Experimental Ethernet Layer 2 Firewall Rules
-
Hello Fellow Netgate community members has anyone else played with the new layer 2 filter?
Per Netgate Docs:
"If an administrator wants to block all L2 traffic by default, they can first craft a ruleset with appropriate pass rules and then follow that with a rule to block any other Ethernet traffic. As the potential for mistakes and disruption is extremely high, this is not considered a best practice at this time."
I wanted to test some configs out today. . .
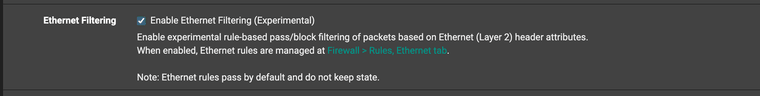
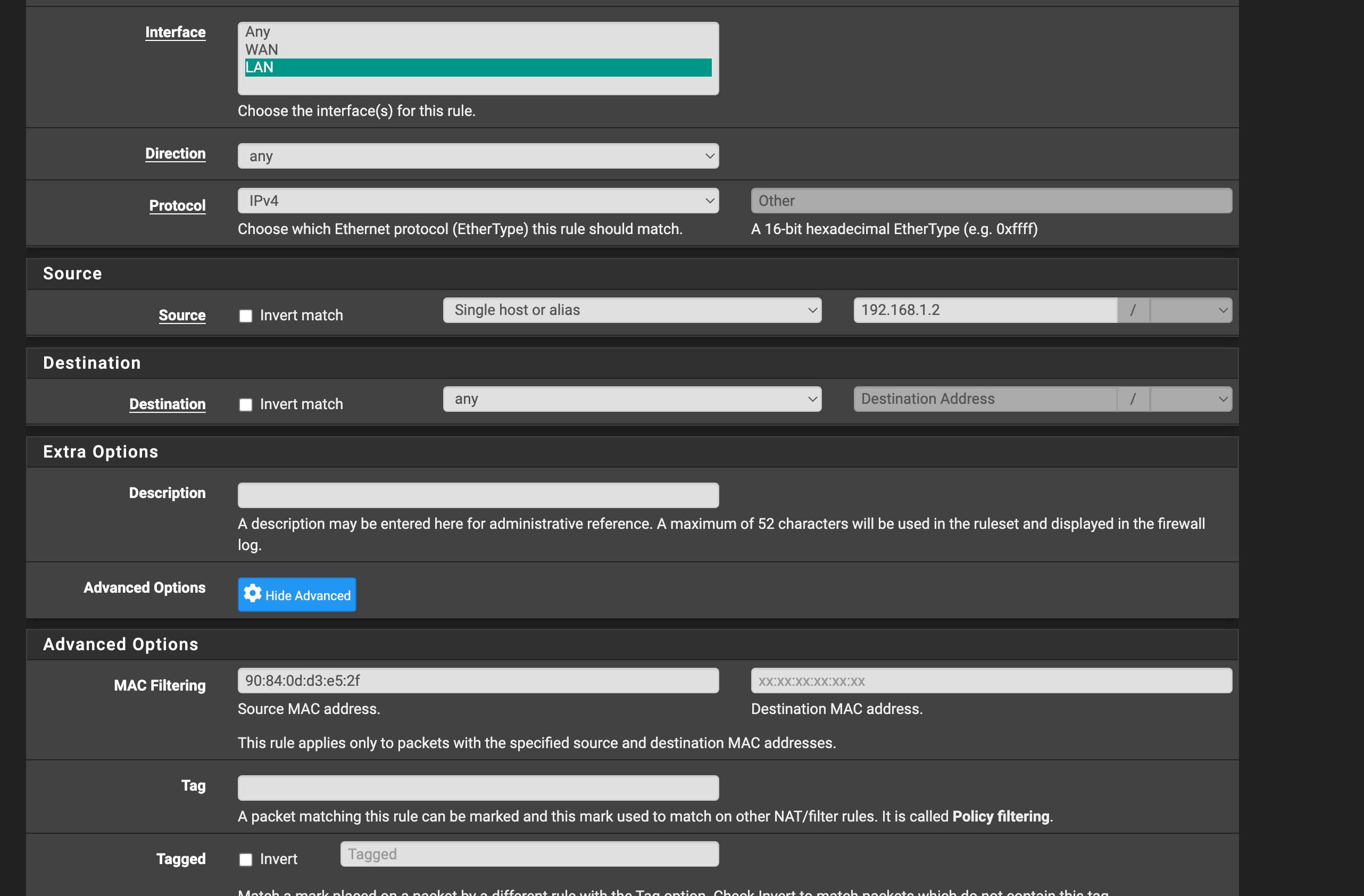
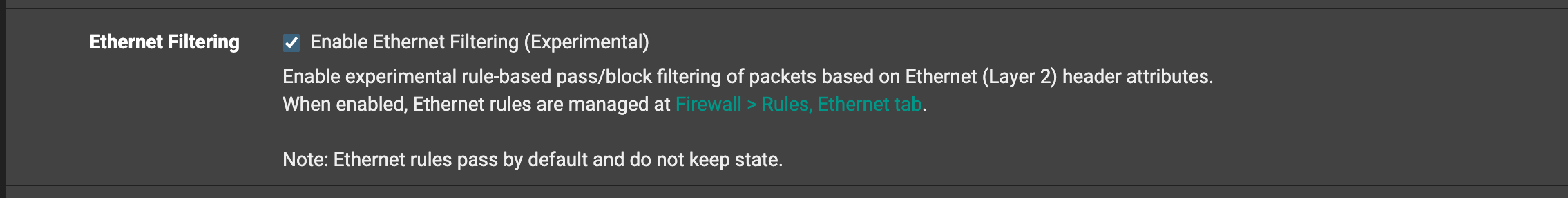
I have started to implement the Experimental Layer 2 Access control lists. However, it does not allow an input for an Alias for a bulk set of Mac addresses. I had to do them each one at a time.
Tell me what you think as this is experimental at this time with 23.05
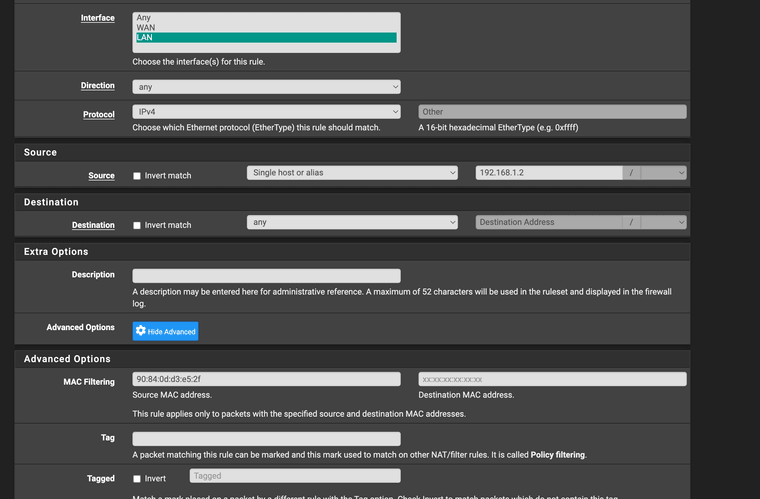
(Rule with Layer 2 options missing Mac Alias sets manual entry)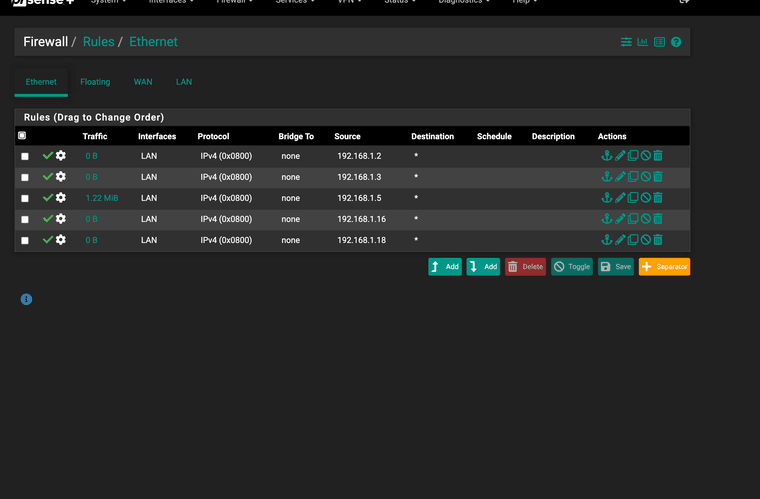
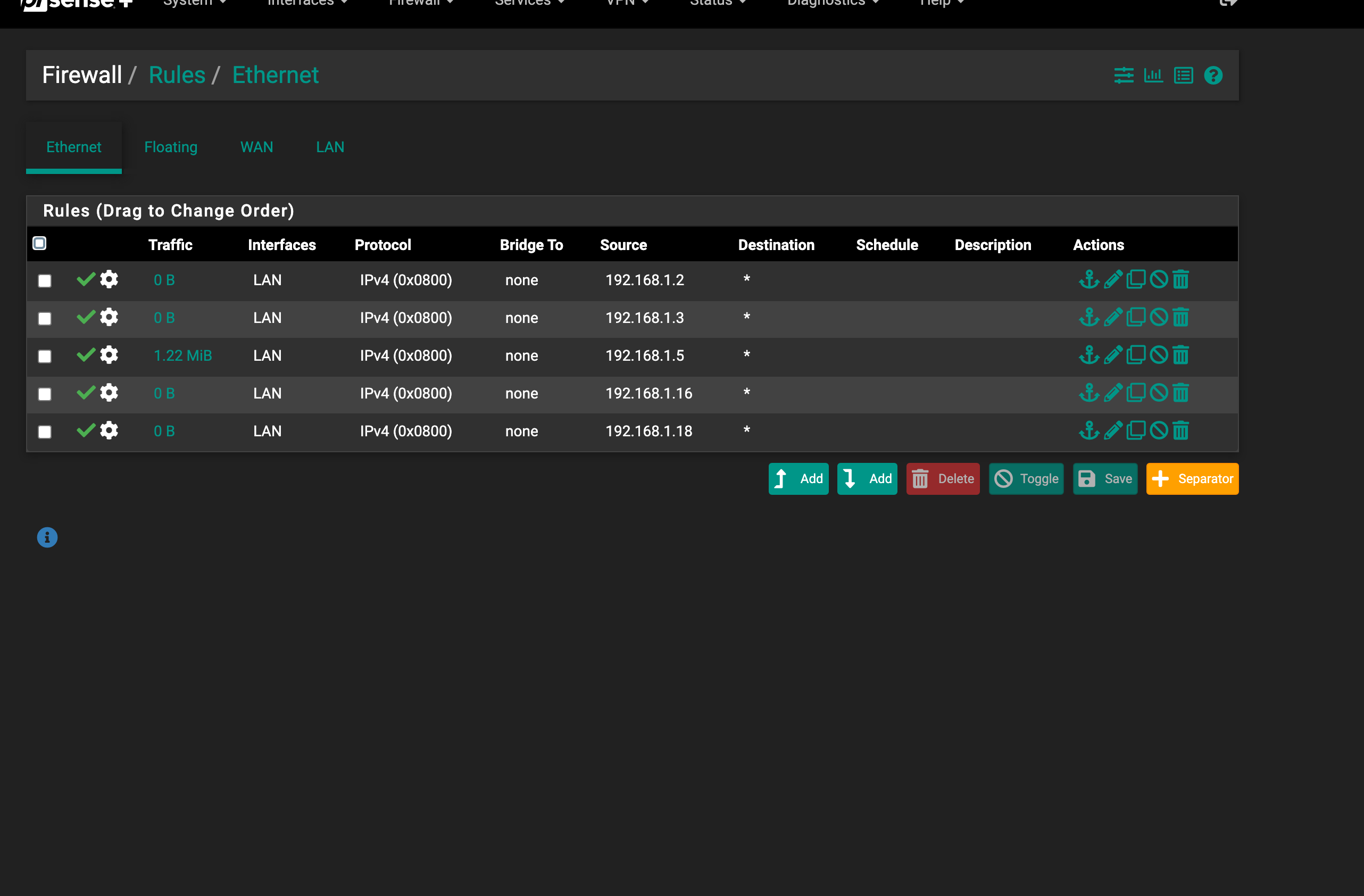
(I have attempted to create a default block "all" however, traffic is blocked stopped even with an ordered approve list)Traffic is being passed. However I want to create a rule that blocks all non approved mac addresses. Everytime I create a list and after create a default block all traffic stops with the default block. It locks me out of the GUI also.
I really don't want to create multiple rules for each ip and mac address one for ARP and one for ipV4 how can i also select both protocols without using any?
-
-
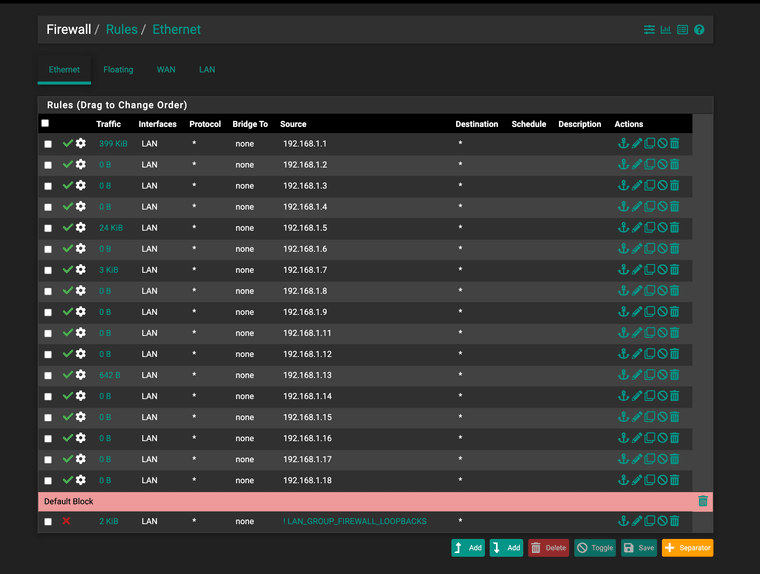
Each Rule is set with a source MAC that matches the IPDefault block all is inverted to an alias
WARNING This locked me out
-
Per Netgate Docs:
"If an administrator wants to block all L2 traffic by default, they can first craft a ruleset with appropriate pass rules and then follow that with a rule to block any other Ethernet traffic. As the potential for mistakes and disruption is extremely high, this is not considered a best practice at this time."
Every configuration I have attempted locked me out I would have to use the console log in to fix it. If I leave the blocks off it works. Or if I just block ipv4 all.
!!!!! WARNING THERE IS POTENTIAL FOR MAJOR ISSUES. SO TESTING THIS OUT CAN AND WILL LOCK YOU OUT OF WEB GUI !!!!
I have been locked out 5 times today and had to log in with the console cable for fix it.
-
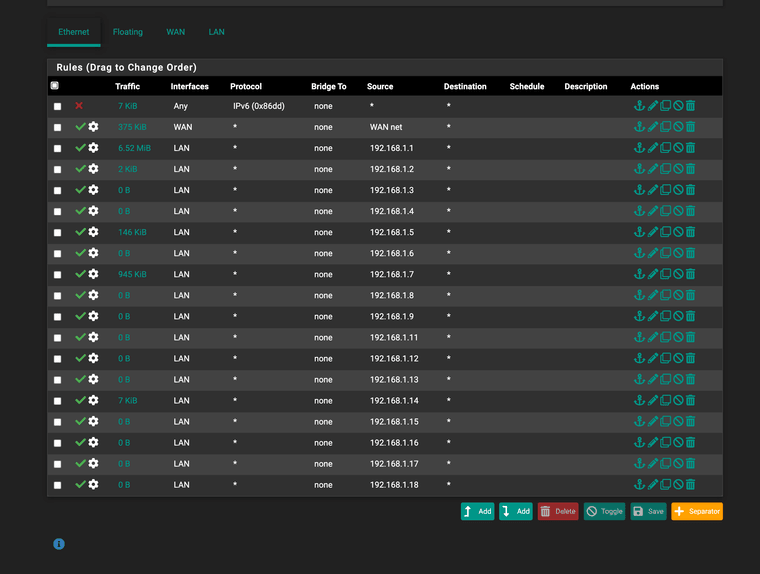
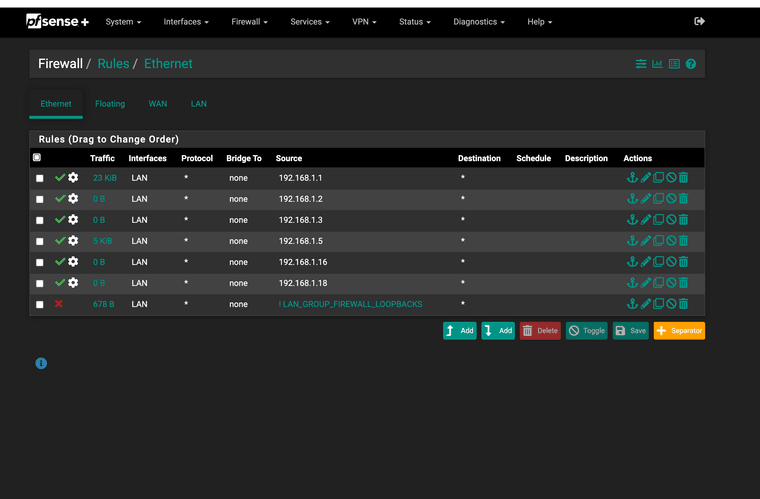
(Blocked IPV6 as my ISP does not hand out IPV6 addresses only IPv4)Per Netgate docs
"Ethernet rules can use Aliases for L3 source/destination matching but there is no support for MAC Address aliases at this time."This works and shows traffic. Each IP has its MAC recorded into the rule.
Working config, Squid, Squidguard, Snort, Lightsquid, Auth-NTP, DNS over port 853, Clam-AV, UpNp for xbox alongside floating Queue CODEL this is functional and other ACLs are still working with this version. I have set the top line to block out all IPV6
Test now running for 24 hours no issues.
-
 J JonathanLee referenced this topic on
J JonathanLee referenced this topic on