Split Tunnel Traffic Failing for Web Traffic
-
OpenVPN connects but I can't figure out where to resolve the DNS issue I'm having when connecting using split tunnel.
I see this in the log:
Mon May 22 14:53:04 2023 Blocking outside dns using service succeeded.
I can't find where to allow outside dns..
Thanks,
Joe
-
@technolust
Block Outside DNS is an option in the OpenVPN server settings. As far as I know, this is not enabled by default.Did you also check DNS Server enable or Redirect IPvx Gateway?
If sou you need to provide a DNS server to the clients and allow the access to it. -
@viragomann worth noting I believe that setting only applies to Windows.
-
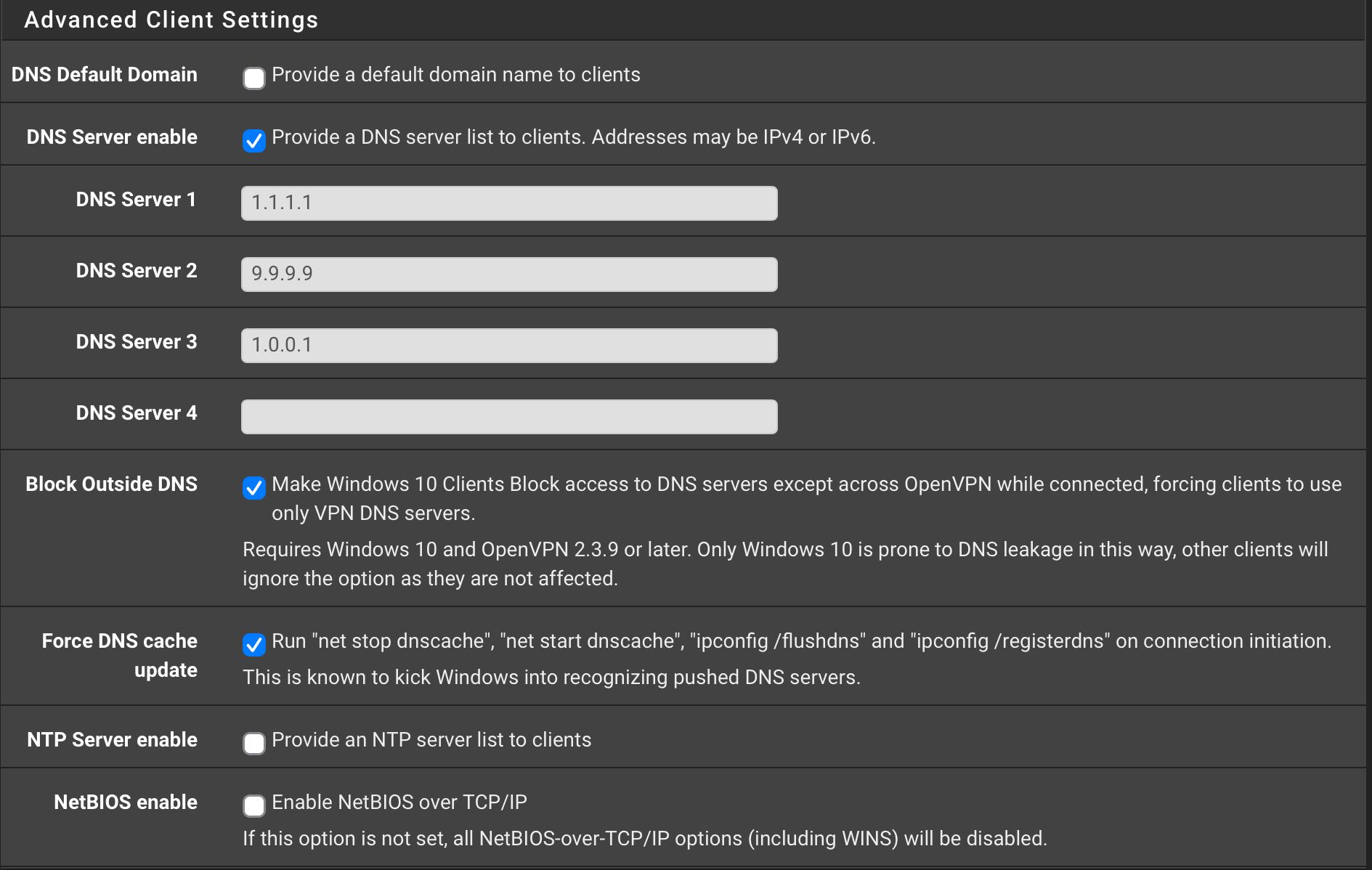
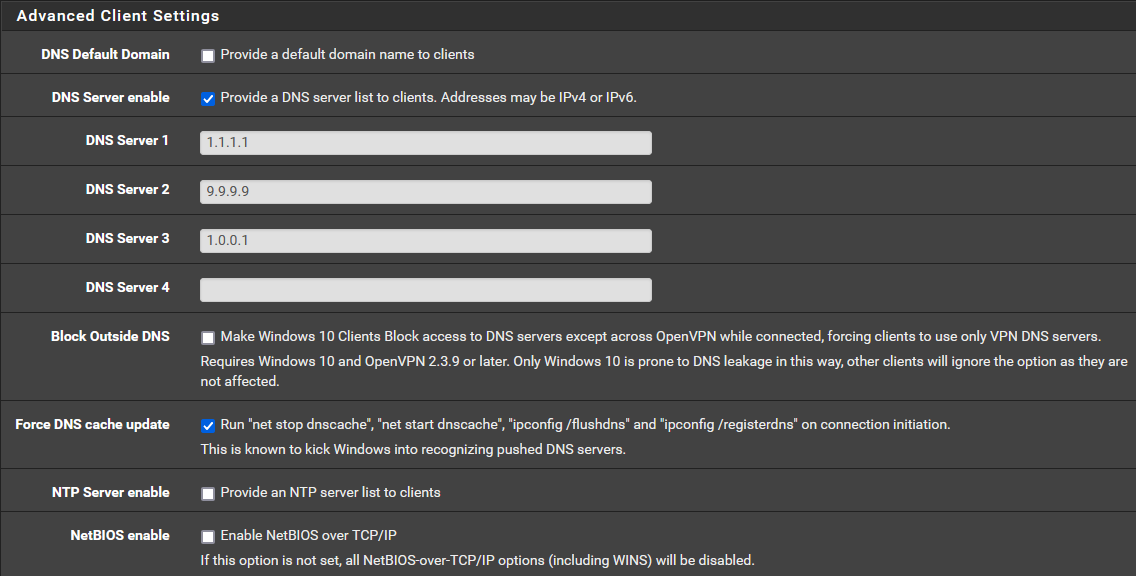
Here are the settings for the DNS, I’m running Windows 11. Will uncheck Block Outside DNS and Uncheck Force DNS cache update. Last time I tried this had no effect on Windows 11 but you know Microsoft and their infinite wisdom…
-
@technolust said in Split Tunnel Traffic Failing for Web Traffic:
Here are the settings for the DNS, I’m running Windows 11.
See in your image this:
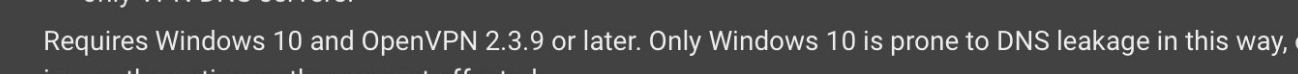
Windows 11 will not work for this.
-
@rcoleman-netgate I knew that but had to leave the house to test. I just made the change and the result is the same. However, if I setup a full tunnel by adding the below to the vpn file I get traffic web traffic without any issues.
redirect-gateway def1
If I remove the redirect-gateway def1 and setup the split tunnel I lose the web traffic again.
Also note, I'm testing on Win11 22H2 I haven't tested Linux yet.. iPhone and Android devices work just fine. Damn Microsoft killing me again!!! -
@technolust said in Split Tunnel Traffic Failing for Web Traffic:
If I remove the redirect-gateway def1 and setup the split tunnel I lose the web traffic again.
Is it due to name resolution not working?
If so, try to provide your pfSense IP as DNS server if you're running unbound on it and remove the public DNS servers. Ensure that access is allowed. Possibly you have to add the VPN tunnel to the Resolver ACLs.If you provide public DNS servers without 'redirect gateway' you would also route them over the VPN by adding them to the "Local Networks".
-
@viragomann It could be due to the name resolution not working but I'm not 100% sure. I thought of this as well. When I go to Cloudflare (1.1.1.1) website shows up.
I renamed the vpn file with redirect-gateway def1 to the original. Checked the box and the issue happens... 1.1.1.1 comes up but dns not working... Then I brought back the redirect vpn file and unchecked the box and it works... Then I reverted the vpn file back to redirect-gateway and left the box unchecked and it works. Almost as if there is a caching issue with the vpn file...
try to provide your pfSense IP as DNS serverI have a pi-hole setup as DNS server.Should I try that IP?
Conf File:
dev tun persist-tun persist-key data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC data-ciphers-fallback AES-256-CBC auth SHA256 tls-client client resolv-retry infinite remote xxx.xxx.xxx.xxx 1194 udp4 nobind verify-x509-name "pffw-cer" name auth-user-pass pkcs12 fw-UDP4-1194.p12 tls-crypt fw-UDP4-1194-tls.key remote-cert-tls server explicit-exit-notifyIf I remove nobind and append "redirect-gateway def1" to the end of the file (full tunnel) it works. This is the only difference between the two files.
Possibly you have to add the VPN tunnel to the Resolver ACLsThis part I don't recall how to do...If you provide public DNS servers without 'redirect gateway' you would also route them over the VPN by adding them to the "Local Networks".Do I need to do this under IPv4 Local network(s) in the Tunnel Settings? -
@technolust said in Split Tunnel Traffic Failing for Web Traffic:
It could be due to the name resolution not working but I'm not 100% sure.
Do an nslookup to get sure. Or even a ping to google.com or whatever.
I renamed the vpn file with redirect-gateway def1 to the original. Checked the box and the issue happens... 1.1.1.1 comes up but dns not working... Then I brought back the redirect vpn file and unchecked the box and it works
Normally this is pushed to clients by the server and hence doesn't need to be set on the client, however, it's possible.
You can enhance the clients log level to see, what configuration changes the client does in the OS with the line:
verb 3try to provide your pfSense IP as DNS server I have a pi-hole setup as DNS server.
Should I try that IP?Yes.
Possibly you have to add the VPN tunnel to the Resolver ACLs This part I don't recall how to do...
This is lapsed, since the Resolver is not the DNS server.
Maybe you have to configure it on the Pi-hole properly.If you provide public DNS servers without 'redirect gateway' you would also route them over the VPN by adding them to the "Local Networks". Do I need to do this under IPv4 Local network(s) in the Tunnel Settings?
Yes, IPv4 addresses have to be added to the "Local IPv4 Networks", IPv6 to the respective other one.
Note to use CIDR notation, e.g. for Cloudflare "1.1.1.1/32".