Update DNS on every VPN connection
-
I have an ALLOW rule based on FQDN Aliases for our dyndns addresses
https://192.168.8.1/firewall_aliases_edit.php?id=0Works fine.
But sometimes the pfsense DNS is not up to date with the remote hostname IP. They have to wait for the DNS to update or someting.
So when a user connects to open VPN and his IP is not right, they are not allowed through as per our Alias rules
I would like to trigger a DNS update to certain DNS server (the dyndns servers) for our hostnames everytime an openvpn connection is started.
Is this possible?
Thanks!
-
@Wastapi said in Update DNS on every VPN connection:
They have to wait for the DNS to update or someting.
How long?
What is the TTL of the host name?
Basically you should set a short TTL like 60 - 120 seconds, so that you only have a short gap.A good advice is also to let the IP renewing be done in the night hours if possible.
-
@viragomann Thanks for your reply.
The DNS is on dyndns.org. No control over the TTL.
Also, the employee IPs are dynamic... So we never know when they change.
Also the employees could be on the road and have an IP from their cell phone, which change quite often. It is updated in dyndns DNS quite fast by the DNS update on the employee computer.But the pfsense DNS is slow to resolve to those host names.
My ideal would be that the Open VPN process resolve the a few hostnames upon new connection request. this would make it work all the time.Any clue how to hook to the Open VPN process to trigger a DNS update?
Thank you
-
@Wastapi It is done every 5 minutes, if this ain't enough, lower the value...
-
@Bob-Dig
Where is it defined to be 5 minutes? URL please -
@Wastapi said in Update DNS on every VPN connection:
Any clue how to hook to the Open VPN process to trigger a DNS update?
Probably not needed.
At the begin, there is the gateway monitor action :
System > Routing > Gateways and edit any gateway to see if "Gateway Action" is checked.
The check is : every xx msec a ping is send to the upstream gateway.
If pings stop to come back, the gateway is reset => the interface is recent.
When reset, many things happen.
One of the action is : all the "Dynamic DNS" are run. That is : the stored (previous) IP is compared with Services > Dynamic DNS > Check IP Services http://http://checkip.dyndns.org/ and if different, an IP change is presumed and the DNS dynamic update kicks in.During all this, your OpenVPN won't work, because the uplink WAN was changing it's IP, so even if you had an IP - and not a host name, it wouldn't work anyway, as the IP is now not valid any more - points to some one else.
This "if WAN IP changed, then dyndns update it" will be done rather quickly - 10 or less seconds ? Typically less.Something you can't change on your side : DNS master to slave syncing time. If "dyndns.org" takes xxx seconds to do so, then that is the time you have to wait.
If you need faster : that's possible.
Example : get a domain name, your own.
Set up your own 'master' DNS, by using bind (named) - activate the dyndns, that is : RFC 2136.
Now, you control nearly everything.
Because DNS rules tell you that you have to have 2 name servers (not less), this boils down to : what I use : one "big iron", my main dedicated server with all the sites, mails, DNS, etc etc, and one small VPS 'else where' that plays the salve DNS server.My home.my-domaine.tld now points to my WAN IP.
If it changes .... the WAN will go down and up : the new IP will get updated in seconds, the host name "home.my-domaine.tld" will be updated a couple of seconds later.So : no need to do dyndns stuff when a OpenVPN user connects.
dyndns stuff happens when the WAN interface comes up.
The WAN interface will go down-up if a new connection has to be initiated.Something as "the ISP just assigns you a new IPv4 without letting you know it" scheme does not exist.
It's more a pppoe that times out, the client - pfSense, renews the connection, and this will trigger a dyndns event.
The DHCP pfsense client renews the lease. If it can't, it will discover a new lease, and in any case : dyndns will get triggered.
Etc.Btw : there is a force dyndns run every ... day ? :
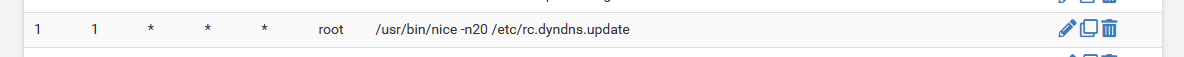
It will just compare the current WAN IP with what http://checkip.dyndns.org/ tells it.
Something would be really bad if this test actually changed the host name. -
Thank you for your reply, but I may have been misunderstood.
The problem is not the Host WAN not being update. The issue is the host not resolving the employees dyndns to the right IP.
When you run rc.dyndns.org, you're telling dyndns to update your hostname with your current IP.
What I want is for the host to update it's local DNS cache so it has all the employees hostname resolving to the correct IP as per DynDNS DNS.
I am really talking about this
https://192.168.8.1/firewall_aliases_edit.php?id=0 -
@Wastapi said in Update DNS on every VPN connection:
@Bob-Dig
Where is it defined to be 5 minutes? URL pleaseIt is called "Aliases Hostnames Resolve Interval", you find it in System - Advanced - Firewall & NAT.