Netgate SG-2100 - OpenVPN can't login to CRM remotely
-
Hello Community,
I haven't been using Pfsense for long and aiming to switch a raft of customers across to it for a bunch of reasons that I'm sure are obvious to all you long time Pfsense users.
Before I even consider rolling this out as the preferred solution, I have a test network which mimics a customer network and setup in everyway. So far I'm really liking Pfsense and have everything up and running by using the Netgate guides which have been great.
In this test environment, I have setup OpenVPN and the remote client can connect without issue, can ping the server on that site (172.31.17.120), access the network shares on that same server and remote print via that server which is also a print server. The issue I have is that when connecting to the CRM software and trying to login, there is an error. The CRM system is installed on the same server that can be pinged and shares accessed. I've tried everything to get this work that I can think of with no joy. I have spoken to the CRM provider and they have said that all user login authentication goes out to the CRM servers managed by them and will only allow users to login if the internet IP Address they're connecting from appears on their whitelist.
For example in this scenario we can assume:
- Remote OpenVPN user in a hotel has internet IP address of 123.123.123.123
- The site and network the OpenVPN user is connected to has an internet IP address of 124.124.124.124
- 124.124.124.124 is the internet IP address of the site that has the server (where the CRM is installed)
- The CRM cloud systems have 124.124.124.124 on their whitelist so users from that physical site can be authenticated and login
- Whitelisting 123.123.123.123 isn't feasible as tomorrow the remote OpenVPN user will be in a different hotel with a different internet IP address.
My question is, how in PfSence can it be configured to present the remote user with the whitelisted IP address of 124.124.124.124 when the address they are connecting from is actually123.123.123.123.
I have tried setting up static routes but this hasn't worked and my gut tells me that this can be managed in the NAT settings and possibly alongside an additional firewall 'pass' rule.
The solution has eluded me and normally I successfully solve everything using just guides and instructions as I find it's the quickest way for me to learn. Not this time however, so I need to lean on this community's knowledge, experience and kindness for sharing their experience and by extension their time. Any suggestions or help would be greatly received.
To recap: In this environment, the remote user could conceivably connect from anywhere in the world so whitelisting specific internet IP addresses naturally isn't feasible.
The remote user must present with the internet IP address of the site that the remote user is connecting to. Essentially, the remote user must appear to have the same IP address of the site and server that the CRM is installed on as this has the whitelisted internet IP address on the CRM provider's systems.Thank you in advance for any help and advice you can provide.
I.T._Lee
-
@i-t-_lee
So the CRM system is not in the local network, where the OpenVPN server ist running, if I got you correctly?
It is outside in the internet, but you can only connect from the public IP the VPN server is running on? -
@viragomann Thanks for the reply.
The database for the CRM is stored on the server that is accessible remotely using OpenVPN. In order to authenticate a user when logging on, the remote client makes a brief call out to the CRM's server in the cloud. This is just for authentication. If the internet IP address of the remote user is not on the whitelist of the CRM server in the cloud, login/authentication fails. Therefore, all remote OpenVPN users need to present with an internet IP address that is on the whitelist. The CRM company have said that remote users need to present with the internet IP address of the host site where the CRM database is located (where the server resides and where the Pfsense router is located...Does that make sense?
-
@i-t-_lee said in Netgate SG-2100 - OpenVPN can't login to CRM remotely:
The CRM company have said that remote users need to present with the internet IP address of the host site where the CRM database is located (where the server resides and where the Pfsense router is located...
So you need to do masquerading on the VPN access going to the CRM authentication server.
At first you have to route the traffic to the CRM over the VPN by adding its IP into the "Local Networks" in the OpenVPN settings. No matter if it's a public IP.
In the firewall rules for the OpenVPN you have to allow the access to the CRM, of course.
For the masquerading go to the outbound NAT settings and check if the OpenVPN tunnel network is already added in the automatic rules.
If it isn't or if you use manual mode, you have to do this manually: Switch the NAT mode to hybrid if it's in automatic, save and add a rule:
interface: WAN
source: OpenVPN tunnel network
destination: any (or only the CRM IP)
translation: interface address (default) -
@viragomann
So correct me if I'm wrong but essentially in Firewall settings I need to switch the Outbound NAT to Hybrid (so I can add an additional rule). Then add an outbound rule that will have the source of the OpenVPN subnet of 172.31.18.0/24 (In this instance this is the OpenVPN subnet).
The destination needs to be either 'Any' or the LAN subnet (172.31.17.0/24) or the specific IP address of the server than houses the CRM database?Any preference of the three options above for destination?
In reference to routing the traffic to the CRM over the VPN, I need to adding the server IP address (where the CRM database is stored) into 'Local Networks' (I can only see an IPv6 option for local networks in OpenVPN settings). Given remote users can already reach the internal server that holds the CRM database, is this step still necessary?
I really appreciate your help, I'm loving Pfsense but still wet behind the ears when it comes to Pfsense (hence the testing and much needed guidance). Simply put Pfsense is laid out very differently to what I'm used to using as enterprise routers.
-
@i-t-_lee said in Netgate SG-2100 - OpenVPN can't login to CRM remotely:
in Firewall settings I need to switch the Outbound NAT to Hybrid (so I can add an additional rule). Then add an outbound rule that will have the source of the OpenVPN subnet of 172.31.18.0/24 (In this instance this is the OpenVPN subnet).
On the outbound NAT page you can see automatically generated rule at the bottom. You will find there your LAN network already. If you can also see the OpenVPN tunnel network, it's all done there, no additional route needed. Therefore I advised you to look for that.
Note that pfSense add the rule automatically if you run through the OpenVPN setup wizard.
If you're missing the OpenVPN tunnel there, you have to add the rule as suggested. In this case, you have also to switch into the hybrid mode, so that manually added rules are applied. In automatic mode only automatically added rules at the bottom are applied.
Yes the source has to be the OpenVPN tunnel network.
The destination needs to be either 'Any' or the LAN subnet (172.31.17.0/24) or the specific IP address of the server than houses the CRM database?
Any preference of the three options above for destination?LAN makes no sense. I try to explain below, what the rule does.
The destination must include the destination IP the clients need to access in the internet. So this is the CRM authentication server, as I got you, which have a public IP.
"Any" matches all destination naturally. If you want your client to access also other IPs in the internet over the VPN set it to any.In reference to routing the traffic to the CRM over the VPN, I need to adding the server IP address (where the CRM database is stored) into 'Local Networks' (I can only see an IPv6 option for local networks in OpenVPN settings). Given remote users can already reach the internal server that holds the CRM database, is this step still necessary?
Yes, you need at least the local servers IP and the public authentication server IP to enter here. This must be networks in CIDR notation and comma separated, e.g.
172.31.17.0/24,124.124.124.124/32This is your whole LAN subnet, if you want to route the CRM only enter its IP with a /32 mask.
I assume, the CRM servers use IPv4 either, so you can leave the IPv6 box blank.
-
@viragomann
Great, thank you for your help so far.This was configured using the wizard so no issues there.
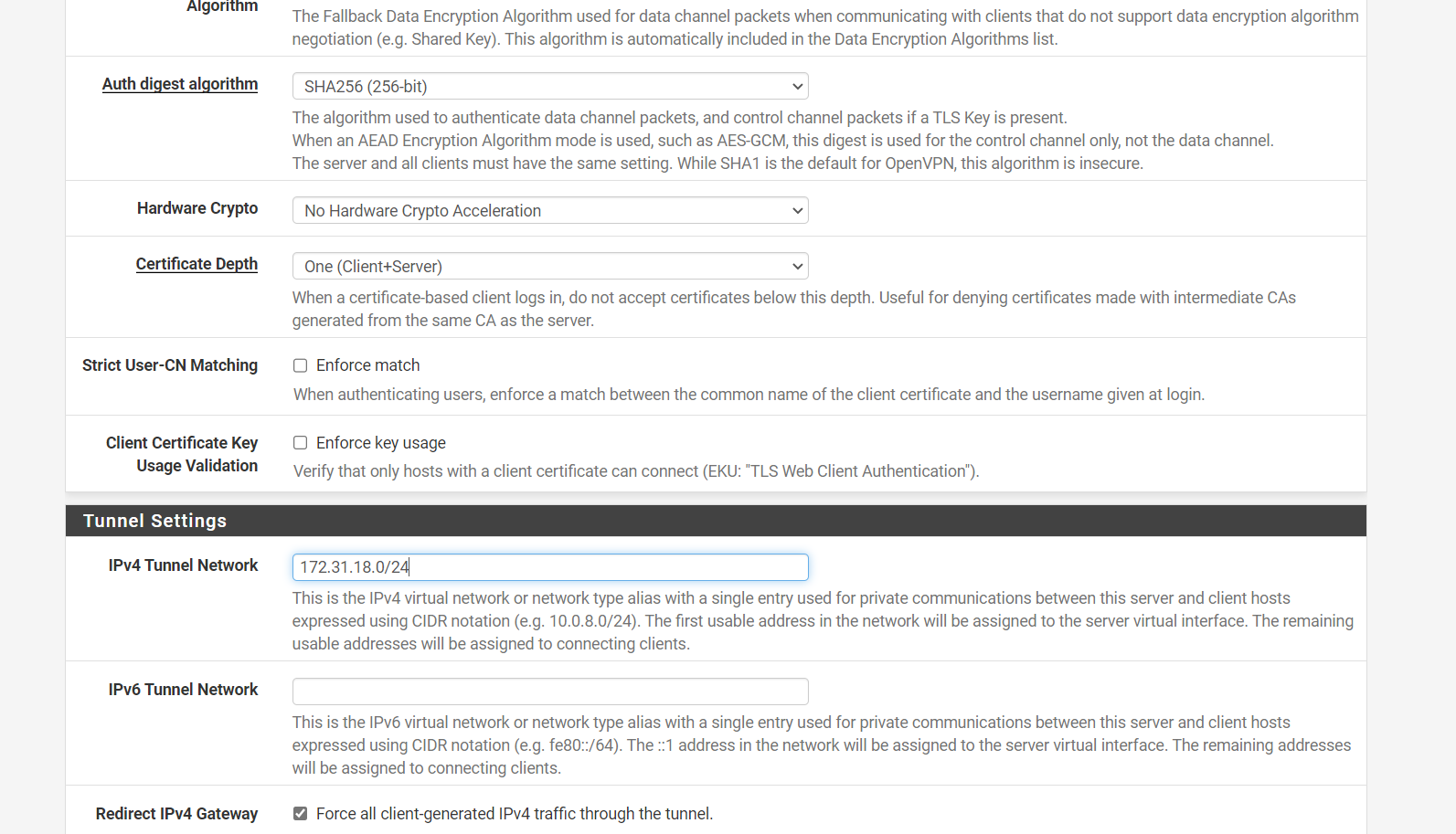
I have attached 2 images of the OpenVPN configuration. The first is the current settings and the second is what I think you are proposing?
The setting to change is located here
VPN>OpenVPN>Servers>EditThe 'Current' setting (below image) contains the 172.31.18.0/24 as the IPv4 Tunnel Network subnet under 'Tunnel Settings' (VPN on a different subnet under Tunnel settings as is the normal scenario).
The Proposed setting (below image) is 172.31.17.0/24,124.124.124.124 in the Tunnel Settings. The LAN followed by the internet IP address (for full internet access). So not the VPN subnet of 172.31.18.0/24,124.124.124.124
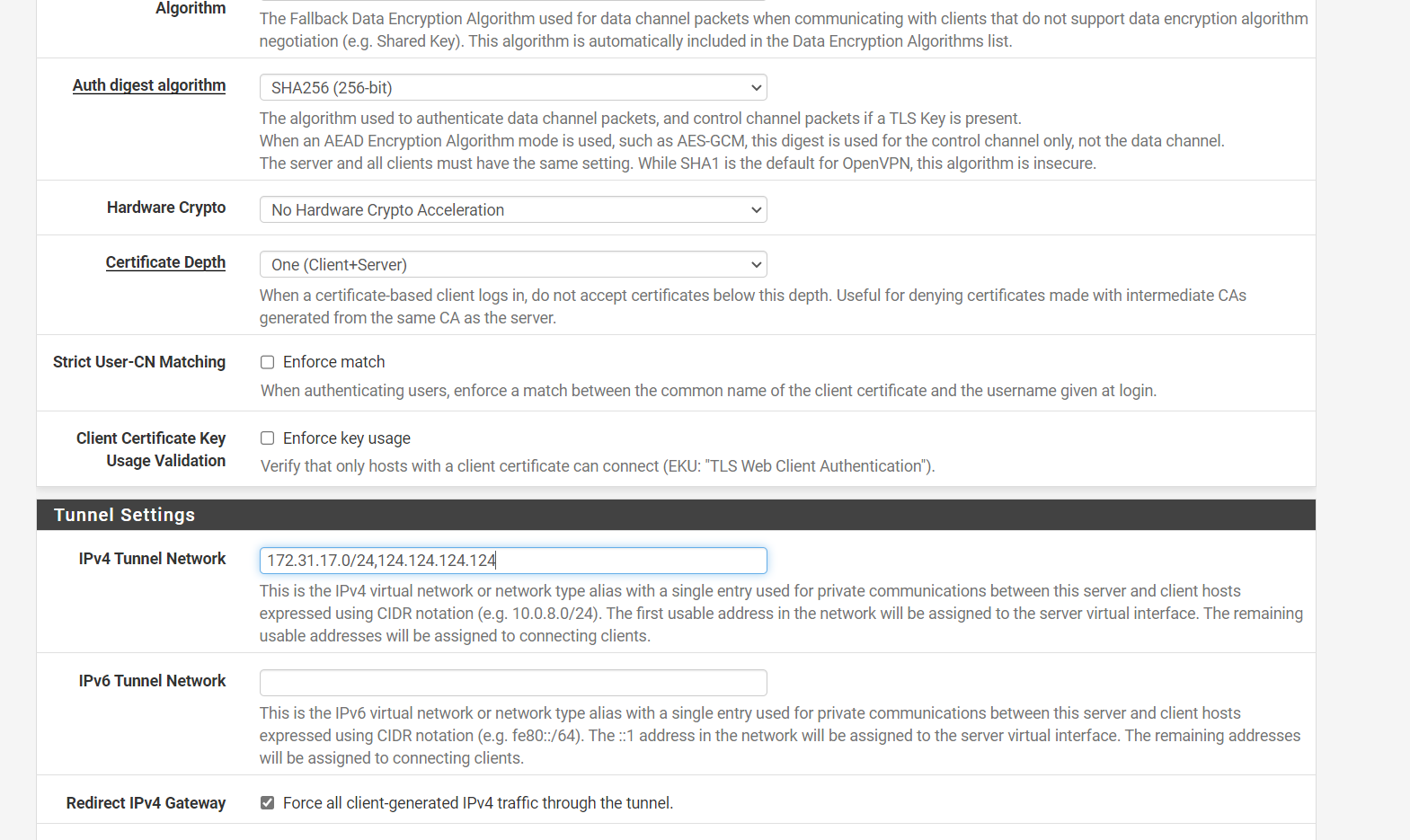
Unless you mean a different field, this is where the Tunnel subnet is defined and I beleive needs to be a different subnet to the main LAN subnet?
To clarify currently 172.31.18.0/24 is the VPN subnet and 172.31.17.0/24 in the LAN subnet.
I really do appreciate you sticking with me.
Thank you.
-
@i-t-_lee
No, the box I was talking about is hidden, because you have checked "Redirect gateway". This forces the whole upstream traffic over the VPN as the hint next to the check box explains.
Don't know if you really want this. My impression was something else. -
With entering network ranges into the "local networks" field, only these networks are routed over the VPN.
Regarding the outbound NAT. This does the masquerading.
This means, it translate the source IP in packets passing out the respective interface into the interface IP.
So if you have added it to WAN, outgoing packets from the stated source to the destination get the WAN IP. -
@viragomann
Now I'm there. Thank you so much. I followed the wizard and the guide on the Netgate website to configure this. From this I determined that the 'Redirect gateway' (Force all client-generated IPv4 traffic through the tunnel) was a requirement to ensure that the OpenVPN remote clients would present the internet IP address of the main site. Now I've unchecked that box, it all makes perfect sense.
Thank you very much for your patience and sticking with me. I knew it was likely something small that I had wrongly configured. Turns out it was a checkbox and as a result, I never actually saw the IPv4 Local network(s) option.
It all makes sense now. I should of led with the pictures.Thank you kindly for all your help,
I.T._Lee