Snort vs Suricata Lists
-
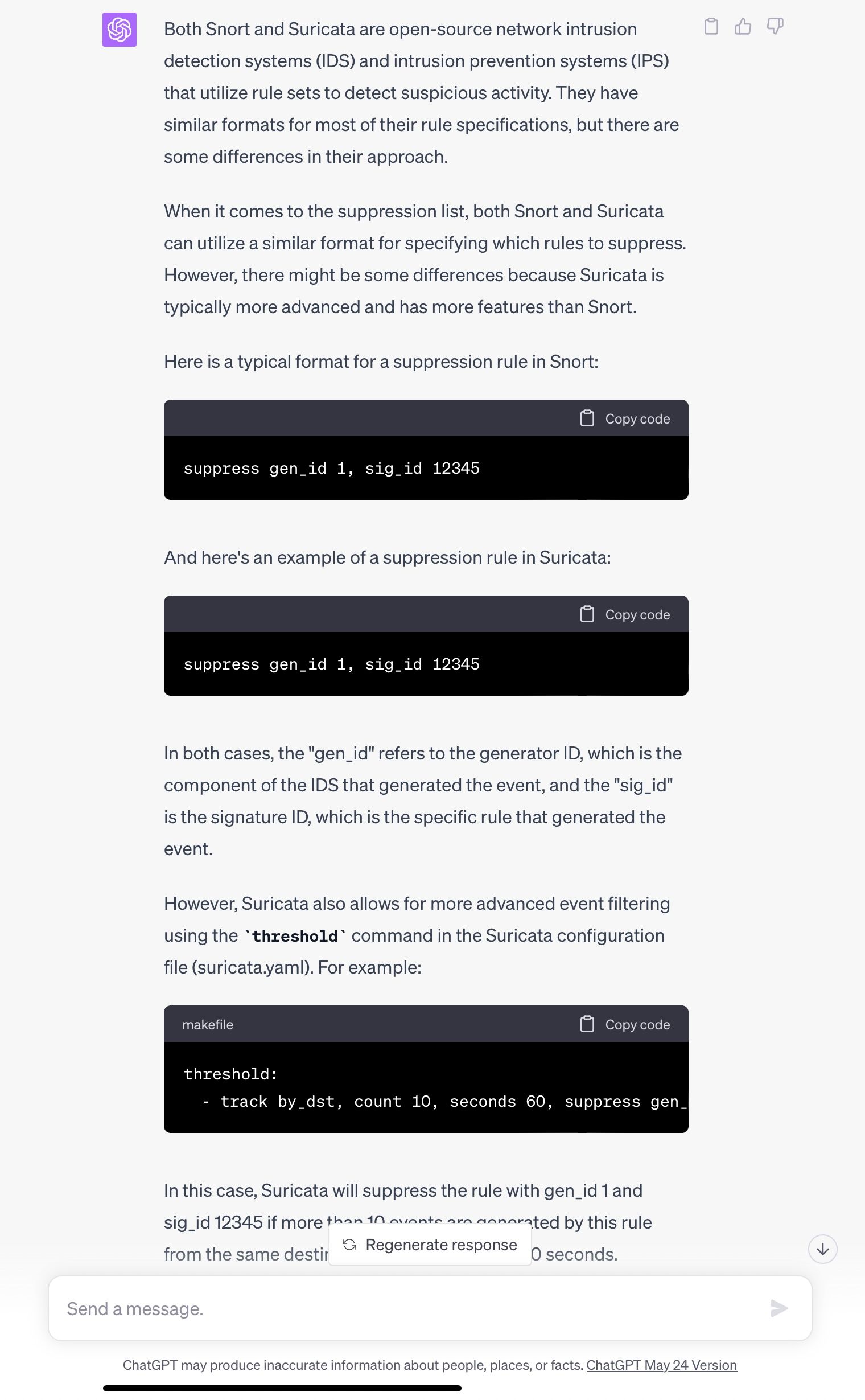
So are the suppression list formats the same if I go from Snort back to Suricata? I would assume so since the rulesets are the same (minus OpenAppID). I spent a lot of time fine tuning those and I'd hate to start over. Obviously I would need to remove any of the L7 stuff. Thanks.
-
-
Thank you, ChatGPT Plus. :)
-
@DefenderLLC said in Snort vs Suricata Lists:
So are the suppression list formats the same if I go from Snort back to Suricata? I would assume so since the rulesets are the same (minus OpenAppID). I spent a lot of time fine tuning those and I'd hate to start over. Obviously I would need to remove any of the L7 stuff. Thanks.
If it comes at one day that snort is not
anymore available for pfSense, you
could also go another way. Set up
a RaspBerry PI 4B 4GB/8GB as a sensor
and another unit as a snort server, done.You may be able to set up more sensors, let us
say on each LAN switch one and then they should be connected to the server to feed him.You may be able enrich that scenario to something else like you want, such;
- IPS in front of your Servers in the DMZ and/or LAN
- IDS at the switches
- OSSec on any other PC/WS/Server
Or snort for the DMZ and snort for the LAN
and OSSec on any PC, Workstation and the
servers. You may be able to do it in pfSense
and outsite like you want to go with it. -
@Dobby_ Good idea. I do have two 8GB RP4B's just sitting around doing nothing. I was using those for Pi-hole before switching to pfBlockerNG.