RDP to Local LAN desktop - Unable to find
-
Hi Everyone,
New to NetGear and networking in general.Goal: from my laptop, I want to remote into my home network (think I've achieved this) and RDP into my desktop tower that is connected via ethernet to a NetGate SG-1100
Setup Laptop (tethered to cellphone to test), Netgate SG-1100 (wired to my ISP router), Tower (wired to SG-1100)
Server Config:
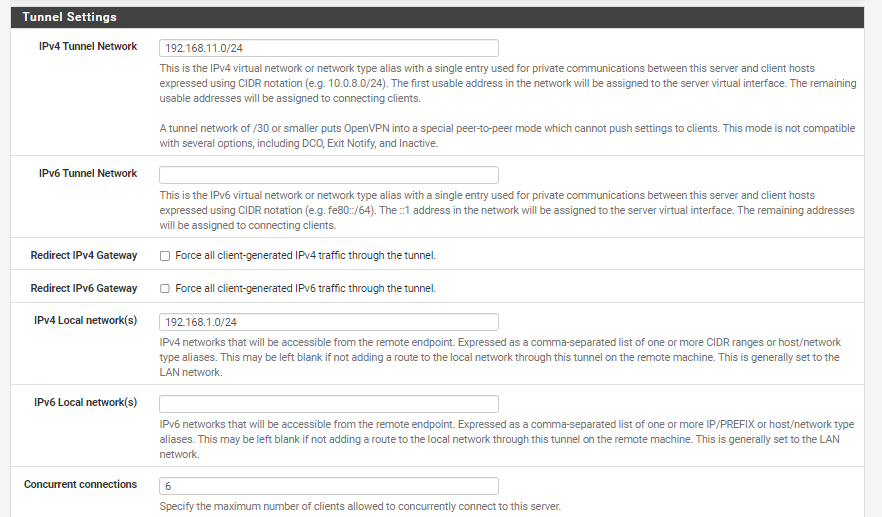
IPv4 Tunnel Network: I essentially make this up, right? Hence the 69s - the idea is that this should be different than my IPv4 Local Network to avoid overlap?
IPv4 Local Network: This should be the default (I haven't changed the default), correct?Firewall Config
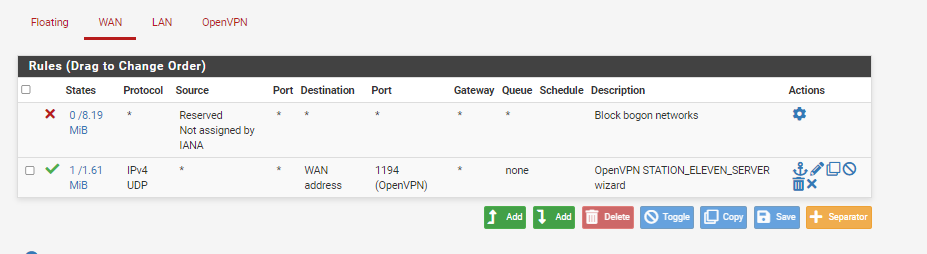
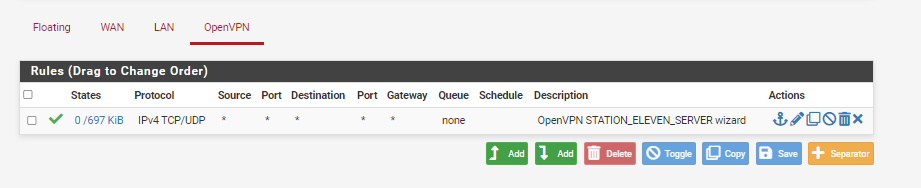
These were created through the wizard
Problem From my laptop, I can connect to the OpenVPN client - I can see that my private IP address is the same as the tunnel address (192.168.11.2). however - If I try to Ping 192.168.1.1 I get 'Request timed out.'
alternatively, if I try to RDP, I can't find my tower (I've confirmed on my regular wifi network, I can RDP).Any thoughts?
thanks in advance! -
You've shown the "WAN" and "OpenVPN" firewall rules.
Both WAN and OpenVPN show that there is/was incoming traffic. That's a good sign.@stationeleven said in RDP to Local LAN desktop - Unable to find:
(I've confirmed on my regular wifi network, I can RDP)
No further info, so I presume from now on : from your regular wifi you have the same network, both for the laptop and the PC tower where you 'RDP' to.
The info you're probably missing is this :
The RDP server process on Tower PC only accepts connections from it's own (= pfSense LAN) network.
So, if your PC Tower has 192.168.1.x, it will only accept, by default, connection from the 192.168.1.x/24 range. That's a security "better safe then sorry" default setting.
When you connect from VPN, your laptop will have, as said : 192.168.11.2
So your power PC will refuse that.
Remember : that device has also a firewall !Solution : modify the firewall on the Tower PC so it also accepts connections from 192.168.11.0/24 also (clean solution) - or do what most do : have it accept connection from 'everybody' (dirty solution).
-
Hi @Gertjan - thanks for your response!
I performed two tests:
-
Setting my tunnel network to 192.168.1.0/14 - which resulted in my OpenVPN laptop having a private IP of 192.168.1.2 (Same subnet) - still no result
-
I've added the following rules on my LAN tower firewall:
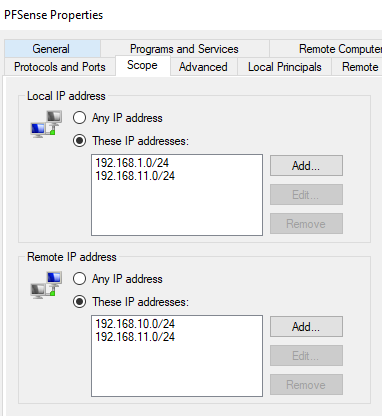
Still no results.
Am I missing some setting here on my LAN tower? Do I need something else to make sure all of it's traffic runs through the NetGate router? I'm not running OpenVPN on the tower, but it has an ethernet cable direct to the NetGate box -
-
@stationeleven said in RDP to Local LAN desktop - Unable to find:
Setting my tunnel network to 192.168.1.0/14 - which resulted
in a big mess.
If your LAN has 192.168.1.0/24 and your OpenVPN interface (tunnel) also uses 192.168.1.0/14 (14 ?) you just broke routing. Thee overlap. That's big no-no land.
"You broke Ethernet".Keep the openvpn tunnel at 192.168.11.1/24
You can ping from the OpenVPN device (192.168.11.2) an interface that you know will reply on ping : 192.168.1.1 = the LAN IP of pfSense ?
The default LAN firewall permits 'ping'.Btw : who is 192.168.10.0/24 ?
@stationeleven said in RDP to Local LAN desktop - Unable to find:
Do I need something else to make sure all of it's traffic runs through the NetGate router?
Noop.
A 'PC' that you buy, with any OS you can obtaion your hands on (Micisoft, MACOS, some Linux clone, FreeBSD etc etc) all will work right after you installed the OS.
As they all use DHCP (and certainly not static IP settings) to obtain an IP gateway, DNS network by default.Run "ipconfig /all" on the server. It should say that all is well.
@stationeleven said in RDP to Local LAN desktop - Unable to find:
I'm not running OpenVPN on the tower, but it has an Ethernet cable direct to the NetGate box
Yeah, don't worry, I have the same setup. OpenVPN on pfSense. So I can connect to that OpenVPN server from all over the planet and use my LAN resources.
pfSense LAN is 192.168.1.1/24 - my Windows server has IP 192.168.1.4 - RDP is activated.
I selected 'private' as a network group, not 'Public' on that server - as that would block any access to the server, even when coming from it's own LAN devices (except Internet = gateway traffic)
And I changed the firewall rule on the server so the "remote desktop" would can accept connection from outside of my LAN.
Have a small tour on the Internet, this subject is very know, especially since 2020 when some major health event forced many people to use equipment remotely. -
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
Check your vpn settings for remote access. VPN for remote access
-
@Gertjan thanks for the thorough reply.
I have moved my tunnel IP back to 192.168.11.1, made sure that was allowed inbound and outbound on my windows firewall for that specific tunnel IP and the IP that shows as my private IP in OpenVPN client.
Still nothing - Ping results in either 'request timed out' or 'general failure', and I'm unable to find my computer via the Remote Desktop Connection app.
Are you able to expand on how you did this:
I changed the firewall rule on the server so the "remote desktop" would can accept connection from outside of my LAN.
-
Solved!
Followed a lot of rabbit holes down until I found these:
https://serverfault.com/questions/1064935/openvpn-server-connexion-ok-but-no-access-to-remote-lanwhich lead to:
https://openvpn.net/community-resources/how-to/#expanding-the-scope-of-the-vpn-to-include-additional-machines-on-either-the-client-or-server-subnetMain take away was that I needed to add
push "route [Local LAN subnet] 255.255.255.0"to the advanced configuration on the server setup.
Still reading a bit more to understand how this worked, but I'm able to ping my local machine as well as remote into it.Happy days.