How to block a Domain and it's subdomains being accessed via IP address (without DNS-Filter)
-
@sgrockfort said in How to block a Domain and it's subdomains being accessed via IP address (without DNS-Filter):
domain 1e100.net and all subdomains
You can do that with simple unbound, that is just a redirect
local-zone: "1e100.net" redirect
local-data: "1e100.net 3600 IN A 127.0.0.1"Would prevent any access to anything.1e100.net
Or just a simple always_nxdomain
local-zone: "1e100.net" always_nxdomain
As to blocking IP.. you would have to use pfblocker and use ASNs or whois info..
-
@johnpoz Hello John, thank you for the quick answer.
accesses to the domain are now blocked. No matter whether I access it by name or IP. However, this does not work on subdomains. Here, the accesses continue to work. Regardless of whether I access it via DNS or IP. I have attached two screenshots...
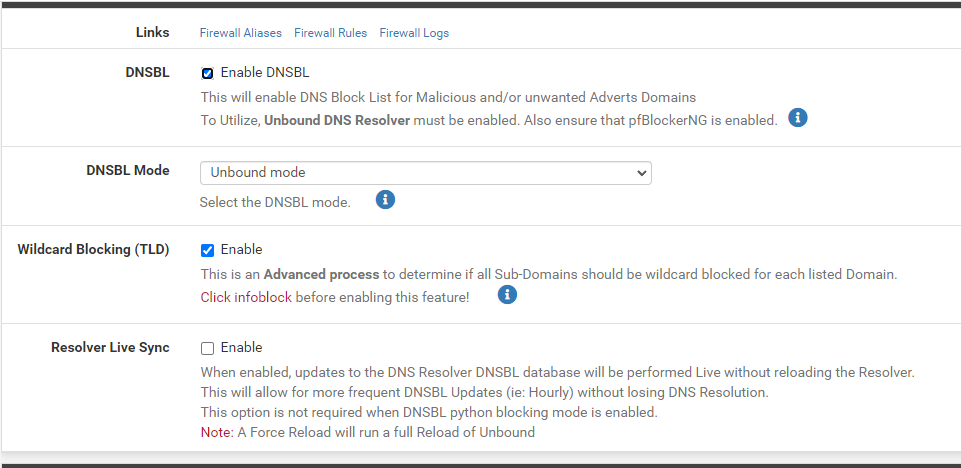
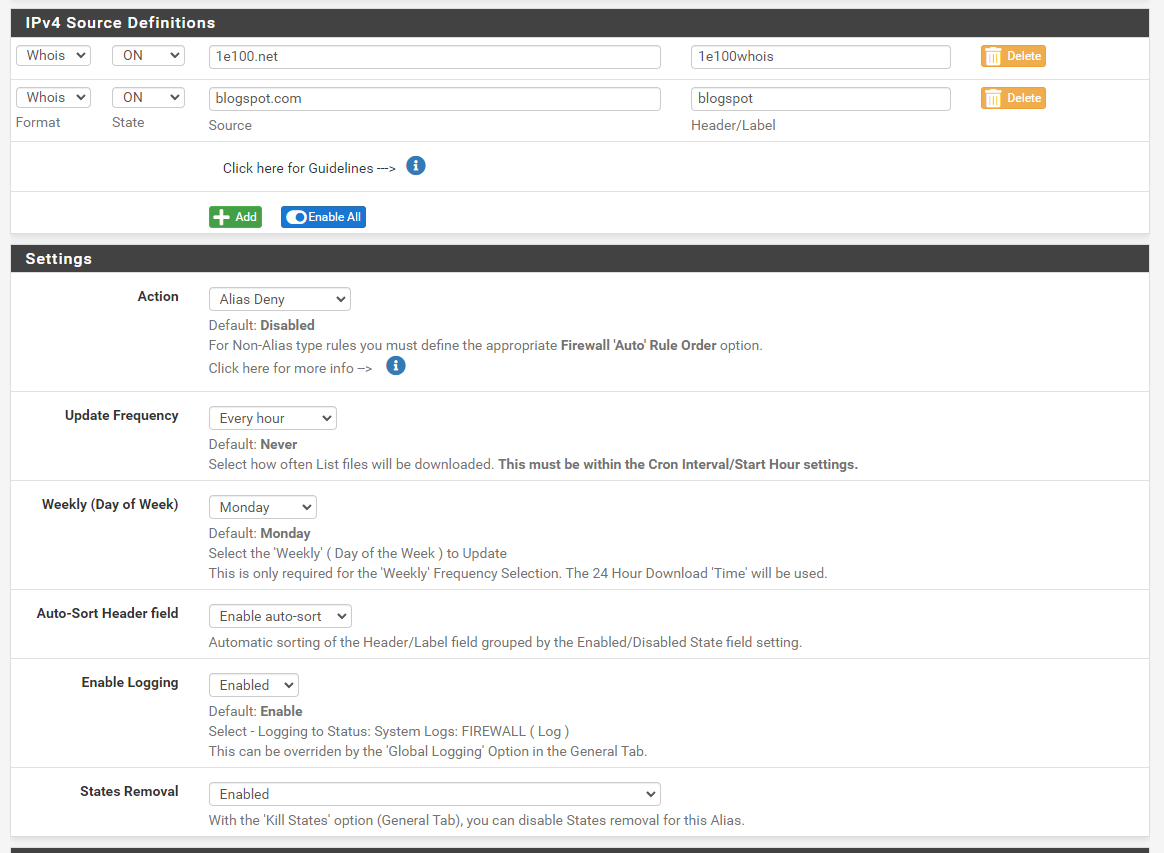

Thank you !!
-
@sgrockfort and what does that whois fill in for your table. and what subdomain are you looking up?
You understand wildcard blocking something.example.com or otherthing.example.com is not what you have there.. and is completely different than a whois lookup.
Also your only blocking tcp.. You understand QUIC and udp is now used to access many things over the internet on 80 and 443.
My example is just in unbound and blocks something.blocked.com or blocked.com or whatever.blocked.com - that is not what your doing with that checkmark in wildcard tld, and what gets blocked with a whois for 1e100.net you would have to look what gets populated in the table..
-
@johnpoz Thank you so far.. It seems I miss some basic understandings and will dive a bit deeper firstly.
What I basically want is to block all connections to 1e100.net and all it tons of subdomains. Regardless if someone (or some process) use a name or an IP.
Thank you

-
@sgrockfort as already went over a dns block can stop something.1e100.net or otherthing.1e100.net
But to block IP you would need to know what IP they are trying to talk to or what ASN that has the IP(s) they are talking too.
Keep in mind that if you look up say something.1e100.net or otherthing.1e100.net, the IPS might be in completely different ASNs So if the the device is using IP to talk that it knows about and doesn't need to look up via dns.. You have to know what IPs those are, then you can either block the specific IP, or the whole netblock(s) that are routed by the ASN..
But there is no dns lookup that can stop a client from using some hard coded IP.. And if they are using hardcoded IPs - how would you know what those are or what ASN they are even in without actually seeing the traffic..
You could block anything.1e100.net and all IPs via asn X for anything at all related to that, but for all you know the IP they are talking to is in asn Y or Z..
Keep in mind as well as now these applications or iot devices are using doh to circumvent any local dns controls.. So you have to block that as well, which can be difficult if they are not using wellknown doh servers, etc.
-
@johnpoz oh wow. This worked fine :-)
I have blocked the ASN that contains the domain and the connections are now blocked. That was the building block I was missing and here I learned something again.
Probably other domains are now also blocked within the ASN that I didn't want to have, but anyway, it was just a matter of understanding.
 Furthermore, I have understood that it does not work the way I thought it would before. (And this was basically my question)
Furthermore, I have understood that it does not work the way I thought it would before. (And this was basically my question) 
Many thanks for your effort !!!!
-
@sgrockfort said in How to block a Domain and it's subdomains being accessed via IP address (without DNS-Filter):
I have blocked the ASN
Yeah that can be very problematic with something like ie100.net (google) But that will most likely show up in lots of ASNs all across the globe.. What specific one(s) did you block?
They use that as the PTR for all of their ips..
https://support.google.com/faqs/answer/174717?hl=en
Not sure exactly how you found it to be honest, you prob shouldn't be blocking that, you blogspot.com would be a forward domain, and again prob hosted off multiple IPs globally.
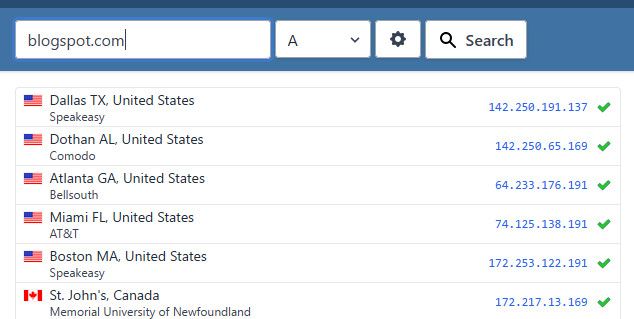
So blocking all of those different IP ranges or ASNs is most likely going to block stuff you don't want to block, etc...
And if your clients are allowed to use IPv6 - its more that would need to be blocked..
edit: As a side not when blocking stuff - keep in mind if your client creates a state to 1.2.3.4 you blocking 1.2.3.0/24 would do nothing because the state would allow the traffic anyway. When you create blocks, you need to make sure there are no existing states currently for the destination IP/Range you want to block.. Or you block will not seem to be working, until that state goes away via timeout or is killed or closed by the normal means, etc.
-
@johnpoz Hello John,
yes, you are right... I blocked AS15169 and the 1e100 was blocked.
Unfortunately, everything else from google too. Of course, this is not what I originaly wanted. But at least I now understand how it basically works or doesn't work.
I am currently working on two other solutions.
-
since I now know the IP ranges of AS15169, I'll build a script that performs a one-time reverse lookup on each IP and thus generate a list of IPs that belong to 1e100.net.
-
I try to find out via wireshark if/which DNS servers Chrome uses for doh and block them. Maybe I can achieve that my own DNS is used or has to be used and can then simply filter out the domain via DNS.
-
-
p.s. I have just blocked the first /24 network, in which there were only IPs with the name 1e100.net. Unfortunately, this actually leads to the fact that everything that somehow goes hand in hand with google no longer works.
As already mentioned, I was more concerned with the technical implementation than with any real benefit.
anyway, thanks again.
-
@sgrockfort said in How to block a Domain and it's subdomains being accessed via IP address (without DNS-Filter):
a list of IPs that belong to 1e100.net.
That is every single one of their IPs ;) -- did you read the link I posted?
;; QUESTION SECTION: ;google.com. IN A ;; ANSWER SECTION: google.com. 192 IN A 142.250.190.46 ;; QUESTION SECTION: ;46.190.250.142.in-addr.arpa. IN PTR ;; ANSWER SECTION: 46.190.250.142.in-addr.arpa. 86400 IN PTR ord37s33-in-f14.1e100.net.They use the 1e100.net for their PTR for every one of their IPs.. This is a "reverse" lookup, again not something you should be concerned with.. You should be concerned with blocking the forward fqdn your device/user is trying to go too.
;; QUESTION SECTION: ;www.google.com. IN A ;; ANSWER SECTION: www.google.com. 676 IN A 172.217.4.68 ;; QUESTION SECTION: ;68.4.217.172.in-addr.arpa. IN PTR ;; ANSWER SECTION: 68.4.217.172.in-addr.arpa. 86400 IN PTR ord37s18-in-f4.1e100.net. 68.4.217.172.in-addr.arpa. 86400 IN PTR lga15s47-in-f68.1e100.net.blogspot.com. 30 IN A 142.251.32.9 9.32.251.142.in-addr.arpa. 86400 IN PTR ord38s33-in-f9.1e100.net. -
@johnpoz said in How to block a Domain and it's subdomains being accessed via IP address (without DNS-Filter):
They use the 1e100.net for their PTR for every one of their IPs.. This is a "reverse" lookup, again not something you should be concerned with.. You should be concerned with blocking the forward fqdn your device/user is trying to go too.
Yes, thank you, I read the article from the link.

I'm not really worried about it either. But I hate it when a system tries to escape my control by cooking its own soup. It's just a principle that triggers me and I enjoy trying to find a solution. Besides, you always learn quite a lot in the process.
I looked at what Chrome does on startup using mitmproxy and if I saw it correctly, Chrome doesn't actually do DoH/DoT queries. Presumably some IPs are actually hardcoded.
The easiest thing to do is probably to uninstall Chrome.

