Isolated network with Internet access only, but NAT from outside
-
Dear all
I would like to isolate two networks so that they only have Internet access. Currently I have solved it with a simple REJECT rule, which denies access to all internal networks.
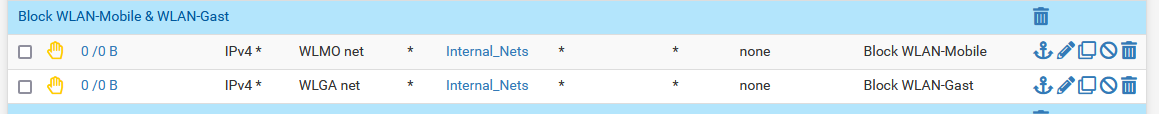
Now, from these two networks also the services of the DMZ should be reached. The networks use public DNS servers, thus receive the public IP of the domain. This is also resolved correctly.
I have chosen the NAT settings as follows:
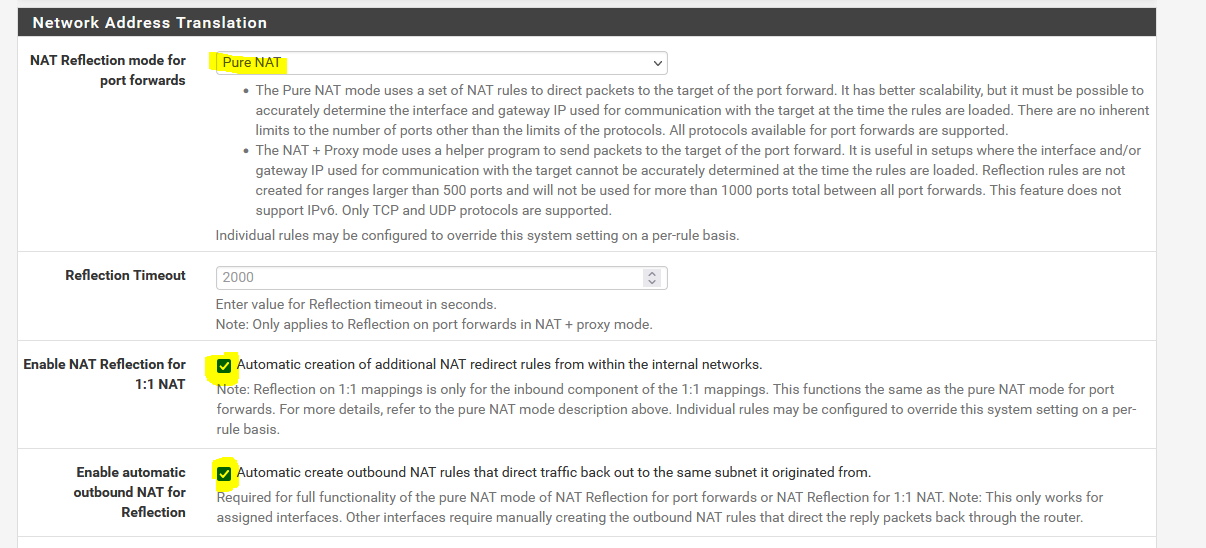
However, the clients in these networks cannot establish a connection. It is not clear to me why, since they go out via the Internet and should come back in like the Internet and NAT.
Does anyone have any idea how I need to set this up correctly?
Thank you and best regards
-
@MisterDeeds-0
I'd not expect to see the rules for both source networks on one rule tab.
It makes no sense having a rule with another source subnet on an interface.
Hint: select 'any' as source in block / reject rules. There is no need to limit it, as long as you don't have multiple subnets on this interface.Consider that with NAT reflection the real destination might be the internal address of the server.
-
Dear @viragomann
Thank you for the answer. The reason why both source networks are on one rule is that I created a Interface Group for all of my interfaces. So I can map all the rules on one page and I have a good overview.
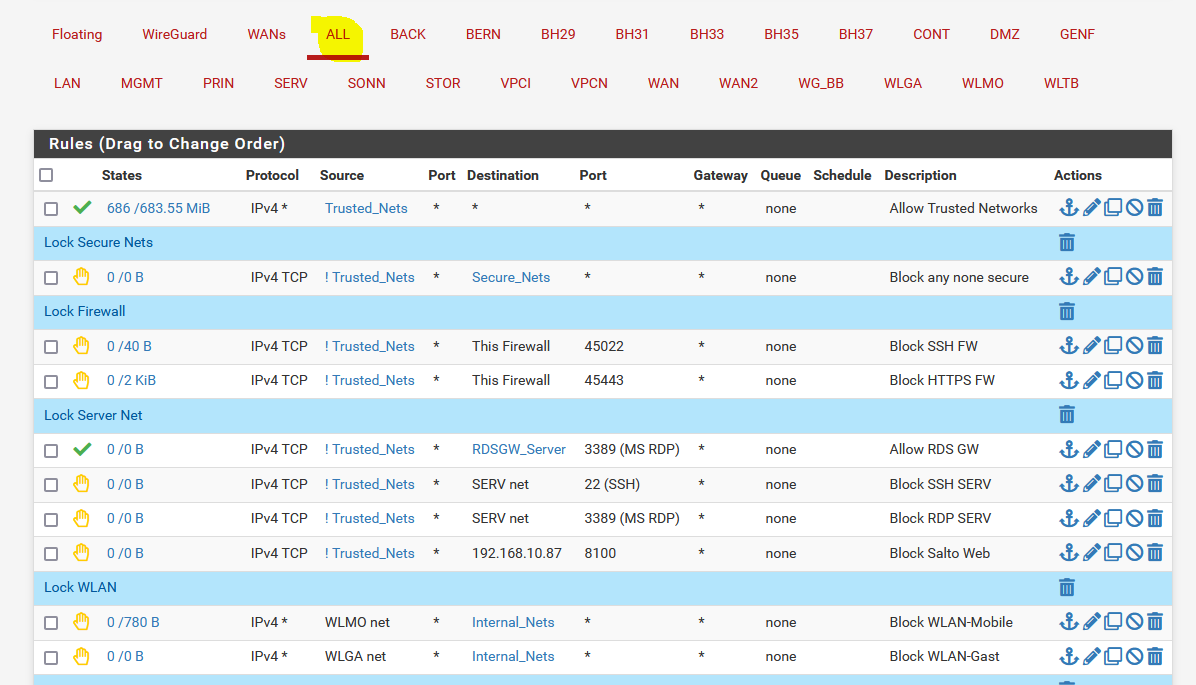
The domain is resolved correctly by the client with the public IP.
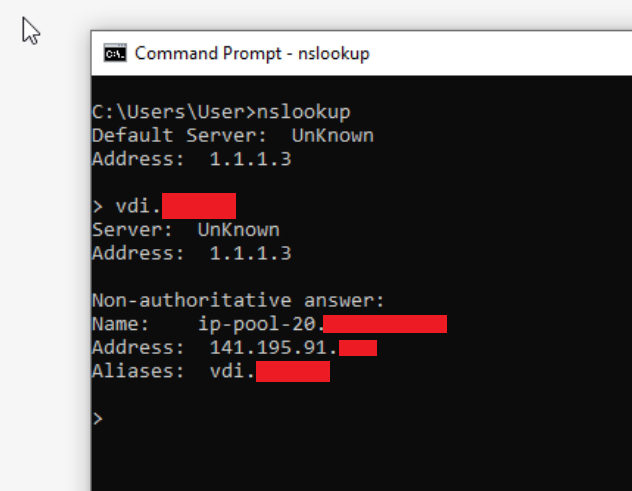
I have the NAT reflection because I have both an internal DNS zone and an external zone with the same domainname.
Is there a better solution so that I can isolate the networks and they can still access the services?
thank you and best regards
-
@MisterDeeds-0 yeah let your internal resolve the internal IP..
-
Dear @johnpoz
Thanks for the answer. I have now changed the DNS to the internal one, as well as left the NAT reflection on. However, it is not clear to me what difference this makes. I still don't want to have to open more ports from these networks. I want the clients to go to the Internet and connect back via the WAN interface.
Thanks and BR
-
@Mister-Deeds
Did you add a rule to permit the access to the internal IP?
You have to add this to the top of the interface group tab above of the reject rules, since if group rules have priority over member if rules. -
@Mister-Deeds said in Isolated network with Internet access only, but NAT from outside:
it is not clear to me what difference this makes
Your not hairpining your connections for one.. No offense but those rules are horrible - you can not not look at that those rules and have any clue to what exactly is allowed or not..
You should write explicit rules that say exactly what they do.. Non secure nets can not go to secure nets - well no shit.. What the default deny does anyway..
-
Dear @viragomann
Dear @johnpozThanks for the answers!
No worries, I dont perceive that as an offense :) For me it is clear and so far everything works.
The only thing that doesn't work for me is that I can access the services I have published via NAT via these two networks.
If I resolve the DNS with the external IP, the client would have to re-enter the network via the WAN interface of the firewall using NAT? Then this should be treated like an external client or not?
Internally there should be no connection from these networks to other networks on the firewall. Therefore I want the domain to be resolved by an external DNS and the clients from this network can only access the domain via WAN.
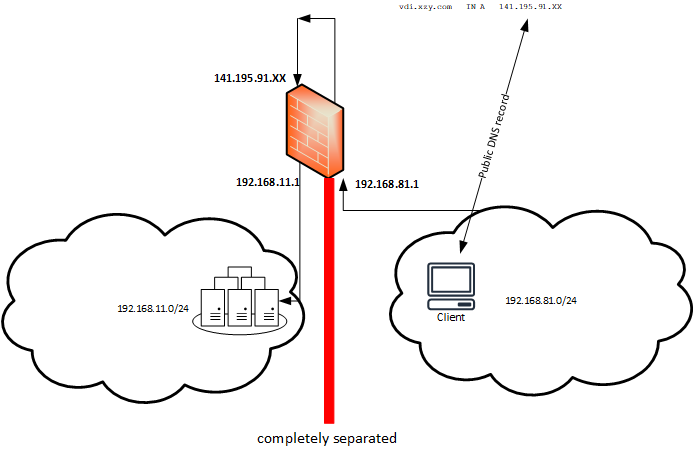
that should be possible, right?
-
@Mister-Deeds said in Isolated network with Internet access only, but NAT from outside:
The only thing that doesn't work for me is that I can access the services I have published via NAT via these two networks.
If I resolve the DNS with the external IP, the client would have to re-enter the network via the WAN interface of the firewall using NAT? Then this should be treated like an external client or not?No, it doesn't behave this way in fact.
If the packets would go out on WAN and re-enter, what should be the source and destination IPs? The WAN for both? No go.
NAT reflection means, that the NAT rule on WAN is also applied to the other internal interfaces, but not shown up in the rule set though.
This means, after the packet enters pfSense the destination address is translated to the redirect target IP. According to Ordering of NAT and Firewall Processing after this firewall rules are probed on the packet.
Hence the pf sees the origin client IP and the internal redirect target IP.So the pass rule on the incoming interface has to match these internal IPs.
So this statement is not solid:
Internally there should be no connection from these networks to other networks on the firewall.
because the traffic initialized by your NAT reflection rules is an internal one.
So again, without allowing it, the NAT reflection will fail.
BTW: the "Enable automatic outbound NAT for Reflection" option, which you've checked, effects that the packets are masqueraded with the pfSense interface IP. So the destination device sees the packets coming from pfSense rather than the origin client.
This is basically only needed if client and server are within the same network segment to avoid asymmetric routing. -
Dear @viragomann
Thank you so much for taking the time to explore this in detail!
I have now done it in the simplest and for me most logical way. I allow only DNS, HTTP and HTTPS, but this in all networks
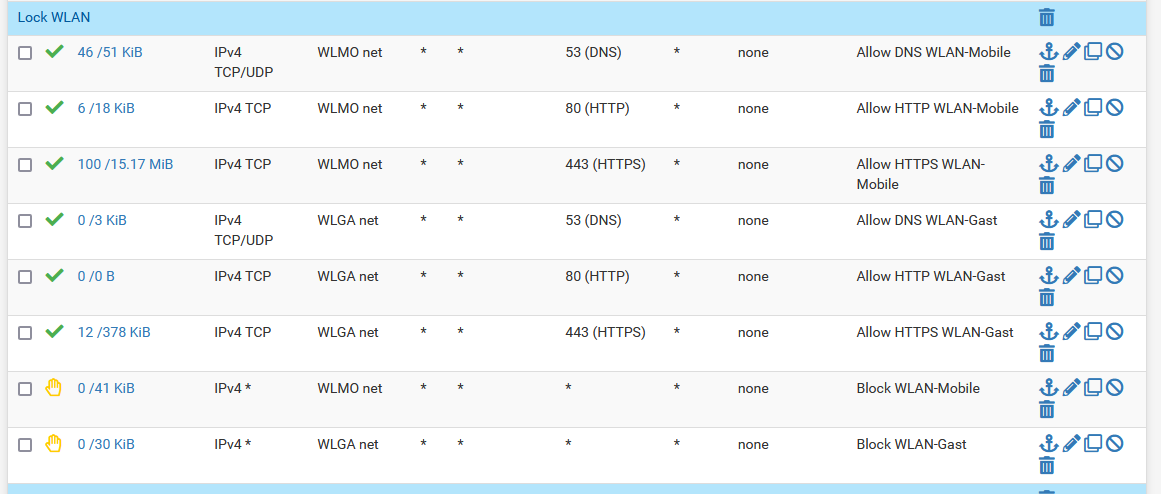
So it's secure enough for me and yet, the networks can access my webservices.
Thanks for the help and explanations!
Best regards