Strange logs on pfSense - most probably somebody has found a way to hack partially the box
-
Hello,
i'm running CE 2.6.0 on a VM and found the following on the logs.
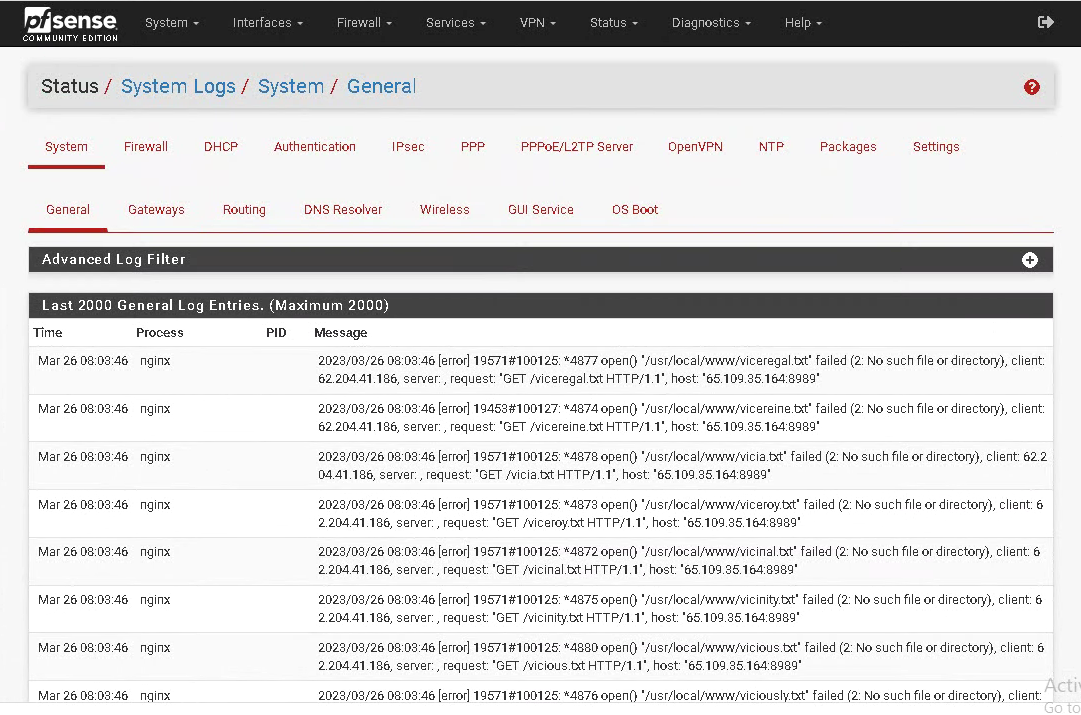
Some other info:
Web interface is not exposed on wan side. Nobody is on the lan side except my VM.
The IP that you see on the picture, is the public ip on the WAN side of pfsense.
8989 is the port of the web interface of pfSense.any idea?
-
This post is deleted! -
@albgen Please provide a screenshot of the WAN firewall rules.
-
What is the client IP shown: 62.204.41.186?
That clearly has access to the webgui. And probably shouldn't.
-
@stephenw10 Dont know how/where this pfsense is placed in the path but clearly there is a port open for management.
Its not hacking if the port is open for the Internet. -
That looks like a remote IP so the webgui is open via some unintentional rule.
It's probably just a config error though rather than some attack. Those logs show generic access attempts.
Steve
-
That is for sure a security problem.
The client IP is not known. There is no rule that allows traffic from wan to the pfsense.Let me ask a different question. From the lan side, how can i trigger a log that?
-
https://www.showmyip.com/ip-whois-lookup/?fields=66846719&ip=62.204.41.186
Looks like it's an Russian IP address, so if you're not in Russia...
-
@mvikman said in Strange logs on pfSense - most probably somebody has found a way to hack partially the box:
https://www.showmyip.com/ip-whois-lookup/?fields=66846719&ip=62.204.41.186
Looks like it's an Russian IP address, so if you're not in Russia...
of course i'm not in Russia and i have nothing to do with a Russian IP.
My Server is in Finland, Helsinki
https://www.showmyip.com/ip-whois-lookup/?fields=66846719&ip=65.109.35.164 -
@albgen I can web to 65.109.35.164 8989 from lovely Illinois, USA. If you need to manage your FW remotely, setup VPN or just manage it locally from the LAN side.
-
@provels said in Strange logs on pfSense - most probably somebody has found a way to hack partially the box:
65.109.35.164 8989
No idea why is accessible. there is no such rule that allows it...
could it be because i have the config like this:
internet---A>Server-B>VMpfSense->LANThe public IP address is at point A and B is a private IP Address
but in any case, those logs are strange. I cannot trigger them
-
Still no rules posted.....
.... -
@pippin said in Strange logs on pfSense - most probably somebody has found a way to hack partially the box:
Still no rules posted.....
-
@albgen Not exactly sure what Server B is, but Internet should go to WAN side of pfSense, then pfSense to LAN. LAN would include the host the PFSense VM is runnng on.
-
@provels said in Strange logs on pfSense - most probably somebody has found a way to hack partially the box:
Not exactly sure what Server B is, but Internet should go to WAN side of pfSense, then pfSense to LAN. LAN would include the host the PFSense VM is runnng on.
A and B are just point i have inserted to make you understand what kind of IP Addresses are setup...
-
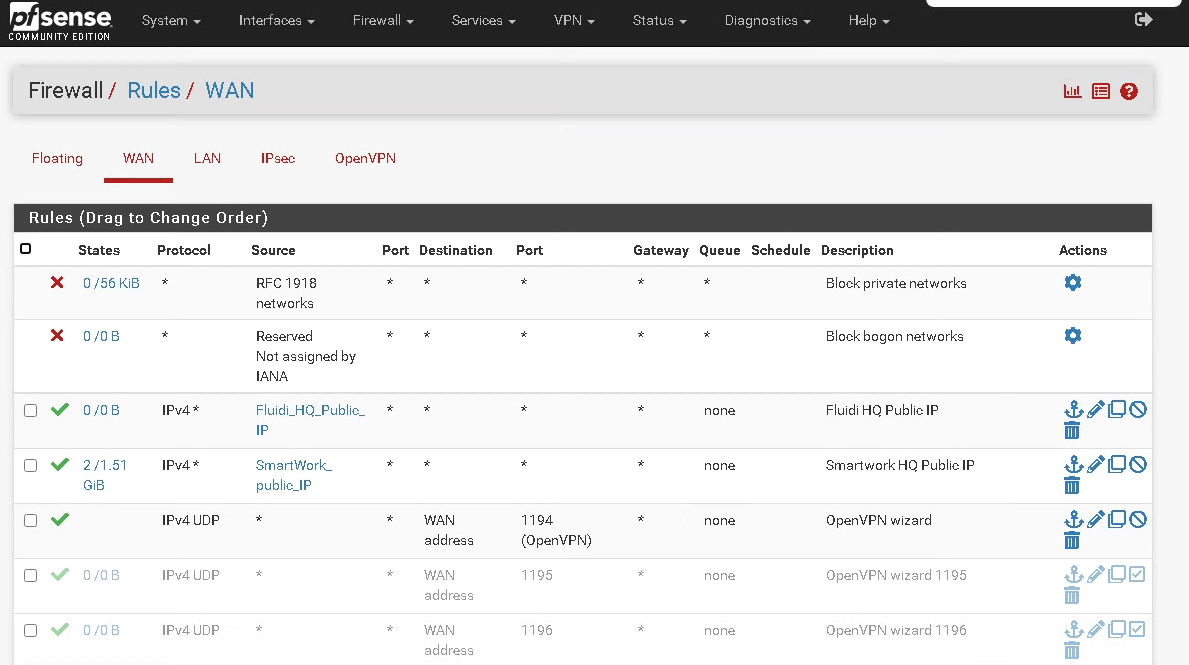
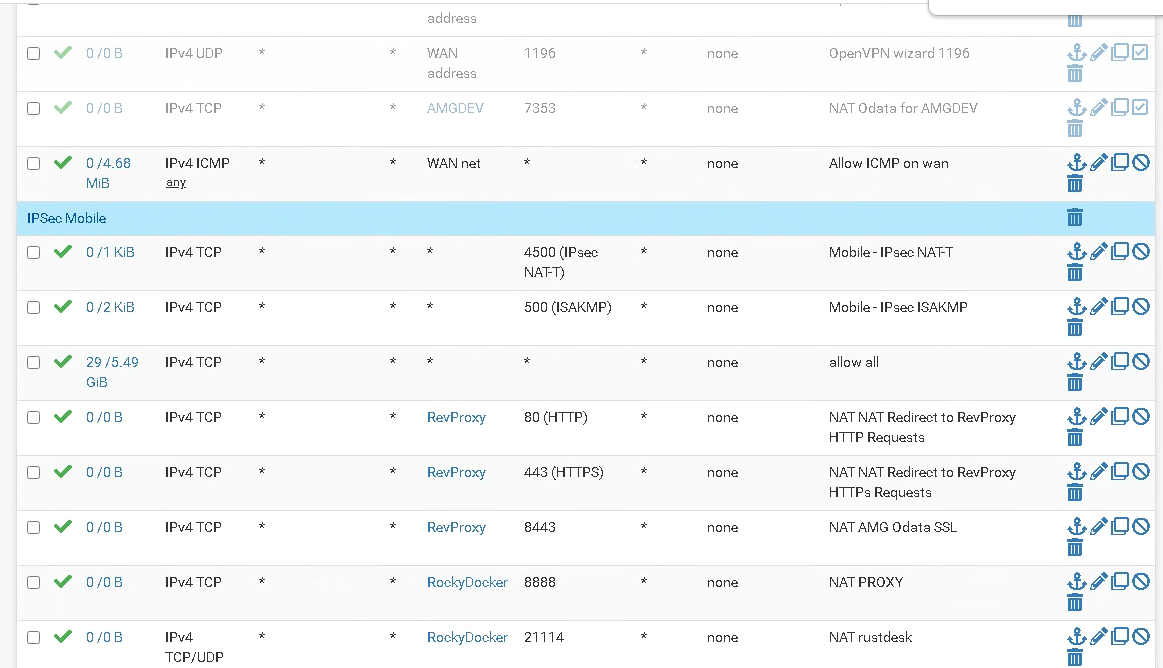
You have a rule allowing all TCP traffic on WAN. That's passing it.
-
Looks like you have an allow all rule. Lots of traffic on it also. 5 GB.
-
yes, correct. the allow all rule was actually allowing everything :)
but the question remains: how have they triggered those kind of logs?
-
@albgen said in Strange logs on pfSense - most probably somebody has found a way to hack partially the box:
yes, correct. the allow all rule was actually allowing everything :)
but the question remains: how have they triggered those kind of logs?
Bots or hackers just checking what you have going on. Given time they'd try a lot more things.
-
Because the webgui on the WAN interface was open to the internet.
You can see the requests they were making were all failing because the pages don't exist in pfSense. And even if they guessed an existing page they would not have been able to access it without logging in. But you should never open the webgui to public access.