Interface rules - best practices for IoT network(s)?
-
@onthebeach If your Wireless is handing out a network that isn't the pfSense one then you're doing multiple layers of routing... Look into AP mode for the Nighthawk
-
@rcoleman-netgate - Thanks for the feedback. Unfortunately, trying to change to AP mode was the first thing I did. Still lost all WiFi …. |-left aligned paragraph
-
@onthebeach Remove the wireless, plug directly into the port.
Does it work? If so it's not pfSense that's the issue but your AP in Router Mode.
-
@rcoleman-netgate - I went ahead and disabled the (prevent incoming traffic) to loop back/reserve IP addresses in the initial setup, and it now allows all of the IOT devices to work.
-
@onthebeach - the question now is, how do I prevent traffic from “reserved addresses” from coming into my network?
-
@onthebeach I'm moving this to Firewall and changing your title.
-
R rcoleman-netgate moved this topic from Problems Installing or Upgrading pfSense Software on
-
@onthebeach said in Interface rules - best practices for IoT network(s)?:
from “reserved addresses” from coming into my network?
Huh?? The block rfc1918 rule is on the WAN of pfsense - why would you connect your AP to pfsense wan?
If your wanting your iot segment not to talk to your other segments.. Something like this would be a locked down network segment
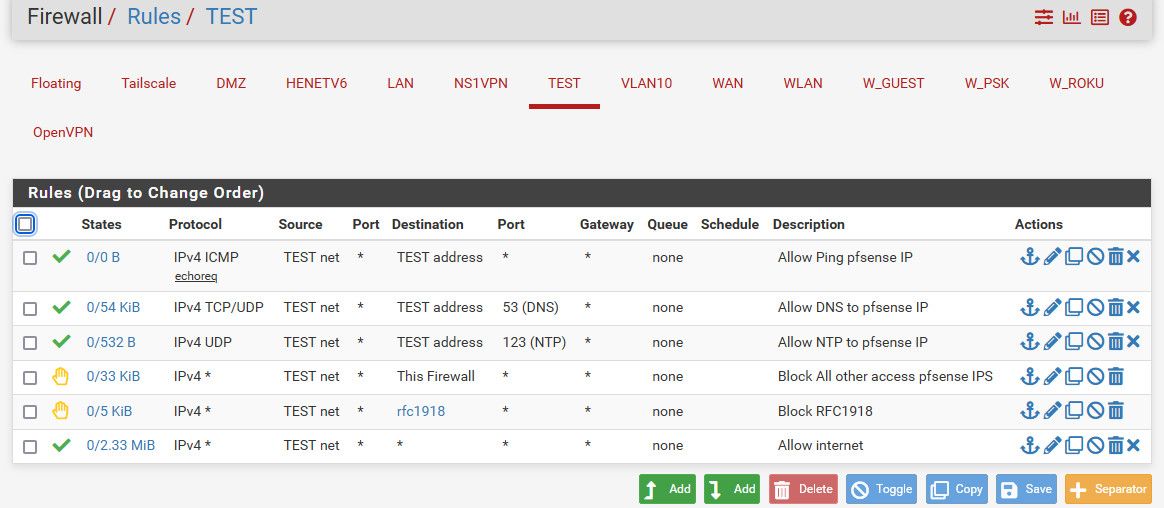
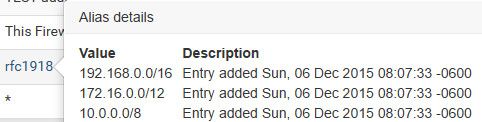
Where the rfc1918 is an alias you create that contains the rfc1918 networks
You allow what you want to pfsense address on that network segment, then block it from going to anything on the firewall, I doubt you want your iot stuff able to reach the gui for example. And then the block to any other rfc1918 which assume your other network segments are using. And then let it out to anything else - ie the internet.
-
@johnpoz - Not sure why this needed to be moved anywhere, this, for me, this has been an installation issue and not a firewall issue (I never got that far). It happened as I started the process and never got to the firewall section. During the setup, pfsense automatically blocks any/all incoming traffic to the WAN that appears as if it’s coming from a reserved ip space. When I deselected this feature, my wireless IOT devices worked without any issues. Nothing was EVER added to the WAN.
-
@onthebeach said in Interface rules - best practices for IoT network(s)?:
a reserved ip space. When I deselected this feature, my wireless IOT devices worked without any issues.
Not sure what you think that did - but it sure didn't fix your issue if you were connecting your AP to your lan network.. That rule blocks unsolicited inbound traffic to your wan that comes from a source IP of rfc1918..
A typical single segment network would be something like this..
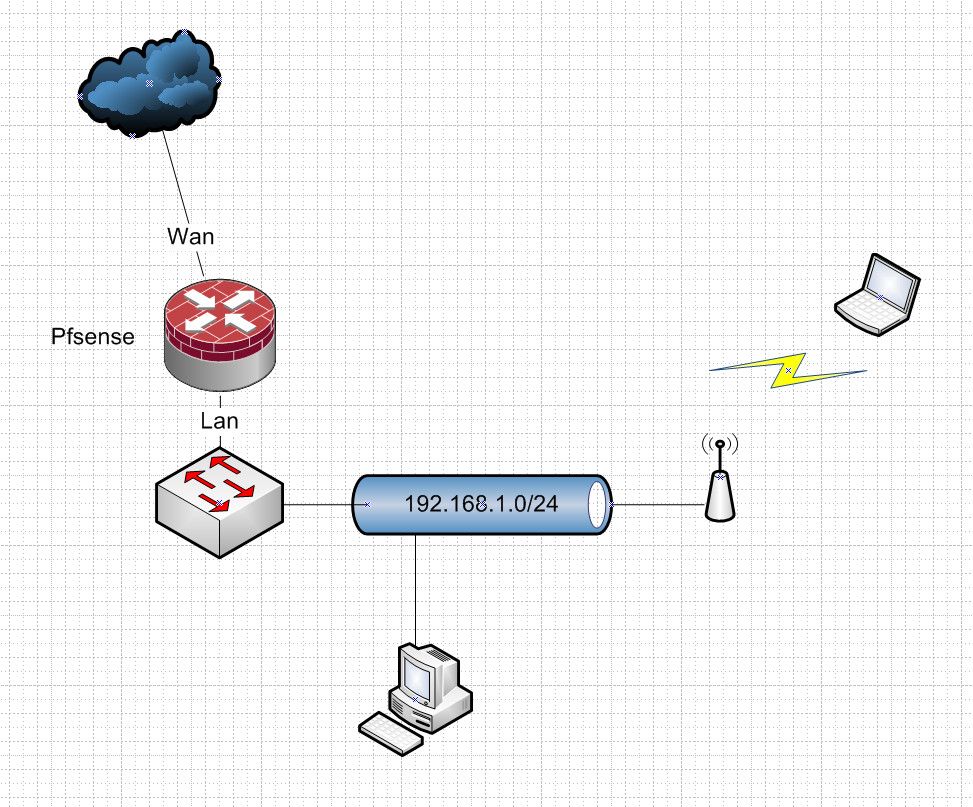
How would the block rfc1918 rule or any other rule on wan have anything to do with your wireless devices?
If you have some unconventional sort of setup, being specific in how you have it setup and how its connected or how you want to set it up would be helpful.
But the wan rules on pfsense would have zero to do with clients be wired or wireless talking to anything, be it the network on pfsense wan also being rfc1918 or the internet. The rules on the wan are only for unsolicited inbound traffic - and would effect your port forwards you might of setup, etc.. But wireless clients would be coming into the lan interface in a normal conventional setup, or some other interface of pfsense on the lan "side" of pfsense..
If you had enabled that rule on a lan side interface - that would block any and all connections from devices coming into that interface - be it wired or wireless.
-
@onthebeach said in Interface rules - best practices for IoT network(s)?:
Not sure why this needed to be moved anywhere, this, for me, this has been an installation issue and not a firewall issue (I never got that far).
While it might be part of your initial configuration what you're describing has nothing to do with the installation of the software onto hardware but the configuration and, specifically, configuring your firewall.