Firewall rules for vlan
-
Now that my network is up and running with basic settings, I’m trying to tune the firewall rules to make it more secure on a standard level ready for specific rules in the future for Plex etc.
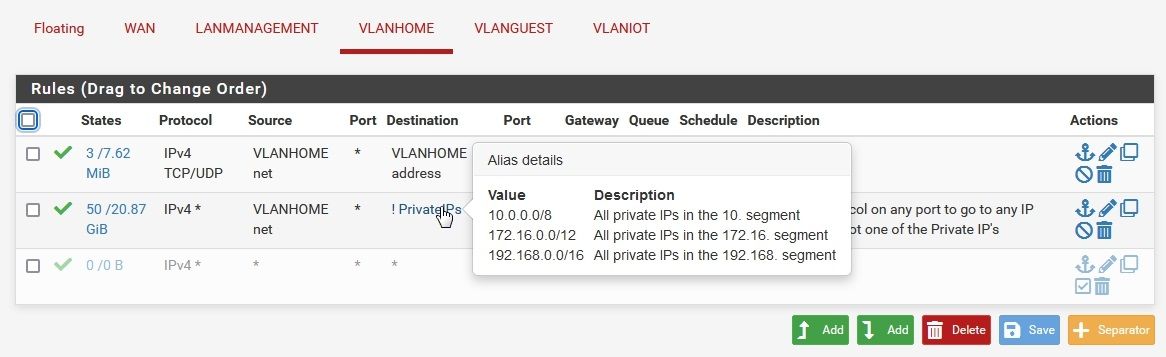
I’ve followed a YouTube video by Raid Owl and now have 2 basic rules in the vlans. One which allows any protocol to from the specific vlan to any IP apart from those IPs within an alias that contain all private IPs and a second rule which allows DNS to work.
As such the devices within the vlan can connect to the internet but not each other and they can’t ping other devices within the vlan either. I’m thinking I should be adding a rule within the HOME vlan and within the IOT vlan to ping (communicate) with each other so that my home network can see my printer, NAS (when built) etc. any reason I shouldn’t be doing this?
I’m also thinking I won’t need this on my GUEST vlan as those devices only need the internet and no interconnectivity.
-
R rcoleman-netgate moved this topic from L2/Switching/VLANs on
-
@Polar_Bear88 I may be misinterpreting what’s written but devices on the same VLAN don’t go through the router so are not affected by firewall rules.
Going between VLANs does need firewall rules. Auto detection/mDNS may need the avahi package but connecting by IP will work. The firewall on the NAS etc. needs to allow the other subnet.
-
@SteveITS
Since adding the rule my devices in the same vlan can no longer ping each other. -
@Polar_Bear88 I hear what you're saying but that's not how it works. If 10.0.0.2/24 wants to talk to 10.0.0.3/24 it would not send the packet to its gateway. From the firewall's perspective a VLAN is not logically different than a physical interface. Does that block rule show traffic in the column to the left? Maybe show us your rules.
-
Will do when I next get a chance. At the minute the time I’m getting to play with it is few and far between so may be a while.
I’ll admit, it’s also entirely possible that as I was tired and it was late at night I could have been mistyping like I sometimes so. In theory I was trying to ping from 10.100.3.5 to 10.100.3.1 (the interface) and to 10.100.3.7 (my iOS device) but that doesn’t mean it’s what I actually typed in.
-
I had a chance to go and re-test things and take some screenshots.
Ive only added the rules to one vlan so far (VLAN HOME) and will roll them out to the other vlans once they're working
On VLAN HOME I had the following IPs:
Desktop = 10.100.3.3
IOS = 10.100.3.6I preformed the following ping tests:
Desktop (10.100.3.3) to Interface (10.100.3.1) = Fail with all packets lost
Desktop (10.100.3.3) to IOS (10.100.3.6) = Fail with all packets lost
Desktop (10.100.3.3) to Laptop (192.168.1.1) = Fail with all packets lost as expected
Desktop (10.100.3.3) to LAN Interface (10.100.3.1) = Fail with all packets lost as expected
Desktop (10.100.3.3) to 8.8.8.8 = Success
Desktop (10.100.3.3) to www.google.com = SuccessOn VLAN IOT I had the following IPs:
Laptop = 10.100.5.205
Device 1 = 10.100.5.3
Device 1 = 10.100.5.5I preformed the following ping tests:
Laptop (10.100.5.205) to Interface (10.100.5.1) = Success
Laptop (10.100.5.205) to Device 1 (10.100.5.3) = Success
Laptop (10.100.5.205) to Device 2 (10.100.5.5) = Success
Laptop (10.100.5.205) to 8.8.8.8 = Success
Laptop (10.100.5.205) to www.google.com = Success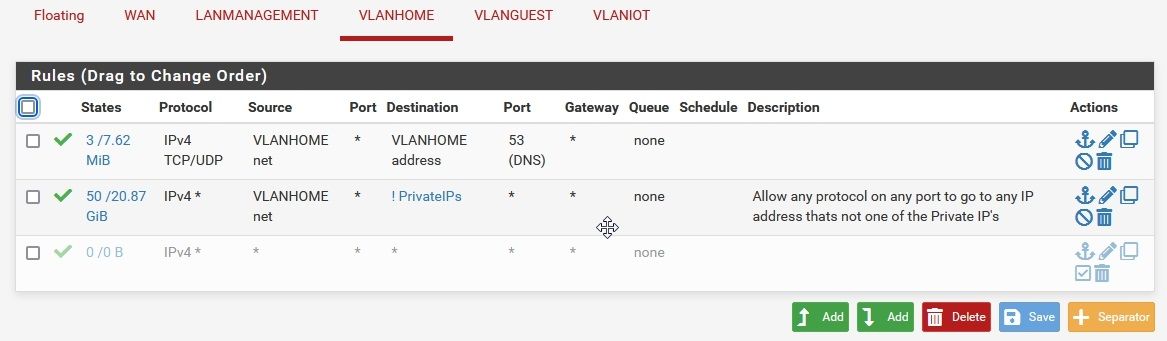
-
@Polar_Bear88 The VLANHOME rules do not allow ICMP to 10.100.3.1, only TCP and UDP for port 53. I don't know why the devices can't ping each other. Is that a wireless network marked as "guest" or "isolate"?
-
Ok so the ping to the interface makes sense and I just nee dto add a rule to allow that if I want it to be able to.
GUEST will be primarily WIFI but there are hardwired connections such as at my test bench in case I'm connecting an untrusted device but I need internet access. The unifi switches are configured to only allow GUEST on that port. It currently has the same rules as IOT until Ive got all the rules working on 1 VLAN and can copy them accross as required.
Hoping someone can weigh in on why devices on the HOME VLAN cant ping each other so I can see where I've configured it wrong
-
@Polar_Bear88 said in Firewall rules for vlan:
why devices on the HOME VLAN cant ping each other
Is the subnet mask on each correct? Do the devices have a firewall and is it allowing ICMP?
-
Sorry for the very delayed reply, this is the first chance Ive had to do some testing.
It now appears as if its working, although please let me know if I'm missing something, and the only thing I've done is that I restarted the router the other day due to some issues with my internet connection.
I started off my confirming all subnets and IPs were correct then proceeded with the following tests
Desktop 10.100.3.3 255.255.255.0
Firestick 10.100.3.5 255.255.255.0
Mobile 10.100.3.6 255.255.255.0
Tablet 10.100.3.7 255.255.255.0Laptop 192.168.1.21 255.255.255.0
Desktop to Firestick SUCCESS
Desktop to Mobile SUCCESS
Desktop to tablet SUCCESS
Desktop to www.google.co.uk SUCCESS
Desktop to 8.8.8.8 SUCCESS
Desktop to 10.100.3.1 FAIL (as expected)
Desktop to Laptop FAIL (as expected)Mobile to Desktop FAIL (Not as expected but research shows this is a windows firewall rule I need to configure)
Mobile to Firestick SUCCESS
Mobile to Tablet SUCCESS
Mobile to www.google.co.uk SUCCESS
Mobile to 8.8.8.8 SUCCESS
Mobile to 10.100.3.1 FAIL (as expected)
Mobile to Laptop FAIL (as expected)Tablet to Desktop FAIL (Not as expected but research shows this is a windows firewall rule I need to configure)
Tablet to Firestick SUCCESS
Tablet to Mobile SUCCESS
Tablet to www.google.co.uk SUCCESS
Tablet to 8.8.8.8 SUCCESS
Tablet to 10.100.3.1 FAIL (as expected)
Tablet to Laptop FAIL (as expected)