Confused about port forwarding
-
I am in the process of switching out a decade-old Netgear Genie router with a pfSense Netgate 3100 that we have had laying around for a few years. I have successfully updated the software on the Netgate 3100 to the latest version (23.05). When the Netgate 3100 is plugged in instead of the Netgear, all Internet traffic works. However, non-PC devices (specifically a multifunction printer and a fire panel) trying to communicate outside the LAN are not working properly. I have tried setting up NAT/firewall rules to match what was setup on the Netgear, but it does not appear to be working. I have spent hours trying to figure out how to get the Netgate to work like the Netgear did for these devices, with no success so far. The CPE is proprietary equipment from Spectrum (formerly Time Warner) and includes both a modem and a router/WAP. We have five static IP addresses from Spectrum. Can someone help guide me to a solution?
-
@23roadsdiverged said in Confused about port forwarding:
non-PC devices (specifically a multifunction printer and a fire panel) trying to communicate outside the LAN are not working properly.
So those are connected behind pfsense - and they get an IP from the dhcp server running on pfsense. Did you change your network from when you installed pfsense, like from 192.168.42/24 to pfsense default of 192.168.1/24 ?
Out of the box there is nothing to do with rules on the lan, it defaults to any any - did you change that? Is it possible these devices are hard coded IPs on the devices? And they are pointing either to different gateway IP? Or dns that your not allowing?
-
@johnpoz The LAN default gateway address (10.x.y.z) is the exact same on both old and new devices, as is the subnet mask.
I have tinkered with the NAT/firewall rules, although 2-3 years ago we had someone attempt to configure it unsuccessfully, and so there was already a firewall rule in place from him. Should I clear all firewall rules? I had thought it was implicit deny... I can list out current NAT/firewall rules if that would help.
They both have DHCP with a limited range, but the given devices have reserved ("static"?) IP addresses outside of the DHCP range. I initially had the printer set as a static IP, but then changed it to dynamic; once pfSense gave it a dynamic IP, I then used pfSense to set it's MAC address to have the same static IP as before.
The fire panel has a static IP (possibly two) that was/were programmed into it by the Fire Panel company and one seems to respond to pings but show offline, while the other does not respond to pings but shows up as online. I was able to find the MAC address of the fire panel and reserve it the same static IP in pfSense as it had previously, I think. Both IP addresses are also outside of the DHCP range.
Regarding DNS, I am not sure how the fire panel is configured. The DHCP settings originally had our AD DS controller using google DNS (8.8.8.8 and 8.8.4.4), which I have switched on both the AD DS controller and the pfSense box to instead point to the Quad9 DNS (9.9.9.9 and 149.112.112.112). Should I switch that back?
-
@23roadsdiverged what did you change the firewall rules too?
Out of the box any device on the lan network of pfsense would be able to go anywhere, it default to any any rule..
So unless your running a captive portal on pfsense or something.. Out of the box any thing on your lan can go anywhere
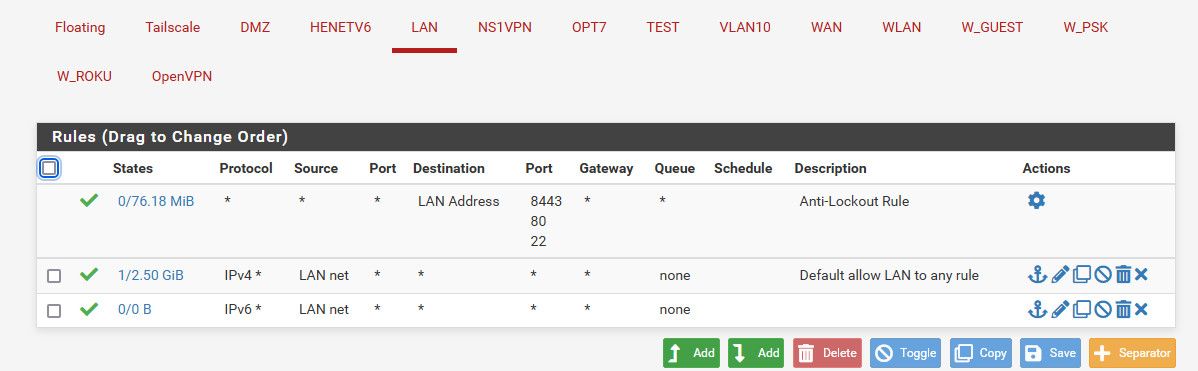
If your saying other devices are working, and you have the default rules, nothing in floating - no weird port forwards or outbound nats setup on the lan.. Then anything should work that is using pfsense as its gateway.
Other thing comes to mind is where your trying to go or test whatever on say a printer would be dns is failing to resolve where they are trying to go..
If all your settings are to allow and still failing whatever your doing to test, I would sniff on pfsense lan interface for the IP of the device to validate its actually sending you traffic, and dns its doing is getting a valid response, etc..
-
This post is deleted! -
This post is deleted! -
@23roadsdiverged those look pretty messed up. Why would you do a port forward for traffic hitting your wan on 10.0.0.251 IP to the same IP?
From your outbound nats, looks to me like you created a vip on pfsense for this 10.0.0.251 address?
What are you wanting to talk to what here? What are the IPs on your pfsense wan and your lan? If you have something on the pfsense wan network and you want it to talk to something pfsense. And its rfc1918 then you would need to turn off the block rfc1918 rules, and then either allow the traffic you want to forward to where. But your forwards are forwarding destination IP to the same IP??
But yeah none of that stuff makes any sense, and sure and the hell isn't going to work.
-
@johnpoz There is nothing in floating, although I believe I am missing the default rules you mentioned. I should probably clear out all the rules I've made and start from scratch, and see if that work?
I'm not sure I know how to do what you are saying regarding DNS and the printer.
-
@23roadsdiverged the default rules are there, but your port forwards are a mess.. never going to work.
What are your networks on your wan and lan.. What IP is trying to talk to what?
-
I have cleared all but the default rules now. Will go check to see if printer works now...
I was told by the Fire Panel company that the Fire Panel needs to be "whitewalled"... googling that term shows nothing. I believe they said it also needs to accept any incoming messages for it.
WAN is one of the static IPs from Spectrum. 24.153.213.114 /29
LAN is 10.0.0.1 /24
-
@23roadsdiverged said in Confused about port forwarding:
LAN is 10.0.0.1 /24
Ok pfsense IP is 10.0.0.254? Why do you have a 10.0.0.251/32 IP setup on pfsense?
What IP pfsense lan?
What network are these fire panel or panels or fire panel servers sitting on? Do you need some IP on the public internet 1.2.3.4 or something that needs to talk to whatever the firepanel IP is that is on your 10.0.0 network behind pfsense?
-
@johnpoz Fire Panel is both 10.0.0.251 and 10.0.0.254, from what I can tell. pfSense is 10.0.0.1.
Multifunction printer is 10.0.0.201
I was trying to get port forwarding to match what was on Netgear Genie.
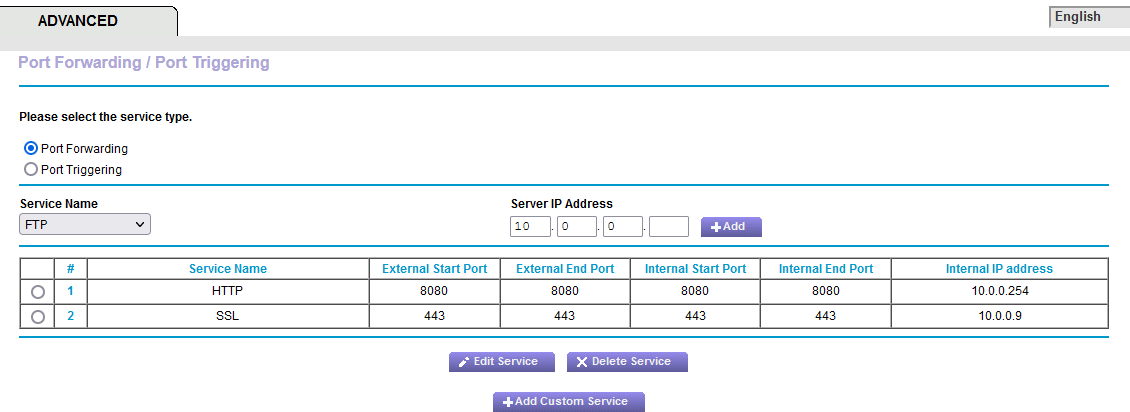
Yes, but on the Netgear router I never needed to know/enter the public IPs that need to talk to the Fire Panel. From looking in Diagnostics -> States, it is attempting to communicate to two public IPs: 64.9.116.20 and 66.153.46.154 through port 5050. Doing a tracert, those lead to getting hung up on the following IP: 206-169-51-51.static.ctl.one [206.169.51.51]. The Fire Panel company did say that they had to turn off their receiving device due to it receiving thousands of messages that it cannot establish a full connection. And from what they have told me in the past, it needs to accept incoming connections on different ports than what it sends out on. I think.
-
This post is deleted! -
@23roadsdiverged you don't need to know the public IPs that want to talk to some internal IP, unless you want to lock it down.. But there is nothing in your rules that would stop 10.0.0.x from talking to some public IP.. But if you need the public internet to be able to talk to 10.0.0.254 that is behind pfsense.
Then that would a port forward on your wan (wan address), that forwards the port to that IP..
example.
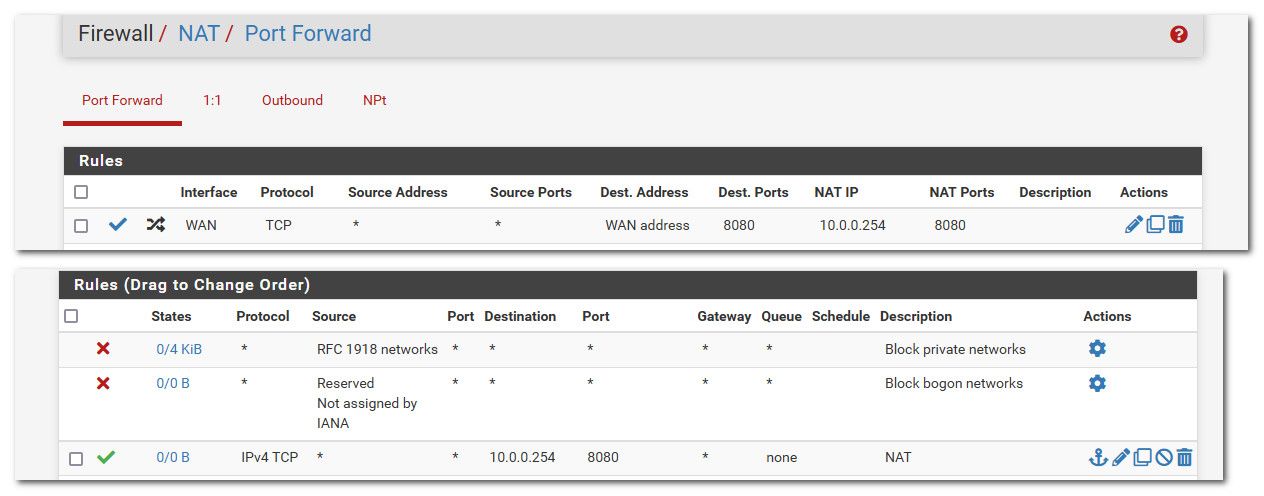
by default pfsense would create the wan firewall rule to allow the port forward
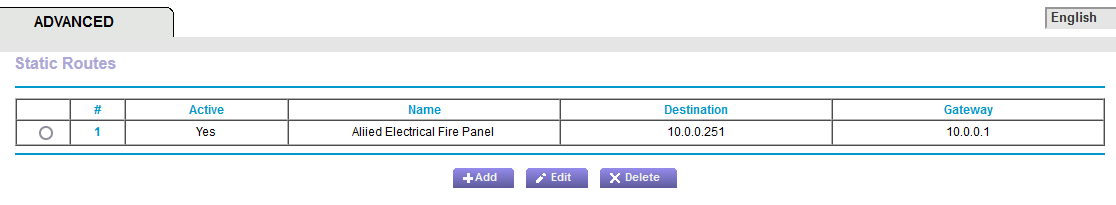
There is no reason you would need a "route" to get to 10.0.0.251, because pfsense knows how to get to anything on your 10.0.0.0/24 network because it is attached to it.
-
@johnpoz Ok, I have cleared out all misconfigured NAT rules and now have only the block Bogon and RFC 1918 ones showing. I then added the rule you described. Here's another thing I don't understand... in the Netgear, this 10.0.0.254 address was not listed in the IPv4 leases... but the 10.0.0.251 was. But the fire panel worked just fine. The 10.0.0.9 IP address listed in the port forwarding also was listed in the IPv4 leases, so I am not sure what that was for (it is also outside of the DHCP range).
-
@23roadsdiverged, if the device is setup up as static IP on the device, then no it wouldn't be listed in some dhcp servers lease table.
-
Sorry, what I meant was in the Netgear it was listed under "Connected Devices" with the static IP, along with all other connected devices, whether static or dynamic IP.
In Netgate/pfSense, the only similar screen I have found is the DHCP leases, I don't see where to access a similar "Connected Devices" page like what the Netgear had. But yeah, pfSense only lists static IPs on that list if I manually configure a device that initially shows up as a dynamically assigned IP.
-
@23roadsdiverged Check the ARP Table.
-
This post is deleted! -
@rcoleman-netgate Ok, so when I looked, sure enough the 10.0.0.251 was not showing up in the ARP table. Feel dumb that I didn't realize the "Connected Devices" on the Netgear is the ARP table... I then reassigned the MAC address to 10.0.0.254, and it shows active and now shows up in the ARP table.... I will see if that, combined with the proper port forwarding from @johnpoz allows communication. Ty both!