Cannot ping new vlan interface
-
@feisal said in Cannot ping new vlan interface:
And machines in the 192.168.4.0 network cannot access the VLAN10 interface.
So there is probably an L2 issue.
What do you get exactly, when you try?
-
@viragomann![ ]
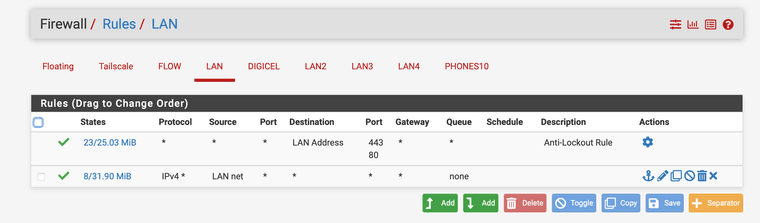
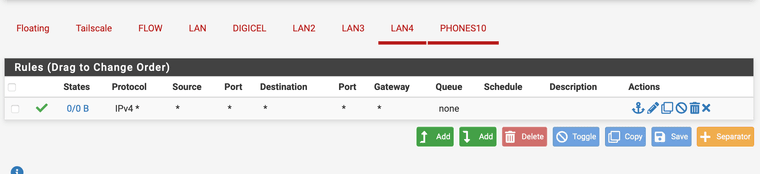
Here are the rules.
I get host unreachable when I try -
@feisal
So I suspect that the layer 2 isn't working properly on that VLAN.If you have it set up correctly on pfSense the failure is probably outside of it.
You can sniff the ARP traffic on the VLAN interface, while you try to ping a device in that VLAN, for further investigation.
You should see ARP requests from pfSense, unless the entry is already in its ARP table. And if there are request you should also see responses if the L2 is working. -
@feisal can it be that the parent of the VLAN interface is in use? I am going to try a different (unused parent) later and report back.
-
my 2 cent,
the cable from pfsense to the switch is not on the right port ? like tagget / untagged / not member ?
the port on the switch should be vid 1 untagged / vid 10 tagged -
@viragomann
I get these
19:07:23.685373 ARP, Request who-has 192.168.4.3 tell 192.168.4.1, length 28
19:07:27.685263 ARP, Request who-has 192.168.4.3 tell 192.168.4.1, length 28So it looks like a L2 problem, but I am not sure how to solve that.
-
@feisal Show your switch config.
As said above, you probably are tagging/untagging ports correctly. -
@Jarhead I am quite sure of that now, I have screwed around with the config so much now that posting it would not be helpful. I will explain what I want to accomplish and maybe someone with more knowledge will have an insight.
I am connecting to a DGS-1210 web managed switch.
Port 24 - traffic from 192.168.1.x (untagged) and VLAN tagged 10 traffic from 192.168.4.x (PBX and its gateway)
Port 6 - untagged phone traffic from 192.168.4.x which I want to tag using a PVID 10
Port 1 - connection to Netgate 4100
other ports - untagged traffic from 192.168.1.xI want the VLAN10 tags preserved along with the untagged traffic sent via port 1 to the Netgate 4100 which has the 192.168.1.1 interface and VLAN10 192.168.4.1 along with their respective DHCP servers.
The phones don't need to get to the Internet just to the PBX which does need to get to the Internet for updates etc. This I can control using firewall rules. -
@feisal said in Cannot ping new vlan interface:
I want the VLAN10 tags preserved along with the untagged traffic sent via port 1 to the Netgate 4100 which has the 192.168.1.1 interface and VLAN10 192.168.4.1 along with their respective DHCP servers.
So configure the port equal to port 24.
However, I'm wondering, why you have VLAN 10 tagged on 24. Is the PBX also configured for tagged VLAN?
-
@viragomann
PBX along with other servers are VMs under Proxmox. So the PBX traffic is tagged with VLAN10 to separate it from the other servers.
The phones and the SIP box from the phone company are on the 192.168.4.x networkwhat do you mean by "So configure the port equal to port 24."?
-
@feisal said in Cannot ping new vlan interface:
what do you mean by "So configure the port equal to port 24."?
Port 1, which you've connected to pfSense. It needs the settings equal to port 24.
LAN 192.168.1.x untagged, VLAN 10 tagged. -
@viragomann
Thank you, will try it after when everyone has stopped work this evening and let you know. -
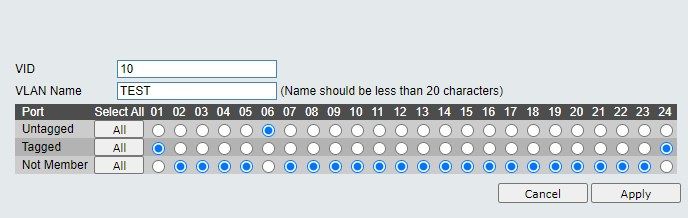
@feisal
Port 1 -> vid 1 untagged / vid 10 tagged
Port 2-5 -> vid 1 untagged / vid 10 not member (or tagged)
Port 6 -> vid 1 not member (or tagged) / vid 10 untagged
port 7-23 -> vid 1 untagged / vid 10 not member (or tagged)
port 24 -> vid 1 untagged / vid 10 tagged (PBX and gateway must have the network card set to vlan10)

-
@kiokoman
Unfortunately, it did not work, same issue, I can ping everything on the VLAN10 from within the VLAN10 except from the PFsense 192.168.4.1 interface.
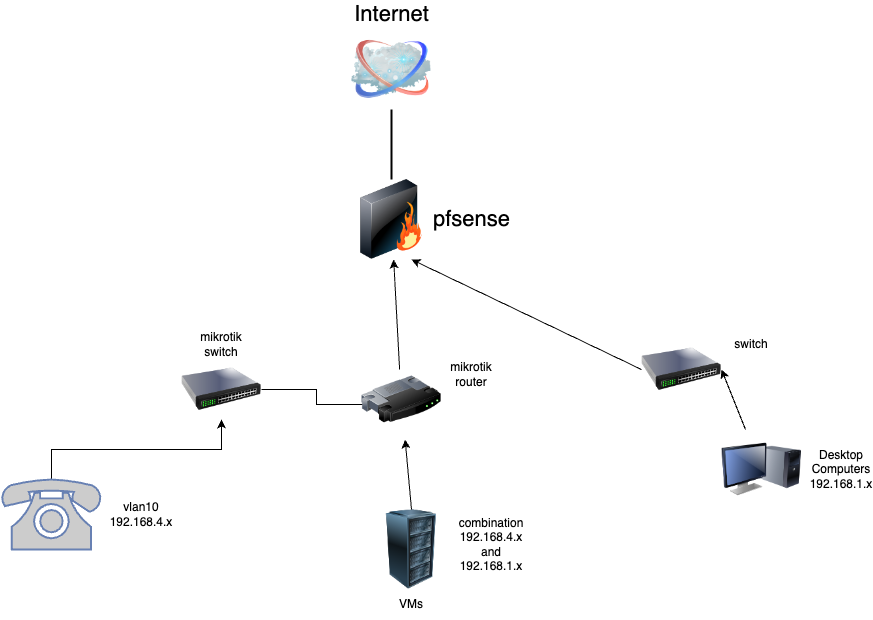
ARP traffic does not want to go down two lines, I guess?I ended up taking all the 192.168.4.x phones and put them in the Mikrotik switch on VLAN10. The Mikrotik switch is connected to a Mikrotik 10G router which is connected to all the VMs.
I made a diagram of what I ended up with.
-
Looking back at the diagram, I wonder if what I was trying to do is impossible and an L3 switch/router was the correct solution.
-
@feisal said in Cannot ping new vlan interface:
ARP traffic does not want to go down two lines, I guess?
No, that's not the issue. ARP packets for the VLAN are tagged as well. So they are separated from the untagged LAN.
I still think, there must be something wrong in the VLAN setup on either end.However, you can try to bring your LAN into a VLAN as well.
Also since you have obviously enough NIC on pfSense, you can split your primary switch into two virtual switches and connect both to different NICs on pfSense. So you can set up all this without any need of a VLAN.
-
@viragomann
Thanks for the suggestion. I will certainly try it, because I want to add another VLAN to the network.
I appreciate the help