Access from PFSense itself is being blocked by Suricata.
-
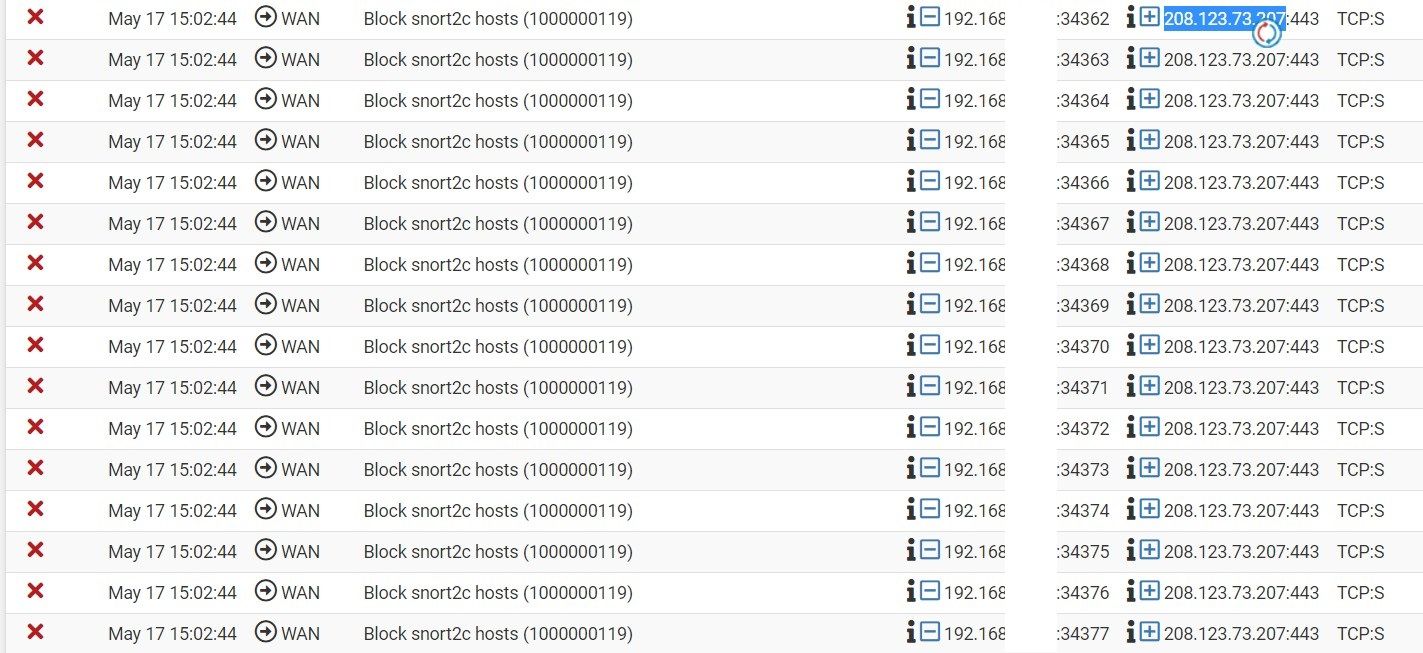
Recently, there have been block logs for access from PFSense itself to destinations such as 208.123.73.207:443. PFSense is connected to only one PC, and I haven't installed any packages that would allow PFSense itself to access other servers... Could you at least determine if the blocked IP addresses are related to suspicious server access?
-
https://208.123.73.207 = files.pfsense.org
-
@dobby_ Thank you for your response. It was indeed the IP address of PFSense, which I overlooked... I thought Suricata wouldn't block it, but it turns out it does unexpectedly. I've learned something from this.
-
@yet_learningpfsense That usually happens when you enabled too much/many rules or implement blocking before your IPS/IDS had a chance to learn what's good from bad.
-
@yet_learningpfsense Also if you’re running Suricata on WAN I’d recommend putting it on LAN. Otherwise it scans outside the firewall so scans all inbound to-be-blocked packets and can only see the NATted IP not LAN devices.