Authentication failed after cert renewal
-
Good day,
First, thanks for reading.
Second, I can't stress enough how perfectly everything was working for the whole year before this.
Per the title, I recently had to renew an expired certificate. I inadvertently renewed the CA as it was initially the only one I saw. Not sure now, in retrospect, if it had expired or not. It may have since all this was set up at or near the same time.
After that potential blunder, I was still getting certificate errors, so I dug a little deeper on the Certificate Manager page and found I missed my OpenVPN-specific cert (didn't notice the tabs at the top; hence why I only saw the CA at first). Renewed that and now it looks like all of my certificates are up to date. The certificate error went away, but now I'm getting a new authentication error. The client side logs aren't very revealing but the server side reads to me like there is still a certificate problem.
My only client is the OpenVPN Connect app on my Android phone.
Things I've tried:
- Reset user password (obviously)
- Renewed all other certs after CA renewal (not sure if it was needed but felt like the right thing to do)
- Restart OpenVPN service
- Re-exported configs for client app; set client up from scratch (I feel like something in this region is where I'm doing something wrong)
- Tried connecting from 4G instead of wifi
- Searched the web for errors in the logs; so far nothing has pointed me in a positive direction
Hardware/setup:
Netgate SG-1100
OpenVPN server created via Wizard (I connect from my phone directly to the IP assigned by my ISP; no dynamic DNS service or anything)
Client config exported via Pfsense's OpenVPN -> Client Export Utility -> Defaults -> OpenVPN Connect (iOS/Android) (which I'm pretty sure is how I did it on initial setup but could be mistaken).Here is an example from the client logs:
21:50:02.770 -- ----- OpenVPN Start ----- 21:50:02.770 -- EVENT: CORE_THREAD_ACTIVE 21:50:02.774 -- OpenVPN core 3.git::d3f8b18b:Release android arm64 64-bit PT_PROXY 21:50:02.776 -- Frame=512/2048/512 mssfix-ctrl=1250 21:50:02.777 -- UNUSED OPTIONS 0 [persist-tun] 1 [persist-key] 2 [ncp-disable] 5 [tls-client] 8 [nobind] 12 [explicit-exit-notify] 21:50:02.777 -- EVENT: RESOLVE 21:50:02.778 -- Contacting <my server IP>:1194 via UDP 21:50:02.778 -- EVENT: WAIT 21:50:02.782 -- Connecting to [<my server IP>]:1194 (<my server IP>) via UDPv4 21:50:03.060 -- EVENT: CONNECTING 21:50:03.063 -- Tunnel Options:V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-256-CBC,auth SHA256,keysize 256,tls-auth,key-method 2,tls-client 21:50:03.064 -- Creds: Username/Password 21:50:03.064 -- Peer Info: IV_VER=3.git::d3f8b18b:Release IV_PLAT=android IV_NCP=2 IV_TCPNL=1 IV_PROTO=30 IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC IV_GUI_VER=net.openvpn.connect.android_3.3.1-9079 IV_SSO=webauth,openurl 21:50:03.235 -- VERIFY OK: depth=1, /CN=bitblizzard-ca/C=US/ST=MI/L=Niles/O=Bitblizzard/OU=All, signature: RSA-SHA512 21:50:03.236 -- VERIFY OK: depth=0, /CN=BitblizzardRoaming/C=US/ST=MI/L=Niles/O=Bitblizzard, signature: RSA-SHA256 21:50:07.178 -- SSL Handshake: peer certificate: CN=BitblizzardRoaming, 2048 bit RSA, cipher: TLS_AES_256_GCM_SHA384 TLSv1.3 Kx=any Au=any Enc=AESGCM(256) Mac=AEAD 21:50:07.179 -- Session is ACTIVE 21:50:07.180 -- EVENT: GET_CONFIG 21:50:07.182 -- Sending PUSH_REQUEST to server... 21:50:08.178 -- Sending PUSH_REQUEST to server... 21:50:08.355 -- AUTH_FAILED 21:50:08.356 -- EVENT: AUTH_FAILED 21:50:08.360 -- EVENT: DISCONNECTED 21:50:08.360 -- Tunnel bytes per CPU second: 0 21:50:08.360 -- ----- OpenVPN Stop -----And here is an example from the server logs (this was after a fresh restart of the service):
Apr 2 19:40:57 openvpn 55784 /usr/local/sbin/ovpn-linkdown ovpns2 1500 1621 10.0.8.1 255.255.255.0 init Apr 2 19:40:58 openvpn 55784 SIGTERM[hard,] received, process exiting Apr 2 19:40:58 openvpn 56262 DEPRECATED OPTION: ncp-disable. Disabling cipher negotiation is a deprecated debug feature that will be removed in OpenVPN 2.6 Apr 2 19:40:58 openvpn 56262 DEPRECATED OPTION: --cipher set to 'AES-256-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add 'AES-256-CBC' to --data-ciphers or change --cipher 'AES-256-CBC' to --data-ciphers-fallback 'AES-256-CBC' to silence this warning. Apr 2 19:40:58 openvpn 56262 OpenVPN 2.5.2 aarch64-portbld-freebsd12.2 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on May 4 2021 Apr 2 19:40:58 openvpn 56262 library versions: OpenSSL 1.1.1k-freebsd 25 Mar 2021, LZO 2.10 Apr 2 19:40:58 openvpn 56368 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Apr 2 19:40:58 openvpn 56368 WARNING: experimental option --capath /var/etc/openvpn/server2/ca Apr 2 19:40:58 openvpn 56368 TUN/TAP device ovpns2 exists previously, keep at program end Apr 2 19:40:58 openvpn 56368 TUN/TAP device /dev/tun2 opened Apr 2 19:40:58 openvpn 56368 /sbin/ifconfig ovpns2 10.0.8.1 10.0.8.2 mtu 1500 netmask 255.255.255.0 up Apr 2 19:40:58 openvpn 56368 /usr/local/sbin/ovpn-linkup ovpns2 1500 1621 10.0.8.1 255.255.255.0 init Apr 2 19:40:58 openvpn 56368 UDPv4 link local (bound): [AF_INET]73.210.203.179:1194 Apr 2 19:40:58 openvpn 56368 UDPv4 link remote: [AF_UNSPEC] Apr 2 19:40:58 openvpn 56368 Initialization Sequence Completed Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 peer info: IV_VER=3.git::d3f8b18b:Release Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 peer info: IV_PLAT=android Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 peer info: IV_NCP=2 Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 peer info: IV_TCPNL=1 Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 peer info: IV_PROTO=30 Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 peer info: IV_GUI_VER=net.openvpn.connect.android_3.3.1-9079 Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 peer info: IV_SSO=webauth,openurl Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #6 / time = (1680478935) 2023-04-02 19:42:15 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 TLS Error: incoming packet authentication failed from [AF_INET]192.168.1.4:59144 Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #7 / time = (1680478935) 2023-04-02 19:42:15 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 TLS Error: incoming packet authentication failed from [AF_INET]192.168.1.4:59144 Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #6 / time = (1680478935) 2023-04-02 19:42:15 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 TLS Error: incoming packet authentication failed from [AF_INET]192.168.1.4:59144 Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #7 / time = (1680478935) 2023-04-02 19:42:15 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 TLS Error: incoming packet authentication failed from [AF_INET]192.168.1.4:59144 Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #6 / time = (1680478935) 2023-04-02 19:42:15 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 TLS Error: incoming packet authentication failed from [AF_INET]192.168.1.4:59144 Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 Authenticate/Decrypt packet error: bad packet ID (may be a replay): [ #7 / time = (1680478935) 2023-04-02 19:42:15 ] -- see the man page entry for --no-replay and --replay-window for more info or silence this warning with --mute-replay-warnings Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 TLS Error: incoming packet authentication failed from [AF_INET]192.168.1.4:59144 Apr 2 19:42:18 openvpn 56368 192.168.1.4:59144 [statik] Peer Connection Initiated with [AF_INET]192.168.1.4:59144 Apr 2 19:42:19 openvpn 19226 user 'statik' could not authenticate.Thanks again for reading...I have a feeling I'm about to feel really silly....
-
OpenVPN server uses a CA and derived from this CA, server certificate.
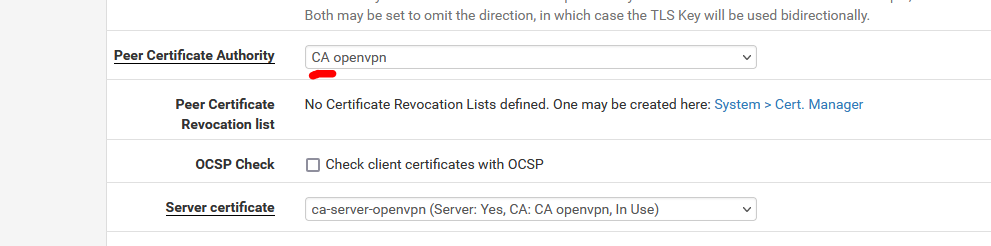
If any of these two changes, re export a openvpn client file, and you'll be fine.
-
@gertjan Thanks. Unless I'm misunderstanding you, I have already tried re-exporting the client config and setting up the client from scratch a few times after renewing all certs.
-
@statikregimen
You got that correctly.
Also : if you renew the CA, re create also the certificates based upon it.
Dono if thats needed, it seems just logic to me. -
Finally had a chance to look at this again after many days... I noticed my webConfigurator certificate was about to expire, even though I was pretty certain I had renewed everything. After renewing, I couldn't reach the server at all from my phone/client. Restarted the OpenVPN service on my Netgate, then phone/client connected but went back to "Authentication Error".
In a fit of desperation, I tried resetting my user password once more and everything started working again. Even after I changed it back to something secure, it has continued working.
Therefore, I guess I screwed up resetting my password before...Very embarrassing lol