Flooding
-
-
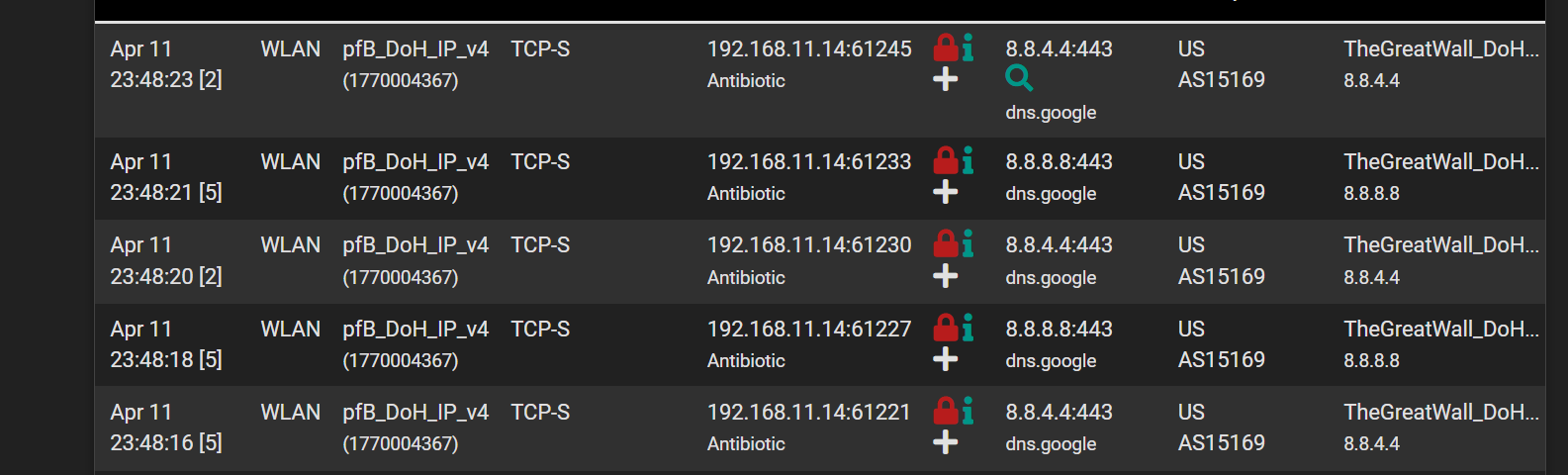
These are blocks from pfBlocker for DNS of HTTPs...
What's sitting at 192.168.11.14? You can find that in DHCP Leases (if it's a DHCP lease) if not you need to do a packet capture to get it's MAC and start hunting it down.
From there you can trace it - you cannot find the detail you need just from the packet because it's going to https
-
@rcoleman-netgate 192.168.11.14 - It's my laptop, some application on him is flooding.
-
This post is deleted! -
@antibiotic OK, then run a PCAP on your device.
The interface is WLAN - you have an interface called "WLAN", yes?
-
@rcoleman-netgate said in Flooding:
then run a PCAP on your device
Do you mean install wireshark To run PCAP? Yes it is WLAN
-
@antibiotic Wireshark
 is one way to do a package capture, yes.
is one way to do a package capture, yes. -
@rcoleman-netgate I did scanning on local host with wireshark. Have a lot of info, could be useful for pro. But again without a name of application?
-
@antibiotic you want the application on the .14 box creating the connections? Wireshark or sniffer not really going to tell you that.
since the traffic is tcp you should be able to just do a netstat with -b to show you the binary that is creating the connection.
-
@johnpoz Should to run this command on pfsense or local host?
-
@antibiotic your computer.
-
I have found this baby, it's a telegram! Thanks' to all for assistanse.