Block External DNS
-
I'm having a hard time figuring out how to block external DNS for all LAN net and allow only a few IP address to access Google DNS servers.
In the firewall LAN rules I have the following:
LAN Rules
Action: Pass
Protocal: IPv4 TCP/UDP
Source: *
Port: *
Destination: LAN address
Port: 53 (DNS)Action: Block
Protocal: IPv4 TCP/UDP
Source: *
Port: *
Destination: *
Port: 53 (DNS)Action: Block
Protocal: IPv4 TCP/UDP
Source: *
Port: *
Destination: *
Port: 853 (DNS over TLS)Action: Block
Protocal: IPv4 TCP/UDP
Source: *
Port: *
Destination: IP_PublicDNS
Port: 443 (HTTPS)In the DNS Resolver I have the following in the custom options:
server:
access-control-view: 192.168.5.24/32 bypass
access-control-view: 192.168.5.102/32 bypass
access-control-view: 192.168.5.109/32 bypass
access-control-view: 192.168.5.0/24 dnsbl
rrset-roundrobin: yes
forward-zone:
name: "."
forward-ssl-upstream: yes
forward-addr: 208.67.222.222@853
forward-addr: 208.67.220.220@853
forward-addr: 8.8.8.8@853
forward-addr: 8.8.4.4@853
view:
name: "bypass"
view-first: yes
include: /var/unbound/host_entries.conf
local-data: "www.youtube.com 60 IN A 216.239.38.119"
view:
name: "dnsbl"
view-first: yes
include: /var/unbound/host_entries.conf
# local-zone: "youtube.com" inform_deny
# local-zone: "facebook.com" inform_deny
include: /var/unbound/pfb_dnsbl.*conf -
@wolf07 To access Google DNS directly? That can be done just with firewall rules. Something like:
Pass LAN Net to LAN_Address:53
Pass (allowed_PC_alias) to (external_DNS_alias):53
Block/reject LAN Net to any:53
Block/reject LAN Net to any:853
Block/reject LAN Net to IP_PublicDNS:443 -
@steveits agreed, while yeah that 853 should be there if your goal is blocking possible external dot access. Clients don't normally do dot, they use doh.. But doesn't hurt to put that in there for sure. Keep in mind there some known dot servers using other ports as well.
Blocking doh or dot seems to be a game of wack-a-mole.. Kind of like blocking spam, you filter one way, and they find some other way to circumvent your filtering.
We can fight the good fight - but blocking doh, if to some unknown IP makes it almost impossible.. While I can have a list of fqdn to filter via dns, and can have a list of known IPs and block those. If the client has some IP its going to use that is not known to be a doh server how do you block it, blocking 443 would break the internet for you.
This is a hill I will die on sort of battle.. But the whole mess of dot and doh is disheartening to be sure.. Put me down as "not a fan" that is for damn sure...
example of the fight.. My stupid wifes phone, while I see it is trying to test doh.. And my blocks are blocking it - I need to spend some time on her phone to figure out if can turn off whatever is trying to do it..
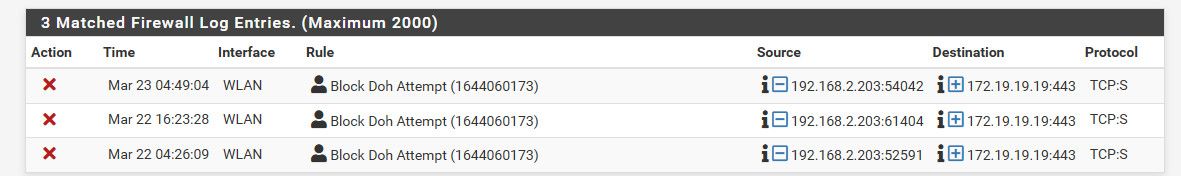
I resolve known doh fqdn to that 172.19.19.19 address, and then log and block any traffic to it - if a client tries to look up some known doh server fqdn, it tries to then access that IP which is blocked and logged.
I could just not resolve that for them, or send them a 0.0.0.0 or something - but this way I can see real easy in my firewall logs devices trying to use any of the doh servers I know about.
-
@steveits What is the difference if I block/reject any to any:53 compare to LAN Net to any:53?
-
@wolf07 Probably not much difference, in practice. I was writing quickly last night. Firewall rules apply as packets arrive on an interface. So in 99.9% of cases the only addresses on LAN are from LAN Net. In theory there could be another routed subnet that is behind LAN.
@johnpoz Someone posted this recently, seems a decent guide on DoH and has a (complex) guide for pfSense, pulling from his lists as URL aliases.
https://github.com/jpgpi250/piholemanual -
@steveits said in Block External DNS:
Probably not much difference, in practice
Exactly - but its good practice to use the network your setting the rule as source. Unless the network is a transit network, there should never be any source traffic hitting that interface that is not XYZ net, etc.
-
@johnpoz Then I suppose it would be more correct to use LAN Net for the pass rules and Any for the block/reject, so nothing slips past.
-
@steveits said in Block External DNS:
Any for the block/reject, so nothing slips past.
Remember there is default deny anyway - so if it wasn't lan net, then it would even be able to go to the 53 your allowing, etc.
Part of why its good practice to use the actual source net in you rules.. Even on your any rule for internet, etc. Unless its a transit network and other networks are going to be source of traffic into the interface, even then you should prob use say an alias or a cidr to limit to what specific downstream networks you have.
-
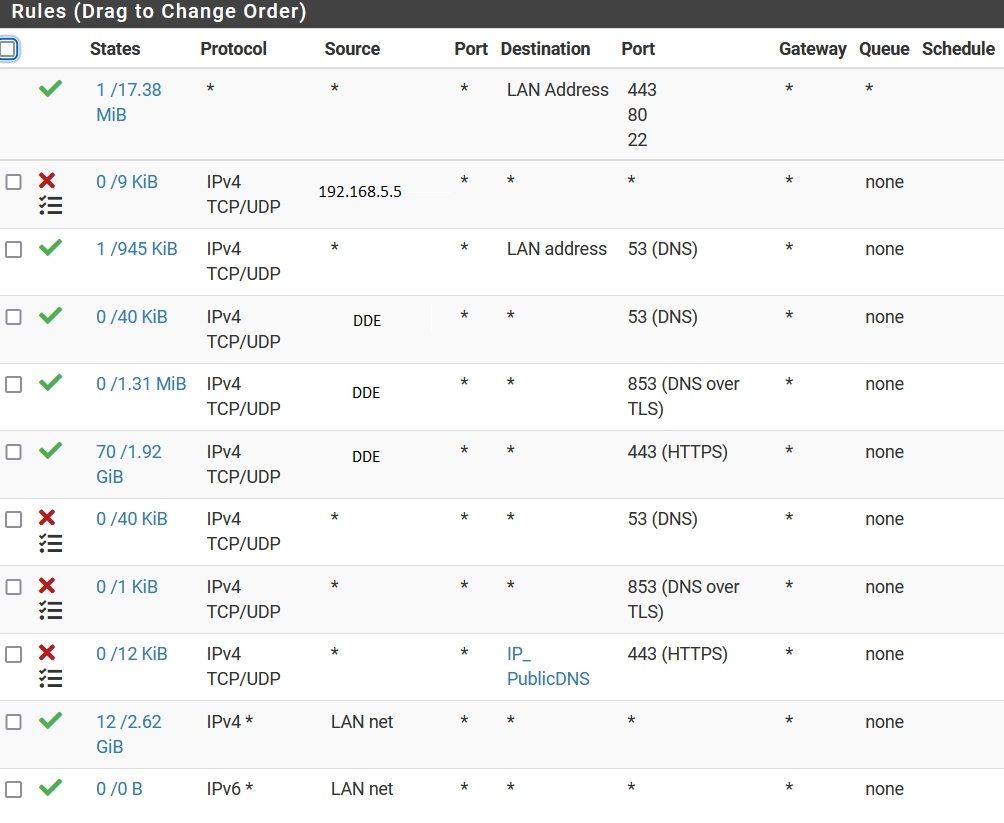
@johnpoz So something like the attached?
-
@wolf07 Sure. Although note blocking to IP_PublicDNS:443 doesn't block to any other DoH servers that aren't in that alias.