Turn PfSense into OpenVPN server with only one NIC
-
First I would like to hear everyone thoughts if this is even possible.
I have an Intel NUC that I'm trying to turn into a OpenVPN/Wireguard/IPSec VPN Server. The NUC I'm dealing with only has one NIC and the environment where it will be going is not VLAN compatible. The WAN I have no VLAN tag on, the em0 interface and a tag on Lan interface em0.10. I created a VIP interface for management and a Loopback interface for OpenVPN. Port forward rule to access the pfSense from WAN interface, this will be behind a NAT router OpenVPN is the only server I have configured so far. I can connect to the OVPN server but it will not route to internet. It's not the rules because I tried adding an any <-> any rule. I disabled the firewall. I'm thinking the issue is my WAN and LAN have the same Layer 2 address so the packet never gets moved to the WAN interface. I tried changing the MAC address of the LAN Interface, but since it is based on the WAN as the parent pfSense will not let me change it. I would like to use pfSense for this server because it has a configuration that I fimilar with and I been using the platform for ever now (since 2006 I believe). I was thinking about creating a Virtual Interface and then binding that to the LAN address but this doesn't seem possible via the GUI. Any help would be appreciated. Is this even possible? NAT rules are setup in outbound NAT for that subnet to be encapsulated when routed out to the internet so that is not the problem. I'm thinking if my NUC had two Interfaces I wouldn't have an issue.
What works:
I can connect to the VPN
I can access the GUI
I can access the VPN SubnetWhat doesn't work:
Traffic will not route to the internetInternet -> pfSense [VPN Server]
Internet <-> [VPN Client] -
@mikeisfly
Yes, basically this should be doable.Does pfSense itself have internet connection?
What is the upstream gateway?
For further investigation, please post the OpenVPN settings, routing table of pfSense and outbound NAT rules.
-
Open VPN Settings:
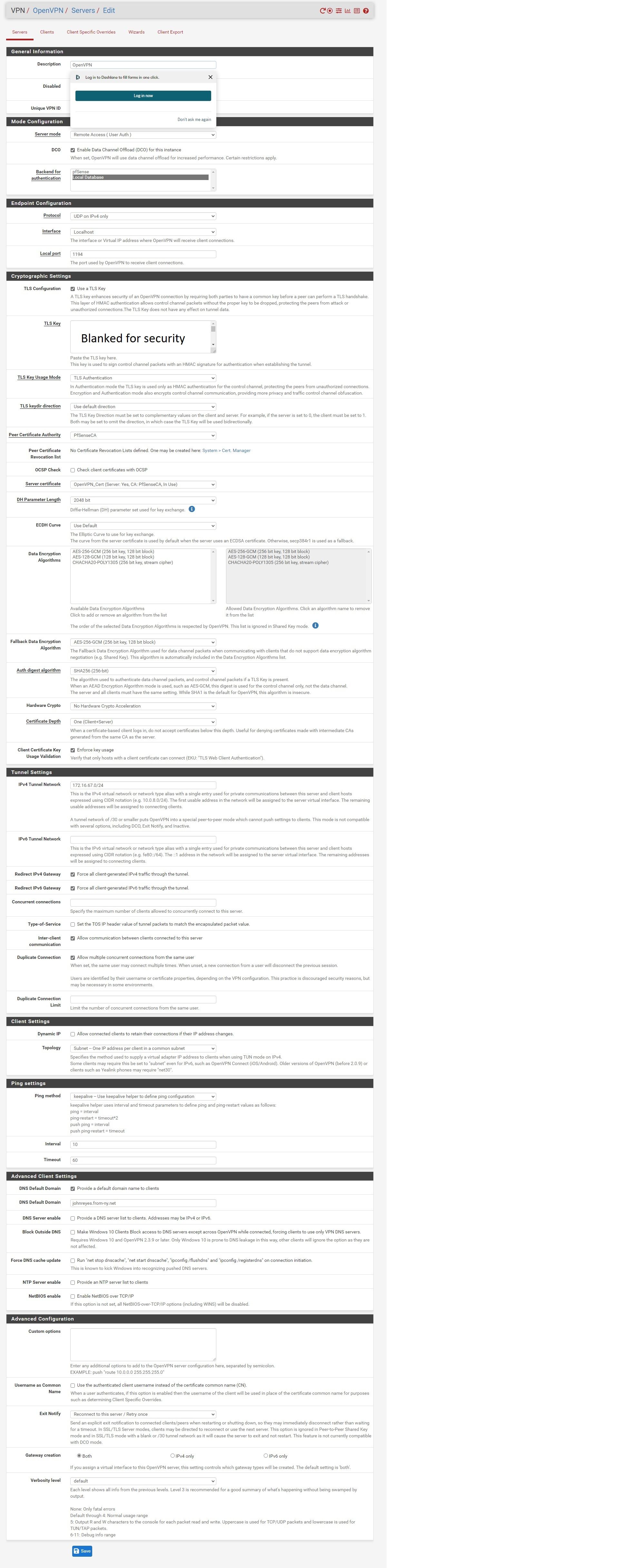
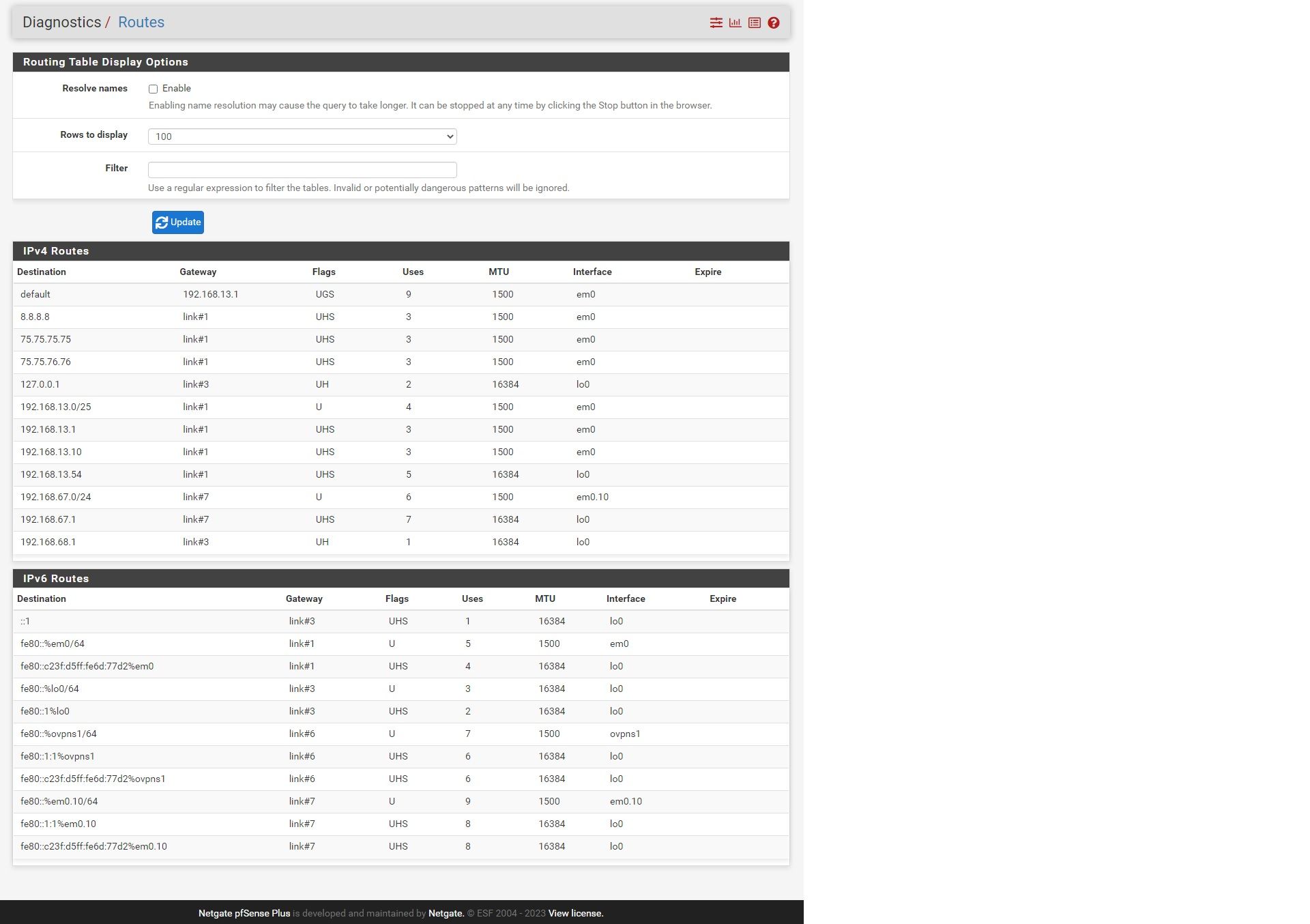
Routing Table:
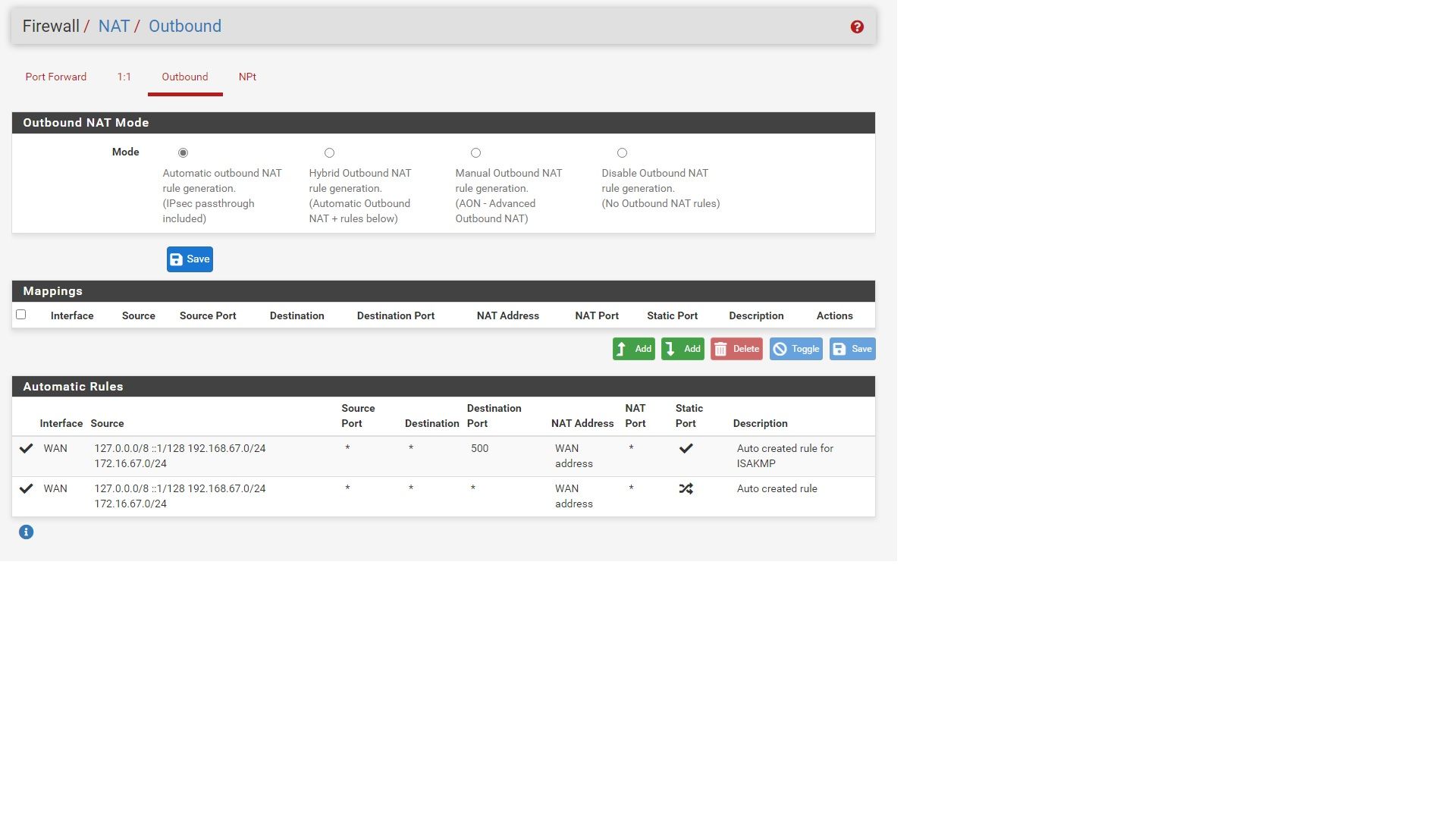
Outbound NAT:
Gateways:
Interfaces:
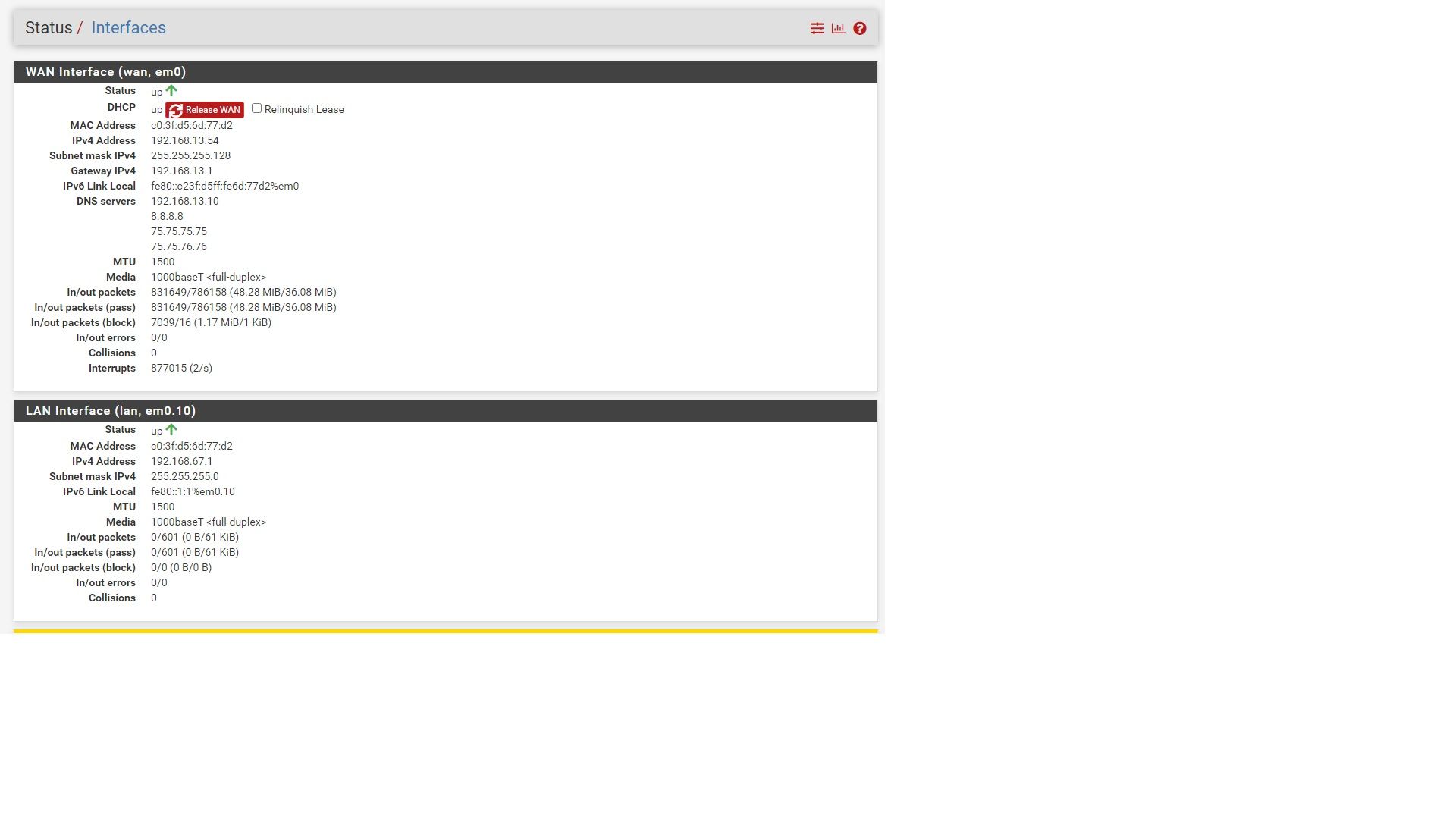
I think the issue is the WAN and LAN have the same MAC so the layer router never switches the frame to the correct interface. But any help is appreciated.
-
Somewhere-on-youtube
 there is a video that explains how to make use of a one-NIC pfSense.
there is a video that explains how to make use of a one-NIC pfSense.
It boils down to : add a small smart switch that does minimal VLAN.
On this smart switch you can split out the real WAN and LAN.Edit : here you have 2 video's
-
@mikeisfly
I'm missing the OpenVPN server in the routes. Was it not up at this time?How do you intend to attache pfSense to your network? Is it the upstream gateway in you LAN?
I.e. ISP router > pfSense > LAN switch.
Or is the ISP router also connected to LAN and has a separate subnet for pfSense WAN?If you want to use the OpenVPN server for your own purposes, you can set it up with a single network within your LAN, forward the OpenVPN packets to it and configure an outbound NAT rule on LAN for masquerading.
-
@viragomann This is for a friend of mine who is not very network savvy. So the way his internet works is he has a Cable modem which is connected to his home router and this pfSense sits behind that. What I wanted to do is setup different VPN servers and just hang it off of one of the ports of his top router and have it just act as a VPN endpoint. Since I'm familiar with pfSense configurations I figured that I could do this pretty easily but as @Gertjan said I'm not sure if this would be possible without a VLAN aware switch. I though about connected a USB dongle just to get another interface with a different MAC so the layer 2 address would be different. Something with dual ports would work perfectly for this. I even tried to setup an openvpn interface on the router but this didn't work either.
@viragomann Yes at the time I was not connected to the VPN. I will connect shortly and post screen shots.
-
Then the 'best' solution will be : replace that 'router' by 'pfSense'.
pfSense, off the shelves, is as any other router out there, with one exception : if it is not ZFS (the file system based) do add a UPS, if power can fail (a lot).
That will solve the VPN issue completely : all LAN devices would be accessible.But : don't go the 'add a USB NIC' route.
-
@mikeisfly said in Turn PfSense into OpenVPN server with only one NIC:
What I wanted to do is setup different VPN servers and just hang it off of one of the ports of his top router and have it just act as a VPN endpoint.
As mentioned, if your intention is to access the home network from remote you can configure pfSense to do masquerading, so there is no need for a WAN and LAN. You can do this with is single interface within the LAN, set a LAN IP and a gateway in the interface settings (this does the masquerading) and forward OpenVPN traffic to it from the router.
With this setup, the local devices would see the pfSense LAN IP as source, when access comes from the VPN though, but for private use this should be okay, I think and you would not need any additional device.
-
@viragomann Great idea never thought of that before, I will give it a try. Thanks
-
@viragomann your idea worked. So this is the steps that I took for anyone else trying to do a similar setup.
- Disabled DHCP Server on LAN network
- Set LAN Interface to DHCP (Save but not applied)
- Whet to interface assignment and set WAN to a VLAN on parent Interface (10 in my example)
- Set LAN to parent interface
- LAN rules were configured for any any but make sure yours are too
- Made sure all outbound NAT rules were configured for LAN and Not WAN (That way upstream router in unaware of pfSense network)
- In Open VPN server I checked the box for Provide a DNS Server list to Clients.
- Force all Client-generated IPv4/IPv6 was already checked but make sure yours is checked to force all traffic through VPN.
That's it. Other than that, OpenVPN is setup like normal. Now I will configure Wiregaurd as a VPN option too for speed.
Thanks to @Gertjan @viragomann for your help. Glad to see that this can be done. Makes it easy to add Remote connections to send to folks.