Captive portal and subnet
-
Hello
Recently i changed from sophos xg310 to pfsense but i have a problem with captive portal so i want to give a propostion and comparaison to this problem :
in sohpos you can apply captive portal in the rules of firewall and the benefit is :
for example i have Lan coming from router
1-172.16.0.0/16 vlan 2
2-192.168.1.0/24 vlan 3
3-192.168.2.0/24 vlan 5
and
pfsense LAN -10.39.39.2/24 routing to 10.39.39.1 in router // static route all vlans (2 3 5) to 10.39.39.1in the rule you can specify the subnet like pfsense source and the you choose aliases but in sophos you can use this rule and checked it if you want to apply a captive portal
but in pfsense yo can't : you have to go captive portal and then choose interface LAN in my case then you can't select the subnet to apply captive portal in my case i want to apply on 172.16.0.0 only .
so we need to add this option in the rule of firewall to give more flexibility . is there a way to modify the code source .
-
@mohie25 said in Captive portal and subnet:
routing to 10.39.39.1
WAN is attached to 10.39.39.1 and LAN is 10.39.39.2/24 ? ( ? )@mohie25 said in Captive portal and subnet:
you have to go captive portal and then choose interface LAN
Humm. I wouldn't advice to use LAN as a captive portal. Keep LAN as a LAN, the network for trusted devices, or at least your 'PC' which you use to admin everything.
Use other, OPTx networks, trusted or not, as auxiliary networks, like the captive portal.@mohie25 said in Captive portal and subnet:
can't select the subnet
The captive portal will use the selected network. Adapt the network ?
-
Wan is attached to pfsense in opt0
Router(Switch L3 Alcatel) --10.39.39.1/24 | | pfsense ( Lan 10.39.39.2/24 opt1 ) (opt0 Internet modem) Add Gateway in pfsense 10.39.39.1 Static Route | | -> 172.16.0.0/16 to 10.39.39.1 -> 192.168.1.0/24 to 10.39.39.1 -> 192.168.2.0/24 to 10.39.39.1---------------------------------Rule on Lan
allow any to any .
-------------------------------every thing work now and all networks work
---------------Captive portal on 172.16.0.0/16 i want to apply captive portal only on this subnet :
-------------> the problem that we have only one interface Lan (the link between switch L3 and Pfsense ) and when we apply this interface on Lan all subnet users will require user name and password.-------------------in sophos firewall they add option in firewall rule is when apply a rule you can choose to apply a captive portal or no and this is what i want now.
cause pfsense in rule can select the subnet easily from source . -
WAN is OPT0 - why not the WAN interface ?
Captive portal on 172.16.0.0/16 = 65534 possibles portal devices ? - Ok, why not.
The pfSense implementation of a portal is : the (dedicated) interface. Carving out a portion for usages is .... IMHO, not possible.
Because you already have a beefy installation, as it has to support to up to 65K users, adding an interfaces seems the most obvious choice.
Also, a portal network is a very not trusted network. A LAN could be a trusted network. Again, IMHO, better to separate these two.Take note : I'm just another portal user.
-
I know this is old, but perhaps my solution will help. Use a two or more router setup, with both subnets using pfsense. Enable on the untrusted subnet, the captive portal. I struggled with the same thing, until I came to that concluion. I just purchased my devices, and will set them up later.
-
@des000
i can't understand your solution, could you please explain more or draw a schema .. -
I'll try to do a diagram:
[Internet] | | [Router1] | | [Switch] | | [Router2]That's a wiring diagram of it. The switch inbetween, from experience, is very important. Clients can be behind either router. I'm working on implementing mine soon, so I can probably tell you what options to set in second router pretty soon. However, I'm hearing that with pfsense, there CAN BE weird stuff going on when you do it. But I hope not.
-
@des000 said in Captive portal and subnet:
However, I'm hearing that with pfsense ....
Don't listen to them. Better yet : consider to tune in somewhere else ;)
The entire Internet is a 'router' chained to a 'router', that's how things work.
Administrating a router after a router (pfSEnse) can be done. Not an issue at all.
The other way around :
Administrating a router (pfSense) after a router (ISP) can be done. Not an issue at all. That's actually what happens out there in most of all cases.BUT : - as there is one -
Do not use a router on the interface you've declared "a captive portal".After your [Switch], you are 'allowed' to put devices like Access Points (not running in router mode

 ) or directly portal client devices.
) or directly portal client devices.
Ones done that, it will work. -
@Gertjan In my new design, I really want to transform dd-wrt into an ap, one way or another and in ONE subnet, enable captive portal. If NOT for that, I probably would stick with 1 pfsense box. I can always add siwitch inbetween with new design. But I probably DO want my guest subnet to have captive portal. However, I'll just try my way, and hope it works. I can troubleshoot, if not. I was going to ignore them and try anyway, anyway...
-
@des000 said in Captive portal and subnet:
want to transform dd-wrt into an ap
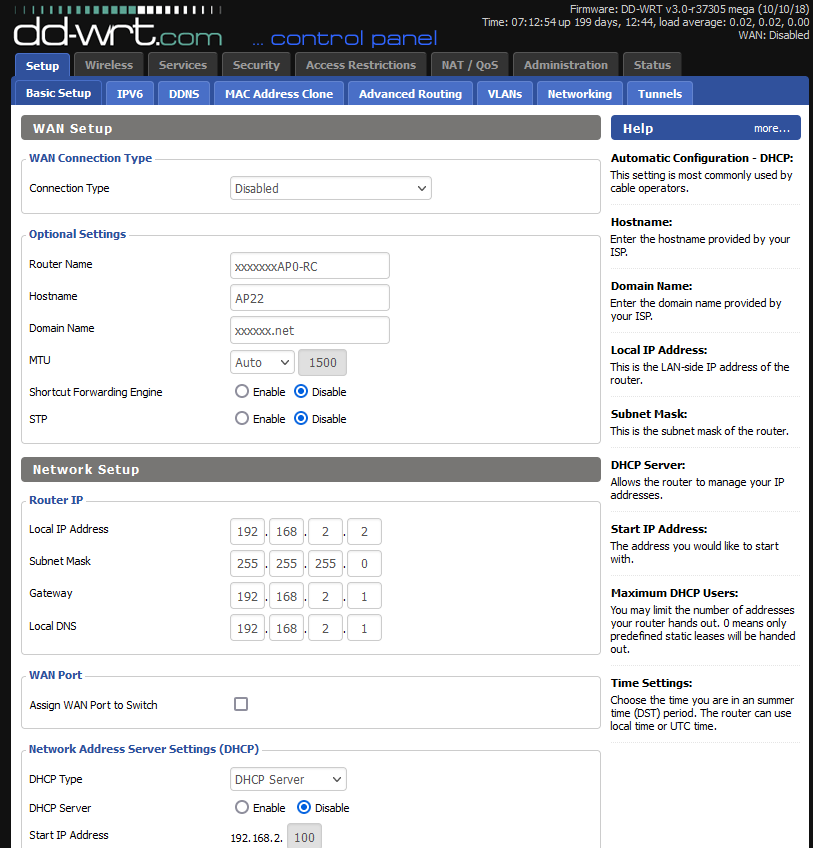
Disable WAN.
Give it a static IP, like 192.168.2.2 / 24
Gateway and DNS is 192.168.2.1 - my captive portal pfSense interface.
Shut down the DHCP server.
You might even assign the WAN port as anther LAN port, if needed.I've 4 of these (192.168.2.2 -> 192.168.2.6)
Btw : Wifi network security :
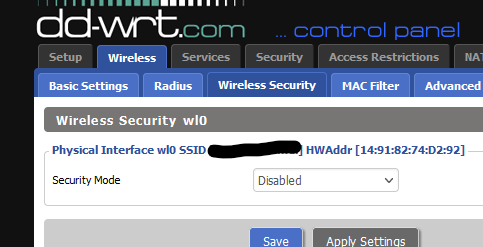
Pretty rock solid.