Synology Package Manager Issue
-
Almost every other day my Synology NAS is not able to connect to the Package manager
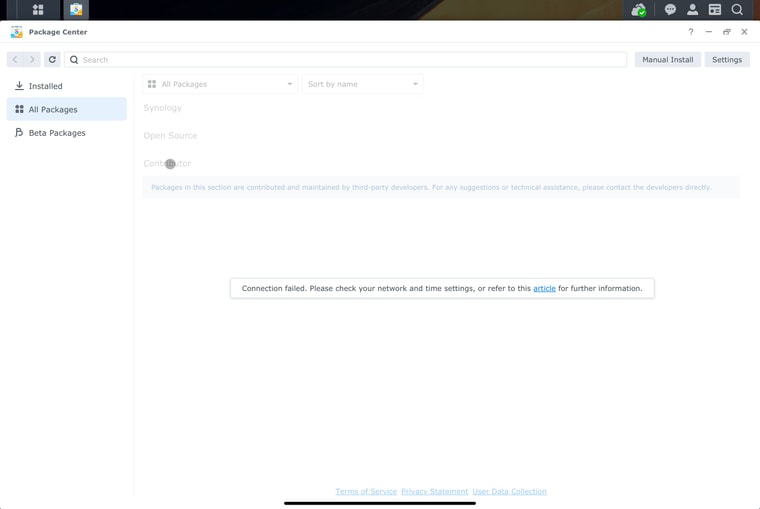
I thought it was a firewall issue, so I allowed all traffic (temporarily) but with no luck. This happens to both my NAS devices. Only way I am able to connect to package manager is by rebooting the PFSENSE (NETGATE 4100) device. It will work for a day or two, then back to the same issue.
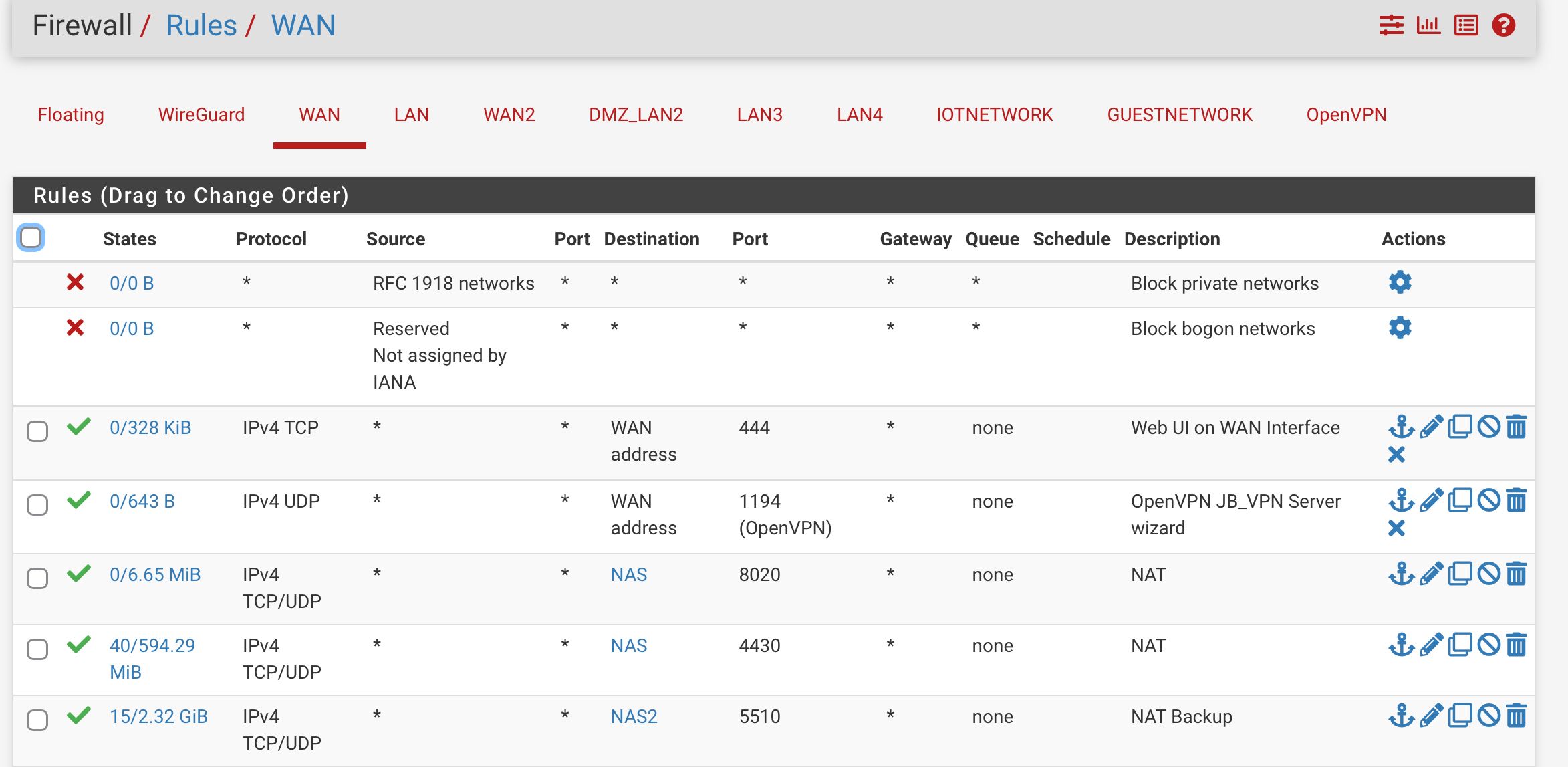
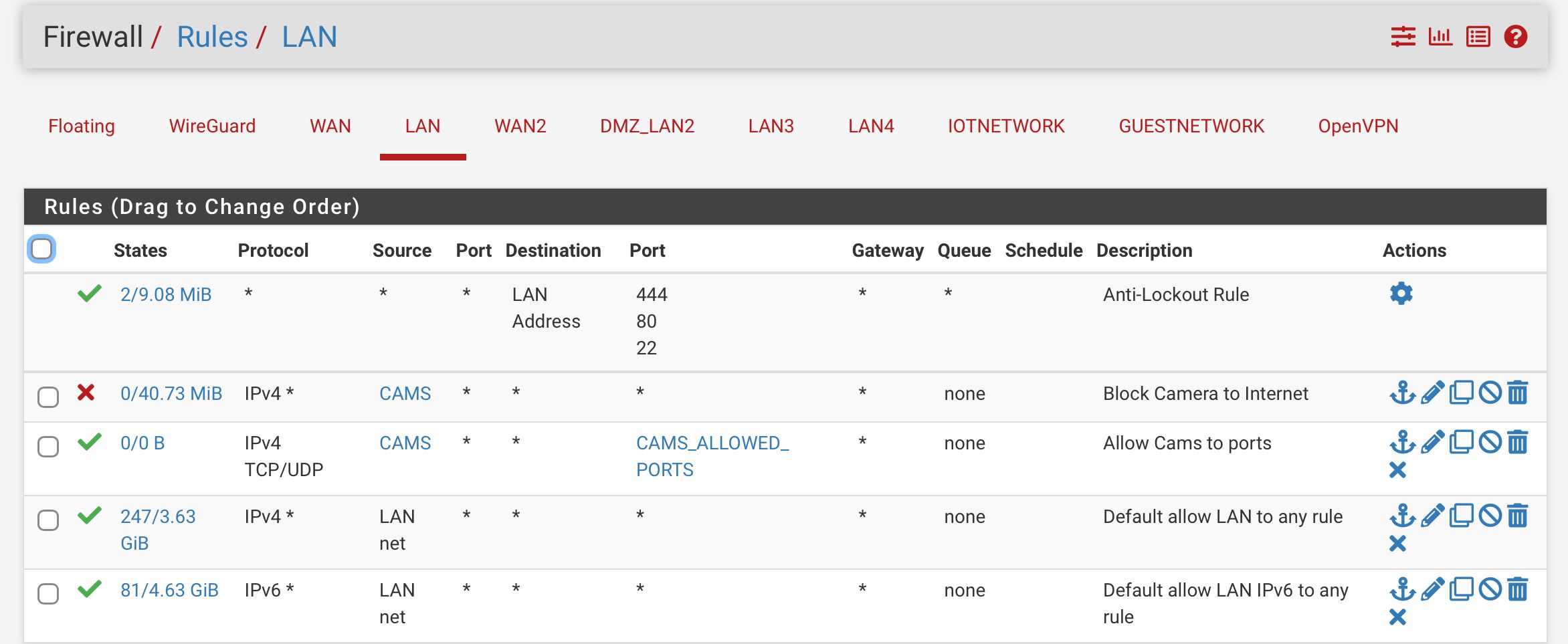
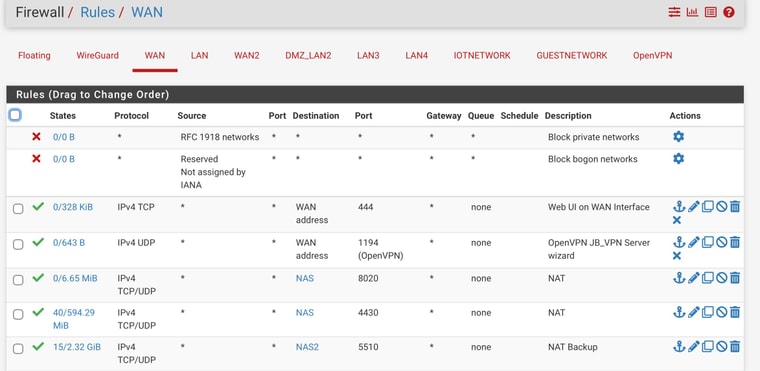
These are my configs on the firewall. Any guidance would be appreciated.
-
@jabren You are running pfBlocker?
-
@michmoor I am not. I was running SNORT a few weeks back to test it, but ended up removing it shortly after.
-
@michmoor What do the firewall logs show then?
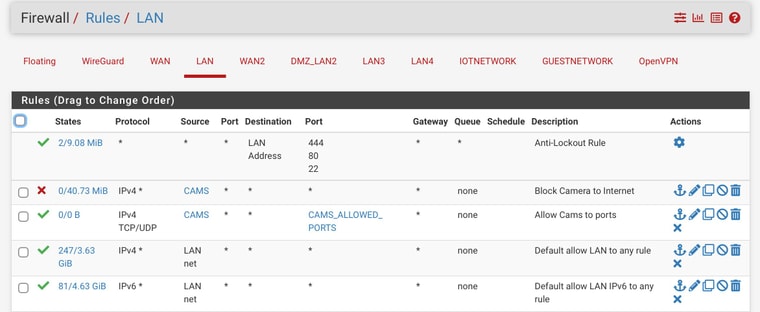
Based on your LAN rule,assuming your Synology doesn't fit into the CAMS alias, your flows should go outbound so if its being blocked the first place i would check is the firewall log. -
@michmoor
NAS as source:
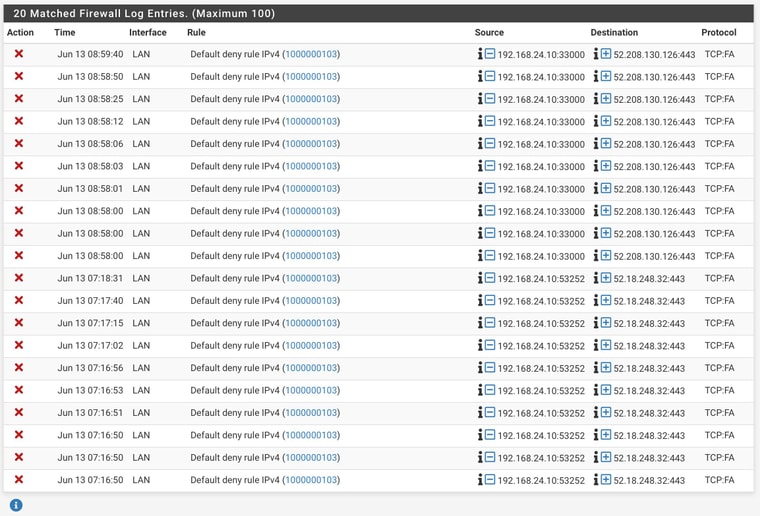
NAS as Destination:
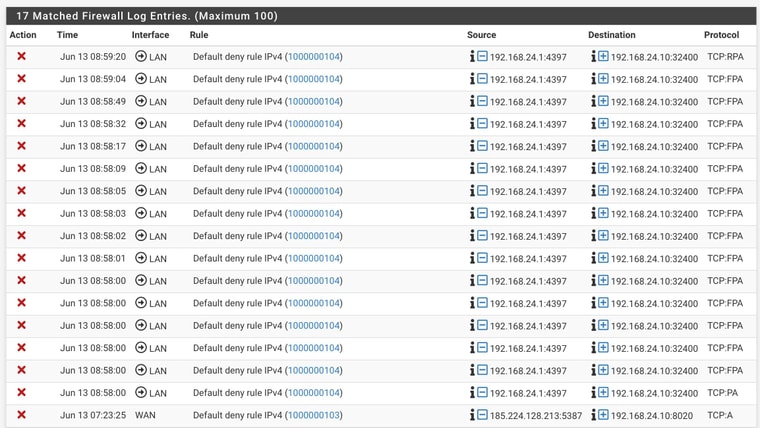
-
@jabren Reload the firewall filter and check again.
-
@michmoor Reloading makes it work, but after a day or two, it will go back to not working,
NAS AS Source:
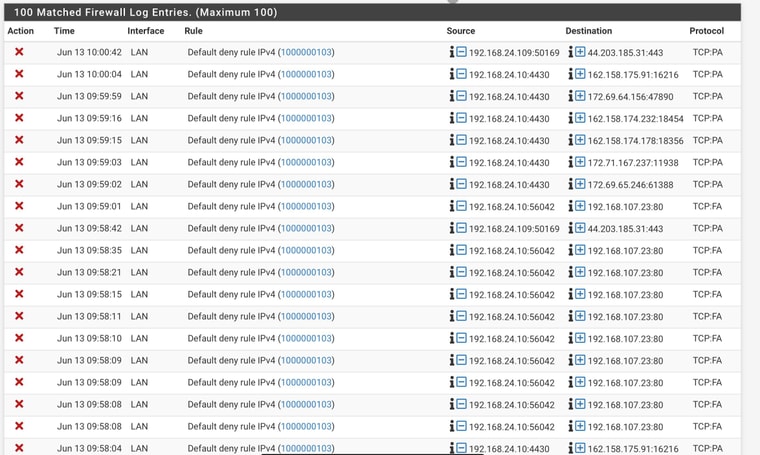
Nothing for NAS as Destination
-
Those are expected blocks from out of state TCP traffic:
https://docs.netgate.com/pfsense/en/latest/troubleshooting/log-filter-blocked.html#troubleshooting-blocked-log-entries-for-legitimate-connection-packetsI would check it's not a DNS issue. make sure the NAS can still resolve when this happens.
Steve
-
@jabren said in Synology Package Manager Issue:
Reloading makes it work, but after a day or two, it will go back to not working,
That doesnt make any sense. If it works because of a matching rule than it works. If it "stops" working is because of another rule that would prevent the flow. is placed above it or a more specific rule denying it.
Its your LAN rules that we are concerned with. Inbound WAN rules dont matter. -
@stephenw10 I may need to wait a day or two for the issue to come up again. After the reboot, everything is working fine.
-
-
...feels like DNS
-
@stephenw10 DNS as in PFSENSE having issues resolving or the DNS servers I have setup are faulty.
FYI, I use the following
DNS 1: IP of PFSENSE
DNS 2: 1.0.0.1
DNS 3: 8.8.8.8 -
Could be either pfSense or the NAS directly. Seems unlikely those three would fail if set on the NAS though.
-
@jabren all of that is out of state.. You need to figure out why that is happening.. You have some asymmetrical setup maybe. Your loosing internet or your ping goes to high and you have pfsense set to reset states?
But yeah every single one of those blocks are out of state blocks. Client should just create a new session. Is your nas multihomed - ie does it have a leg in more then one network... Ie this 192.168.24 and 192.168.107? That can cause all kinds of weirdness.. If not careful on how you set that up..
Or does this pc have multiple connections in both networks?
edit:
example of this, even the best of us ;) can run into a doh moment.. I had setup a network on my nas 192.168.2/24 so I could do some iperf testing across pfsense.. Had source natted the traffic so when I talked to the 192.168.2 address from my 192.168.9 network the nas answered back via its 192.168.2 address.This was meant to be just a temp thing for a hey can my pfsense route at gig for some other thread ;)
I forgot to turn it off.. Then on my phone I was access shares off its 192.168.9.10 address, but my phone was on the 192.168.2 wireless network.. Sometimes it would work, sometimes it would fail - I could access one share, but not another one, etc. etc.. all weird..
Well guess what - the client had a 192.168.2 address, so vs the nas sending traffic back via its 192.168.9 address it would say oh I have a interface in the 192.168.2 and try and answer with that.. which would fail because it was out of state..
Multihoming devices can lead into all kinds of issues if your not careful, and fully understand what can happen when you set that up.. And what your talking to and what that something your talking to might answer back with, etc.
-
@johnpoz The NAS only has a single network. The 192.168.107 are IOT devices which the firewall only has a rule that allows from main to IOT. I noticed SNORT config still exist on the config.xml file. I’m not sure if it causes any issues (since I did uninstall of snort). It may not even be an issue, but worth bringing up.
-
@jabren your blocks are all out of state.. There are FA, which means client is trying to close the session, but maybe it was closed already?
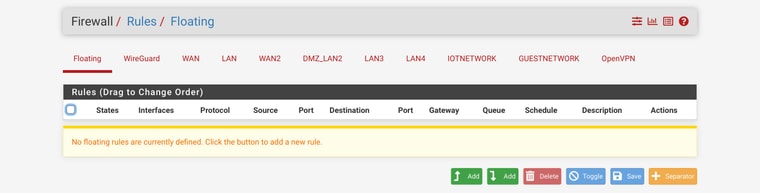
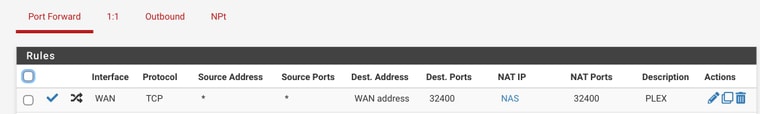
I just noticed you have outbound traffic being blocked as well that 24.1 talking to 24.10 on 32400 (plex?) which is a RA, with push flag.. Why are you blocking outbound traffic? That has to be a floating rule..
What is 24.1? I would "guess" that is pfsense IP?? maybe not.. But your blocking outbound traffic.. What are you floating rules?
-
-
@jabren did you edit the rules since you posted those blocks? The only way you can get an outbound block is with floating rules. Unless IPS can do it - but I don't think so, I don't use either of the IPS packages on any sort of reg bases..
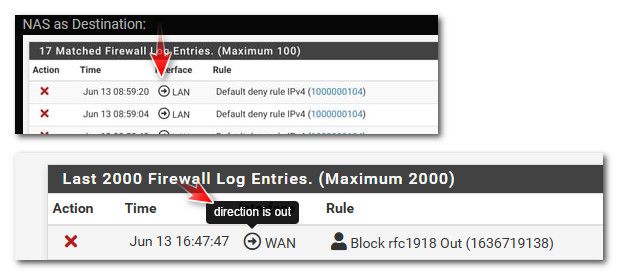
A port forward on your wan wouldn't come from a 192.168.24.1 address, unless you were also doing an outbound nat (ie source natting) traffic. Or you have rfc1918 on your wan?
But says that is the default rule?? Very odd.. Possible some odd thing happening with your states and they are being reset.. Are you interfaces going up and down, or seeing slow pings?
-
Outbound traffic will still be blocked if it's out of state. Which that is. None of those block logs look like they would cause this.