IP Alias List Creation Issue
-
Weird issue here. I'm attempting to use pfBlockerNG_devel to download an IP list from an INTERNAL apache server then add it as an alias list to pfsense. The list a clear-text file of JUST IP addresses yet when pfBlockerNG updates, I get this in the log viewer:

Here's the IP List setup:
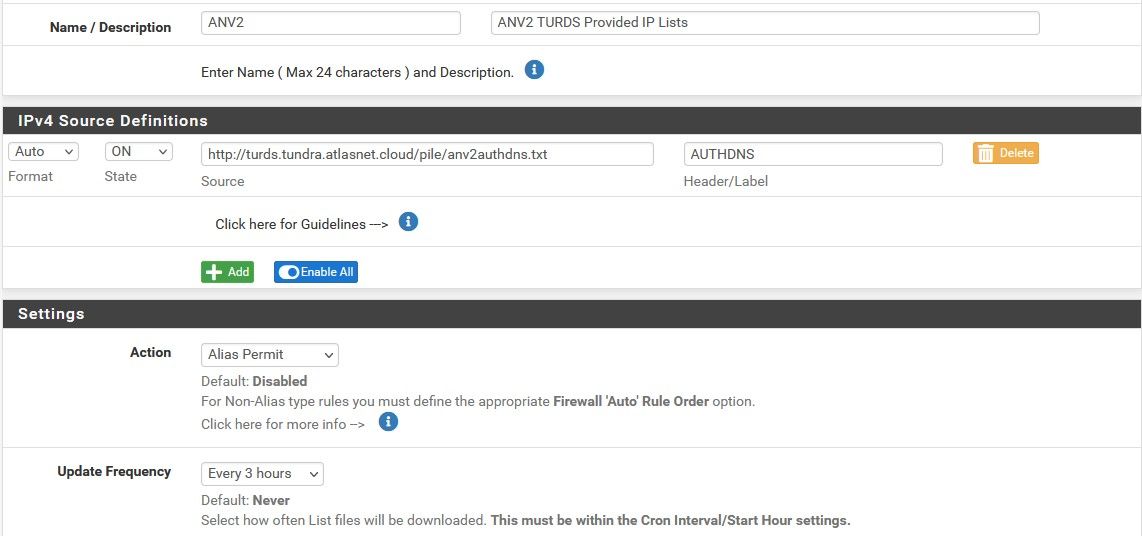
Any ideas ? This is one of the last few pieces holding up build completion.
-
@jcook-atlas I bet your custom list contains private ip addresses?
I have a similar problem as you. PFBlockerNG is supposed to have a setting in the IP tab called "suppression" normally disabling suppression will allow private IPs to stay in the customer lists downloaded. This new version appears to be broken and strips out all RFC1918/Loopback addresses from lists downloaded even if suppression is disabled.
-
I found an alternative to using pfBlockerNG to accomplish list downloads.
For others looking for this solution here it is:
-
create your list as a simple plain-text TXT document with JUST a line-by-line listing of the network (in CIDR), the host IP (straight or CIDR), or the URL.
-
publish that TXT file on a TRUSTED (and preferably INTERNAL) web-server (I personally prefer Apache)
-
from the pfSense Firewall menu, choose 'Aliases' >> URLs >> 'Add' >> Set the 'Type' drop-down to "URL Tables (IPs)", enter the http/https address of the list you are hosting in the 'URL Table (IPs)' URL field, then set the update window. Click Save and your are done.
To update more frequently that daily, set up a CRON job to execute '/etc/rc.update_alias_url_data' as root at what ever periodicity that you want - again, I prefer 90-min updates so my CRON jobs are running at 0 0,3,6,9,12,15,18,21 * * * and 30 1,4,7,10,13,16,19,22 * * *
All and all pretty simple, straight-forward and sustainable.
-
-
J jcook.atlas referenced this topic on
-
@jcook-atlas. this is the exact setup i was using before switching to pfblockerng. i switched because of needing to touch the alias file and change the date to older to make it actually update. I'll check my notes on it.
Thanks for the suggestion. This may work in the interim but I would love to see the designed functionality of PFBlocker fixed.