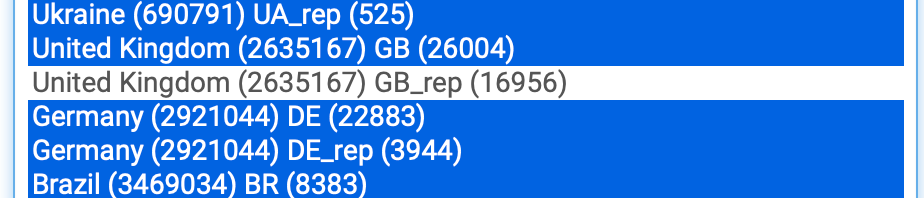
GeoIP "GB_rep_v4.txt" list contains my domain ISP
-
@Cabledude said in GeoIP "GB_rep_v4.txt" list contains my domain ISP:
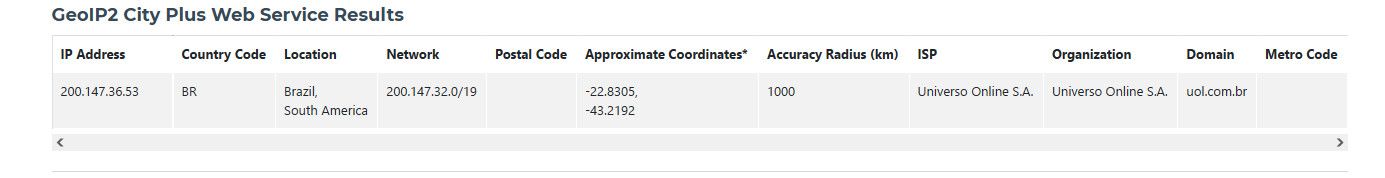
200.147.36.53
now sure where your looking but that is clearly listed as being in BR.
So max mind shows it
https://www.maxmind.com/en/geoip-demo
You can also use ip info as a check
https://ipinfo.io/I then created a br alias, and ran an update and then looked in the table.
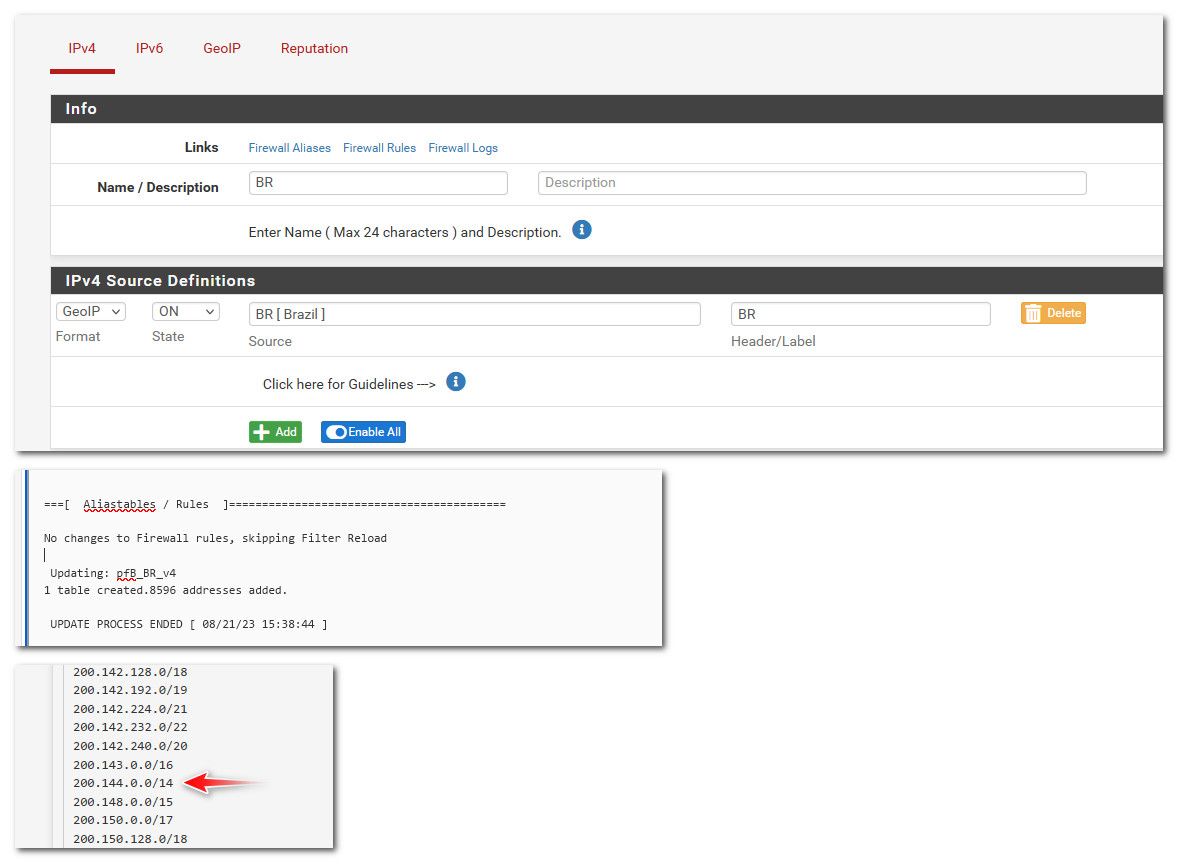
Maybe your confused by it in a /14 that includes that IP.
200.144.0.0/14 would be all of these addresses = 200.144.0.0 - 200.147.255.255
So yes 200.147.36.53 is included
-

You could call your ISP and let them know you need a new IP because your on the blacklist...
-
@johnpoz said in GeoIP "GB_rep_v4.txt" list contains my domain ISP:
Maybe your confused by it in a /14 that includes that IP.
200.144.0.0/14 would be all of these addresses = 200.144.0.0 - 200.147.255.255
Yup that is where I went bad. Thank you for clearing that up.
So the Maxmind BR list does in fact contain this arbitrary test IP and very likely most if not all IP's in Brazil.I was still wondering what the use of these GeoIP lists could be now that it turns out certainly not to be for malicious IP blocking. Then I noticed coincidentally that NtopNG also has a Maxmind GeoIP option, used to visualize the source (coordinates) of logged IP's. So in that use case it's even required to have the database cover the entire country or region.
-
@JonathanLee said in GeoIP "GB_rep_v4.txt" list contains my domain ISP:
You could call your ISP and let them know you need a new IP because your on the blacklist...
Thanks for your reply Jonathan, however above in this topic it is discussed that the Maxmind GeoIP database turns out not to be a blacklist but an all inclusive country IP list, despite the "top spammers" naming.
-
@Cabledude You could use GeoIP for blocking traffic from maybe China. Or allow only your home country to access your own VPN. Endless possibilities...
-
@Cabledude yes Palo Alto firewalls does the same thing, they have full country blocks but it's not under the a spamer branding nameplate. That seems weird to brand it as top spammers. They have a full blocks of IP addresses that are assigned to specific countries. It's weird it's branded as top spammers. I had my android phone end up on a Spamhaus list I just contacted their help desk and they helped me resolve the issue.
-
@Cabledude said in GeoIP "GB_rep_v4.txt" list contains my domain ISP:
I was still wondering what the use of these GeoIP lists
All of them, or ones you create? Those built in ones where you can edit a few to be on or off the list that has all countries in a specific region of the world? I really see no point to those to be honest.
But what is handy with geoip based lists is when you create your own that are allow vs block. I guess you could edit one of those lists, say for me the north america one.. To just include the countries I would want to allow, but the list is still large for all I want to allow is US..
I use geoip list to allow access to my vpn, my plex.. None of my users would be anywhere outside the US, if they are going to travel then they need to let me know so I can add the country they are in to the allow list.
For my plex I currently have family member living in Morocco, so that list has US and Morocco Allowed.. If your coming from france, mexico, China, etc.. then your not accessing my plex server. Ie any IP that is not from US or Morocco is not allowed in the forward to my plex.
You could block the world if you would, but allow list is almost always shorter than block - so just allow what you want, anything that is not specifically allowed is blocked anyway.
Why would you create a list that includes every IP that is not in the UK? When its easier simpler and a much shorter list to just pick the IPs that are in the UK and allow those, vs blocking every other IP.
-
@Cabledude said in GeoIP "GB_rep_v4.txt" list contains my domain ISP:
Would highly recommend adding Spamhaus Zen to your mail server. These are to be used in the Mail server (not pfBlockerNG):
Zen is completely different from DROP. https://www.spamhaus.org/zen/
Traditionally a reverse block list looks up the sending IP to see if it's in the list and if so rejects the message, and the sending server can return the error code to the sender. The policy list for example contains residential DHCP addresses identified by their ISP as not allowed to be a mail server. A web site likely wouldn't want to block all residential IPs."The Spamhaus DROP (Don't Route Or Peer) lists are advisory "drop all traffic" lists, consisting of netblocks that are "hijacked" or leased by professional spam or cyber-crime operations (used for dissemination of malware, trojan downloaders, botnet controllers). The DROP lists are a tiny subset of the SBL, designed for use by firewalls and routing equipment to filter out the malicious traffic from these netblocks."
-
@johnpoz said in GeoIP "GB_rep_v4.txt" list contains my domain ISP:
But what is handy with geoip based lists is when you create your own that are allow vs block. I guess you could edit one of those lists, say for me the north america one.. To just include the countries I would want to allow, but the list is still large for all I want to allow is US..
I use geoip list to allow access to my vpn, my plex.. None of my users would be anywhere outside the US, if they are going to travel then they need to let me know so I can add the country they are in to the allow list.
Thank you for your explanations. Yes I understand Allow some is better than block all but some.
So just to be clear how you implement this... I assume you:
-
go to pfBlocker -> IP -> GeoIP -> North America
-
Edit (pencil on right)
-
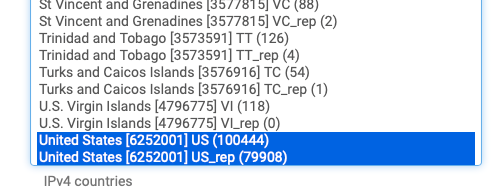
Click United States US and US_rep and hit Save
-
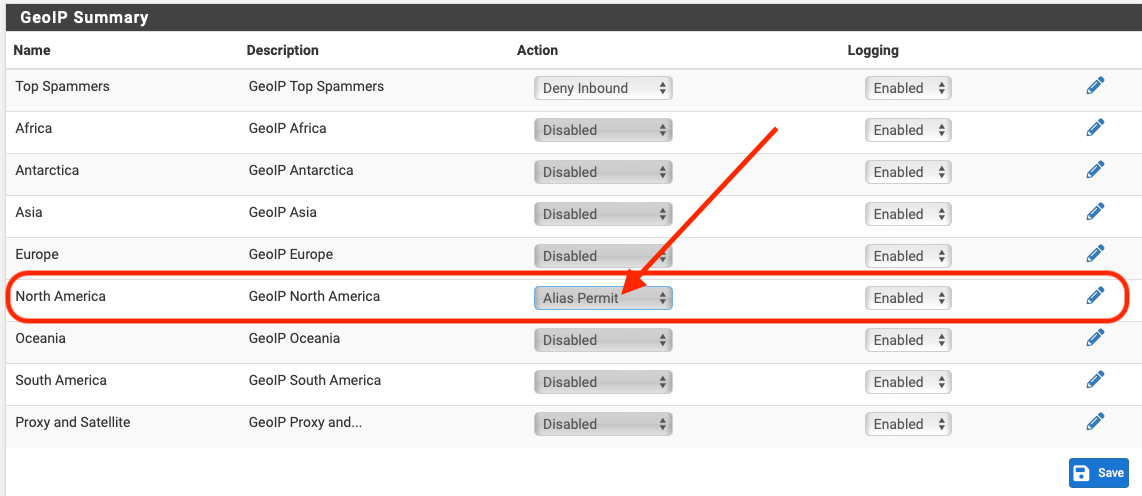
Select "Alias Permit" which according to the pfB info "'Alias' rules create an alias for the list (and do nothing else)."
-
Reload -> IP
-
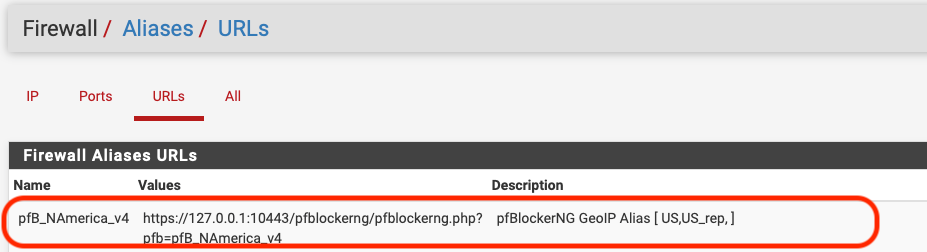
Go to Firewall -> Aliases and check that the list is there
-
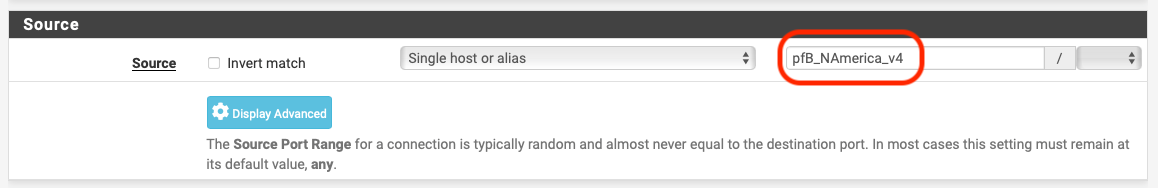
Go to Firewall -> Rules, select your (V)LAN and create new rule
-
Use the alias to block or allow
Or did you mean something entirely different?
-
-
@Cabledude Just to note it, Alias Permit is to allow traffic. IIRC pfB does require a port selection for that, rather than opening all of WAN.
If you just want your own rules I use Alias Native which just creates an alias. No need to worry if the deduplication setting will strip out anything, and allows finer control over rule ordering.
-
@SteveITS Thank you Steve. So I gather that apart from the Alias options (Permit vs Native etc.) the steps I laid out are accurate?
Just for learning purposes I created two Aliases:
- North America US + US_rep / Alias Permit
- Africa MW (Malawi) / Alias Native
I see no difference in the Firewall / Aliases / URL's tab:
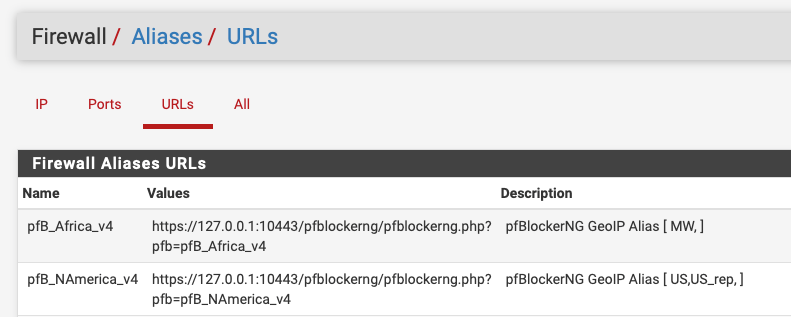
Therefore I still don't quite understand what you just wrote about deduplication / strip / finer control over rule ordering.
Care to elaborate? Please be patient I am completely new to this method of building rules with Alias lists.
Thanks!
Pete -
@Cabledude said in GeoIP "GB_rep_v4.txt" list contains my domain ISP:
Select "Alias Permit" which according to the pfB info "'Alias' rules create an alias for the list (and do nothing else)."
No that is not what "I" do - I just use pfblocker to create native lists.. I then use those lists in my firewall rules or forwards. Nor do I edit the built in regions.
I just create my own aliases..
Here for example is the one for my plex.
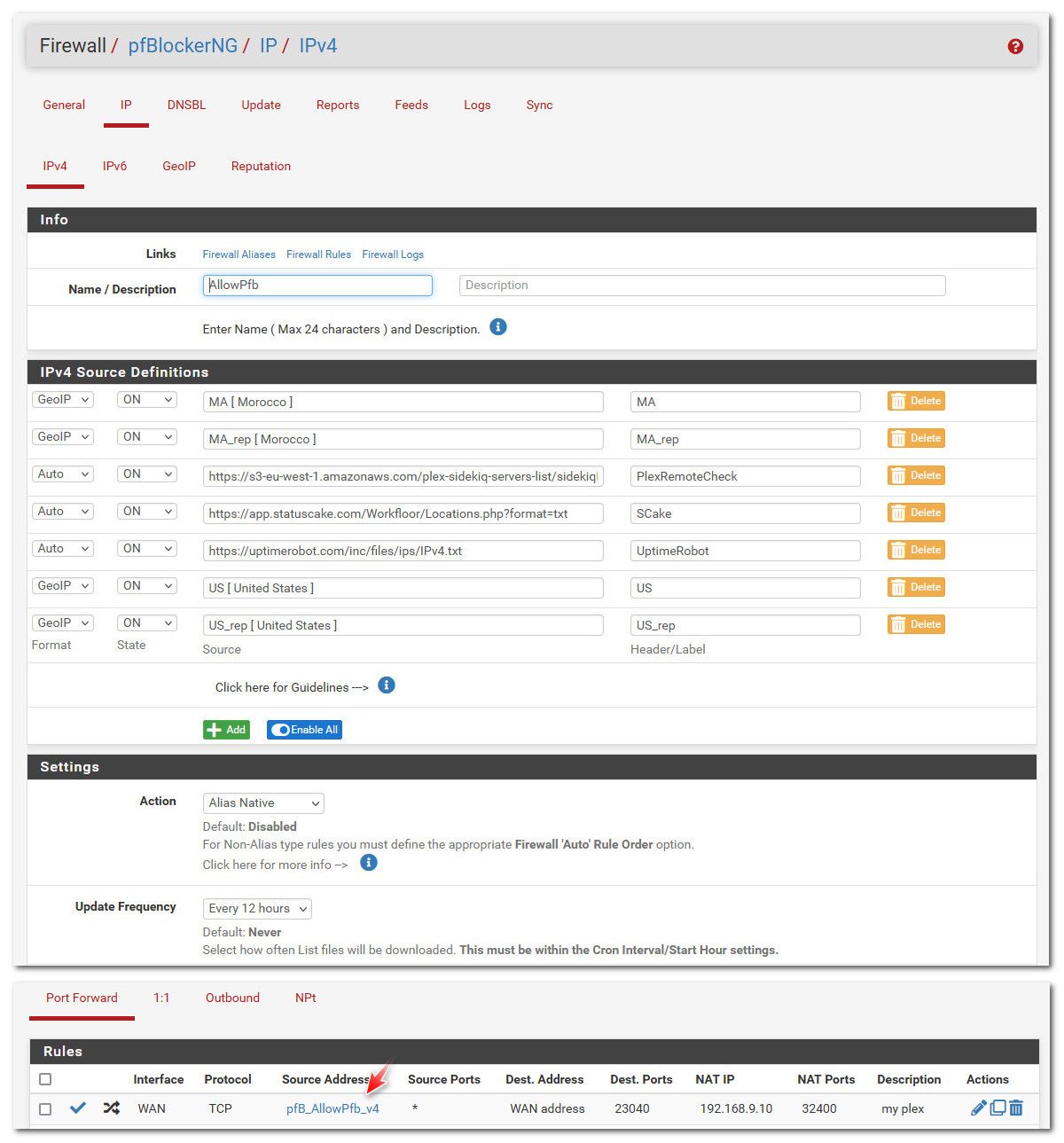
Those other lists in the alias are the status cake IPs and UPtime robot IPs and plex IPs that check if your server is available remotely. These IPs might not just be in the US.. They could be IPs from really anywhere.. So they need to be included to be able to talk to my plex if I want to show that it is online for my monitoring - I get an alert from from status cake or uptime robot if it can not talk to my plex server. The us and morocco geoip base lists make sure that my users can talk to my plex, as long as they are coming from IPs in those lists.. If one of my users decided to take a trip to canada or germany - they would be out of luck unless they let me know, so I could add those where they are at to the list.
I also do use some lists for blocking, but they are not geoip based. Stupid scanning services.. Digital Ocean, Shodan, strechoid, etc. DO - nothing good is ever going to come from there ;) That scan deny list is high up on my rules..
pfblocker is a very powerful tool - I barely scratch the surface of what it can actually do. But I currently don't have desire to use its other features. But I for sure use it, how you use it is up to you.. But its great for creating aliases be they asn based, list based, geoIP based, etc. etc..
-
@johnpoz Excellent example, thank you. So you simply go to pfBlocker / IP / IPv4 and click Add to create a new list. I had not thought of that.
Then in WAN rules, you forward plex traffic sent to port 23040 to your plex server, while allowing only the IPv4 addresses in your custom list. Very clever.
So the key is that the lists are just lists (no block / allow) and you use them in the firewall rule as source and you set the firewall rule to block or allow.
-
Hi all, I really learned some nice things today so thanks to you all, I really appreciate it.