Rule Behavior Check Please!
-
Hi All,
I've been running Suricata now for a while (in IDS mode) and would like to enable blocking (legacy mode) on the LAN interface. However, I was wondering about the behavior for an alert that pops up once and a while (see screenshot below). In this case, an alert is thrown because a client made a suspicious DNS request to the router. So, if I enabled blocking, would this block the client, the router, both or neither?
Any insight would be super helpful. I really don't want to accidently lock myself out or something.

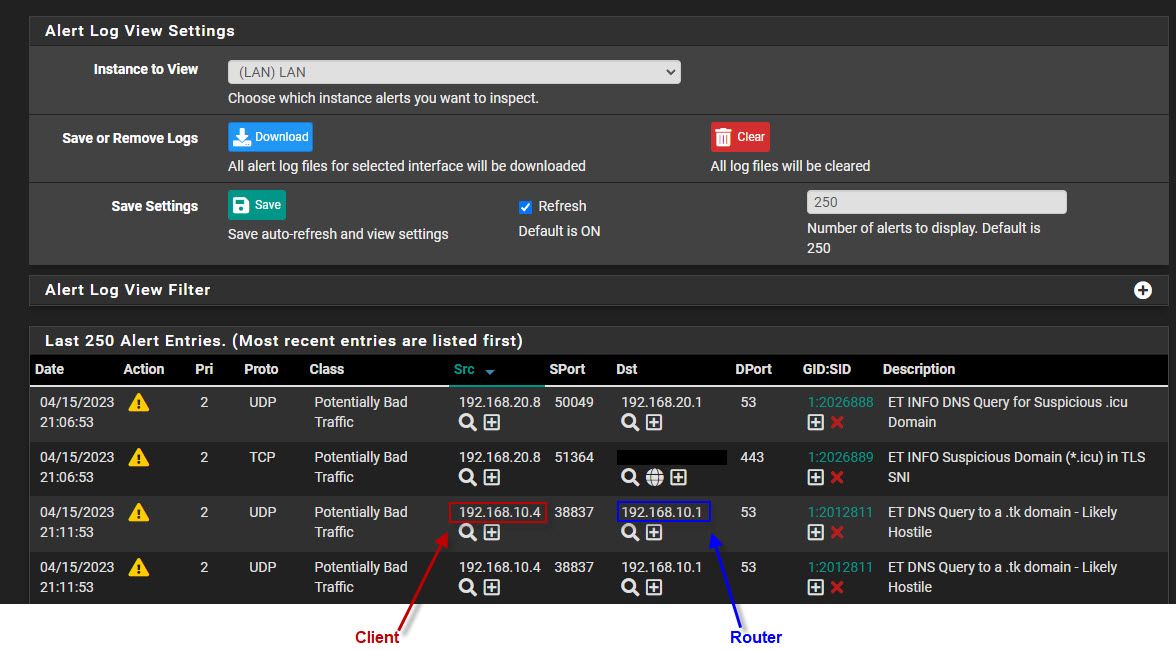
-
@uplink said in Rule Behavior Check Please!:
I've been running Suricata now for a whi
If its anything like snort, you define if you block the source, destination or both.
-
@uplink Local addresses never will be blocked, at least in theory.

But in any way, you should disable rules that don't fit your needs. -
@uplink said in Rule Behavior Check Please!:
Hi All,
I've been running Suricata now for a while (in IDS mode) and would like to enable blocking (legacy mode) on the LAN interface. However, I was wondering about the behavior for an alert that pops up once and a while (see screenshot below). In this case, an alert is thrown because a client made a suspicious DNS request to the router. So, if I enabled blocking, would this block the client, the router, both or neither?
Any insight would be super helpful. I really don't want to accidently lock myself out or something.


There is an automatic default pass list that is created and honored to prevent blocking of any direct firewall interface IP addresses (meaning the actual /32 IP address assigned to the firewall interface). Additionally, the default Pass List contains all locally defined IP subnets. IP addresses contained in a Pass List (including the default one) are not blocked.
-
Hey @bmeeks ,
Sounds like those default lists you are talking about are maybe those "Home_Net" and "External_Net" lists? So in my example, it sounds like I will see this alert, but neither of these internal IPs will actually be blocked (even though blocking is enabled).
I think I understand. Thank you all so much for the quick response!
-
@uplink said in Rule Behavior Check Please!:
Hey @bmeeks ,
Sounds like those default lists you are talking about are maybe those "Home_Net" and "External_Net" lists? So in my example, it sounds like I will see this alert, but neither of these internal IPs will actually be blocked (even though blocking is enabled).
I think I understand. Thank you all so much for the quick response!
Well, that's not totally correct for HOME_NET and EXTERNAL_NET. Those are specialized variables that serve another purpose related to how rules are triggered. More on that in a second.
I was specifically speaking of a new drop-down that will appear when you enable Legacy Mode Blocking called Pass List. There are some default entries that get populated for the "default" Pass List. That drop-down is hidden until you enable Legacy Blocking Mode.
HOME_NET and EXTERNAL_NET are used in the conditionals for rule triggering. HOME_NET is the collection of IP addresses and/or subnets that are to be protected. That variable represents your "network treasure" you are protecting. EXTERNAL_NET is usually defined as !HOME_NET (where the exclamation point means logical NOT). Or in other words, EXTERNAL_NET is the IP addresses of the "bad guys". And by using the definition !HOME_NET for EXTERNAL_NET, that means any IP address not covered in HOME_NET is automatically in EXTERNAL_NET. Many of the rules are written similar to this:
alert tcp $HOME_NET any -> $EXTERNAL_NET any ....So this rule snippet needs an IP address in the $HOME_NET variable to be communicating with an IP address in the $EXTERNAL_NET variable (and the protocol must be
tcpfor this example rule) in order for the rule to trigger. Conversely, you will also see rules written like this:alert udp $EXTERNAL_NET any -> $HOME_NET any ....This rule requires an IP in EXTERNAL_NET to be attempting to send a
udppacket to an IP in HOME_NET in order to trigger.You should never monkey around with HOME_NET or EXTERNAL_NET unless you are quite experienced with IDS/IPS operation and fully understand the potential consequences of a misconfiguration there. Putting the wrong values in those variables can render the IDS/IPS almost worthless because the rule conditional for source and destination will not be satisfied and therefore the rule will not trigger.
-
Oh, I see the PASS list now, it was right below the EXTERNAL_NET in the UI. Also, thank you so much for that explanation on HOME_NET and EXTERNAL_NET. That makes sense the way you've explained it. I really apricate you taking the time to do that. :)