Captive Portal configuration for multiple VLAN
-
I am trying to activate a captive portal for more than one interfaces (meaning two different VLAN). The attempt is to also use HTTPS login. If I specify the hostname of the pfsense host (e.g. pfsense.example.com), it resolves to the LAN address. So far so good, but when a DHCP client (not in LAN) attempts to be redirected to the captive portal, it times out. For example:
LAN: 192.168.42.0/24
VLAN 1: 192.168.10.0/24 (Captive portal enabled)
VLAN 2: 192.168.20.0/24- DHCP client gets an IP from VLAN 1.
- Hitting the browser, it tries to redirect to pfsense.example.com, which resolves (successfully) to the LAN address.
- The timeout occurs.
The firewall rules for VLAN 1 allow everything (for troubleshooting) and the logs don't indicate it's a firewall deny case, at least up to the current investigation progress.
An option would be to override the DNS host in the resolver, but it does not support a per interface override. Haven't explored the possibility of a forwarder or BIND for now.
Am I missing something with regards to the captive portal setup maybe?
-
Do it like this :
For VLAN 1: 192.168.10.0/24 - create a host override (under Services > DNS Resolver > General Settings - at the bottom) : portal1.example.com pointing to 192.168.10.1
For VLAN 1: 192.168.20.0/24 - create a host override (under Services > DNS Resolver > General Settings - at the bottom) : portal2.example.com pointing to 192.168.20.1If possible, use the acme.sh pfSense package to get a *.example.com certicate.
Then
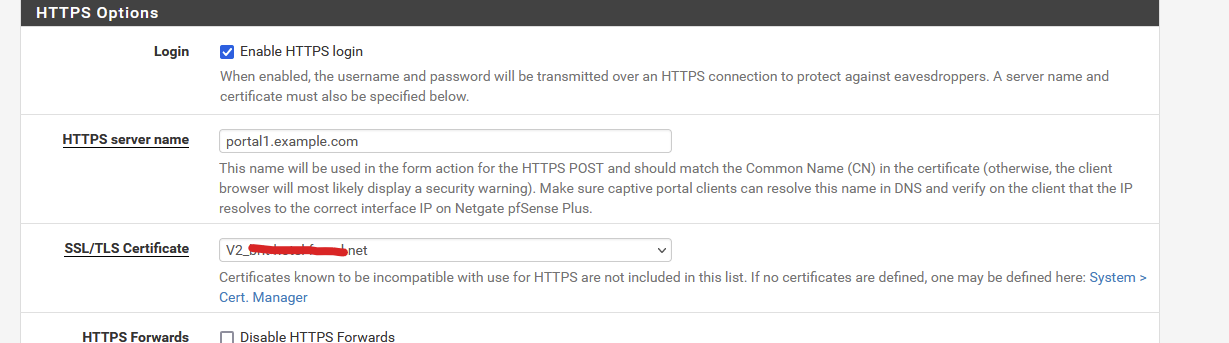
for the first "192.168.10.0/24" portal.
And portal2.example.com" for the "192.168.20.0/24" portal.This is the issue :
@salousama said in Captive Portal configuration for multiple VLAN:
Hitting the browser, it tries to redirect to pfsense.example.com,
when the device (portal user) isn't authenticated, the GUI firewall rules aren't even used yet.
So you can't redirect to 'LAN'.The captive portal uses "Hidden" pf (firewall) rules that :
Let pass DNS (port 53, TCP and UDP) request to itself (pfSense).
Redirect incoming 'TCP 80' to the internal 127.0.0.1:800a
Redirect incoming 'TCP 443' to the internal 127.0.0.1:800(a+1
)Nothing else passes.
Again : when authenticated, the GUI captive portal interface firewall rules come into action.
-
@Gertjan Thank you for your response and effort, it all makes sense then.. I will try out the different DNS overrides and see how that will go.