Assit with tagged vs untagged VLAN TPlink switch
-
Hey all! Would love to get some help here on proper setting of VLANs. I have created all the VLANs and set the firewall and dhcp settings. Pfsense has an IP of 10.1.60.1. My TPlink swtich is plugged into the LAN port and also on 10.1.60.X. I would like to move my workstations onto VLAN 50. Pfsense is on port 1. Workstations are on port 2. I would like to still be able to acess the switch from my workstation. I am having a hard time setting the VLAN configuration on the switch. I thought I had a good handle on tagged vs untagged but I am getting something wrong. Additionally should my swtich be sitting on the same VLAN as Pfsense? Does it matter? If VLAN 60 is my management VLAN and VLAN 50 is my workstations. How should I be setting the switch tagged vs untagged so that I can commuincate to my switch from my workstation?
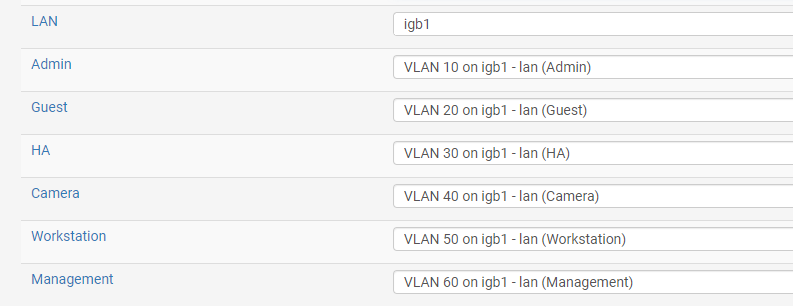
-
@imv8n what tplink?
The smaller/smart ones I doubt they allow their management to be on a tagged vlan..
So the management of tplink would be whatever IP is untagged that is plugged into igb1, on the switch this would be vlan 1.
so vlan 1 would be untagged on the tplink port, the pvid would be vlan 1.
All those other vlans 10 to 60 would be tagged on this port. And any other port you would just plug some other device in would be untagged on what vlan you want that port to be on, with the pvid being set to that vlan ID as well
-
@johnpoz TPLINK TL-SG108E
I was under the impression that using VLAN 1 was not best practice and poses some security risks. What are your thoughts on this?
-
@imv8n while yes not using vlan 1 in a corp/enterprise environment is not common practice.. There is really zero you could do about it on such a switch.. Now sure if you want to buy an enterprise grade fully managed switch - sure you could get away from the default untagged vlan 1 ;)
In a home or small business it is of little security concern..
Vlan 1 is just the default vlan of really any switch, this is untagged traffic.. Every switch be it cheap one, or a $2k enterprise switch will default to vlan 1.. And act like just a dumb switch out of the box where all ports are in this vlan and all traffic is untagged.
There really is zero security concern in a smb or home setup where you should have to worry about just using vlan 1 untagged on your switch for untagged/native network..
Most of the time this practice is just part of the security policy of a corp setup, and really to be honest has to do more with minimize mistakes where something could end up on that default vlan that shouldn't be.. You could get very close to this sort of setup by just placing your unused ports in a vlan you don't actually use for anything, and actually disable the port if possible completely when not used as well. I have that same tl108e switch, older model - and they had shit firmware on them that didn't even allow you to remove a port from vlan 1.. Hopefully your model and firmware does not have that issue - if you it is, its not really useful as an actual vlan switch. They did finally get around to fixing it, but didn't actually back port the firmware, but from threads here you can actually put v3 hardware firmware on the v2 hardware, and it now thinks is v3, and allows you to remove vlan 1 from ports it shouldn't be on.
The practice on not using vlan 1 for anything is just a way to keep mistakes from happening and stuff accidentally getting added to that vlan where management normally happens. So you normally on enterprise gear can change the management vlan to either be a different untagged vlan or even a tagged vlan, etc.. I wouldn't be concerned in a small setup or a home, etc.. I have that switch v2 model running v3 firmware
"1.0.0 Build 20171214 Rel.70905"
Which is the latest available for my older model..
I use vlan 1 on it, its not a problem.. Ports not in use are not even enabled. But sure someone could unplug something and get on vlan 1 on that switch, but its management IP is on my actual vlan 7, which is used for my rokus and such equipment. Its a pretty locked down vlan ;) then again not worried about some "hacker" breaking into my house and plugging into the switch behind my TV for the TV and shield TV device there, and oh my raspberry pi that is on vlan 3... I just have it there behind the TV because I use it as ntp server, and the wall behind my TV is next to my garage so allows for the GPS antenna to actually be in the garage and get better signal ;)
Keep in mind that vlan 1 on any switch is just the default untagged vlan - so it doesn't have to actually be your overall network default vlan, etc. In my case its on my main switches vlan 7 network.. I just untagged vlan 7 on the upstream switch its uplinked too.. Untagged vlans don't actually have to match VLAN IDs across switches.
If you don't want something to get plugged into the wrong port and be on a vlan you don't want it to be - just put all your unused ports in say vlan 99 on the switch, and don't actually use vlan 99 for anything in your network, and disable the port in the switch... So even if something were to get plugged into the wrong port, it wouldn't actually get on your network on some vlan you wouldn't want it to be on.
Without you on purpose configuring the port to be enabled and on the vlan you want that device to be on, etc.
-
@johnpoz I very much appreciated the detailed reply. I am clear on it not being that big of a deal and how to proceed. Thanks!
-
@imv8n said in Assit with tagged vs untagged VLAN TPlink switch:
TPLINK TL-SG108E
Be careful. Some TP-Link switches don't handle VLANs properly. I believe this is one, though it may have been fixed by now.