Replacing old Cisco ASA w/new Netgate trouble
-
We have a somewhat sprawling campus that is tied together with fiber to an old Cisco WS-C3750G-12S fiber switch. There are a number of VLANs across the campus, but in the fiber switch's configuration, port 12, to which the ASA is connected, is configured as such:
!
interface GigabitEthernet1/0/12
description *** Connected to 3825 Router ***
switchport mode access
!I cannot find any indication that the ASA 5512X (despite the model name in the switch configuration description line) is in the least bit recognizing or implementing VLANs on any of its ports. Likewise, the switch port configuration suggests to me that no VLAN is specifically assigned to that port.
That being said, I have duplicated the settings from the ASA as best I can in the new Netgate including the LAN IP address. On the Netgate, ethernet port 1 has been designated the WAN port as lagg0.4090 while ethernet ports 2 through 8 are lagg0.4091 and are designated as the LAN interface. With a laptop directly connected to one of the LAN ports, I am able to access the internet, however connecting the fiber switch to those ports yields no internet connection to the rest of the network.
Incidentally, I inadvertently at one point set the laptop's default gateway to the IP address of the fiber switch and was able then to ping any connected device in the network from the laptop, so it seems that traffic CAN flow over the connection if it originates on the Netgate side. I was not able to ping the laptop, or even the Netgate from the network side.
I'm not a Cisco guy - this fiber switch will be the last Cisco component in our network remaining from an old government build. It still works well and is pretty rock solid for our needs, but I feel like its the port configuration on the switch that is making things difficult.
Happy to provide further information/configuration/screenshots as necessary.
-
@glyphmon
The edge router is likely only handling internet traffic... if you have a campus design, there's a distribution stack somewhere doing the core routing... and you either have a bunch of static routes pointing back to the core or a summary route that covers everything.You'll need to review the config on the ASA and determine where those routes are pointing and duplicate them on the Netgate.
If you'd like some assistance... post a network map and the ASA config.
-
@glyphmon
My guess is that your Cisco switchport is set up for "Untagged Vlan1 access" (default native vlan).
Aka. a normal "access ethernet port" no vlan tagging, member of Vlan1 (or whatever your native vlan is set to ... Default is Vlan1)./Bingo
-
Thank you both for your help so far. After some additional troubleshooting, I've made some progress and I'm not certain that there is a configuration issue with the Cisco switch. I've attached a picture of the connections.
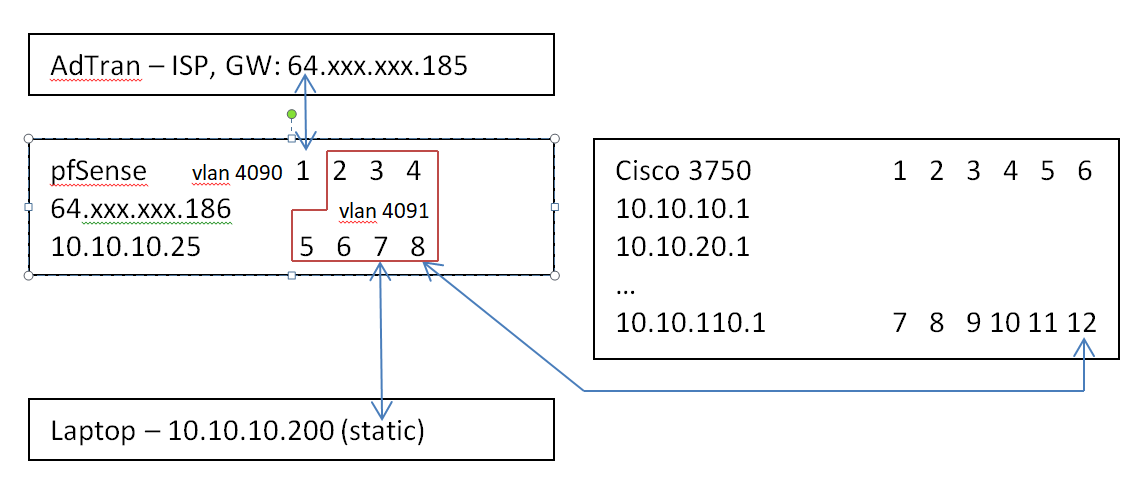
Tonight, by creating a static route for internal traffic to be routed back to the rest of the network (10.10.0.0/16 to 10.10.10.1), I was able to reach all internal hosts on the network from the laptop. I did not specify an upstream gateway. I was also able to ping the laptop from hosts on the network, as well as access file sharing between them, so I know traffic is flowing well from laptop, through the Netgate, through the Cisco switch, out through the other switches on their various subnets and VLANs, to those hosts, and back.
I was not initially able to ping the Netgate from the LAN however, but there was a setting in the Advanced configuration for the firewall to filter traffic on the same interface (i.e., LAN to LAN) which, when disabled, allowed hosts on the LAN to ping 10.10.10.25.
The laptop has perfect internet access, yet nothing on the rest of the LAN can get out. Pinging 8.8.8.8 yields no result, and a traceroute gets to the subnet's default gateway (i.e., 10.10.70.1) but does not make the next hop to 10.10.10.25.
ip route 0.0.0.0 0.0.0.0 10.10.10.25 is specified in the Cisco switch from the prior configuration with the ASA, as was an EIGRP setting, however, removing the EIGRP setting didn't change the situation.
So the fact that I can get traffic between hosts on the LAN and the laptop connected directly to the Netgate suggests to me that the VLAN configuration (or lack thereof) on both the Netgate, and the Cisco switch port 12 is not what is preventing traffic from moving.
I can provide configurations of the ASA and pfSense, but I'm not sure of the most efficient way to extract that for posting here, so if they're desired, let me know how best to do so. The output of show running-config on the Cisco switch is below with crypto and identifying information removed.
Current configuration : 9702 bytes
!
! Last configuration change at 10:28:38 EST Fri Mar 1 2019 by acadia
! NVRAM config last updated at 10:29:18 EST Fri Mar 1 2019 by acadia
!
version 12.2
service nagle
no service pad
service tcp-keepalives-in
service tcp-keepalives-out
service timestamps debug uptime
service timestamps log uptime
service password-encryption
!
boot-start-marker
boot-end-marker
!
logging buffered warnings
logging console warnings
logging monitor warnings
!
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization exec default local
!
!
!
aaa session-id common
clock timezone EST -5
clock summer-time EDT recurring
switch 1 provision ws-c3750g-12s
system mtu routing 1500
vtp domain YourNameHere
vtp mode transparent
no ip source-route
ip routing
ip domain-name alternate.local
ip dhcp excluded-address 10.10.20.1 10.10.20.50
ip dhcp excluded-address 10.10.30.34
ip dhcp excluded-address 10.10.20.200 10.10.20.254
!
ip dhcp pool AP
network 10.10.20.0 255.255.255.0
default-router 10.10.20.1
option 60 ascii "CiscoAPc1130"
option 43 hex f10c.0a0a.0a02.0a0a.0a03.0a0a.0a04
dns-server 10.10.70.5
domain-name substitute.local
option 42 ip 10.10.10.1
!
!
login on-failure log
login on-success log
!
!
!
!
!
errdisable recovery cause bpduguard
errdisable recovery interval 60
!
spanning-tree mode mst
spanning-tree extend system-id
spanning-tree vlan 1-4094 priority 4096
!
vlan internal allocation policy ascending
!
vlan 20
name AP
!
vlan 30
name FIRE_LIGHT_HVAC
!
vlan 40
name DH
!
vlan 50
name EH
!
vlan 60
name WH
!
vlan 70
name OPERATIONS
!
vlan 80
name MESH
!
vlan 90
name SC
!
vlan 100
name GUEST
!
vlan 110
name Rock
!
vlan 999
name MANAGEMENT
!
ip ssh version 2
!
!
interface GigabitEthernet1/0/1
description *** Fiber to WH ***
switchport trunk encapsulation dot1q
switchport mode trunk
speed nonegotiate
udld port disable
!
interface GigabitEthernet1/0/2
description *** Fiber to BH/DH ***
switchport trunk encapsulation dot1q
switchport mode trunk
switchport nonegotiate
udld port aggressive
!
interface GigabitEthernet1/0/3
description *** Fiber to EH ***
switchport trunk encapsulation dot1q
switchport mode trunk
switchport nonegotiate
udld port aggressive
!
interface GigabitEthernet1/0/4
description *** Fiber to MA ***
switchport trunk encapsulation dot1q
switchport mode trunk
speed nonegotiate
udld port disable
!
interface GigabitEthernet1/0/5
description *** Fiber to WT AP through DH ***
switchport trunk encapsulation dot1q
switchport trunk native vlan 20
switchport mode trunk
!
interface GigabitEthernet1/0/6
description *** Fiber to Operations through MA ***
switchport trunk encapsulation dot1q
switchport mode trunk
speed nonegotiate
udld port disable
!
interface GigabitEthernet1/0/7
description *** Fiber to GH ***
switchport trunk encapsulation dot1q
switchport mode trunk
speed nonegotiate
udld port disable
!
interface GigabitEthernet1/0/8
description *** Fiber to SC ***
switchport trunk encapsulation dot1q
switchport mode trunk
speed nonegotiate
udld port disable
!
interface GigabitEthernet1/0/9
!
interface GigabitEthernet1/0/10
description *** Connected to House Keeping ***
switchport mode access
!
interface GigabitEthernet1/0/11
description *** Uplink to ROCKSW1 ***
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet1/0/12
description *** Connected to 3825 Router ***
switchport mode access
!
interface Vlan1
ip address 10.10.10.1 255.255.255.0
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan20
description *** AP VLAN ***
ip address 10.10.20.1 255.255.255.0
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan30
description *** Fire, HVAC, and Lighting VLAN ***
ip address 10.10.30.1 255.255.255.0
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan40
description *** DH VLAN ***
ip address 10.10.40.1 255.255.255.0
ip access-group ops_lockdown in
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan50
description *** EH VLAN ***
ip address 10.10.50.1 255.255.255.0
ip access-group ops_lockdown in
ip helper-address 10.10.10.6
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan60
description *** WH VLAN ***
ip address 10.10.60.1 255.255.255.0
ip access-group ops_lockdown in
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan70
description *** Operations VLAN ***
ip address 10.10.70.1 255.255.255.0
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan80
description *** Mesh VLAN ***
ip address 10.10.80.1 255.255.255.0
ip access-group ops_lockdown in
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan90
description *** SC VLAN ***
ip address 10.10.90.1 255.255.255.0
ip access-group ops_lockdown in
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan100
description *** Guest VLAN ***
ip address 10.10.100.1 255.255.255.0
ip access-group ops_lockdown in
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan110
description *** Rock VLAN ***
ip address 10.10.110.1 255.255.255.0
ip helper-address 10.10.70.5
no ip redirects
no ip unreachables
no ip proxy-arp
!
interface Vlan999
description *** Management VLAN ***
ip address 10.10.99.1 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
!
!
router eigrp 10
network 10.10.0.0 0.0.255.255
passive-interface default
no passive-interface Vlan1
eigrp stub connected summary
!
ip classless
ip route 0.0.0.0 0.0.0.0 10.10.10.25
no ip http server
ip http secure-server
!
ip access-list extended ops_lockdown
permit tcp any host 10.10.70.5 eq domain
permit udp any host 10.10.70.5 eq domain
permit udp any host 10.10.70.5 eq bootpc
permit udp any host 10.10.70.5 eq bootps
permit ip any host 10.10.70.29
permit udp 10.10.100.0 0.0.0.255 host 10.10.100.75 eq domain
permit tcp 10.10.100.0 0.0.0.255 host 10.10.100.75 eq domain
deny ip any 10.10.30.0 0.0.0.255
deny ip any 10.10.70.0 0.0.0.255
permit ip 10.10.100.0 0.0.0.255 host 10.10.100.1
deny ip 10.10.100.0 0.0.0.255 10.0.0.0 0.255.255.255
permit ip any any
!
logging trap notifications
logging source-interface Vlan999
logging 10.200.201.17
logging 10.10.10.252
logging 10.10.70.29
!
banner motd ^CCC
********** Unauthorized Access Prohibited **********
^C
!
line con 0
exec-timeout 0 0
line vty 0 4
session-timeout 35791
logging synchronous
transport input ssh
line vty 5 15
session-timeout 35791
logging synchronous
transport input ssh
!
ntp clock-period 36029035
ntp server 129.6.15.28
end -
@glyphmon
Regarding your ASA, you should be able to grab the config with "copy run tftp:" and then attach it.... or manually cut-n-paste, but I would add code tags if you're gonna do that, so it doesn't take up so much space.Looks like the 3750 is your core L3 switch. Personally, I would reconfigure G1/0/12 as a routed port but let's see what your ASA looks like. A couple things that also need to be looked at:
-
Are all your subnets covered in your outbound NAT rules? If not, you'll need to switch to Hybrid mode and add them.
-
Are the firewall rules on the LAN interface allowing traffic from your other subnets or is it still at the default "LAN net"? If not, I would switch to an any/any rule until basic IP communication is established.
-
Verify your DHCP server(s) are handing out the respective SVI's on your 3750 as the default gateway.
-
-
@marvosa Thanks again for your help. It is now working. It was at least the firewall rules issue ("LAN net" didn't cut it), and adding rules for each subnet was the final piece. I also went through and added the individual subnets in the outbound NAT rules. Between those two changes - we have access on all subnets.