SSL cert with purchased domain name
-
Hi, I have purchased a domain name (let’s pretend it’s abc.net) I followed the steps to setup acme cert. however when I login to pfsense firewall gui, it gives me the msg connection not secured Can someone pls guide me on this? Theee is no error if I use self signed cert.
Followed but did not setup haproxy: https://jarrodstech.net/how-to-pfsense-haproxy-setup-with-acme-certificate-and-cloudflare-dns-api/
-
@unraveller349 said in SSL cert with purchased domain name:
(let’s pretend it’s abc.net) I followed the steps to setup acme cert
In System > Certificate Manager > Certificates the certificate obtained from Letsencrypt shows up :
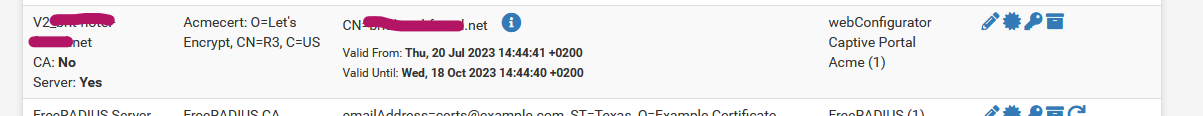
I use this certificate for the pfSense GUI (webConfigurator) as indicated.
I never bothered to change the default TLS port number 443 :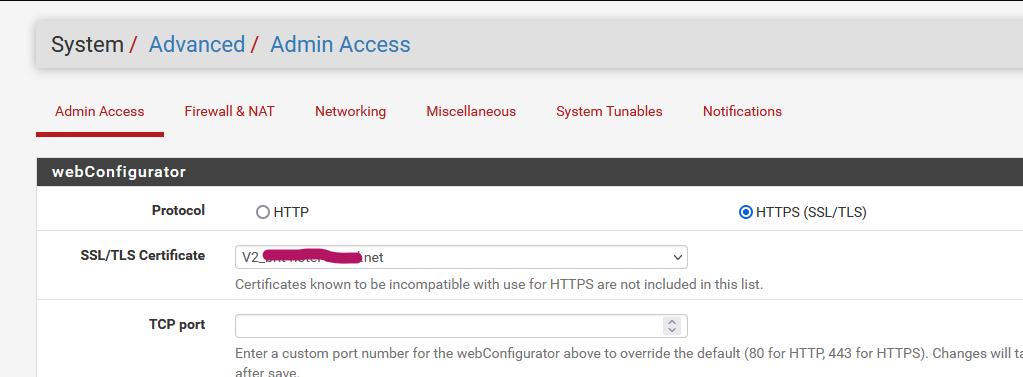
so 'https' selected means : use port 443, which is the default browser's https port.
You've selected the certificate obtained by acme / Letsencrypt ?acme needs a "method" so you can proof to Letsencrypt that 'you' 'own' (actually : rent) the domain name.
I've read the steps, and saw at step 21 :Thats it for the Cert! You now have a certificate for your domain that will auto renew.
That should be it : select this domain for the web configurator, select 'https', save and done.
edit : not sure why HA_Proxy is needed.
These big tutos are nice, but everywhere things evolve constantly. Cloudflaire will change it's procedures, as does acme;sh, as does Letsenecrypt.
If you don't know what and why you are doing things, chances are great that over time it just doesn't work anymore, and that adjustments have to be made. -
@Gertjan did all that but when I login to the firewall gui, it will still say ‘your connection isn’t private. ‘
-
@unraveller349 just to further clarify, it says NET::ERR_CERT_COMMON_Name_invalid
-
Ah, ok.
When you ask for a certicate, like pfsense.abc.net, you have to do this first :
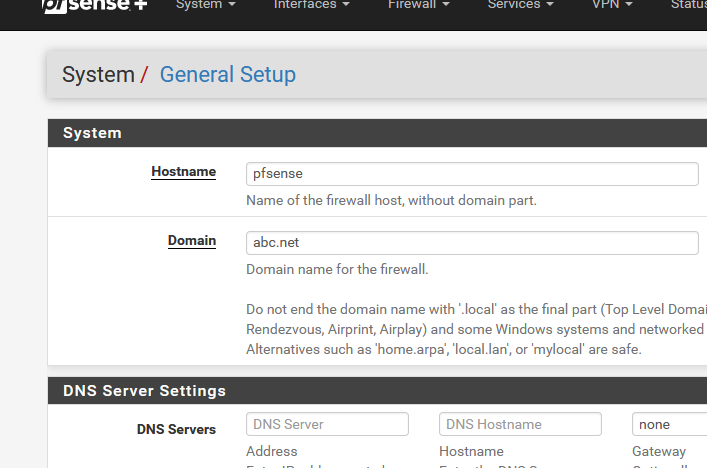
Btw :
You've set this :
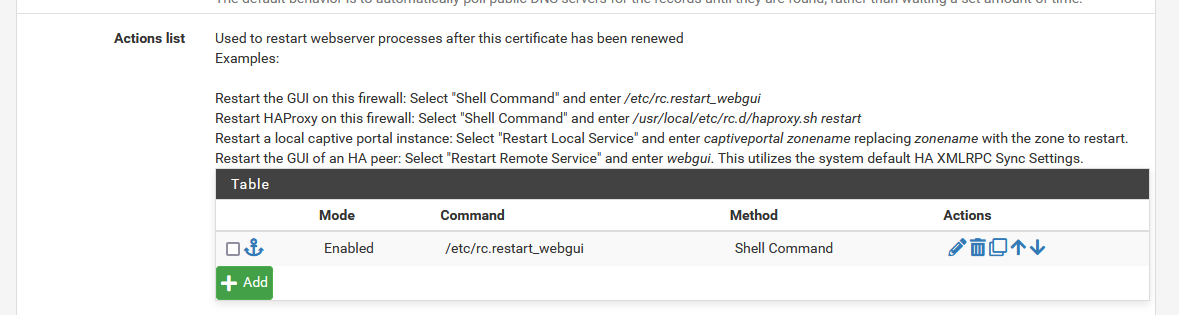
?
If a new certificate was obtained, the webconfigurator has to be restarted so it will use the new certificate. That's what the 'action' is for.In your browser, you should from now on using
https://pfsense.abc.netbecause the browser will first resolve 'pfsense.abc.net", it will obtain the pfSense LAN IP.
Did you check that ?nslookup pfsense.abc.netreturns 192.168.1.1 ? (or whatever your pfSense LAN IP is).
Then it connects to 192.168.1.1, using port 443 (because of https).
The web server, pfSense GUI, will send a certificate over that says : I'm am "pfsense.abc.net" and because the browser was looking for "pfsense.abc.net" everything is fine.If you were using https://192.168.1.1 then the test will fail.
Because "192.168.1.1" isn't part of the name (SAN) of the certificate.