OpenVPN Remote users are able to access Router but not hosts on local network
-
@gizmobrat
Assumed that OpenVPN server is running on the default gateway, check if the destination device's firewall allows access from outside of its subnet. -
@viragomann
I am not able to reach any devices on the 10.0.0.0/24 subnet with the exception of the router. I am unable to reach any of the hosts even with Firewalls disabled on both remote host and host on the network. This leads me to believe that either I need to set a default gateway on the VPN or I need to set up a way to route traffic between the two local networks. Any Ideas?Thanks
gizmobrat -
@gizmobrat
Can you confirm that the remote pfSense running the server is the default gateway in the remote network?Also ensure that the local network is not overlapping with the remoute.
Maybe you can post the clients route table for verification.If that's given sniff the traffic on the remote LAN interface with packet capture on pfSense, while you try to access a remote device from the client to see if the packets are passed through.
-
@viragomann
The PF sense router is the device that is running the OpenVPN server.
The local network is 10.0.0.0/24 on the Lan Interface 10.0.0.1 is he default gateway
The VPN Network is 10.0.2.0/24 on the OpenVPN interface.
The remote network is 192.168.1.1Below is the remote Windows 10 route table and IPconfig
IPv4 Route Table =========================================================================== Active Routes: Network Destination Netmask Gateway Interface Metric 0.0.0.0 0.0.0.0 192.168.1.1 192.168.1.174 25 10.0.0.0 255.255.255.0 10.0.2.1 10.0.2.2 281 10.0.2.0 255.255.255.0 On-link 10.0.2.2 281 10.0.2.2 255.255.255.255 On-link 10.0.2.2 281 10.0.2.255 255.255.255.255 On-link 10.0.2.2 281 127.0.0.0 255.0.0.0 On-link 127.0.0.1 331 127.0.0.1 255.255.255.255 On-link 127.0.0.1 331 127.255.255.255 255.255.255.255 On-link 127.0.0.1 331 192.168.1.0 255.255.255.0 On-link 192.168.1.174 281 192.168.1.174 255.255.255.255 On-link 192.168.1.174 281 192.168.1.255 255.255.255.255 On-link 192.168.1.174 281 192.168.56.0 255.255.255.0 On-link 192.168.56.1 281 192.168.56.1 255.255.255.255 On-link 192.168.56.1 281 192.168.56.255 255.255.255.255 On-link 192.168.56.1 281 224.0.0.0 240.0.0.0 On-link 127.0.0.1 331 224.0.0.0 240.0.0.0 On-link 192.168.56.1 281 224.0.0.0 240.0.0.0 On-link 192.168.1.174 281 224.0.0.0 240.0.0.0 On-link 10.0.2.2 281 255.255.255.255 255.255.255.255 On-link 127.0.0.1 331 255.255.255.255 255.255.255.255 On-link 192.168.56.1 281 255.255.255.255 255.255.255.255 On-link 192.168.1.174 281 255.255.255.255 255.255.255.255 On-link 10.0.2.2 281 =========================================================================== Persistent Routes: NoneWindows IP Configuration Unknown adapter OpenVPN Wintun: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . : Ethernet adapter Ethernet 2: Connection-specific DNS Suffix . : Link-local IPv6 Address . . . . . : fe80::9dad:46f6:ba7f:13fc%6 IPv4 Address. . . . . . . . . . . : 192.168.1.174 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.1.1 Ethernet adapter Ethernet 3: Connection-specific DNS Suffix . : Link-local IPv6 Address . . . . . : fe80::679f:839e:efa0:54a9%23 IPv4 Address. . . . . . . . . . . : 192.168.56.1 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : Unknown adapter OpenVPN TAP-Windows6: Connection-specific DNS Suffix . : Link-local IPv6 Address . . . . . : fe80::fe25:85c2:b1b1:e166%29 IPv4 Address. . . . . . . . . . . : 10.0.2.2 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : Wireless LAN adapter Wi-Fi 2: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . : Wireless LAN adapter Local Area Connection* 11: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . : Wireless LAN adapter Local Area Connection* 12: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . : Ethernet adapter Bluetooth Network Connection 2: Media State . . . . . . . . . . . : Media disconnected Connection-specific DNS Suffix . :When Running packet sniff on the PF sense on the OpenVPN interface I can see 10.0.2.2 (Remote windows 10) on the VPN interface but not on the LAN interface when running a ping for 10.0.0.250.
-Douglas
-
@gizmobrat
The client side route look well. No conflict there to see.When Running packet sniff on the PF sense on the OpenVPN interface I can see 10.0.2.2 (Remote windows 10) on the VPN interface but not on the LAN interface when running a ping for 10.0.0.250.
So we are back at the firewall rules. The pinged IP is existing, I guess, and you can ping it from pfSense itself?
You said you ran the wizard. This should have added a rule on the OpenVPN tab allowing any source to any destination. Can you verify this?Or maybe can you see any blocks in the firewall logs?
-
@viragomann
10.0.0.250 is the file server and it can be pinged from PFSense and from local devices. I have attached screenshots of the Firewall rules dealing with OpenVPN. Going to start looking at logs now.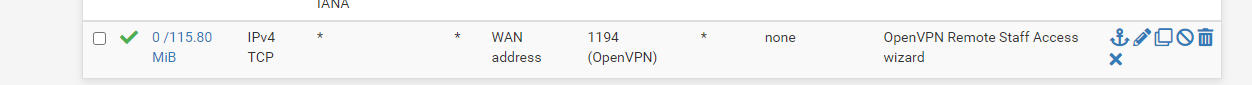
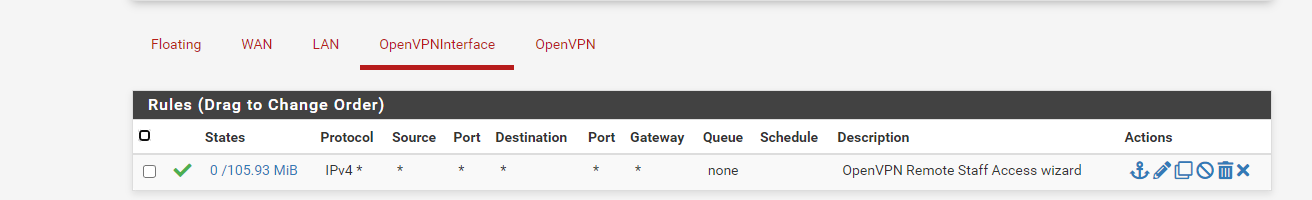
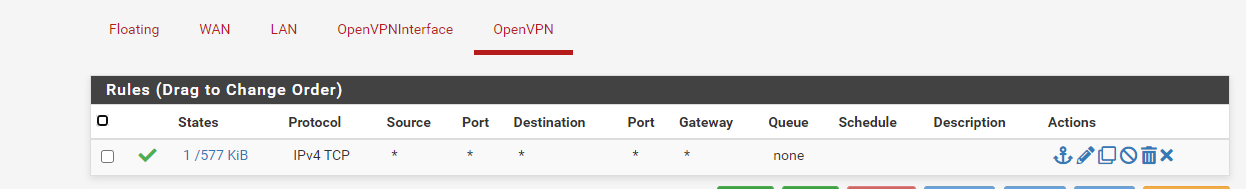
-
@viragomann
Looking through the logs, I am seeing the following items being blocked on destination 10.0.2.2.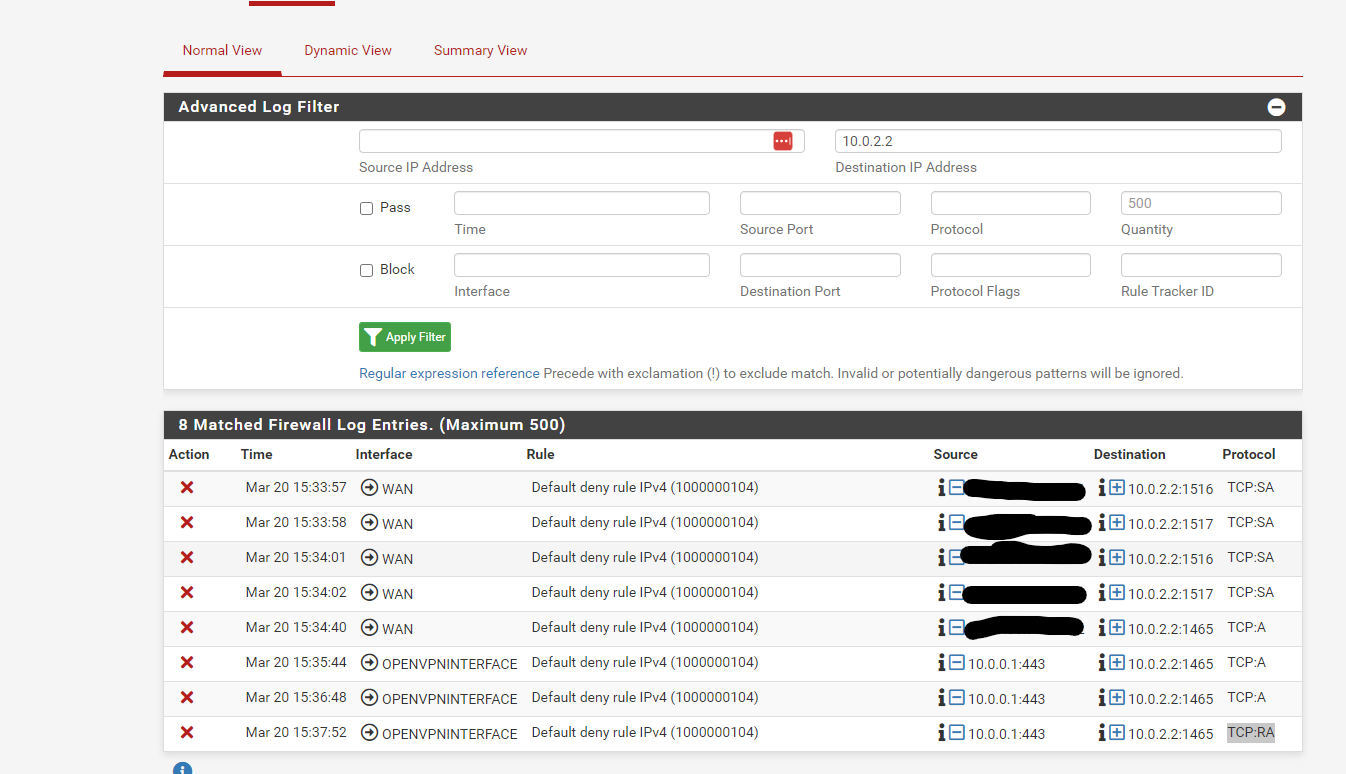
-
@gizmobrat
The rule on OpenVPN only allows TCP. So it doesn't match to ping.
However, since you have assigned the OpenVPNInterface to the server, where the rule allows any, ping should be allowed though.Note that OpenVPN is an interface group. It includes all OpenVPN instances running on the machine.
Rules on interface groups a probed before one on the member interface. Hence such rule have priority.When you ping 10.0.0.250 from pfSense, change the source to the OpenVPN server and check if you get still responses.
-
@viragomann
When pinging from the OpenVPN Interface I get 100% packet loss. So will this be a firewall or a routing error?Secondly under Interfaces/Interface Groups I am seeing no groups.
-
@gizmobrat said in OpenVPN Remote users are able to access Router but not hosts on local network:
@viragomann
When pinging from the OpenVPN Interface I get 100% packet loss. So will this be a firewall or a routing error?I suspect, it is. But on the server side. Either the destination device blocks the ping or it routes responses to anywhere else than back to pfSense.
Are you sure it has pfSense set as default gateway?Secondly under Interfaces/Interface Groups I am seeing no groups.
You can see custom groups only there. OpenVPN is implicitly added by pfSense.
But that shouldn't matter so far.
You wouldn't need to assign an interface to the server for your purposes. It's only needed for policy routing or alike.