pfblocker blocking odd requests from pfsense.. i think
-
Hi,
I'm getting a lot of blocked dns requests from pfblockerng-devel showing what looks like pfsense making dns requests to domains like these. Why would pfsense be trying to lookup/connect to these kinds of domains? I'm using quad9 for my dns on pfsense and pfblockerng-devel so the ns domains are a puzzle.
Thanks!!
-
I'm seeing the same thing.
One thing that might explain this, is that I'm using this : Redirecting Client DNS RequestsAs stated over there :
With this port forward in place, DNS requests from local clients to any external IP address will result in the query being answered by the firewall itself. Access to other DNS servers on port 53 is impossible
and the firewall itself == 127.0.0.1
Btw : I presume you already knew that pfSense will not visit or 'DNS lookup' sites like, for example, bitbucket.org.
-
@gertjan said in pfblocker blocking odd requests from pfsense.. i think:
I'm seeing the same thing.
One thing that might explain this, is that I'm using this : Redirecting Client DNS RequestsAs stated over there :
With this port forward in place, DNS requests from local clients to any external IP address will result in the query being answered by the firewall itself. Access to other DNS servers on port 53 is impossible
and the firewall itself == 127.0.0.1
Btw : I presume you already knew that pfSense will not visit or 'DNS lookup' sites like, for example, bitbucket.org.
I'm not using that, instead I've just got a floating rule blocking all outgoing requests except for pfsense (but I might just institute your setup). I hope pfsense isn't doing this but I can't seem to find anything pointing toward the source of these requests.
-
@omethe said in pfblocker blocking odd requests from pfsense.. i think:
I can't seem to find anything pointing toward the source of these requests
There is a way.
You can proof that pfSense will never visit any marketo dot com or bitbucket do org by itself.Access the console - the real 'comm port' or VGA access.
You have a switch on your LAN ? Leave it there, and remove all devices from that switch.
Reboot pfsense with the console.When it's up, goto the command line and type :
tail -f /var/log/pfblockerng/dns_reply.logand now wait.
If there are any DNS requests, they are related to pfSense Netgate itself.
Or pfBlockerng updating its lists.I'm pretty sure there will be no no marketo dot com requests.
-
@gertjan said in pfblocker blocking odd requests from pfsense.. i think:
@omethe said in pfblocker blocking odd requests from pfsense.. i think:
I can't seem to find anything pointing toward the source of these requests
There is a way.
You can proof that pfSense will never visit any marketo dot com or bitbucket do org by itself.Access the console - the real 'comm port' or VGA access.
You have a switch on your LAN ? Leave it there, and remove all devices from that switch.
Reboot pfsense with the console.When it's up, goto the command line and type :
tail -f /var/log/pfblockerng/dns_reply.logand now wait.
If there are any DNS requests, they are related to pfSense Netgate itself.
Or pfBlockerng updating its lists.I'm pretty sure there will be no no marketo dot com requests.
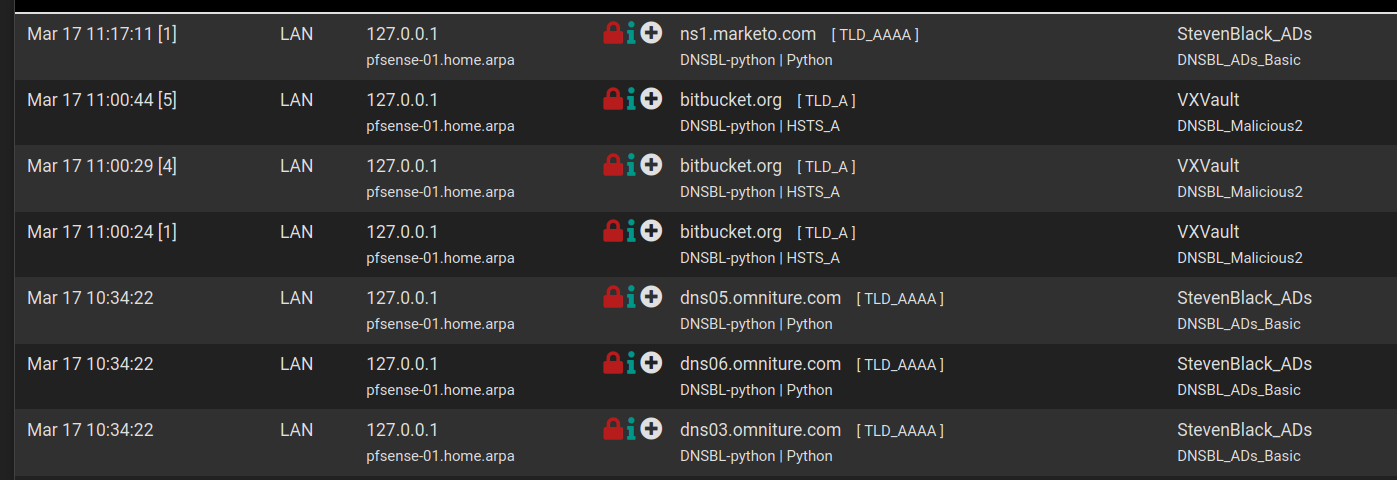
Ok so I did a packet capture on port 53 for a while until one of the entries showed up;
Mar 17 19:01:13 127.0.0.1
pfsense-01.home.arpa TLD_A
DNSBL-python | HSTS_A LAN bitbucket.org VXVault
DNSBL_Malicious2had a look at the packet capture and can't see any dns requests for bitbucket at that time. in fact there were no requests for bitbucket in the capture at all.
19:00:54.913997 (oui Unknown) > (oui Unknown), ethertype IPv4 (0x0800), length 107: (tos 0x0, ttl 64, id 8058, offset 0, flags [none], proto UDP (17), length 93, bad cksum 0 (->4526)!)
pfsense-01.home.arpa.domain > windows-vm-01.home.arpa.64964: [bad udp cksum 0x164b -> 0x25cf!] 48475 q: A? mclb-gcp.nimbus.bitdefender.net. 1/0/0 mclb-gcp.nimbus.bitdefender.net. A 34.149.211.227 (65)19:01:14.099910 (oui Unknown) > (oui Unknown), ethertype IPv4 (0x0800), length 87: (tos 0x0, ttl 64, id 12162, offset 0, flags [DF], proto UDP (17), length 73)
michael-lt.home.arpa.45362 > pfsense-01.home.arpa.domain: [udp sum ok] 55614+ A? safebrowsing.googleapis.com. (45)I'm really not sure where this is coming from?
-
If nothing is in the local - resolver - dns cache
I just visited bitbucket dot org with my browser, and saw this :
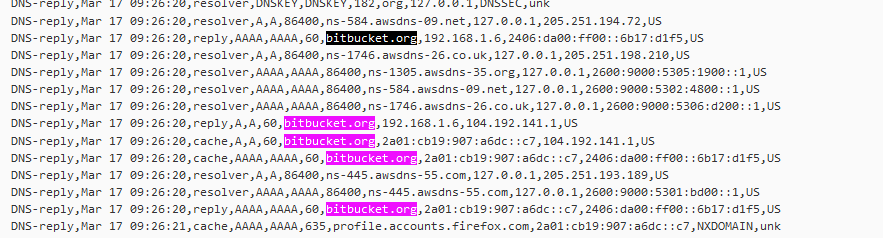
For me, the answer A and AAAA were served from the resolver cache ( aha ?! ).
I guess I already visited, directly or indirectly, somehow that site .... in the past.I do have :
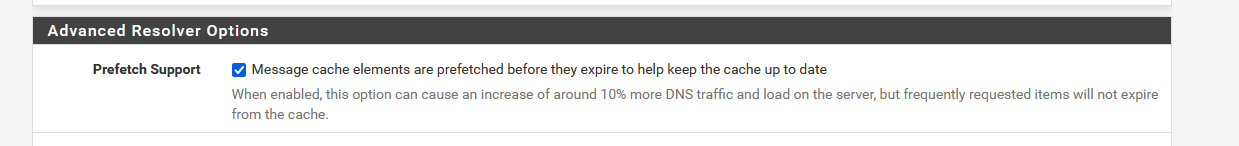
activated, and my unbound / resolver rarely restarts, so it will, ones something is in the dns cache, refresh as soon as TTL becomes zero. That will be the moment that 'pfsense' == 127.0.0.1 == unbound itself will look for bitbucket.org, just to keep zone info it up to date.
edit :
Maybe it's a HSTS story.
[23.01-RELEASE][admin@pfSense.my-local.mess]/usr/local/pkg: grep -R 'bitbucket' * pfblockerng/pfb_py_hsts.txt:bitbucket.com pfblockerng/pfb_py_hsts.txt:bitbucket.io pfblockerng/pfb_py_hsts.txt:bitbucket.organd that checks out : bitbucket.* is on the Chrome HSTS is used by pfblockerng :
Do some reading and clicking here
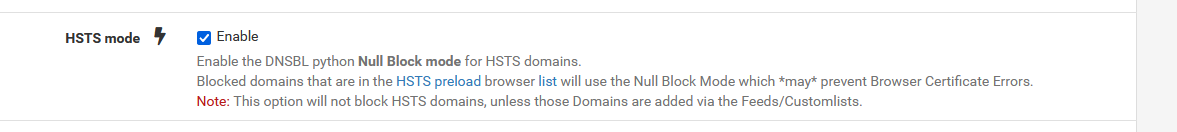
( Please, don't ask me what HSTS is
 )
) -
@gertjan said in pfblocker blocking odd requests from pfsense.. i think:
If nothing is in the local - resolver - dns cache
I just visited bitbucket dot org with my browser, and saw this :

For me, the answer A and AAAA were served from the resolver cache ( aha ?! ).
I guess I already visited, directly or indirectly, somehow that site .... in the past.I do have :

activated, and my unbound / resolver rarely restarts, so it will, ones something is in the dns cache, refresh as soon as TTL becomes zero. That will be the moment that 'pfsense' == 127.0.0.1 == unbound itself will look for bitbucket.org, just to keep zone info it up to date.
edit :
Maybe it's a HSTS story.
[23.01-RELEASE][admin@pfSense.my-local.mess]/usr/local/pkg: grep -R 'bitbucket' * pfblockerng/pfb_py_hsts.txt:bitbucket.com pfblockerng/pfb_py_hsts.txt:bitbucket.io pfblockerng/pfb_py_hsts.txt:bitbucket.organd that checks out : bitbucket.* is on the Chrome HSTS is used by pfblockerng :
Do some reading and clicking here

( Please, don't ask me what HSTS is
 )
)well i've worked out where bitbucket is coming from, one of my blocklists APT1_Report is hosted by bitbucket. But bitbucket is blocked by another list. I've got a few others to sort out.
-
@omethe said in pfblocker blocking odd requests from pfsense.. i think:
one of my blocklists APT1_Report is hosted by bitbucket. But bitbucket is blocked by another list

Seen that before : the 'pfBlockerng DNSBL or IP feed' that includes the host names or IP's of the source of other feeds.
Now I think about it : take this very known DNSBL feed :
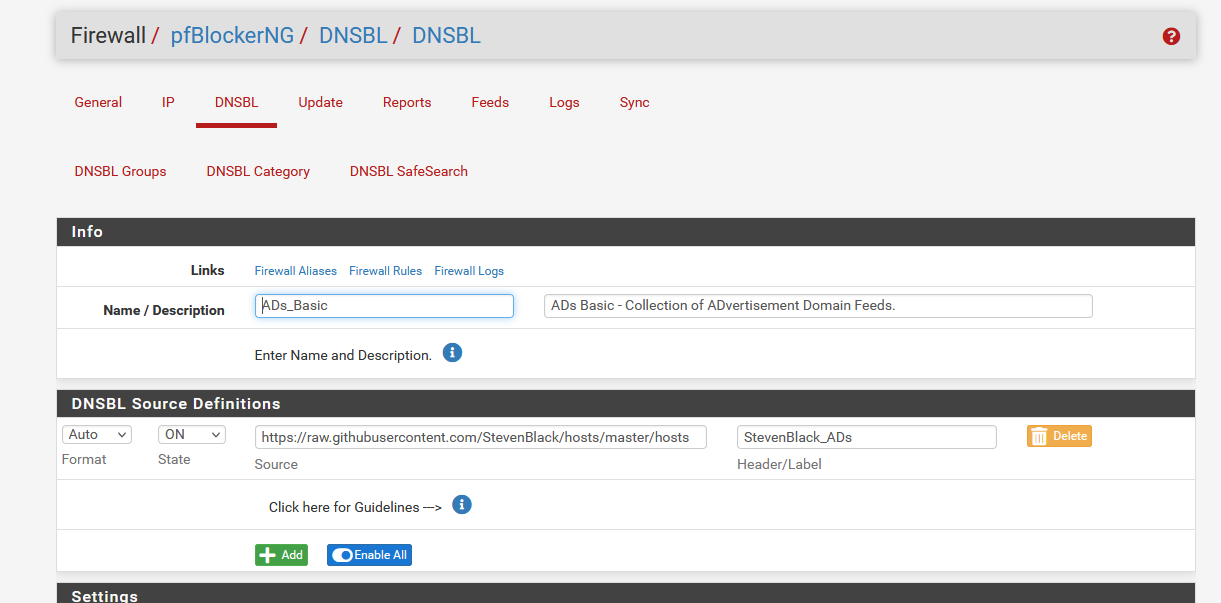
It would be a good 'anti shoot in the foot' thing to warn the pfSense admin that the host :
raw.githubusercontent.com has been blocked on some other DNSBL list - or on it's own list
As soon as all the feeds are loaded, the source host name of all feeds, like raw.githubusercontent.com should be checked if they exist in the entire 'global' list, and warn the user is that's the case. -
@gertjan said in pfblocker blocking odd requests from pfsense.. i think:
@omethe said in pfblocker blocking odd requests from pfsense.. i think:
one of my blocklists APT1_Report is hosted by bitbucket. But bitbucket is blocked by another list

Seen that before : the 'pfBlockerng DNSBL or IP feed' that includes the host names or IP's of the source of other feeds.
Now I think about it : take this very known DNSBL feed :

It would be a good 'anti shoot in the foot' thing to warn the pfSense admin that the host :
raw.githubusercontent.com has been blocked on some other DNSBL list - or on it's own list
As soon as all the feeds are loaded, the source host name of all feeds, like raw.githubusercontent.com should be checked if they exist in the entire 'global' list, and warn the user is that's the case.or at least have a tickbox option to whitelist the domains of all the feeds added.
-
well, if you add a feed that is hosted 'off-site', some where on the internet I guess you want to be able to resolve that host nam, and not getting a 0.0.0.0 as an answer ..... if not, whats the point of adding / using that host name in a feed URL
