New setup with 2100: Can't ping connected Cisco switch or any of it's devices
-
Hi all, long time reader but first time poster and I'm having some big problems which I really need to figure out urgently.
I have set up a new system with the following topology (greatly simplified).
My problem:
The Cisco switch does NOT show up in the ARP table, neither does any of the devices connected to the Cisco switch. It is not pingable from the router.What I've tried
I can from my laptop, ping the Netgate router just fine through the LAN interface. It's shown in the ARP table correctly. In that table is also the 4G router and all the interfaces of the 2100, but nothing else.
The LAN interface and VLAN 1 will not be used in this system at all, only for test.My configuration
I've gone to the Assign page and defined all my VLANs in the VLAN page, assigning them to the LAN switch, as they are all internal. I then made new interfaces from those and assigned them a gateway IP and the correct subnet mask.I then went to the Switch page, Ports tab and enabled 802.1Q. I then tagged port 1 as trunk, with VLAN 666 as the PVID. As far as I understand, this PVID shouldn't be too important, but correct me if I'm wrong. Then port 1 was removed from the default list, which consisted of all five ports as VLAN 1 access port.
There was also a VLAN page under Switch, I can't recall completely what I did there, I at least tried to assign the VLAN 400 to this port.I set up LLDP and I CAN get LLDP info from the Cisco switch if I set the PVID to 1 on the 2100 switch only.
I don't know if this is some limitation of LLDP or not.From the Cisco switch, I've reviewed the settings and it seems correct. The connected port, number 24, has a trunk, the management VLAN is 400, and the management IP of the switch is set correctly. Yet I can not ping the 2100 from the Cisco switch either. Right now there are no other devices I can ping on the management VLAN because they are not yet properly set up.
I'm at a complete loss to what is going on here, and hope some network guru can come in and help out.
-
@noechoreply I'm not familiar with configuring Netgate appliances, but in general, we'd need to:
-
Validate that the VLANs are created on the correct interface
-
Verify the VLANs exist on the switch(s)
-
Verify the VLANs are allowed to traverse the trunk
-
Verify the SVI is configured and enabled
-
Verify the interfaces are enabled
-
Verify rules exist on each interface to allow the traffic
Can we see the following:
-
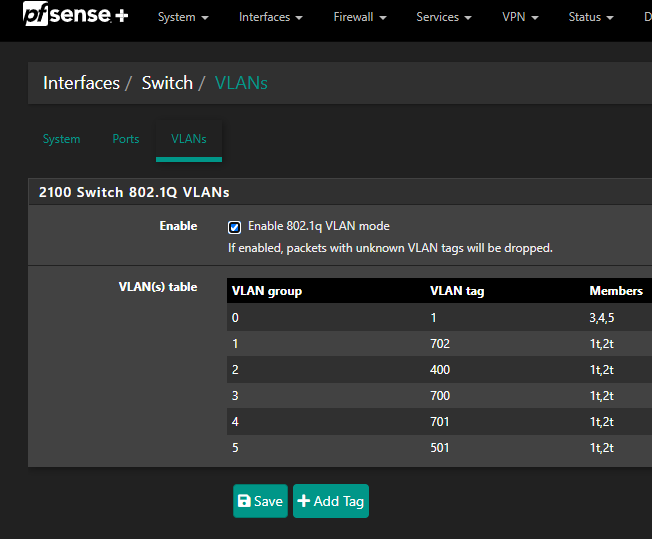
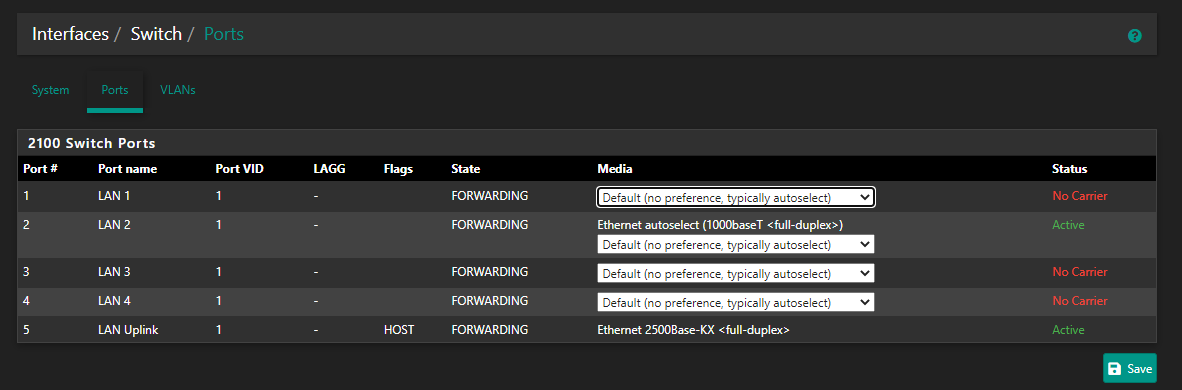
Interfaces -> Switch -> Ports
-
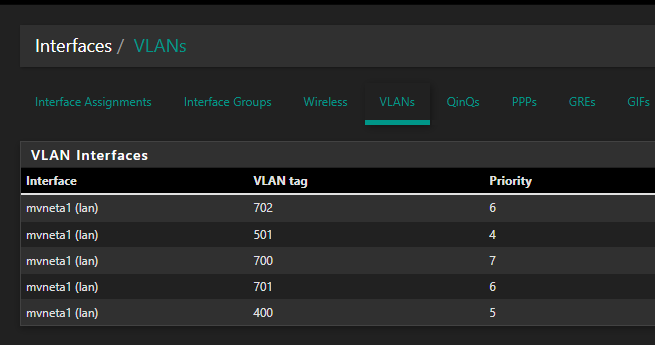
Interfaces -> Switch -> VLANs
-
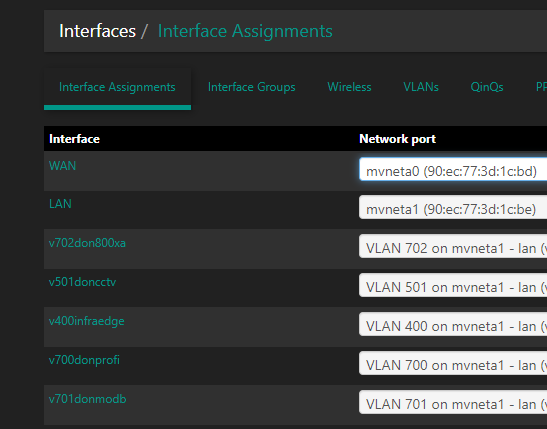
Interfaces -> Assignments -> VLANs
-
Interfaces -> Assignments
-
Config from the 9200
-
-
@marvosa hi and thank you for taking time to reply to my post.
From the Netgate 2100, I'm still waiting for access to it. But during the weekend I set up a test system using a third party router with pfsense, it did not have a built in switch though.
From there I was able to reproduce what I did on the production router, and everything went fine. I noticed that if the VLAN was not defined explicitly to be on the trunk in the connected switch (Aruba type), a similar situation would occur. And I read up that it would only show up in the ARP table if it's connected with an IP address, so if it either doesn't carry the VLAN 400 or have set the IP correctly on that, it wouldn't show up.From the Cisco I have copied some relevant settings here. I can't see anything wrong but I'm no Cisco ninja.
Define VLAN
!
vlan 400
name vlan400-infraedge
!
Configure interface on VLAN
!
interface Vlan400
ip dhcp client client-id ascii HOSTNAME
ip address 172.xx.xx.10 255.255.255.0
!ip default-gateway 172.xx.xx.1
ip forward-protocol nd
ip http server
ip http authentication local
ip http secure-server
ip http client source-interface Vlan400
ip route 0.0.0.0 0.0.0.0 192.xx.xx.1
ip ssh source-interface Vlan400
ip ssh version 2
ip scp server enable
!
!Define interface
!
interface GigabitEthernet1/0/24
description uplink
switchport mode trunk
logging event trunk-status
ip dhcp snooping trust
!sho int status:
Gi1/0/24 uplink connected trunk a-full a-1000 10/100/1000BaseTXfrom sho int:
Vlan400 is up, line protocol is up , Autostate Enabled
Hardware is Ethernet SVI, address is 88fc.5d86.6a52 (bia 88fc.5d86.6a52)
Internet address is 172.17.26.10/24
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive not supported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 19:20:24, output 00:00:01, output hang never
Last clearing of "show interface" counters never
Input queue: 0/375/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
112 packets input, 9330 bytes, 0 no buffer
Received 0 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
17 packets output, 1734 bytes, 0 underruns
Output 0 broadcasts (0 IP multicasts)
0 output errors, 2 interface resets
0 unknown protocol drops
0 output buffer failures, 0 output buffers swapped outsho int from port:
sho int Gi1/0/24 switchport
Name: Gi1/0/24
Switchport: Enabled
Administrative Mode: trunk
Operational Mode: trunk
Administrative Trunking Encapsulation: dot1q
Operational Trunking Encapsulation: dot1q
Negotiation of Trunking: On
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: disabled
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk associations: none
Administrative private-vlan trunk mappings: none
Operational private-vlan: none
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALLProtected: false
Unknown unicast blocked: disabled
Unknown multicast blocked: disabled
Vepa Enabled: false
App Interface: false
Appliance trust: none -
-
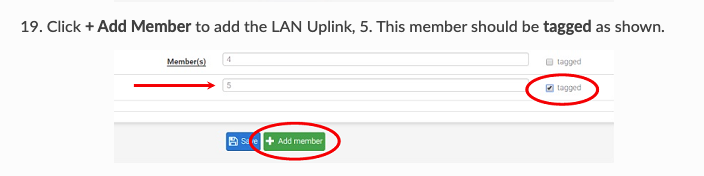
This issue is resolved thanks to the amazing Netgate support. They pointed out that I needed to put ALL VLANS to TAGGED on PORT 5. Since my lab router didn't have this switch, that's why it worked there. I do not have the definite explanation to why it's like that.
-
@noechoreply said in New setup with 2100: Can't ping connected Cisco switch or any of it's devices:
I do not have the definite explanation to why it's like that.
Stated in many threads on the forum and in the documentation:
port 5 is the IC in the 2100 and it has to be tagged for the VLANs to be seen in the pfSense side of the hardware. The switch is not directly tied to pfSense and has to be linked through, using port 5.
Step 19 here:
https://docs.netgate.com/pfsense/en/latest/solutions/netgate-2100/configuring-the-switch-ports.html