firewall default deny all with allow all statement
-
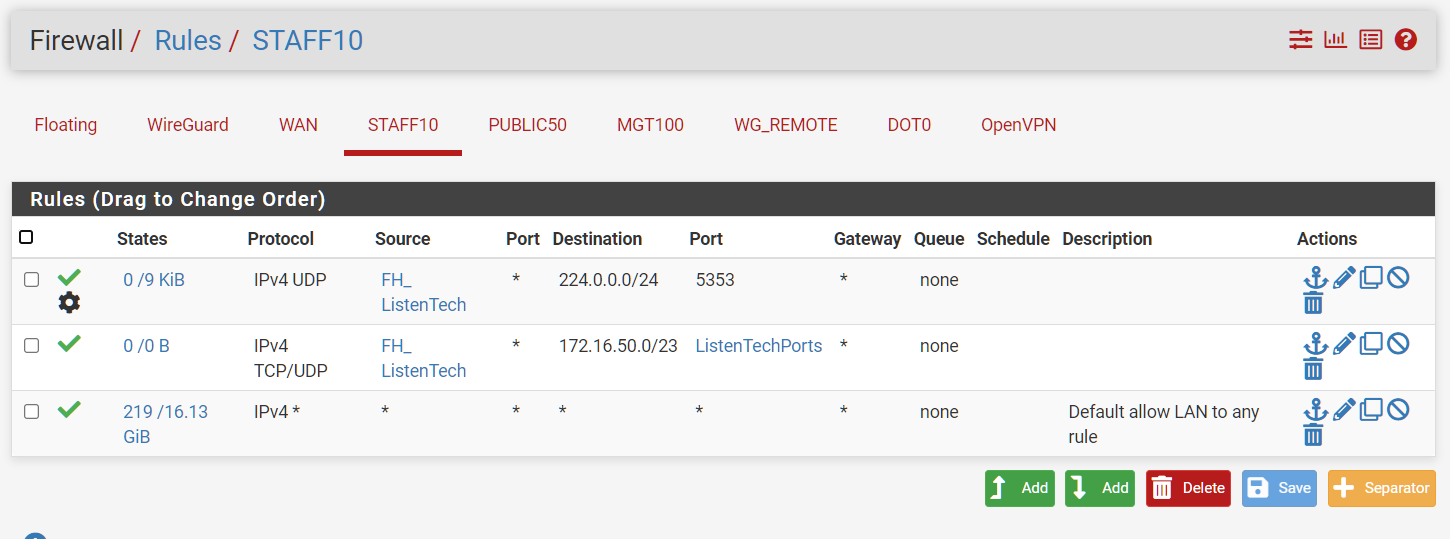
Why do I see default denies for an allow-all network?
Feels like this again [same client]
https://forum.netgate.com/topic/174989/snort2c-host-block?_=1682465358279All my other pfSense installs which are much more complicated [even running virtualized] are rock solid. But this client [with two different hardware platforms] seems to always trigger something. Gah.
Literally nothing on this install except wireguard.
-
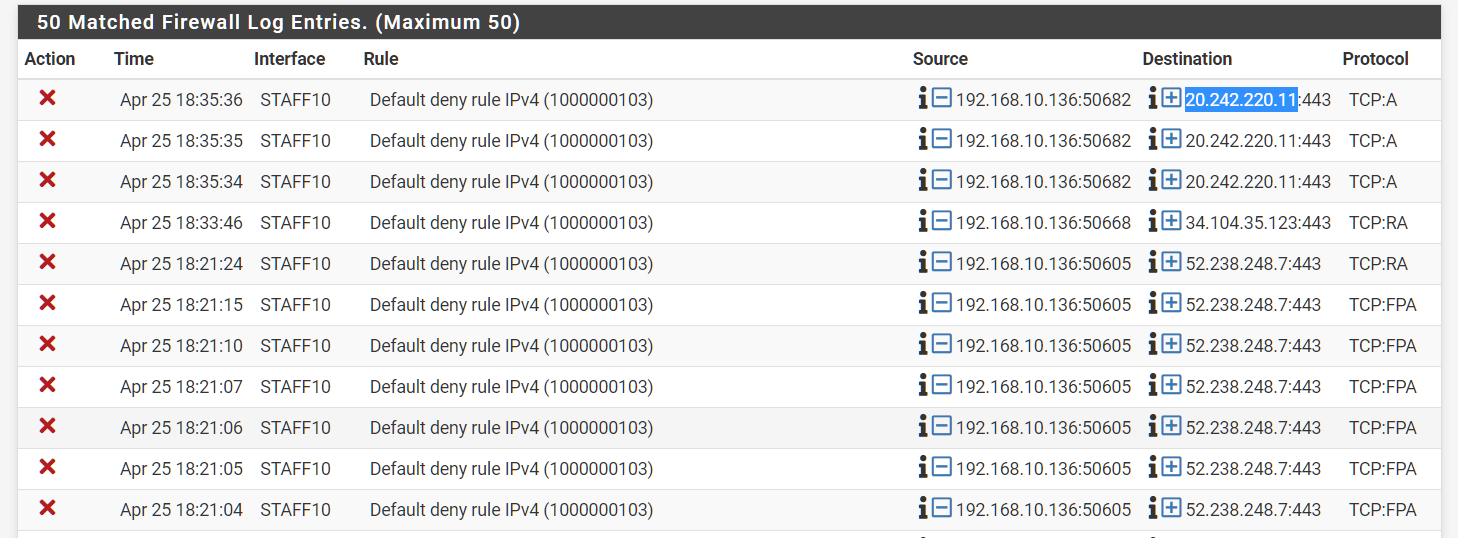
@lightingman117 those are just all out of state blocks...
-
-
How did y'all tell from the images alone?
I looked at the TCP flags and didn't think anything of them.
In other news - I found out the real problem.
Mikrotik CRS354-48G-4S+2Q+RM needed to be restarted (after a lightning strike).
[certain ports] Network was super slow/unresponsive.
PING worked
DHCP workedBut HTTP(S) traffic did not.
SMB did not.WiFi worked fine.
Other computers worked fine.Very weird issue (IMO).
-
@lightingman117 said in firewall default deny all with allow all statement:
TCP flags and didn't think anything of them.
Well you need to ;)
Anything other than S (syn) that is blocked would mean that pfsense does not have a state to why its blocked. If it was a SYN block - that points to pfsense not having a rule to allow whatever the traffic is.
Seeing out of state blocks like FA, or R with some other flags possible like E in there or P etc.. Its normal to see these now an then.. If your seeing SA (syn,ack) this would point to asymmetrical traffic flow.. But now and then seeing some out of state F or FA, etc. is common to see now and then.. Devices trying to reuse a old session, phones are horrible about this - or maybe they are retrans and pfsense already closed the state, etc.
-
@lightingman117 FWIW we disable logging of packets blocked by the default rules. It eliminates a lot of log noise, and we can always turn it on if necessary while debugging.
-
@lightingman117 same here.. default deny logging disabled on mine. I have no desire to see out of state blocks. Or any sort of nonsense noise on my wan either.
I log blocks that might interest me, on the wan this is only SYN traffic, and some common and interesting UDP ports. And some other things that interest me that might be trying to talk to my IP. But if some random packet hits my IP that is not a syn, and would never be allowed anyway - I don't really have a desire to see it in my logs, it just fills them up making it harder to see the interesting stuff.
On my lan side interfaces I have blocks that log for stuff that would be of interest to me if devices on those networks tried to go there or on specific ports, that sort of thing.
And as mentioned by @SteveITS you can always trigger the default log back on if your actually trying to troubleshoot something that is not working, or whenever else you might want to take a peek.