echo: write error on stdout
-
Hi everyone, I'm having a problem validating the SSL certificate on the Let's Encrypt production server with the pfSense Acme client using "Standalone http server". However, I have the same settings in the certificate that I test on the Let's Encrypt test server and it does work great.
The output of testSSL Renew is this and it is correct.
testSSL
Renewing certificate
account: test
server: letsencrypt-staging-2/usr/local/pkg/acme/acme.sh --issue --domain 'www.nidaval.com' --standalone --listen-v4 --httpport '8080' --domain 'nidaval.com' --standalone --listen-v4 --httpport '8080' --home '/tmp/acme/testSSL/' --accountconf '/tmp/acme/testSSL/accountconf.conf' --force --reloadCmd '/tmp/acme/testSSL/reloadcmd.sh' --log-level 3 --log '/tmp/acme/testSSL/acme_issuecert.log'
Array
(
[path] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/
[PATH] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/
[port] => 8080
[ipv6] =>
)
[Wed May 10 00:47:11 CEST 2023] Using CA: https://acme-staging-v02.api.letsencrypt.org/directory
[Wed May 10 00:47:11 CEST 2023] Standalone mode.
[Wed May 10 00:47:11 CEST 2023] Standalone mode.
[Wed May 10 00:47:11 CEST 2023] Multi domain='DNS:www.nidaval.com,DNS:nidaval.com'
[Wed May 10 00:47:11 CEST 2023] Getting domain auth token for each domain
[Wed May 10 00:47:14 CEST 2023] Getting webroot for domain='www.nidaval.com'
[Wed May 10 00:47:14 CEST 2023] Getting webroot for domain='nidaval.com'
[Wed May 10 00:47:14 CEST 2023] www.nidaval.com is already verified, skip http-01.
[Wed May 10 00:47:14 CEST 2023] nidaval.com is already verified, skip http-01.
[Wed May 10 00:47:14 CEST 2023] Verify finished, start to sign.
[Wed May 10 00:47:14 CEST 2023] Lets finalize the order.
[Wed May 10 00:47:14 CEST 2023] Le_OrderFinalize='https://acme-staging-v02.api.letsencrypt.org/acme/finalize/100777814/8665388574'
[Wed May 10 00:47:16 CEST 2023] Order status is processing, lets sleep and retry.
[Wed May 10 00:47:16 CEST 2023] Retry after: 3
[Wed May 10 00:47:19 CEST 2023] Polling order status: https://acme-staging-v02.api.letsencrypt.org/acme/order/100777814/8665388574
[Wed May 10 00:47:19 CEST 2023] Downloading cert.
[Wed May 10 00:47:19 CEST 2023] Le_LinkCert='https://acme-staging-v02.api.letsencrypt.org/acme/cert/faef45479be9ef7a676a86d4dfbc85e973a5'
[Wed May 10 00:47:20 CEST 2023] Cert success.
-----BEGIN CERTIFICATE-----
MIIFYDCCBEigAwIBAgITAPrvRUeb6e96Z2qG1N+8helzpTANBgkqhkiG9w0BAQsF
ADBZMQswCQYDVQQGEwJVUzEgMB4GA1UEChMXKFNUQUdJTkcpIExldCdzIEVuY3J5
cHQxKDAmBgNVBAMTHyhTVEFHSU5HKSBBcnRpZmljaWFsIEFwcmljb3QgUjMwHhcN
MjMwNTA5MjE0NzI0WhcNMjMwODA3MjE0NzIzWjAaMRgwFgYDVQQDEw93d3cubmlk
YXZhbC5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDsm6ryArmz
ygkYnIBcYFwwBDTtRYYb/EPhRJwdT8VLve5+85MlIWCgQO3rHiRrUuDafjsOghJv
S6bEAsccV/zRltXyLuvP+pT2H6AhQcr/2pQs3wsS974qFi7BcFIJx5n9BL+lFl4A
8vnXTF/592UMp3zWIJC9t6gxxSbRIDPYnclpwyTC/1raGTfi1bQtAAXecYf9I2MB
PITkFHwtfJYmtGWLWmQXis1BPCE37qpKNIWP3QFY44RO4Rekn6bFxHibrKA2kreo
RHaOSmVd6DAICZzlN6OsWGE5mMnSw4GZLJ8G3IU2SPYGZ2XNO6PUJisOiUCkTWBp
idPHTC1w+m4PAgMBAAGjggJeMIICWjAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0lBBYw
FAYIKwYBBQUHAwEGCCsGAQUFBwMCMAwGA1UdEwEB/wQCMAAwHQYDVR0OBBYEFLvK
UPh8/s90zziDdPnmK2i6ul+/MB8GA1UdIwQYMBaAFN5yekjfMcOmUN+fhSPfVzdL
XS5lMF0GCCsGAQUFBwEBBFEwTzAlBggrBgEFBQcwAYYZaHR0cDovL3N0Zy1yMy5v
LmxlbmNyLm9yZzAmBggrBgEFBQcwAoYaaHR0cDovL3N0Zy1yMy5pLmxlbmNyLm9y
Zy8wJwYDVR0RBCAwHoILbmlkYXZhbC5jb22CD3d3dy5uaWRhdmFsLmNvbTBMBgNV
HSAERTBDMAgGBmeBDAECATA3BgsrBgEEAYLfEwEBATAoMCYGCCsGAQUFBwIBFhpo
dHRwOi8vY3BzLmxldHNlbmNyeXB0Lm9yZzCCAQMGCisGAQQB1nkCBAIEgfQEgfEA
7wB1AO2rnR3dg3OVn/UqiORrtLzDxMxNdopgzP9ONi1/uNZoAAABiAKyrZ0AAAQD
AEYwRAIgEqhvD+4yINQfOrT0WgkMEqG1hpIrkraMz17zG+QlfeMCIAw9dQTmvlDu
3205xJ11YA5FYdU9xNfq223pOzTy5nkkAHYAsMyD5aX5fWuvfAnMKEkEhyrH6IsT
LGNQt8b9JuFsbHcAAAGIArKtkwAABAMARzBFAiEA9TcKMJd1+/mNtfGZJs++EfAw
nJ1DVTZnoIJRwOyUK6QCIESxYTGFh/pHNFMY4t3FdsCYItk2lNQLAXVaKGxaMAIu
MA0GCSqGSIb3DQEBCwUAA4IBAQCwxJJnL1EaDPwTsBG22xSrxKia7zXdvYXEyHDO
cmGbbaNrHnZEyAXIVZ6ybeYhaOCPRVC41RK1IMEsP3FRWueQp+7KW003JHR2BZOx
m/7yu3qu6GvXbtyhjl+w7Bpq+NACFiuB1qv+nRubUZmjfiSXX4Uu9nwZ8rN6Dhaf
B2gygP3phQA3pAyRM6horNRngp8+QZpNFjfZc6VzyrHhPXkzESINDwP0jzxiIibh
V3PKr+Z4ZAxlkLE6bGQMeMgf2vLn2Ls5xjHdtpCmPz3TzvmLB2ghPT2Eyt95k72X
m8oCu6xB/UyTuftj/LQCWSPXWxTatZqgXUrNZEa3Zj3bXc2Q
-----END CERTIFICATE-----
[Wed May 10 00:47:20 CEST 2023] Your cert is in: /tmp/acme/testSSL//www.nidaval.com/www.nidaval.com.cer
[Wed May 10 00:47:20 CEST 2023] Your cert key is in: /tmp/acme/testSSL//www.nidaval.com/www.nidaval.com.key
[Wed May 10 00:47:20 CEST 2023] The intermediate CA cert is in: /tmp/acme/testSSL//www.nidaval.com/ca.cer
[Wed May 10 00:47:20 CEST 2023] And the full chain certs is there: /tmp/acme/testSSL//www.nidaval.com/fullchain.cer
[Wed May 10 00:47:20 CEST 2023] Run reload cmd: /tmp/acme/testSSL/reloadcmd.shIMPORT CERT testSSL, /tmp/acme/testSSL/www.nidaval.com/www.nidaval.com.key, /tmp/acme/testSSL/www.nidaval.com/www.nidaval.com.cer
update cert![Wed May 10 00:47:21 CEST 2023] Reload successThe output of NidavalSSL Renew is this and it is not correct.
NidavalSSL
Renewing certificate
account: Produccion
server: letsencrypt-production-2/usr/local/pkg/acme/acme.sh --issue --domain 'www.nidaval.com' --standalone --listen-v4 --httpport '8080' --domain 'nidaval.com' --standalone --listen-v4 --httpport '8080' --home '/tmp/acme/NidavalSSL/' --accountconf '/tmp/acme/NidavalSSL/accountconf.conf' --force --reloadCmd '/tmp/acme/NidavalSSL/reloadcmd.sh' --log-level 3 --log '/tmp/acme/NidavalSSL/acme_issuecert.log'
Array
(
[path] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/
[PATH] => /etc:/bin:/sbin:/usr/bin:/usr/sbin:/usr/local/bin/
[port] => 8080
[ipv6] =>
)
[Wed May 10 12:14:47 CEST 2023] Using CA: https://acme-v02.api.letsencrypt.org/directory
[Wed May 10 12:14:47 CEST 2023] Standalone mode.
[Wed May 10 12:14:47 CEST 2023] Standalone mode.
[Wed May 10 12:14:48 CEST 2023] Multi domain='DNS:www.nidaval.com,DNS:nidaval.com'
[Wed May 10 12:14:48 CEST 2023] Getting domain auth token for each domain
[Wed May 10 12:14:54 CEST 2023] Getting webroot for domain='www.nidaval.com'
[Wed May 10 12:14:54 CEST 2023] Getting webroot for domain='nidaval.com'
[Wed May 10 12:14:54 CEST 2023] Verifying: www.nidaval.com
[Wed May 10 12:14:54 CEST 2023] Standalone mode server
[Wed May 10 12:15:00 CEST 2023] Pending, The CA is processing your order, please just wait. (1/30)
2023/05/10 12:14:56 socat[27152] E write(6, 0x800add000, 20): Broken pipe
echo: write error on stdout
printf: write error on stdout
2023/05/10 12:14:58 socat[37713] E write(6, 0x800add000, 17): Broken pipe
echo: write error on stdout
echo: write error on stdout
printf: write error on stdout
2023/05/10 12:15:00 socat[38507] E write(6, 0x800add000, 17): Broken pipe
echo: write error on stdout
echo: write error on stdout
printf: write error on stdout
2023/05/10 12:15:02 socat[49811] E write(6, 0x800add000, 17): Broken pipe
echo: write error on stdout
echo: write error on stdout
printf: write error on stdout
2023/05/10 12:15:04 socat[59603] E write(6, 0x800add000, 17): Broken pipe
echo: write error on stdout
echo: write error on stdout
printf: write error on stdout
2023/05/10 12:15:06 socat[60651] E write(6, 0x800add000, 17): Broken pipe
echo: write error on stdout
echo: write error on stdout
printf: write error on stdout
[Wed May 10 12:15:07 CEST 2023] www.nidaval.com:Verify error:88.26.16.154: Invalid response from http://www.nidaval.com/.well-known/acme-challenge/JgQLrsY3qPf292dqb4Zbsf9r1qj6e69JAnJiZ6NMZuk: 503
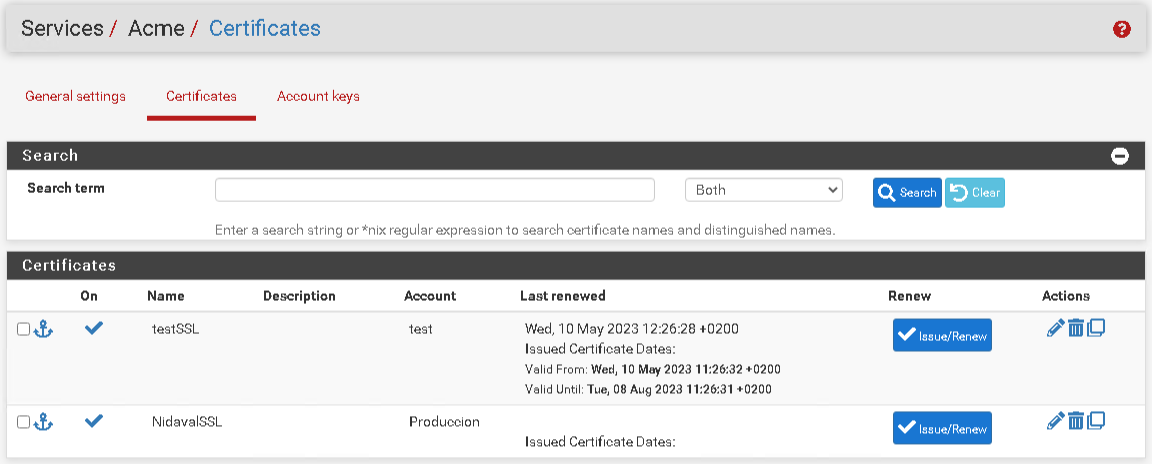
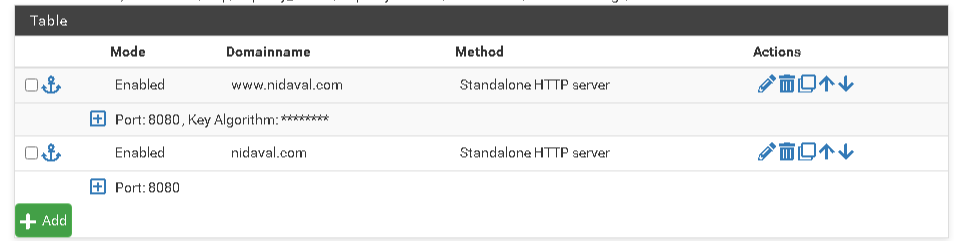
[Wed May 10 12:15:07 CEST 2023] Please check log file for more details: /tmp/acme/NidavalSSL/acme_issuecert.logYou have the configuration of both certificates in the image ...
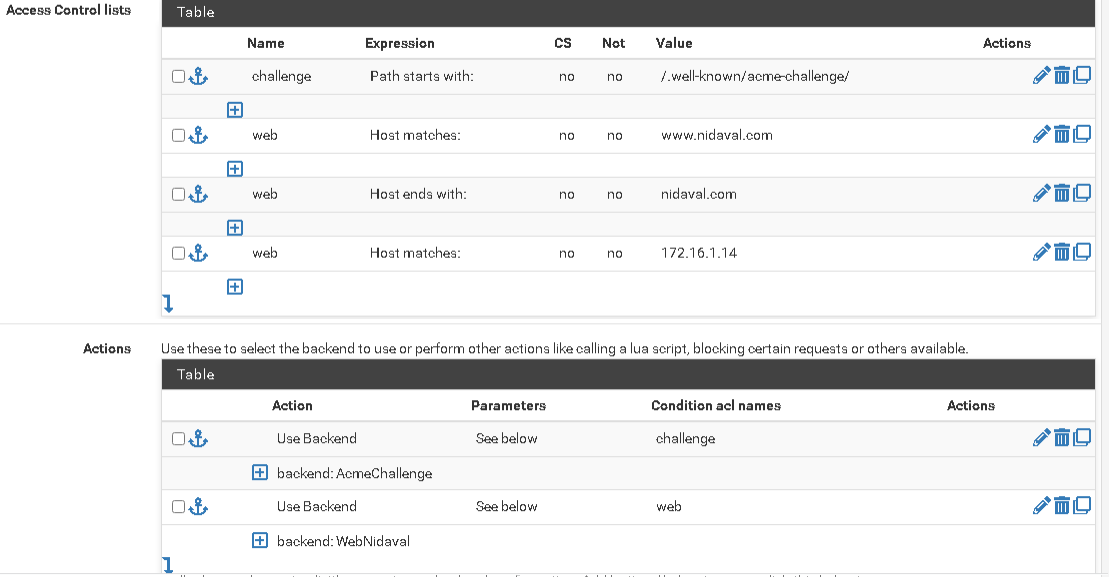
... and you have the HAProxy frontend configuration in the image.
The versions on my system are:
pfSense v2.6.0
acme v0.7.3- pecl-ssh2 v1.3.1
- socat 1.7.4.2
- php74 v7.4.26
HAProxy v0.61_7
Could you help me?
-
Did you ever get this sorted? I have a similar issue.