ISP blocking and VPN
-
Good day to all!
I have VPN client on my pfsense installed. All working fine , all my LAN network use VPN client and if checking IP show me the VPN client IP address. But in my country government block some sites from watching. If I'm start using VPN client directly from home laptop I can entering this sites but when start use pfsense VPN client can not. Can someone explain this magic and what can I do to bypass this just using VPN client on pfsense. -
@antibiotic What are you doing for dns, its possible the dns for where you are trying to go is blocked or redirected to somewhere else, etc..
You most likely want to make sure your dns is being done through the vpn as well.
Even if pfsense routes traffic out a vpn connection, the dns pfsense does might just go out your normal wan, etc.
-
@johnpoz I have default settings regarding DNS.
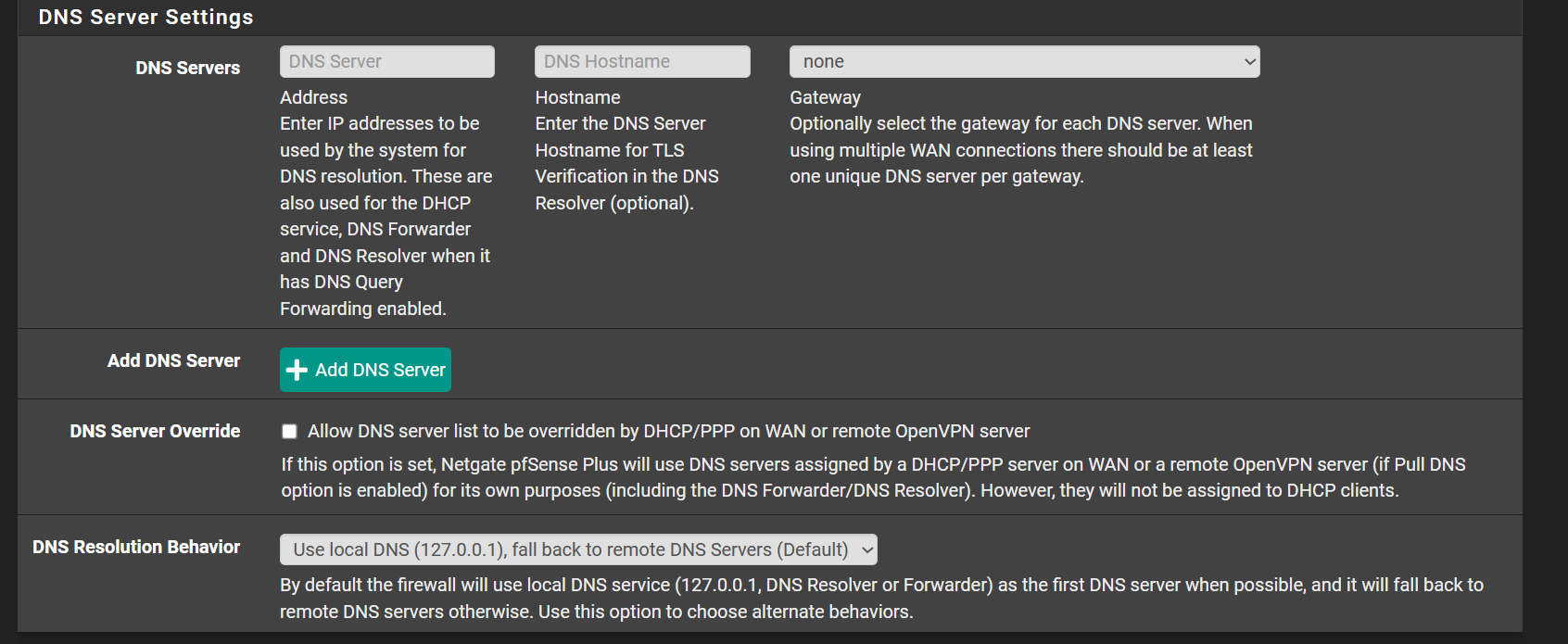
-
@johnpoz You most likely want to make sure your dns is being done through the vpn as well (Could you please show me , what should I do to prevent this?)
-
@antibiotic well out of the box unbound resolves.. So you could set unbound to use your vpn interface for dns, or you could use localhost for your outbound interface, if your default route on pfsense is using vpn.
Or you could run another dns on your network so it routes out your vpn for sure like your clients.
Some vpn clients don't like you to use any other dns then the one they provides.. So you might need to setup unbound to forward to whatever your vpn dns is providing, etc.
To test if dns related - set one of your clients on your network to use the vpn dns, or some external dns which would flow through the vpn and see if you can connect to that your trying to connect to.
-
@johnpoz Could you please more in details, I'm not a expert in pfsense. I will try all options to find out what working for me.
-
@johnpoz Solved when set outbound interface to localhost. But default gateway should left ISP or my VPN in state routing
for more private? Because working and open blocking sites in both way? -
@antibiotic there are many ways to skin this cat.. Without the specific details of how you setup, etc..
But for example here I changed my unbound to use my vpn interface, then on a client I do a dnsleak test on one of the leak test sites and you can see it shows my "leak" IP as my vps that I have my vpn connection running too
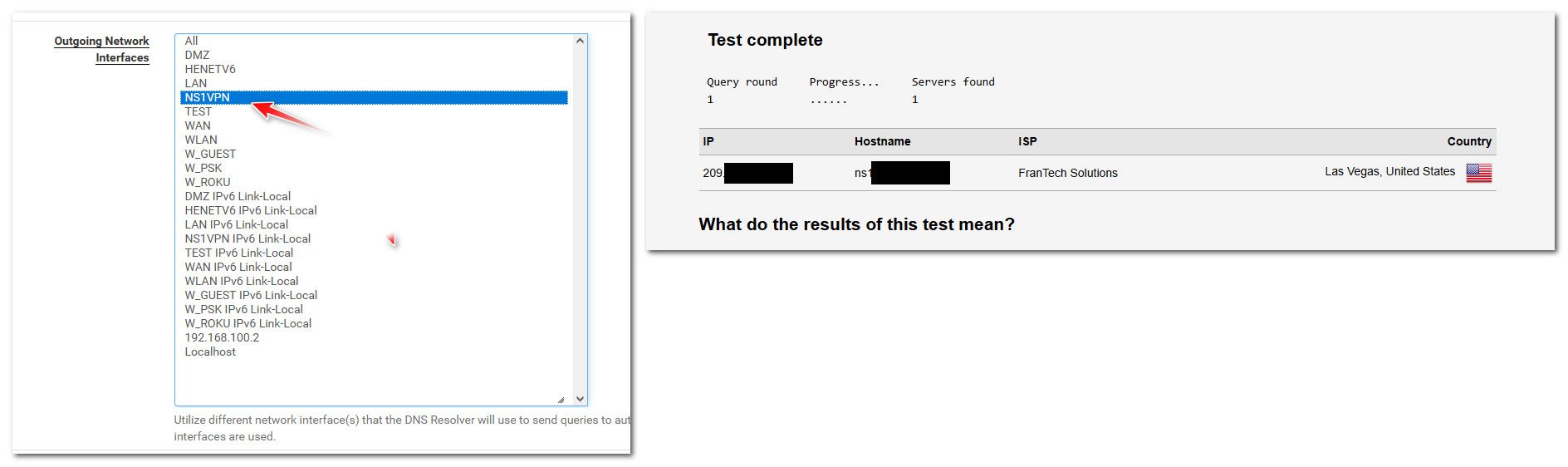
If I just let unbound use my normal wan, or local host since my default route is my isp.. Which it should be even when using a vpn.. You can see it shows my actual wan connection IP.
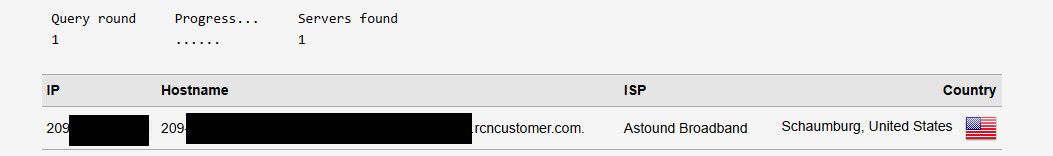
-
@johnpoz What done. Set in system-routing to VPN client gateway default not ISP gateway. DNS resolver set to localhost outgoing interface and network interface to LAN and localhost. DNS leak test now show only VPN DNS servers a lot. Can entering blocking news sites in my region. Should now calm down for privacy?)) or did wrong something or its looks OK?
-
@antibiotic like I said different ways to skin the cat.. Setting your vpn connection in routing gui shouldn't be a big deal, I wouldn't do it that way myself.. But if its working, then you should be good.. But if your vpn goes down your going to loose all connectivity most likely?
-
@johnpoz Ah understood if going down VPN will lost my inet but if reset to default ISP gateway now and use in this way, during VPN problem on upstream VPN servers. My inet will exist with DNS resolver settings above? Second question: with default ISP gateway will this less privacy? Should I create for every other VPN location new VPN client in pfsense or exist way to combine a few locations in one settings? I mean to choose different locations like in VPN client on PC.