritative NS on your network for your domain ok sure.. I wouldn't ever do it in a million years.. But you do you - but what do you think is going to happen when you run recursive dns open to the public??
If your going to run dns for your domain(s) fine - but it shouldn't resolve anything else.. I just hit your IP asking for google - and got response..
;; QUESTION SECTION: ;www.google.com. IN A ;; ANSWER SECTION: www.google.com. 300 IN A 108.177.122.105 www.google.com. 300 IN A 108.177.122.104 www.google.com. 300 IN A 108.177.122.106 www.google.com. 300 IN A 108.177.122.147 www.google.com. 300 IN A 108.177.122.103 www.google.com. 300 IN A 108.177.122.99 ;; Query time: 82 msecYour dns should only answer for the domains its authoritative for...
edit: I see your using buddydns.com as your secondary NS for your domain.. They are not recursive, if I ask them for google.com they refuse, which is how you run an authoritative NS
; <<>> DiG 9.16.36 <<>> @b.ns.buddyns.com www.google.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 57839 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;www.google.com. IN A -
@johnpoz Thanks.
To be honest, I thought I had DNS Recursive disabled. I might have tested the DNS Server a while back and got sidetracked and forgot to change it.
I have now disabled it again and will monitor it.I have been running my own DNS for years without issues I am aware of until now.
Thank you both for your information and insight.
Wayne -
@carrzkiss said in DNS - higi.com - Attacks on my DNS Server with random IP Addresses:
without issues I am aware of
Been there - seen that.
And I still don't see what I ... do not see.I just double checked my own config (it's a bind domain master), and found :
options { ...... allow-query { any; }; recursion yes; ..... };So I went OMG mode. I was 'no' in the past. But things change.
But then, I recalled that that is actually the advised option these days withallow-recursion { 127.0.0.1; ::1; };for good manners.
-
@carrzkiss why would you be running a 1 second TTL? That is just insane! Even for your NS records??
-
@johnpoz
I followed the information from a video on how to do the SSL from LetsEncrypt, and they set it for that.
I set it for 1 second for testing and forgot to set it back. Has been at 1 second for a week.All my TTLs are 1 hour and have been since I started doing this in 2000. And has just been set back.
The cool thing about others checking out your work is they, as long as they know what they are looking for or looking at, will catch what you might have missed or, in my case, forgotten.Thanks.
-
Here, an automated 'other' for you https://www.zonemaster.net/
Your mission :
After every change you make to a zone file for a domain, use this or another DNS checker.
And when you think you're done : go for a zero fault with this one : https://dnsviz.net/
@carrzkiss said in DNS - higi.com - Attacks on my DNS Server with random IP Addresses:
I set it for 1 second for testing
See https://github.com/acmesh-official/acme.sh/blob/799e402077f7430895c98d445e0d61cdec16b64a/dnsapi/dns_nsupdate.sh#L31 which is 60 seconds, and still qualifies 'insane', but that zone record added by acme.sh will only exist during verification, as it is deleted afterwards.
The (probably) real goal is : the slave(s) have to sync the added record before verification by LE can take place. Some slaves sync up = XFER right after they receive the notification from the master. Other take 'ages' to do so'. That's why the acme.sh 'dnssleep' is needed. -
@carrzkiss said in DNS - higi.com - Attacks on my DNS Server with random IP Addresses:
All my TTLs are 1 hour and have been since
Still showing your NS as 1 second
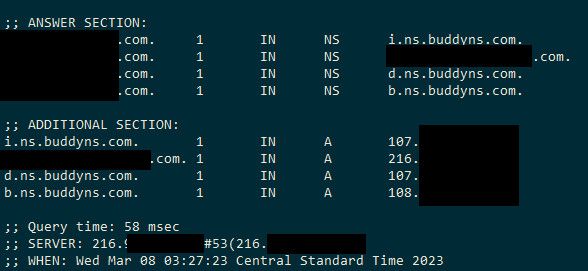
As well as the A record for just your domain.
Your NS records should be much higher than 1 hour anyway.. A records ok, but the NS there is no reason for them to only be an hour.
I would do a full double check - also showing other issues.. Wrong IP in parent for your NS, etc.
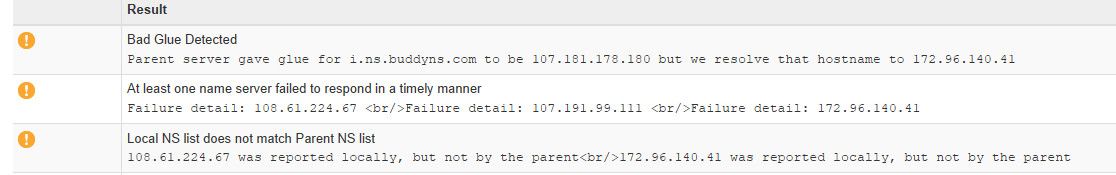
I just asked all the buddydns ns you have listed, and none of them answered for your domain. They all gave me REFUSED..
I only show 1 of your entries for your buddy NS actually matching, and he doesn't answer for your domain
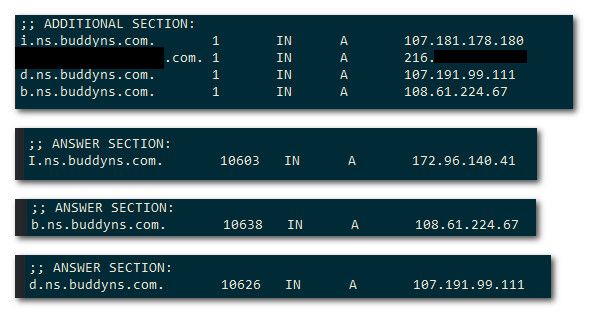
The (probably) real goal is
Agreed, I use a sleep of 180 seconds and have no issues with using acme with cloudflare as the NS for my domains I use ACME with..
Changing the ttl to one second, what you going to change to this every time your acme updates?
-
@johnpoz @Gertjan
Thanks a lot, guys.
OK, so it seems that one of the domains was 3 days past due on Renewal (It just took over an hour to get it renewed because Domain.com's site is messed up, so I had to wait in chat for over an hour to chat with someone and get the domain renewed.
Time to find a new Domain Reservoir to go to, as domain.com has had way too many issues over the last year.)BuddyNS
When I was working on PFSense and setting it up, the sites were unreachable for several days, so BuddyNS removed them.
Only one of my sites stayed, but not sure why.
All sites are now listed back with BuddyNS.I have to wait until later tonight or tomorrow for zonemaster.com to pick up on the updated information, as it is still picking up on the domain.com's crap.
Once again. I would like to thank both of you for being there and helping with stuff I might have completely overlooked.
And in this case, the BuddyNS would have been overlooked altogether. -
@carrzkiss Don't get me wrong this sort of stuff can be invaluable in learning how to run dns and the inner workings.. But they are also examples why I would never do it..
I come from the age before there were world wide anycast networks with pops all over the world that will host your dns, either for "free" or for less money then it cost to power your server most likely ;) I would be hard pressed to find a reason why I would host my own public facing dns on my own infrastructure today.. Maybe you run the hidden master on your network..
Let the big dogs maintain all the details to be honest.. There are plenty to choose from.. Let them handle the possible dos attacks, the amplification attacks, etc.
They offer very advanced features of dns with a click, dnssec for example - you pretty much flip a toggle and your domain is now dnssec, etc. They have api's for some really advanced stuff, failover for services that if go down the dns will point elsewhere automagically, etc..
If your site is production, and needs to be up - why let something like dns bring down your site, etc. And you actually pay for it - you prob have a SLA that would be almost impossible to maintain without crazy time and effort and money putting in the requirements to maintain say even 3 or 4 9s, etc.
I am more than happy to help in anyway I can run your own - but I personally wouldn't do it. I don't even run my personal dns anymore for play sites.. Where I have a few users.. I did back in the early days of dnssec as a learning curve on what you had to do - the drawback then was actually finding a registrar for your domain that actually supported it, even though some time ago it became a requirement to be an accredited registrar - and still you see some that support for it is PITA to use, or just borked anyway.. And even then I didn't run it on my own connection, I ran it on some low level vpses that cost peanuts to have, I still maintain a couple of them for just test boxes for other things, just not dns any more.
It can be a great learning tool for sure - like some of the problems your having.. But in the big picture if actually a production something - I wouldn't do it..
Now local dns that is a different fish to fry, and that is where you can get all your fun with running your own dns ;) When all the headaches of public facing is no longer your concern - it works, is up and is global.. And you can just worry about your service.. Depending on what that is - that could/should more than likely be hosted by one of the big dogs as well.. Global CDNs don't down very often - and when they do, its normally not just your site ;) hehehe
-
@carrzkiss still at 1 ms TTL..
And your SOA expire is set below the recommended level at only 604800, rfc1912 recommends 2 weeks as the min value.
Your TTL in your SOA is set to 1 hour, 3600 but you prob have 1 second set on your actual records.