Help understanding DNSBL alerts
-
Hello all,
I just installed the PfBlockerNG package yesterday, ie:DNSBL lists. I then went on the internet to see how well the Ad blocking was working, I only visited one site.
Since then, some of the alerts I've received are confusing to say the least. Can someone with a lot of experience with these alerts take a look at them and help me understand what I am looking at? Many thanks!
-
@Rogerthat said in Help understanding DNSBL alerts:
confusing
When you decide to use a list/feed like this :
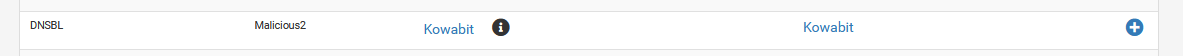
the idea is that you hover your mouse over the black round I after Kowabit.
It says "Contains false positives!".
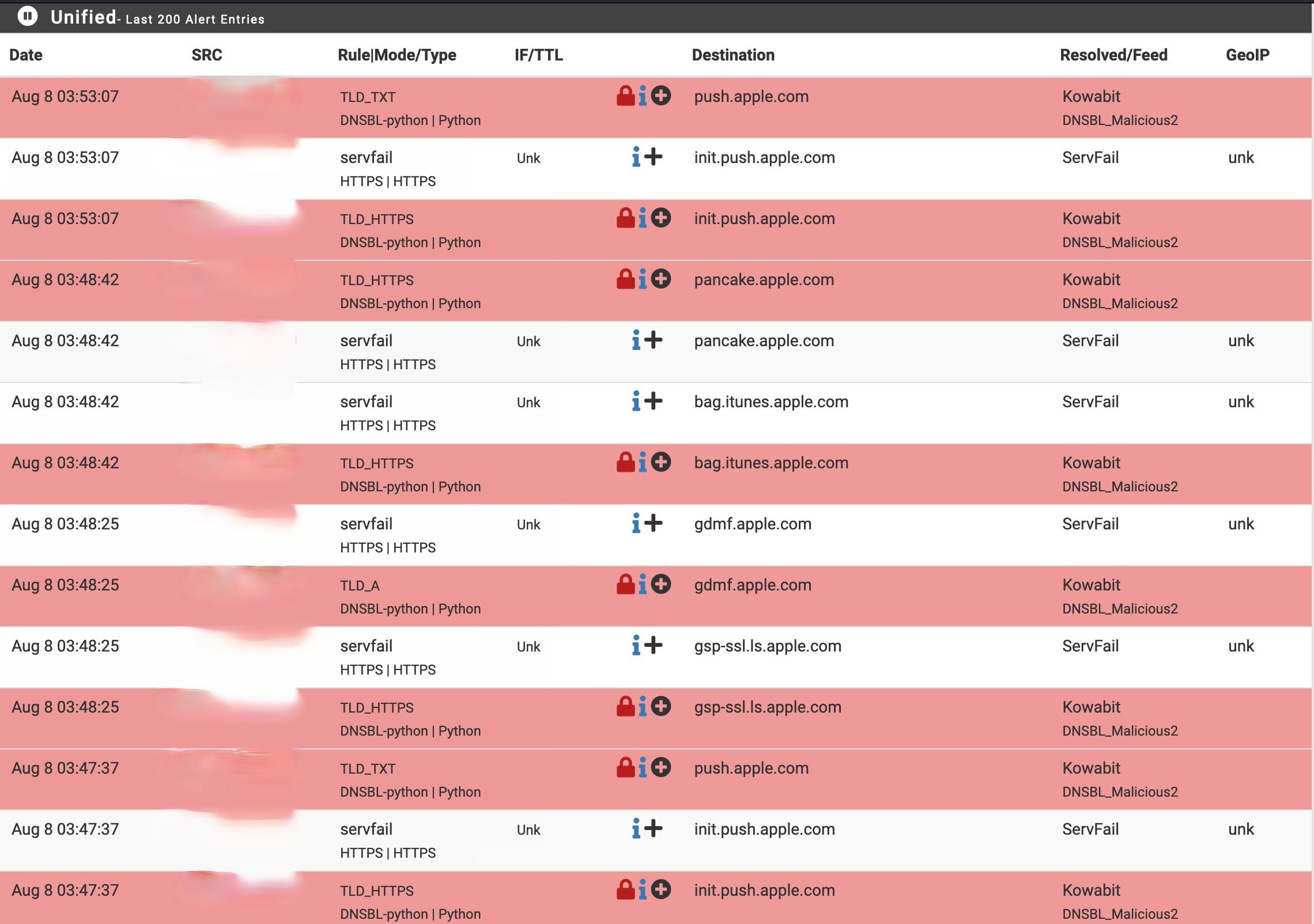
You've found that this warning is correct. This list seems to contain *.apple.com
An now you want to visit something from *.apple.com.
Red hail "alert" storm guaranteed.My advise : when you download a feeds, you will have the URL.
Copy the URL to a browser, open it, and ... yes ! read it !! (before using it). When you find plenty of apple.com, microsoft.com, youtube.com google.com etc and you don't want to do anything with these guys, then the list is for good you.
If not, ditch the list/feeds, or start whitelisting a lot, and check very often for false positives etc. -
@Gertjan thanks for replying, and the advice for picking out future lists/feeds.
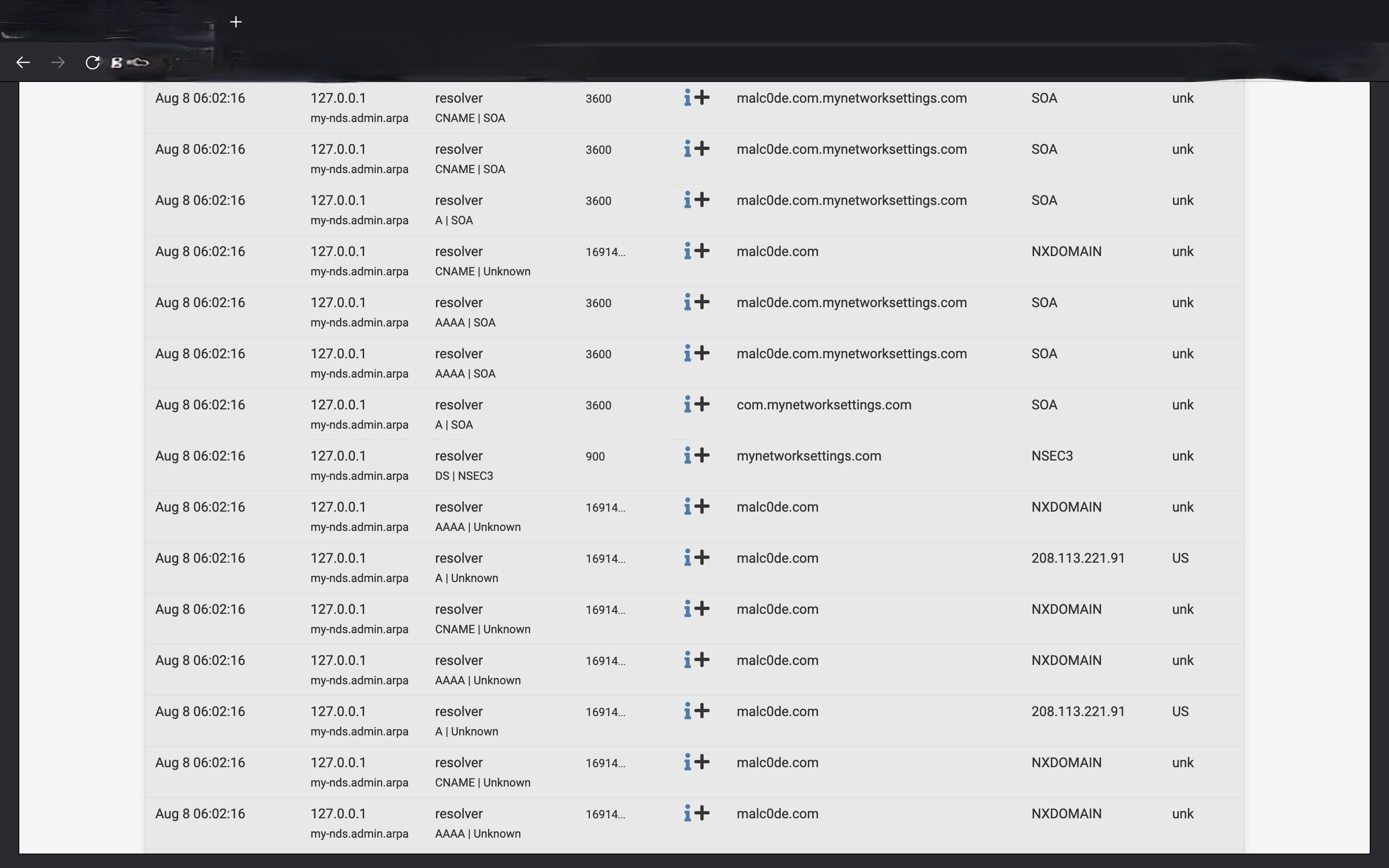
But what about the 2nd screenshot in mostly grey. While there are no red alerts, there are several entries referencing the website for my ISP Admin page, which I absolutely have not accessed from my network in pfsense. So what exactly are the Malc0de entries trying to tell me? Did something from mynetworksettings dot com try to access pfsense?
-
@Rogerthat said in Help understanding DNSBL alerts:
Did something from mynetworksettings dot com try to access pfsense?
Look at your WAN firewall rules : can traffic come in ?
Probably not.
So even if they are really trying, you won't be able to see it.When you see this :

You can see from where the request came from.
If below 127.0.0.1 you see : pfsense, then it's pfsense itself or unbound (because I auto refresh everything that's in the unbound dns cache)
Or for example "gauche2", a LAN PC, doing its Windows update thing.In your case, the request came from "my-dns.admin.arpa"
Btw : the log you showed is the one that shows the request, request type, source, etc etc with the result or unk for unknown = no answer.
-
@Gertjan Ok, thank you for the explanation. But how to make pfsense stop sending these requests? Clearing a cache?
-
@Rogerthat said in Help understanding DNSBL alerts:
But how to make pfsense stop sending these requests? Clearing a cache?
By disconnection the LAN interface.
Devices on LAN won't ask pfSense (unbound) to do resolving, so unbound stops resolving.
.... ok ... sorry. Had to say it.
Unbound does nothing if it isn't ask to do something. The ones asking it to do something are ... your LAN devices.But there is more.
If you checked this option :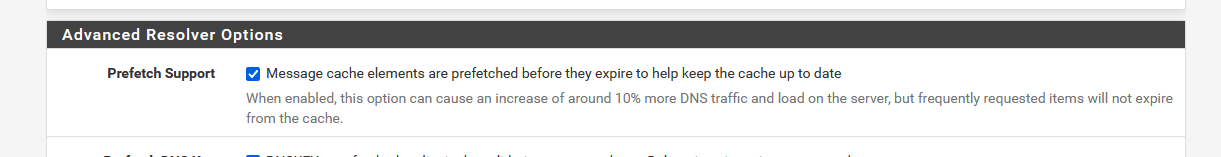
then ubound will resolve again - all by itself - any host name that have their TTL approaching zero.
Normally, this is a good thing to do, as an initial request involves a lookup, and any further requests for the same host name will get served out of the cache, always "fresh".Also, pfSense has also work for unbound : any Netgate 'related host names for the checkup if updates are available. These lookups are actualy very minimal.
And pfSense is sure enough not looking for malcode.com. or malcode.com.mynetworksettings.com. -
@Gertjan Ok, so I am just confused as to why my device would be sending these requests when I connect to the LAN interface, if I am not actually trying to reach those domains? Will unchecking the box you pictured above, stop it from doing that?
-
@Rogerthat said in Help understanding DNSBL alerts:
so I am just confused as to why my device would be sending these requests when I connect to the LAN interface, if I am not actually trying to reach those domains?
Not you as a person.
But, for example, if you are using a Windows PC or modern handheld device as a smartphone, hundreds of tasks running right now are communication with something somewhere on the Internet.
"Doing there things".
These processes uses host names that have to be resolved first.
That are the host names you saw in your Unified log.
If you want to know what is actually going on, that you should take a look at every process on your system, and checking with whatever means you have to see what it is doing.@Rogerthat said in Help understanding DNSBL alerts:
Will unchecking the box you pictured above, stop it from doing that?
That option will keep already lookup up host name up to date in the unbound DNS resolver cache.
If a domain xxxx.tld is in the cache, that is because your LAN device has asked for it.