Site-to-Site OpenVPN Problem on 2.7.0
-
Just adding my 2 cents here, I am also having issues with OpenVPN since the upgrade to 2.70.
Pfsense is configured as the OpenVPN server, after the upgrade to 2.70 my LAN clients (192.168.0.1/24) on the Pfsense side could not trace or ping anything to the client side anymore
So I deleted the Pfsense OpenVPN server config and then followed this guide and set it all up from scratch, but I still have the same issue :-
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html
The OpenVPN client establishes the tunnel to Pfsense, Pfsense FW can ping all clients on the remote client subnet (192.168.8.0/24) and the remote firewall on the client side can ping all hosts on the Pfsense LAN (192.168.0.1/24) including the Pfsense FW
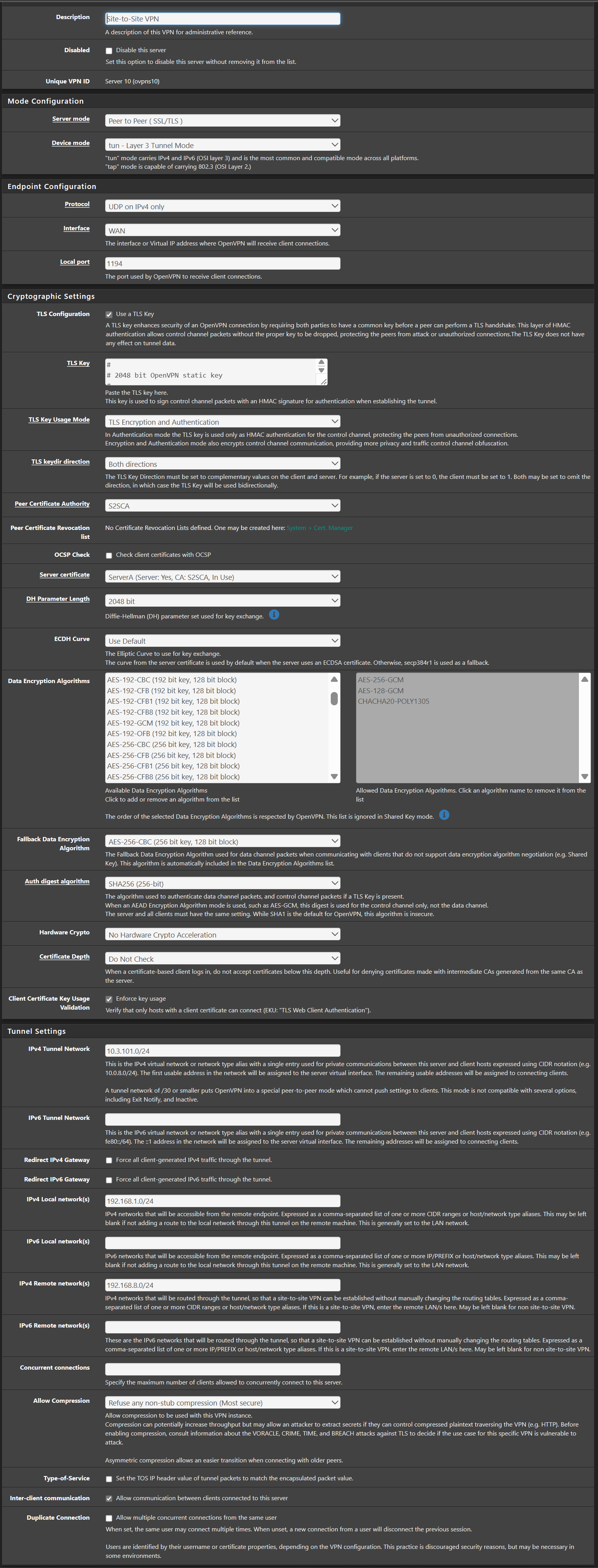
Tunnel :-
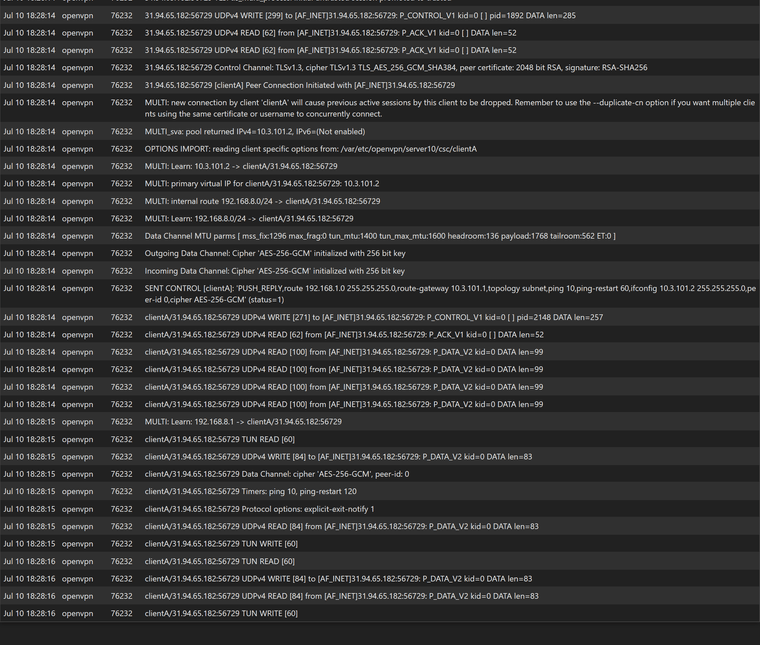
OpenVPN logs :-
All I see in regards to ICMP from 192.168.1.11 to 192.168.8.0 when pinging from the Pfsense client side in states is :-

The Firewall and NAT rules are also setup as per the linked document above.
-
I moved this to another thread because that other thread isn't the place to add on new potentially unrelated issues even if the symptoms seem similar.
-
- Look under Diagnostics > Routes and:
- Make sure there is a default route for IPv4
- See what the entry for
192.168.8.0/24looks like. Is it pointing to the correct OpenVPN interface/address?
- Make sure you do not have any routes for
192.168.8.0/24under System > Routing, Routes tab - Try a ping from the firewall itself using the LAN for the source
- Check the LAN rules, make sure the client on LAN isn't hitting a rule with a gateway set
- Look under Diagnostics > Routes and:
-
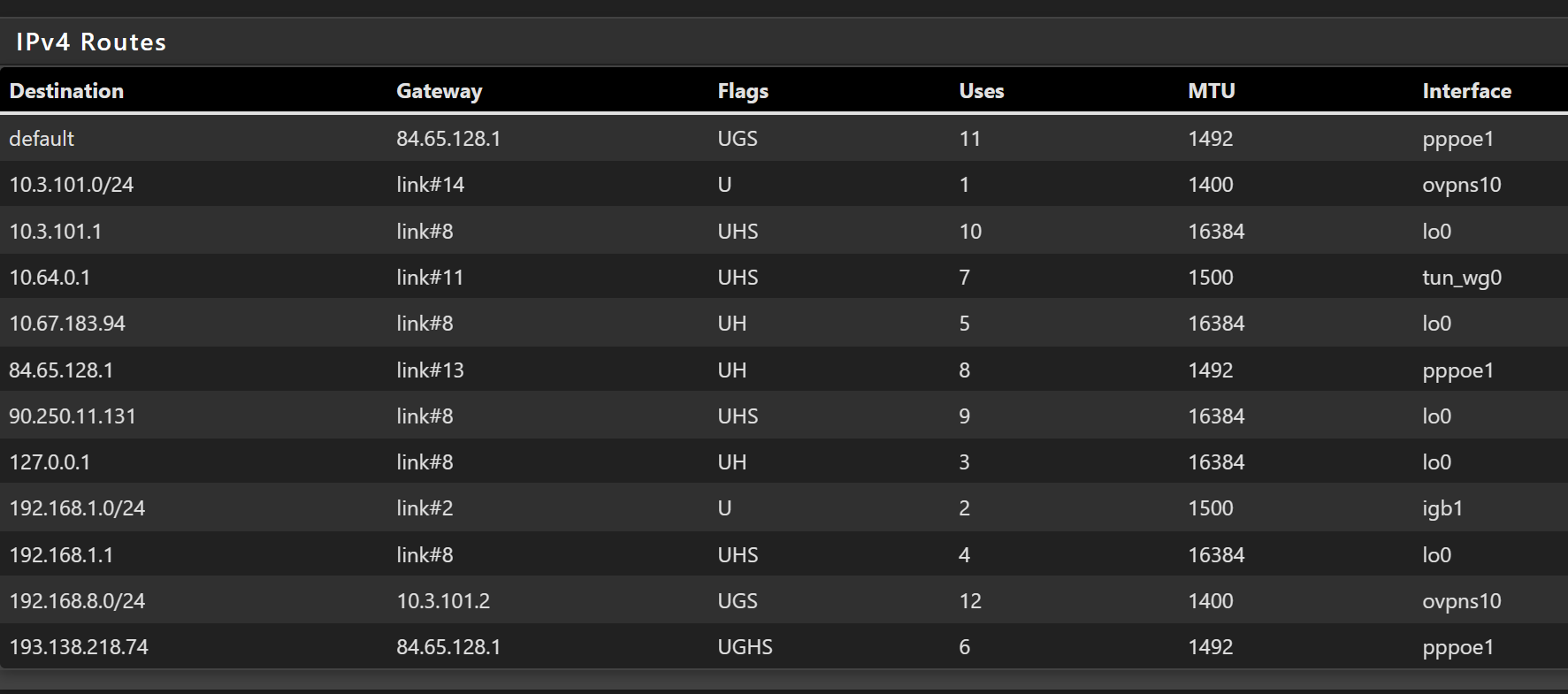
IPV4 routes, ovpns10 is the correct interface and there is a default route :-
System /Routing / Static Routes :-
Ping from LAN :-
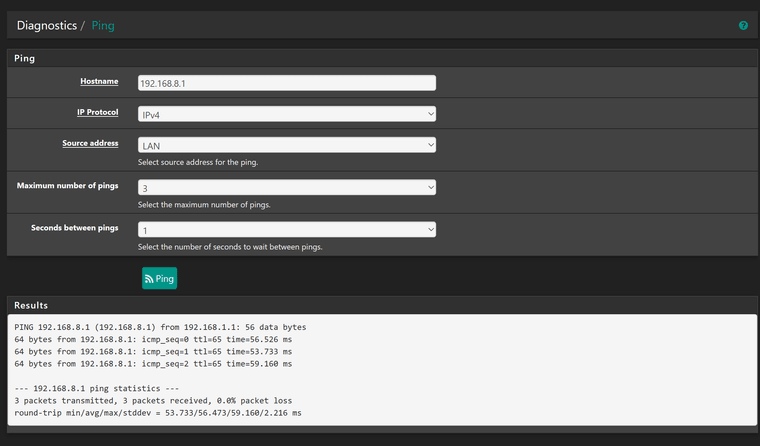
So I guess, last thing to check is the LAN rules
-
@Doody
Change the tunnel subnet mask to /30 in the server settings if you need only one client to connect, otherwise configure a CSO for each. -
@viragomann said in Site-to-Site OpenVPN Problem on 2.7.0:
@Doody
Change the tunnel subnet mask to /30 in the server settings if you need only one client to connect, otherwise configure a CSO for each.No, don't do that. OpenVPN is neglecting that code path so it may stop working in the future. Stick with SSL/TLS and overrides.
-
@jimp
So in future you need to configure a CSO for each single site to site? -
@viragomann said in Site-to-Site OpenVPN Problem on 2.7.0:
@jimp
So in future you need to configure a CSO for each single site to site?That seems to be the way they're pushing people upstream. Though you can also use TAP mode in certain cases if you want to use things like routing protocols.
With DCO mode on Plus you can use traditional routing because of the way it's hooked into the kernel. It works more like a regular interface there instead of only using OpenVPN's internal routing.
But for plain site-to-site setups with OpenVPN they really want people using the client/server/override model.
-
With DCO mode on Plus you can use traditional routing because of the way it's hooked into the kernel. It works more like a regular interface there instead of only using OpenVPN's internal routing.