OpenVPN site to site works with shared key but doesn't with SSL/TLS
-
Hello,
For the past few days i've been struggling with creating a VPN lan to lan connection using OpenVPN and IPsec. When using shared key, there is connectivity between sites and there are no issues, but when changing to SSL/TLS, OPENVPN/IPsec tunnel appears UP but there is no connection between endpoints. The firewalls can ping everything that is connected to them but endpoints can't.
If i switch back to shared key it works again, since shared key si not secure i need to have it working with SSL/TLS certificates.I've tried creating and intermediate CA, creating CSR on client and signing it on the server side, i don't think it's an issue related to certificates since the tunnel is up.
I don't know why the traffic isn't routing when using certificates. Here is the topology im using, in a LAB with virtualbox
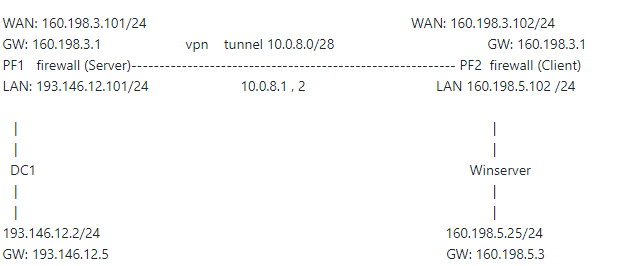
For testing purposes , all the traffic is allowed, there are no blocking rules. Also i tried every type of encryption, nothing works (no encryption, AES-256 with SHA256, secp384r1 for the certificates with SHA512).
This is the actual config.ovpn of the VPN Server:
dev ovpns1
verb 11
dev-type tun
dev-node /dev/tun1
writepid /var/run/openvpn_server1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp4
auth SHA512
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
local 160.198.3.101
tls-server
server 10.0.8.0 255.255.255.0
client-config-dir /var/etc/openvpn/server1/csc
ifconfig 10.0.8.1 10.0.8.2
tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'PF1' 2"
lport 1194
management /var/etc/openvpn/server1/sock unix
max-clients 50
push "route 193.146.12.0 255.255.255.0"
remote-cert-tls client
route 160.198.5.0 255.255.255.0
capath /var/etc/openvpn/server1/ca
cert /var/etc/openvpn/server1/cert
key /var/etc/openvpn/server1/key
dh /etc/dh-parameters.4096
ecdh-curve secp384r1
tls-auth /var/etc/openvpn/server1/tls-auth 0
data-ciphers none:AES-256-GCM
data-ciphers-fallback AES-256-GCM
allow-compression no
topology subnet
explicit-exit-notify 1
inactive 300 -
@GMQsync
Change the tunnel mask to /30. -
@viragomann It really worked just by changing the tunnel mask
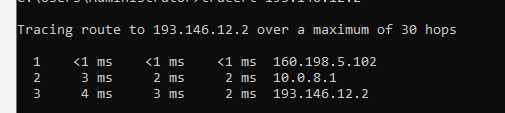
Thanks a lot mate!