Problem Captive Portal pfSense 2.7 with allowed ip addresses
-
After upgrading to pfSense 2.7 the captive portal no longer manages the ip addresses entered in the submenu IP ADDRESSES ALLOWED, finding me the login page for authentication even to the ip that I would not want. With version 2.6 of pfSense it worked perfectly. Did anyone have the same problem and solved it?
-
In the 2.7 release notes, What does "Captive Portal has been migrated from IPFW to PF" mean?
-
@TheBigWizard said in Problem Captive Portal pfSense 2.7 with allowed ip addresses:
What does "Captive Portal has been migrated from IPFW to PF" mean
Read a couple of links shown here : pfSense ipfw to pf.
pf, the native pfSense firewall, couldn't handle MAC addresses, or the captive portal needs this functionality. So, the other FreeBSD firewall, was used.
Netgate has modified pf upstream, so it could also handle MAC addresses. So, from now on, only pf is used, ipfw isn't needed anymore.
There is more then only "handle MAC addresses" of course.Btw : I'm using 23.05.1, comparable to 2.7.0 and IP ADDRESSES ALLOWED works fine for me.
-
@Gertjan So, now to make "IP ADDRESSES ALLOWED" work in Captive Portal, how can I do?
-
@TheBigWizard
i am wonder if there is a way to add this rules (allowed ip address ) in CLI mode,
like easyrule
i can't find any user interface to manage the Pf and pfctrl is limited to some functionality
??
we must wait for any patch or any update or we must use another firewall like OPNsense -
@bendida
Having pfSense in production, replacement is not easy. And anyway I would replace it with pfSense 2.6 .
As mentioned by @Gertjan , with pfSense+ 23.05.1 the Captive Portal with IP ADDRESSES ALLOWED works without problems. I could use the commercial version or go back to 2.6 .Are there other solutions?
-
@TheBigWizard
Using 23.05.1, and IMHO, 2.7.0 should / would be the same.
I added an IP to the list : 192.168.2.6 - my phone.
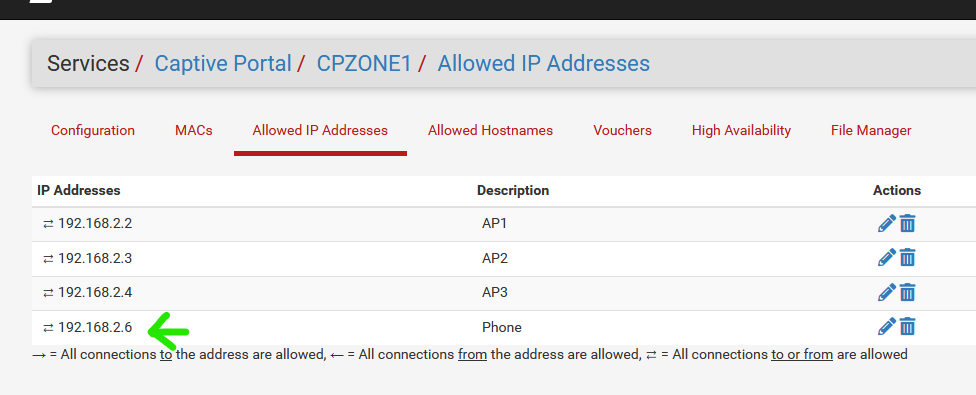
Take note of the first 3 devices 192.168.2.2 to 192.168.2.4 : these are my access points for my captive portal.
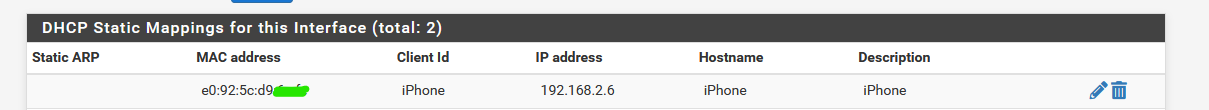
To make sure my phone using this IP, and without modifying my phone, I've set up a MAC Lease on the captive portal DHCP server :
I activated the SSID of my captive portal.
My phone got the good, 192.168.2.6 IP (and correct DNS, gateway etc) :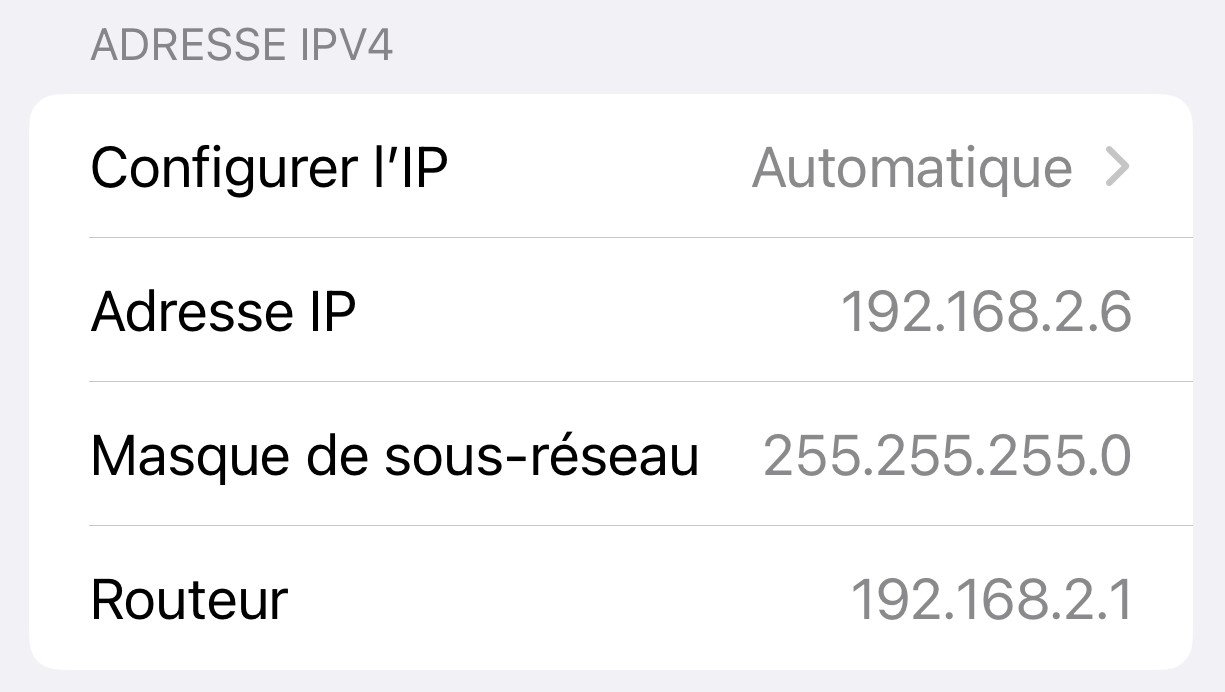
Let's check the firewall :
[23.05.1-RELEASE][root@pfSense.bhf.net]/root: pfSsh.php playback pfanchordrill ...... cpzoneid_2_allowedhosts rules/nat contents: cpzoneid_2_allowedhosts/192.168.2.2_32 rules/nat contents: ether pass in quick proto 0x0800 l3 from any to 192.168.2.2 tag cpzoneid_2_auth dnpipe 2000 ether pass in quick proto 0x0800 l3 from 192.168.2.2 to any tag cpzoneid_2_auth dnpipe 2001 cpzoneid_2_allowedhosts/192.168.2.3_32 rules/nat contents: ether pass in quick proto 0x0800 l3 from any to 192.168.2.3 tag cpzoneid_2_auth dnpipe 2002 ether pass in quick proto 0x0800 l3 from 192.168.2.3 to any tag cpzoneid_2_auth dnpipe 2003 cpzoneid_2_allowedhosts/192.168.2.4_32 rules/nat contents: ether pass in quick proto 0x0800 l3 from any to 192.168.2.4 tag cpzoneid_2_auth dnpipe 2004 ether pass in quick proto 0x0800 l3 from 192.168.2.4 to any tag cpzoneid_2_auth dnpipe 2005 cpzoneid_2_allowedhosts/192.168.2.6_32 rules/nat contents: ether pass in quick proto 0x0800 l3 from any to 192.168.2.6 tag cpzoneid_2_auth dnpipe 2008 ether pass in quick proto 0x0800 l3 from 192.168.2.6 to any tag cpzoneid_2_auth dnpipe 2009 cpzoneid_2_auth rules/nat contents: cpzoneid_2_auth/192.168.2.85_32 rules/nat contents: ether pass in quick proto 0x0800 from 92:63:2b:ed:13:1c l3 from 192.168.2.85 to any tag cpzoneid_2_auth dnpipe 2006 ether pass out quick proto 0x0800 to 92:63:2b:ed:13:1c l3 from any to 192.168.2.85 tag cpzoneid_2_auth dnpipe 2007The line mentionning "192.168.2.6_32" indicates that it i part of the cpzoneid_2_allowedhosts anchor : these 4 IPs are passing through.
The last set mentioning "192.168.2.85_32" is a classic logged in, connected portal user.I did not have saw the captive portal login page.
-
@Gertjan
It works for you. For me after upgrading to 2.7 it no longer works. I can not figure out if it was a decision of the developers or a bug of 2.7. Is there a way to report this? -
@TheBigWizard said in Problem Captive Portal pfSense 2.7 with allowed ip addresses:
Is there a way to report this?
Developers won't show there nose because someone said : "it doesn't work".
Start giving details.For example :
pfSsh.php playback pfanchordrillHow did you set up your portal ?
Btw : I'm using the portal right now, on 23.05.1 which has the same code base as 2.7.0.
When I have some time, I fire up a dedicated device with 2.7.0.edit : Knows issues and bugs where the last one to date is 'BS' (IMHO) and the before last is already resolved (see this forum).
-
@Gertjan Thanks, let me know how your test with 2.7 goes.
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
@Gertjan
hello, have you tested pfSense 2.7 ? -
@TheBigWizard said in Problem Captive Portal pfSense 2.7 with allowed ip addresses:
@Gertjan
hello, have you tested pfSense 2.7 ?Noop.
Haven't been able to go home yet (working for a hotel, it's high season and all that).But : follow also this : Captive Portal NOT working in 2.7.0 thread.
It was resolved (The portal works after all) and asked a favor back : check "allowed IP addresses" please, as the test take a minute or two.I've compared the 'code' between 2.7.0 and my 23.05.1 as I'm using it right now.
It's identical**, so I'll motivate you : Only our "local settings differ".** not the kernel - I presume the embedded name is different.
-
@Gertjan Thanks!
-
It has been tested : see here, the last two posts Captive Portal NOT working in 2.7.0
Allowed IP working and does not show up under Captive Portal since it's a bypass.
-
same problem
Install version 2.7.0: new disk + import config from 2.5.2
Enabled services: DNS Resolver, Captive Portal, OpenVPN server, ntpd
Installed Packages: pfBlockerNG-devel (3.2.0_6), haproxy (0.63_1)
Others: DHCP, DNS (with forward to firewall) on domain controllerIPs from Captive portal’s Allowed IP Address List not have access with no authentication, but if add MAC of IP to "MAC Address Control" pass without requiring authentication.
PS: This configuration worked fine on version 2.5.2.
-
I reinstalled pfsense 2.6 and configured ldap gsuite. Everything works perfectly. Also "allowed IP addresses" of the captive portal.
-
-
As showed in the other thread I linked above, the "2.7.0" portal works just fine.
Some thoughts though :
if this gets involved :@sanrzn said in Problem Captive Portal pfSense 2.7 with allowed ip addresses:
haproxy (0.63_1)
Others: DHCP, DNS (with forward to firewall) on domain controllerthen the setup will need more attention.
I'm pretty sure that if the classic setup was used : pfSense is the DNS, and handles the DHCP, the portal works.
Now, step by step : remove DHCP, have it being handled by another DHCP server : and test (!) : it can be done. It's a question of the correct 'settings' and all devices/systems involved.
Next step : pfSense isn't handling the DNS anymore on the portal : that can be arranged also.
Another step "domain controller" : ok, why not. Things are getting way more complicated as even more things have to be checked. I never did this myself, but I presume it is possible. -
Hi,
I had the same problem.I found out that switching the Webconfigurator back to english language helps.
pfSense expects to get as direction value either "both", "from" or "to".
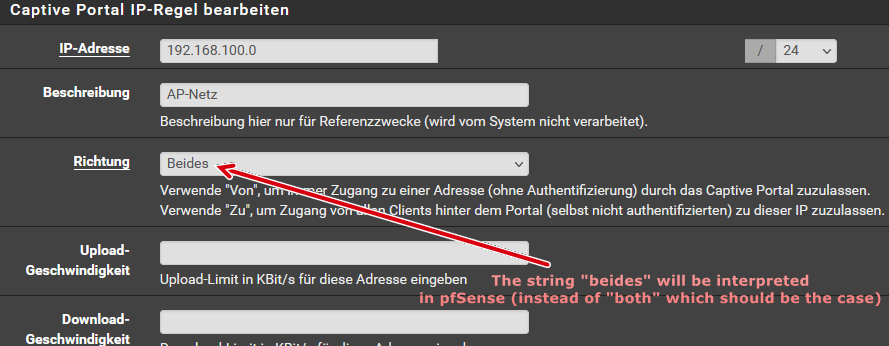 
After switching back to english, you have to edit and save the wrongly saved "Allowed IP address" entries.
Even if I export the configuration (with the german translated WebConfigurator) I found the translated string as value in the config.xml.
HTH
-
@wtasin HI,
so using the English language, does it work?